CN111787538A - Host resource configuration apparatus, method, and computer-readable storage medium - Google Patents
Host resource configuration apparatus, method, and computer-readable storage mediumDownload PDFInfo
- Publication number
- CN111787538A CN111787538ACN202010307435.6ACN202010307435ACN111787538ACN 111787538 ACN111787538 ACN 111787538ACN 202010307435 ACN202010307435 ACN 202010307435ACN 111787538 ACN111787538 ACN 111787538A
- Authority
- CN
- China
- Prior art keywords
- host
- network
- resource configuration
- slave
- establishing
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
- 238000000034methodMethods0.000titleclaimsabstractdescription57
- 238000012795verificationMethods0.000claimsdescription15
- 238000001514detection methodMethods0.000claimsdescription4
- 238000013468resource allocationMethods0.000claims1
- 230000002452interceptive effectEffects0.000abstractdescription5
- 230000005012migrationEffects0.000abstractdescription4
- 238000013508migrationMethods0.000abstractdescription4
- 230000000694effectsEffects0.000description55
- 230000007774longtermEffects0.000description24
- 230000005540biological transmissionEffects0.000description9
- 239000000523sampleSubstances0.000description6
- 238000004891communicationMethods0.000description5
- 238000005516engineering processMethods0.000description5
- 238000000060site-specific infrared dichroism spectroscopyMethods0.000description5
- 230000003993interactionEffects0.000description3
- 238000012986modificationMethods0.000description3
- 230000004048modificationEffects0.000description3
- 239000008186active pharmaceutical agentSubstances0.000description2
- 230000003542behavioural effectEffects0.000description2
- 230000006870functionEffects0.000description2
- 238000012545processingMethods0.000description2
- 230000002159abnormal effectEffects0.000description1
- 230000007812deficiencyEffects0.000description1
- 238000010586diagramMethods0.000description1
- 239000003999initiatorSubstances0.000description1
- 230000000977initiatory effectEffects0.000description1
- 230000007246mechanismEffects0.000description1
- 230000003287optical effectEffects0.000description1
- 230000008569processEffects0.000description1
- 238000011160researchMethods0.000description1
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/06—Authentication
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W48/00—Access restriction; Network selection; Access point selection
- H04W48/16—Discovering, processing access restriction or access information
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W76/00—Connection management
- H04W76/10—Connection setup
Landscapes
- Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Computer Security & Cryptography (AREA)
- Mobile Radio Communication Systems (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本申请涉及网络接入技术领域,具体涉及一种主机资源配置方法,一 种应用所述主机资源配置方法的主机资源配置装置,以及一种计算机可读 存储介质。The present application relates to the technical field of network access, and in particular, to a host resource configuration method, a host resource configuration device applying the host resource configuration method, and a computer-readable storage medium.
背景技术Background technique
随着以智能手机、平板电脑为首的电子装置的使用日益频繁,越来越 多的用户通过各种电子装置进行组织活动,比如一起出游、建立兴趣爱好 集群、建立资源分享群等等。一般来说,电子装置组建活动时,会至少有 一台主机和一台从机(或辅机)。一般其中一部设备为主机,其他的为从机, 主机不能更换,从机可以随时退出。With the increasingly frequent use of electronic devices such as smart phones and tablet computers, more and more users use various electronic devices to organize activities, such as traveling together, establishing hobby clusters, establishing resource sharing groups, and so on. Generally speaking, there will be at least one master and one slave (or auxiliary) when an electronic device is organized. Generally, one of the devices is the master, and the others are slaves. The master cannot be replaced, and the slaves can exit at any time.
为了实现主机和从机之间的连接,现有技术可以采用下述几种。In order to realize the connection between the master and the slave, the following types of technologies can be adopted in the prior art.
Ad-hoc模式:(点对点)模式是最早期的直连方式,它是一种特殊的无 线移动网络。网络中所有结点的地位平等,无需设置任何的中心控制结点。Ad-hoc mode: (peer-to-peer) mode is the earliest direct connection method, which is a special wireless mobile network. All nodes in the network have equal status, and there is no need to set up any central control node.
SoftAP(共享)模式:SoftAP(共享)模式要某个终端虚拟成AP,以 此来实现连接。目前来说一般SoftAP模式可以接入的终端数为7~10个。 这种模式在3G路由器、手机中有很多的应用。SoftAP (shared) mode: SoftAP (shared) mode requires a terminal to be virtualized into an AP to realize the connection. Generally speaking, the number of terminals that can be accessed in SoftAP mode is 7 to 10. This mode has many applications in 3G routers and mobile phones.
此外,如果采用WiFi直连作为核心技术,就是WiFi设备点对点连接 (WiFi P2P),允许具有适当硬件的Android 4.0(API级别14)或更高版本 的设备通过Wi-Fi直接相互连接,而无需中间接入点。使用这些API,可以 发现并连接到其他设备(前提是每个设备支持Wi-Fi P2P),然后通过比蓝 牙连接更长的距离快速连接进行通信。In addition, if WiFi Direct is used as the core technology, it is WiFi Device Peer-to-Peer (WiFi P2P), which allows Android 4.0 (API level 14) or higher devices with appropriate hardware to connect directly to each other over Wi-Fi without intermediaries Access Point. Using these APIs, it is possible to discover and connect to other devices (provided each device supports Wi-Fi P2P), and then communicate over faster connections over longer distances than Bluetooth connections.
WiFi Direct(WiFi P2P)技术是Ad-hoc模式的延续,它要比Ad-hoc 模式更快,同时也支持WPA2的加密机制。最大传输距离可达到200米,最 大传输速度为250Mbps,使用2.4GHz与5GHz两种频段频段,并它支持一对 一,以及一对多模式。WiFi Direct (WiFi P2P) technology is the continuation of Ad-hoc mode, it is faster than Ad-hoc mode, and also supports WPA2 encryption mechanism. The maximum transmission distance can reach 200 meters, the maximum transmission speed is 250Mbps, using two frequency bands, 2.4GHz and 5GHz, and it supports one-to-one and one-to-many modes.
然而,现有技术的主机只设置一部设备,主机单一,一旦主机出现异 常,整个party活动均停止;而WiFi直连虽然解决了资源共享问题,支持 一对一,以及一主机对多从机的模式,但是,不支持多主机对一从机的模 式,主机不能进行迁移切换等。However, the host in the prior art is only set up with one device, and the host is single. Once the host is abnormal, the whole party activity will stop; while the WiFi direct connection solves the problem of resource sharing and supports one-to-one and one-to-many slaves However, it does not support the multi-master to one-slave mode, and the master cannot perform migration and switching.
针对现有技术的多方面不足,本申请的发明人经过深入研究,提出一 种主机资源配置装置、方法及计算机可读存储介质。In view of various deficiencies in the prior art, the inventor of the present application, after in-depth research, proposes a host resource configuration apparatus, method, and computer-readable storage medium.
发明内容SUMMARY OF THE INVENTION
本申请的目的在于,提供一种主机资源配置装置、方法及计算机可读 存储介质,能够通过多台主机提供资源服务,实现主机之间的切换,方便 更换主机资源,方便用户使用,促进用户设备之间的互动性能。The purpose of this application is to provide a host resource configuration device, method and computer-readable storage medium, which can provide resource services through multiple hosts, realize switching between hosts, facilitate the replacement of host resources, facilitate user use, and promote user equipment. interactive performance.
为解决上述技术问题,本申请提供一种主机资源配置方法,作为其中 一种实施方式,包括步骤:In order to solve the above-mentioned technical problems, the present application provides a method for configuring host resources, which, as one of the implementations, includes the steps:
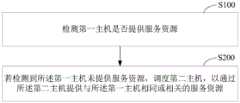
检测第一主机是否提供服务资源;Detecting whether the first host provides service resources;
若检测到所述第一主机未提供服务资源,调度第二主机,以通过所述 第二主机提供与所述第一主机相同或相关的服务资源。If it is detected that the first host does not provide service resources, a second host is scheduled to provide the same or related service resources as the first host through the second host.
作为其中一种实施方式,所述方法还包括步骤:As one of the embodiments, the method further includes the steps:
所述第一主机将包括所述第一主机和所述第二主机的网络信息发送给 网络连接的从机,以使得所述从机可根据所述网络信息接入所述第一主机 或第二主机获取服务资源。The first host sends network information including the first host and the second host to a network-connected slave, so that the slave can access the first host or the second host according to the network information. The second host obtains service resources.
作为其中一种实施方式,所述第一主机将包括所述第一主机和所述第 二主机的网络信息发送给网络连接的从机的步骤之前,还包括:As an implementation manner, before the step of sending the network information including the first host and the second host to the network-connected slave, the first host further includes:
第一主机与第二主机之间建立网络连接,以进行配对绑定。A network connection is established between the first host and the second host for pairing and binding.
作为其中一种实施方式,所述第一主机与第二主机之间建立网络连接, 以进行配对绑定的步骤,具体包括:As an implementation manner, the step of establishing a network connection between the first host and the second host to perform pairing and binding specifically includes:
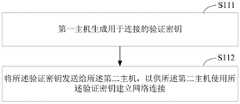
第一主机生成用于连接的验证密钥;the first host generates an authentication key for the connection;
将所述验证密钥发送给所述第二主机,以供所述第二主机使用所述验 证密钥建立网络连接。The verification key is sent to the second host for the second host to use the verification key to establish a network connection.
作为其中一种实施方式,所述第一主机与第二主机之间建立网络连接 的步骤,还包括:As one of the implementation manners, the step of establishing a network connection between the first host and the second host further includes:
第一主机获取所述第二主机通过网络发送的属于所述第二主机的第二 网络标识,以将属于第一主机的第一网络标识和所述第二网络标识配置成 所述网络信息。The first host obtains the second network identifier belonging to the second host sent by the second host through the network, so as to configure the first network identifier and the second network identifier belonging to the first host as the network information.
作为其中一种实施方式,所述第一主机与第二主机之间建立网络连接 的步骤之后,还包括:As one of the implementation manners, after the step of establishing a network connection between the first host and the second host, it further includes:
第一主机将所述服务资源的信息表和/或数据内容发送给第二主机,以 使得所述第二主机根据所述信息表和/或数据内容提供相同或相关的服务 资源。The first host sends the information table and/or data content of the service resource to the second host, so that the second host provides the same or related service resource according to the information table and/or data content.
作为其中一种实施方式,所述第一主机与第二主机之间建立网络连接 的步骤之后,还包括:As one of the implementation manners, after the step of establishing a network connection between the first host and the second host, it further includes:
第一主机获取网络连接的从机列表;The first host obtains a list of slaves connected to the network;
将所述从机列表发送给所述第二主机进行缓存。Sending the slave list to the second host for caching.
作为其中一种实施方式,所述方法还包括步骤:As one of the embodiments, the method further includes the steps:
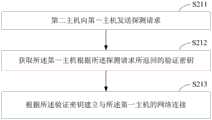
第二主机向第一主机发送探测请求;The second host sends a probe request to the first host;
获取所述第一主机根据所述探测请求所返回的验证密钥;obtaining the verification key returned by the first host according to the probe request;
根据所述验证密钥建立与所述第一主机的网络连接。A network connection with the first host is established according to the authentication key.
作为其中一种实施方式,所述根据所述验证密钥建立与所述第一主机 的网络连接的步骤之后,还包括:As one of the implementation manners, after the step of establishing a network connection with the first host according to the verification key, the method further includes:
第二主机获取自身的第二网络标识;The second host obtains its own second network identifier;
将所述第二网络标识发送给所述第一主机,以供所述第一主机或其他 从机接入。Sending the second network identification to the first host for access by the first host or other slaves.
为解决上述技术问题,本申请还提供一种主机资源配置装置,作为其 中一种实施方式,其配置有处理器,所述处理器用于执行主机资源配置程 序,以实现包括如上所述的主机资源配置方法。In order to solve the above-mentioned technical problem, the present application also provides a host resource configuration device, as one of the embodiments, it is configured with a processor, and the processor is configured to execute a host resource configuration program, so as to realize the host resource including the above-mentioned host resources. configuration method.
为解决上述技术问题,本申请还提供一种计算机可读存储介质,作为 其中一种实施方式,其用于存储主机资源配置程序,所述主机资源配置程 序在被处理器执行时,以实现包括如上所述的主机资源配置方法。In order to solve the above technical problems, the present application also provides a computer-readable storage medium, which is used as an implementation manner to store a host resource configuration program, and when the host resource configuration program is executed by a processor, to achieve Host resource configuration method as described above.
本申请提供的主机资源配置装置、方法及计算机可读存储介质,所述 主机资源配置方法包括步骤:检测第一主机是否提供服务资源,若检测到 所述第一主机未提供服务资源,调度第二主机,以通过所述第二主机提供 与所述第一主机相同或相关的服务资源。通过上述方式,本申请能够通过 多台主机提供资源服务,实现主机之间的切换,方便更换主机资源,方便 用户使用,促进用户设备之间的互动性能。The host resource configuration device, method and computer-readable storage medium provided by the present application, the host resource configuration method includes the steps of: detecting whether a first host provides service resources, and if it is detected that the first host does not provide service resources, scheduling the first host A second host, so as to provide the same or related service resources as the first host through the second host. In the above manner, the present application can provide resource services through multiple hosts, realize switching between hosts, facilitate replacement of host resources, facilitate user use, and promote interactive performance between user equipment.
上述说明仅是本申请技术方案的概述,为了能够更清楚了解本申请的 技术手段,而可依照说明书的内容予以实施,并且为了让本申请的上述和 其他目的、特征和优点能够更明显易懂,以下特举较佳实施例,并配合附 图,详细说明如下。The above description is only an overview of the technical solution of the present application, in order to be able to understand the technical means of the present application more clearly, it can be implemented according to the contents of the description, and in order to make the above and other purposes, features and advantages of the present application more obvious and easy to understand , the following specific preferred embodiments, and in conjunction with the accompanying drawings, are described in detail as follows.
附图说明Description of drawings
图1为本申请主机资源配置方法一实施方式的流程示意图。FIG. 1 is a schematic flowchart of an embodiment of a method for configuring host resources according to the present application.
图2为实现本申请主机资源配置方法一具体应用例的流程示意图。FIG. 2 is a schematic flowchart of implementing a specific application example of the host resource configuration method of the present application.
图3为实现本申请主机资源配置方法另一具体应用例的流程示意图。FIG. 3 is a schematic flowchart of implementing another specific application example of the host resource configuration method of the present application.
图4为本申请主机资源配置方法一具体应用例的流程示意图。FIG. 4 is a schematic flowchart of a specific application example of the host resource configuration method of the present application.
图5为本申请主机资源配置装置一实施方式的功能模块示意图。FIG. 5 is a schematic diagram of functional modules of an embodiment of an apparatus for configuring host resources according to the present application.
具体实施方式Detailed ways
为更进一步阐述本申请为达成预定申请目的所采取的技术手段及功 效,以下结合附图及较佳实施例,对本申请详细说明如下。In order to further illustrate the technical means and effects adopted by the present application to achieve the intended application purpose, the present application is described in detail below in conjunction with the accompanying drawings and preferred embodiments.
通过具体实施方式的说明,当可对本申请为达成预定目的所采取的技 术手段及效果得以更加深入且具体的了解,然而所附图式仅是提供参考与 说明之用,并非用来对本申请加以限制。Through the description of the specific embodiments, the technical means and effects adopted by the present application to achieve the intended purpose can be more deeply and specifically understood. However, the accompanying drawings are only used for reference and description, and are not used for the present application. limit.
请参阅图1,图1为本申请主机资源配置方法一实施方式的流程示意图。Please refer to FIG. 1 , which is a schematic flowchart of an embodiment of a method for configuring host resources according to the present application.
需要说明的是,本实施方式所述主机资源配置方法可以应用到手机、 平板电脑、笔记本电脑以及其他可穿戴设备中,其可以包括但不限于如下 几个步骤。It should be noted that the host resource configuration method described in this embodiment can be applied to mobile phones, tablet computers, notebook computers and other wearable devices, which may include but are not limited to the following steps.
步骤S100,检测第一主机是否提供服务资源;Step S100, detecting whether the first host provides service resources;
步骤S200,若检测到所述第一主机未提供服务资源,调度第二主机, 以通过所述第二主机提供与所述第一主机相同或相关的服务资源。Step S200, if it is detected that the first host does not provide service resources, schedule a second host to provide the same or related service resources as the first host through the second host.
在本实施方式中,所述方法还可以包括步骤:所述第一主机将包括所 述第一主机和所述第二主机的网络信息发送给网络连接的从机,以使得所 述从机可根据所述网络信息接入所述第一主机或第二主机获取服务资源。In this embodiment, the method may further include the step of: the first host sending network information including the first host and the second host to a network-connected slave, so that the slave can Access to the first host or the second host according to the network information to obtain service resources.
具体而言,本实施方式所述第一主机将包括所述第一主机和所述第二 主机的网络信息发送给网络连接的从机的步骤之前,还可以包括:第一主 机与第二主机之间建立网络连接,以进行配对绑定。Specifically, before the step of sending the network information including the first host and the second host to the network-connected slaves by the first host in this embodiment, the first host may further include: the first host and the second host Establish a network connection between them for pairing and binding.
值得一提的是,请参阅图2,本实施方式所述第一主机与第二主机之间 建立网络连接,以进行配对绑定的步骤,具体可以包括:It is worth mentioning that, referring to FIG. 2 , the steps of establishing a network connection between the first host and the second host in this embodiment to perform pairing and binding may specifically include:
步骤S111,第一主机生成用于连接的验证密钥;Step S111, the first host generates a verification key for connection;
步骤S112,将所述验证密钥发送给所述第二主机,以供所述第二主机 使用所述验证密钥建立网络连接。Step S112: Send the verification key to the second host, so that the second host can use the verification key to establish a network connection.
在具体的实施方式中,所述第一主机与第二主机之间建立网络连接的 步骤,还可以包括:第一主机获取所述第二主机通过网络发送的属于所述 第二主机的第二网络标识,以将属于第一主机的第一网络标识和所述第二 网络标识配置成所述网络信息。In a specific implementation manner, the step of establishing a network connection between the first host and the second host may further include: the first host acquiring the second host belonging to the second host sent by the second host through the network A network identifier, so as to configure the first network identifier and the second network identifier belonging to the first host as the network information.
需要说明的是,本实施方式所述第一主机与第二主机之间建立网络连 接的步骤之后,还包括:第一主机将所述服务资源的信息表和/或数据内容 发送给第二主机,以使得所述第二主机根据所述信息表和/或数据内容提供 相同或相关的服务资源。It should be noted that, after the step of establishing a network connection between the first host and the second host in this embodiment, the step further includes: the first host sending the information table and/or data content of the service resource to the second host , so that the second host provides the same or related service resources according to the information table and/or data content.
在本实施方式中,所述第一主机与第二主机之间建立网络连接的步骤 之后,还包括:第一主机获取网络连接的从机列表;将所述从机列表发送 给所述第二主机进行缓存。In this embodiment, after the step of establishing a network connection between the first host and the second host, the step further includes: the first host acquires a list of slaves connected to the network; and sending the slave list to the second host host for caching.
需要补充说明的是,在另一个实施方式中,请参阅图3,所述方法还可 以包括步骤:It should be added that, in another embodiment, referring to Fig. 3, the method may also include the steps:
步骤S211,第二主机向第一主机发送探测请求;Step S211, the second host sends a probe request to the first host;
步骤S212,获取所述第一主机根据所述探测请求所返回的验证密钥;Step S212, obtaining the verification key returned by the first host according to the probe request;
步骤S213,根据所述验证密钥建立与所述第一主机的网络连接。Step S213, establishing a network connection with the first host according to the verification key.
进一步而言,本实施方式所述根据所述验证密钥建立与所述第一主机 的网络连接的步骤之后,还包括:第二主机获取自身的第二网络标识;将 所述第二网络标识发送给所述第一主机,以供所述第一主机或其他从机接 入。Further, after the step of establishing a network connection with the first host according to the verification key in this embodiment, it further includes: the second host obtains its own second network identifier; sent to the first host for access by the first host or other slaves.
下面将结合具体实施例对上述实施方式进行举例说明。The foregoing implementation manner will be illustrated below with reference to specific embodiments.
1.选定第一主机、第二主机,第一主机、第二主机相互绑定;第一主 机、第二主机二者优先配对,第一主机的无线网络设备根据探测请求帧生 成带有WP/WP2认证的PMK密钥并发送给第二主机;第二主机端以开放鉴权 方式与第一主机设备建立连接;连接建立之后,第二主机自动生成带有自 身标识的无线地址信息传送给第一主机;1. Select the first host and the second host, and the first host and the second host are bound to each other; the first host and the second host are paired preferentially, and the wireless network device of the first host generates a WP with WP according to the detection request frame. The PMK key authenticated by /WP2 is sent to the second host; the second host establishes a connection with the first host device in an open authentication mode; after the connection is established, the second host automatically generates wireless address information with its own identity and transmits it to the first host;
2.第一主机机作为主机,利用现有的分享共享方式将含有第一主机、 第二主机二者的无线入网标识分享出去,从机partyer选择加入;2. The first host computer is used as the host computer, and the wireless network access identifier containing the first host computer and the second host computer is shared by using the existing sharing and sharing method, and the slave partyer chooses to join;
3.由于从机中存在第一主机和第二主机的两个配对信息,一旦从机确 认加入即确认同意加入第二主机;第二主机再次接收到第一主机的配对信 息,选择加入,此时也默认以将所有从机列表缓存至第二主机端;3. Since there are two pairing information of the first host and the second host in the slave, once the slave confirms to join, it confirms that it agrees to join the second host; the second host receives the pairing information of the first host again, and chooses to join. It also defaults to cache all slave lists to the second host;
4.由此完成将主、副主机的无线配对信息植入到各从机中;4. From this, the wireless pairing information of the master and slave masters are implanted into each slave;
5.第一主机退出,第二主机直接发挥主机作用提供资源服务。5. The first host exits, and the second host directly plays the role of the host to provide resource services.
本实施方式基于WiFi直连的核心技术共享文件数据的方案。依靠主从 机的相互绑定,使得从机同时访问了两台主机,在优先的原则下已首次分 享者作为第一主机,而第二主机作为备选。在第一主机退出后,信号间自动 搜索,默认自动连接第二主机使得party活动连续地持续进行下去。从而 在不违背WiFi直连的技术前提下,实现主机资源的自动迁移。This embodiment is based on the solution of sharing file data based on the core technology of WiFi direct connection. Relying on the mutual binding of master and slave, the slave accesses two masters at the same time. Under the principle of priority, the first sharer is the first master, and the second master is the alternative. After the first host exits, the signals are automatically searched, and the second host is automatically connected by default so that the party activities continue continuously. Therefore, the automatic migration of host resources can be realized without violating the technical premise of WiFi direct connection.
请参阅图4,在party上当主机A因为异常而退出的时候,主机B会直 接上位,由此保证了party的延续性;主机A退出了,主机A宿主迁移的 时候,歌曲列表可以跟着直接迁移,当然还可以听到不一样的歌曲,即可 以听到主机B的歌曲,增加了播放的选择性。此外,本实施方式可以不限 于两个主机,还可以设置3个或更多个主机。Please refer to Figure 4. When host A quits due to an exception on the party, host B will directly take over, thus ensuring the continuity of the party; when host A quits and host A is migrated, the song list can be directly migrated. , of course, you can also hear different songs, that is, you can hear the songs of host B, which increases the selectivity of playback. Furthermore, the present embodiment may not be limited to two hosts, and three or more hosts may be provided.
本实施方式还可以对从机加入主机进行活动组织的方式进行举例说 明,具体包括如下步骤。This embodiment can also illustrate the manner in which the slave joins the host to organize activities, which specifically includes the following steps.
设置用于加入集群活动的会话分享模式;Set the session sharing mode for joining cluster activities;
根据所述会话分享模式生成会话加入路径;generating a session joining path according to the session sharing mode;
根据所述会话加入路径提供用于实现可跨设备扫描接入的第一网络入 口,和/或,根据所述会话加入路径提供用于实现键入信息接入的第二网络 入口,以进行会话通信连接。Providing a first network entry for implementing cross-device scan access according to the session joining path, and/or providing a second network entry for implementing keyed information access according to the session joining path, for session communication connect.
值得说明的是,本实施方式的集群活动,可以指的是多人语音共享, 比如卡拉OK等party活动,或者其他户外活动等。It should be noted that the cluster activity in this embodiment may refer to voice sharing among multiple people, such as party activities such as karaoke, or other outdoor activities.
在本实施方式中,所述会话分享模式,指的是需要实现与其他设备建 立连接,从而进行数据分享、活动分享等行为模式。In this embodiment, the session sharing mode refers to a behavioral mode that needs to establish a connection with other devices, thereby performing data sharing, activity sharing, and the like.
值得一提的是,本实施方式的会话加入路径,可以指的是通过网络、 端口、通信方式、物理连接等进行相互连接的途径。It is worth mentioning that the session joining path in this embodiment may refer to a path for connecting to each other through a network, a port, a communication method, a physical connection, or the like.
在本实施方式中,所述跨设备,一般而言指的是可以跨过第一/第二主 机,而在从机之间实现快速分享由第一/第二主机发起的分享活动。In this implementation manner, the cross-device generally means that the first/second host can be crossed, and the sharing activity initiated by the first/second host can be quickly shared between the slaves.
通过上述方式,本申请能够支持随时随地快速加入分享队列,融入 party活动的效果。Through the above method, the present application can support the rapid joining of the sharing queue anytime and anywhere, and integrate into the effect of party activities.
进一步而言,本实施方式所述根据所述会话加入路径提供用于实现可 跨设备扫描接入的第一网络入口的步骤,具体可以包括:提供用于实现可 跨设备扫描的短时效二维码或长时效二维码进行接入的第一网络入口。Further, the step of providing a first network entry for realizing cross-device scanning access according to the session joining path described in this embodiment may specifically include: providing a short-term two-dimensional two-dimensional network for realizing cross-device scanning. The first network entry for accessing via code or long-term QR code.
本实施方式所述的短时效二维码,可以指的是维持几小时、几天或者 几周时间的有效期的二维码;相对地,所述长时效二维码,则可以指的是 相对于该短时效二维码而设置的有效期更长的二维码,比如可以是几天、 几周或者几个月,甚至永久有效等。The short-term two-dimensional code in this embodiment may refer to a two-dimensional code that maintains a validity period of several hours, days or weeks; relatively, the long-term two-dimensional code may refer to a relatively long-term two-dimensional code. A two-dimensional code with a longer validity period is set for the short-lived two-dimensional code, such as a few days, a few weeks, or a few months, or even a permanent validity.
需要说明的是,本实施方式所述根据所述会话加入路径提供用于实现 键入信息接入的第二网络入口的步骤,具体包括:提供用于实现键入信息 进行蓝牙匹配接入的第二网络入口。It should be noted that the step of providing a second network entry for implementing key-in information access according to the session joining path in this embodiment specifically includes: providing a second network for implementing key-in information for Bluetooth matching access Entrance.
容易理解的是,在一些场景下,用户之间不便于近距离沟通,比如在 大型商场或者广场等,用户如果分别位于不同的位置,一般难以很快找到 彼此,或者分饰不同的角色时会安排在不同的位置,因此,针对这些场景, 本申请可以提供其他接入分享会话的方式,比如直接通过蓝牙等各种近场 或远距离网络进行连接等。It is easy to understand that in some scenarios, it is not convenient for users to communicate at close range, such as in large shopping malls or squares. Arranged in different locations, therefore, for these scenarios, the present application can provide other ways of accessing the sharing session, such as connecting directly through various near-field or long-distance networks such as Bluetooth.
具体而言,本实施方式所述提供用于实现可跨设备扫描的短时效二维 码或长时效二维码进行接入的第一网络入口的步骤,还可以包括:通过发 起所述集群活动的第一/第二主机和/或参与所述集群活动的从机提供所述 短时效二维码或长时效二维码。Specifically, the step of providing a first network entry for implementing a cross-device scannable short-term QR code or a long-term QR code for access as described in this embodiment may further include: initiating the cluster activity by The first/second host and/or the slaves participating in the cluster activity provide the short-term QR code or the long-term QR code.
换而言之,本实施方式可以通过从机实现彼此之间的party活动分享, 方便用户操作。In other words, in this embodiment, party activities can be shared between each other through the slaves, which is convenient for users to operate.
值得一提的是,本实施方式所述通过发起所述集群活动的第一/第二主 机和/或参与所述集群活动的从机提供所述短时效二维码或长时效二维码 的步骤,具体可以包括如下:It is worth mentioning that in this embodiment, the first/second host that initiates the cluster activity and/or the slave that participates in the cluster activity provides the short-term QR code or the long-term QR code. The steps may specifically include the following:
判断是否为通过参与所述集群活动的从机提供所述短时效二维码或长 时效二维码;Determine whether the short-term two-dimensional code or the long-term two-dimensional code is provided by the slaves participating in the cluster activity;
若为通过参与所述集群活动的从机提供所述短时效二维码或长时效二 维码,判断当前第一/第二主机是否仍为发起所述集群活动的第一/第二主 机;If the short-term two-dimensional code or the long-term two-dimensional code is provided by the slaves participating in the cluster activity, it is judged whether the current first/second host is still the first/second host that initiated the cluster activity;
若当前第一/第二主机仍为发起所述集群活动的第一/第二主机,提供 所述短时效二维码或长时效二维码;若当前第一/第二主机不再为发起所述 集群活动的第一/第二主机,停止提供所述短时效二维码或长时效二维码。If the current first/second host is still the first/second host that initiated the cluster activity, provide the short-term QR code or long-term QR code; if the current first/second host is no longer the initiator The first/second host that is active in the cluster stops providing the short-term two-dimensional code or the long-term two-dimensional code.
容易理解的是,本实施方式在通过非第一/第二主机实现分享活动时, 如果为了避免权限等安全问题,可以通过判断是否相同第一/第二主机的方 式进行鉴定认证,即判断当前第一/第二主机是否为最初发起活动的第一/ 第二主机。It is easy to understand that in this embodiment, when sharing activities are implemented through non-first/second hosts, in order to avoid security issues such as permissions, authentication can be performed by judging whether the first/second hosts are the same, that is, to determine whether the current host is the same. Whether the first/second host is the first/second host that originally initiated the activity.
进一步而言,本实施方式所述若当前第一/第二主机不再为发起所述集 群活动的第一/第二主机,停止提供所述短时效二维码或长时效二维码的步 骤之后,还包括:提示向当前第一/第二主机请求更新短时效二维码或长时 效二维码,和/或,提供用于实现键入信息进行蓝牙匹配接入的第二网络入 口。Further, in this embodiment, if the current first/second host is no longer the first/second host that initiated the cluster activity, the step of stopping providing the short-term QR code or long-term QR code Afterwards, it also includes: prompting the current first/second host to request to update the short-term two-dimensional code or long-term two-dimensional code, and/or providing a second network entry for implementing key-in information for Bluetooth matching access.
容易理解的是,本实施方式在对第一/第二主机进行鉴定之后,可以对 网络入口作进一步的智能提醒,并对二维码进行更新。It is easy to understand that in this embodiment, after the first/second host is authenticated, further intelligent reminders can be made to the network entry, and the two-dimensional code can be updated.
具体而言,本实施方式所述根据所述会话加入路径提供用于实现可跨 设备扫描接入的第一网络入口的步骤,具体可以包括如下几种方式:Specifically, the step of providing a first network entry that can be scanned across devices according to the session join path described in this embodiment may specifically include the following ways:
方式一,提供WiFi网络作为所述第一网络入口,并设置或更新包括标 识SSID和密码的入网信息;Mode one, provide WiFi network as described first network entrance, and set or update the network access information including identification SSID and password;
或方式二,提供命令传输通道的服务端口为socket服务端,以作为所 述第一网络入口,并设置端口连接请求中携带socket客户端口,且所述 socket客户端口的端口号为预设的非公开端口号;Or mode 2, the service port that provides the command transmission channel is the socket server, which is used as the first network entry, and the port connection request is set to carry the socket client port, and the port number of the socket client port is a preset non- public port number;
或方式三,提供多媒体数据传输通道的服务端口作为所述第一网络入 口,以用于收发包括有移动终端的网络IP地址的服务信息。Or the third way, the service port of the multimedia data transmission channel is provided as the first network entrance, so as to send and receive service information including the network IP address of the mobile terminal.
需要补充说明的是,本实施方式还可以包括:通过所述集群活动进行 多媒体数据交互Party模式活动,其中,所述多媒体数据包括即时的音频 数据、视频数据、音视频数据。It should be supplemented that this embodiment may further include: performing multimedia data interactive Party mode activities through the cluster activities, wherein the multimedia data includes real-time audio data, video data, and audio and video data.
当然,除了进行音频数据、视频数据、音视频数据的分享之外,还可 以对其他资源数据、文件文档或者用户活动等进行分享,在此不作限定。Of course, in addition to sharing audio data, video data, and audio and video data, other resource data, file documents, or user activities can also be shared, which is not limited here.
请接着参阅图5,本申请还提供一种主机资源配置装置,作为其中一种 实施方式,其配置有处理器51,所述处理器51用于执行主机资源配置程序, 以实现包括如图1及其实施方式所述的主机资源配置方法。Referring next to FIG. 5 , the present application further provides a host resource configuration device, as one of the implementations, it is configured with a
所述处理器51用于检测第一主机是否提供服务资源;The
若检测到所述第一主机未提供服务资源,所述处理器51用于调度第二 主机,以通过所述第二主机提供与所述第一主机相同或相关的服务资源。If it is detected that the first host does not provide service resources, the
在本实施方式中,所述第一主机将包括所述第一主机和所述第二主机 的网络信息发送给网络连接的从机,以使得所述从机可根据所述网络信息 接入所述第一主机或第二主机获取服务资源。In this embodiment, the first host sends network information including the first host and the second host to a network-connected slave, so that the slave can access the network according to the network information. The first host or the second host obtains service resources.
具体而言,本实施方式所述第一主机将包括所述第一主机和所述第二 主机的网络信息发送给网络连接的从机之前,还可以包括:第一主机与第 二主机之间建立网络连接,以进行配对绑定。Specifically, in this embodiment, before the first host sends the network information including the first host and the second host to the network-connected slave, it may further include: a connection between the first host and the second host Establish a network connection for pairing bonding.
值得一提的是,本实施方式所述第一主机与第二主机之间建立网络连 接,以进行配对绑定,具体可以包括:It is worth mentioning that a network connection is established between the first host and the second host in this embodiment for pairing and binding, which may specifically include:
第一主机生成用于连接的验证密钥;the first host generates an authentication key for the connection;
将所述验证密钥发送给所述第二主机,以供所述第二主机使用所述验 证密钥建立网络连接。The verification key is sent to the second host for the second host to use the verification key to establish a network connection.
在具体的实施方式中,所述第一主机与第二主机之间建立网络连接, 还可以包括:第一主机获取所述第二主机通过网络发送的属于所述第二主 机的第二网络标识,以将属于第一主机的第一网络标识和所述第二网络标 识配置成所述网络信息。In a specific implementation manner, establishing a network connection between the first host and the second host may further include: the first host acquiring a second network identifier belonging to the second host sent by the second host through the network , to configure the first network identifier and the second network identifier belonging to the first host as the network information.
需要说明的是,本实施方式所述第一主机与第二主机之间建立网络连 接之后,还包括:第一主机将所述服务资源的信息表和/或数据内容发送给 第二主机,以使得所述第二主机根据所述信息表和/或数据内容提供相同或 相关的服务资源。It should be noted that, after the network connection is established between the first host and the second host in this embodiment, the method further includes: the first host sends the information table and/or data content of the service resource to the second host, so as to The second host is caused to provide the same or related service resources according to the information table and/or data content.
在本实施方式中,所述第一主机与第二主机之间建立网络连接之后, 还包括:第一主机获取网络连接的从机列表;将所述从机列表发送给所述 第二主机进行缓存。In this embodiment, after the network connection is established between the first host and the second host, the method further includes: the first host acquires a list of slaves connected to the network; and sending the list of slaves to the second host for processing cache.
需要补充说明的是,在另一个实施方式中,请参阅图3,第二主机向第 一主机发送探测请求;获取所述第一主机根据所述探测请求所返回的验证 密钥;根据所述验证密钥建立与所述第一主机的网络连接。It should be added that, in another embodiment, referring to FIG. 3 , the second host sends a probe request to the first host; obtains the verification key returned by the first host according to the probe request; The authentication key establishes a network connection with the first host.
进一步而言,本实施方式所述根据所述验证密钥建立与所述第一主机 的网络连接的之后,还包括:第二主机获取自身的第二网络标识;将所述 第二网络标识发送给所述第一主机,以供所述第一主机或其他从机接入。Further, after establishing the network connection with the first host according to the verification key in this embodiment, the method further includes: the second host obtains its own second network identifier; sending the second network identifier to the first host for access by the first host or other slaves.
下面将结合具体实施例对上述实施方式进行举例说明。The foregoing implementation manner will be illustrated below with reference to specific embodiments.
1.选定第一主机、第二主机,第一主机、第二主机相互绑定;第一主 机、第二主机二者优先配对,第一主机的无线网络设备根据探测请求帧生 成带有WP/WP2认证的PMK密钥并发送给第二主机;第二主机端以开放鉴权 方式与第一主机设备建立连接;连接建立之后,第二主机自动生成带有自 身标识的无线地址信息传送给第一主机;1. Select the first host and the second host, and the first host and the second host are bound to each other; the first host and the second host are paired preferentially, and the wireless network device of the first host generates a WP with WP according to the detection request frame. The PMK key authenticated by /WP2 is sent to the second host; the second host establishes a connection with the first host device in an open authentication mode; after the connection is established, the second host automatically generates wireless address information with its own identity and transmits it to the first host;
2.第一主机机作为主机,利用现有的分享共享方式将含有第一主机、 第二主机二者的无线入网标识分享出去,从机partyer选择加入;2. The first host computer is used as the host computer, and the wireless network access identifier containing the first host computer and the second host computer is shared by using the existing sharing and sharing method, and the slave partyer chooses to join;
3.由于从机中存在第一主机和第二主机的两个配对信息,一旦从机确 认加入即确认同意加入第二主机;第二主机再次接收到第一主机的配对信 息,选择加入,此时也默认以将所有从机列表缓存至第二主机端;3. Since there are two pairing information of the first host and the second host in the slave, once the slave confirms to join, it confirms that it agrees to join the second host; the second host receives the pairing information of the first host again, and chooses to join. It also defaults to cache all slave lists to the second host;
4.由此完成将主、副主机的无线配对信息植入到各从机中;4. From this, the wireless pairing information of the master and slave masters are implanted into each slave;
5.第一主机退出,第二主机直接发挥主机作用提供资源服务。5. The first host exits, and the second host directly plays the role of the host to provide resource services.
本实施方式基于WiFi直连的核心技术共享文件数据的方案。依靠主从 机的相互绑定,使得从机同时访问了两台主机,在优先的原则下已首次分 享者作为第一主机,而第二主机作为备选。在第一主机退出后,信号间自动 搜索,默认自动连接第二主机使得party活动连续地持续进行下去。从而 在不违背WiFi直连的技术前提下,实现主机资源的自动迁移。This embodiment is based on the solution of sharing file data based on the core technology of WiFi direct connection. Relying on the mutual binding of master and slave, the slave accesses two masters at the same time. Under the principle of priority, the first sharer is the first master, and the second master is the alternative. After the first host exits, the signals are automatically searched, and the second host is automatically connected by default so that the party activities continue continuously. Therefore, the automatic migration of host resources can be realized without violating the technical premise of WiFi direct connection.
请参阅图4,在party上当主机A因为异常而退出的时候,主机B会直 接上位,由此保证了party的延续性;主机A退出了,主机A宿主迁移的 时候,歌曲列表可以跟着直接迁移,当然还可以听到不一样的歌曲,即可 以听到主机B的歌曲,增加了播放的选择性。此外,本实施方式可以不限 于两个主机,还可以设置3个或更多个主机。Please refer to Figure 4. When host A quits due to an exception on the party, host B will directly take over, thus ensuring the continuity of the party; when host A quits and host A is migrated, the song list can be directly migrated. , of course, you can also hear different songs, that is, you can hear the songs of host B, which increases the selectivity of playback. Furthermore, the present embodiment may not be limited to two hosts, and three or more hosts may be provided.
具体而言,本实施方式资源配置装置可以具体指所述第一/第二主机, 具体实现可以为手机、平板电脑、笔记本电脑以及其他可穿戴设备。Specifically, the resource configuration apparatus in this embodiment may specifically refer to the first/second host, and may be specifically implemented as a mobile phone, a tablet computer, a notebook computer, and other wearable devices.
在具体工作过程中,所述处理器51用于设置用于加入集群活动的会话 分享模式;In the specific working process, the
所述处理器51用于根据所述会话分享模式生成会话加入路径;The
所述处理器51用于根据所述会话加入路径提供用于实现可跨设备扫描 接入的第一网络入口,和/或,根据所述会话加入路径提供用于实现键入信 息接入的第二网络入口,以进行会话通信连接。The
值得说明的是,本实施方式的集群活动,可以指的是多人语音共享, 比如卡拉OK等party活动,或者其他户外活动等。It should be noted that the cluster activity in this embodiment may refer to voice sharing among multiple people, such as party activities such as karaoke, or other outdoor activities.
在本实施方式中,所述会话分享模式,指的是需要实现与其他设备建 立连接,从而进行数据分享、活动分享等行为模式。In this embodiment, the session sharing mode refers to a behavioral mode that needs to establish a connection with other devices, thereby performing data sharing, activity sharing, and the like.
值得一提的是,本实施方式的会话加入路径,可以指的是通过网络、 端口、通信方式、物理连接等进行相互连接的途径。It is worth mentioning that the session joining path in this embodiment may refer to a path for connecting to each other through a network, a port, a communication method, a physical connection, or the like.
在本实施方式中,所述跨设备,一般而言指的是可以跨过第一/第二主 机,而在从机之间实现快速分享由第一/第二主机发起的分享活动。In this implementation manner, the cross-device generally means that the first/second host can be crossed, and the sharing activity initiated by the first/second host can be quickly shared between the slaves.
通过上述方式,本申请能够支持随时随地快速加入分享队列,融入 party活动的效果。Through the above method, the present application can support the rapid joining of the sharing queue anytime and anywhere, and integrate into the effect of party activities.
进一步而言,本实施方式所述处理器51用于根据所述会话加入路径提 供用于实现可跨设备扫描接入的第一网络入口,具体可以包括:所述处理 器51用于提供用于实现可跨设备扫描的短时效二维码或长时效二维码进行 接入的第一网络入口。Further, in this embodiment, the
本实施方式所述的短时效二维码,可以指的是维持几小时、几天或者 几周时间的有效期的二维码;相对地,所述长时效二维码,则可以指的是 相对于该短时效二维码而设置的有效期更长的二维码,比如可以是几天、 几周或者几个月,甚至永久有效等。The short-term two-dimensional code in this embodiment may refer to a two-dimensional code that maintains a validity period of several hours, days or weeks; relatively, the long-term two-dimensional code may refer to a relatively long-term two-dimensional code. A two-dimensional code with a longer validity period is set for the short-lived two-dimensional code, such as a few days, a few weeks, or a few months, or even a permanent validity.
需要说明的是,本实施方式所述处理器51用于根据所述会话加入路径 提供用于实现键入信息接入的第二网络入口,具体包括:所述处理器51用 于提供用于实现键入信息进行蓝牙匹配接入的第二网络入口。It should be noted that the
容易理解的是,在一些场景下,用户之间不便于近距离沟通,比如在 大型商场或者广场等,用户如果分别位于不同的位置,一般难以很快找到 彼此,或者分饰不同的角色时会安排在不同的位置,因此,针对这些场景, 本申请可以提供其他接入分享会话的方式,比如直接通过蓝牙等各种近场 或远距离网络进行连接等。It is easy to understand that in some scenarios, it is not convenient for users to communicate at close range, such as in large shopping malls or squares. Arranged in different locations, therefore, for these scenarios, the present application can provide other ways of accessing the sharing session, such as connecting directly through various near-field or long-distance networks such as Bluetooth.
具体而言,本实施方式所述处理器51用于提供用于实现可跨设备扫描 的短时效二维码或长时效二维码进行接入的第一网络入口,还可以包括: 所述处理器51用于通过发起所述集群活动的第一/第二主机和/或参与所述 集群活动的从机提供所述短时效二维码或长时效二维码。Specifically, the
换而言之,本实施方式可以通过从机实现彼此之间的party活动分享, 方便用户操作。In other words, in this embodiment, party activities can be shared between each other through the slaves, which is convenient for users to operate.
值得一提的是,本实施方式所述通过发起所述集群活动的第一/第二主 机和/或参与所述集群活动的从机提供所述短时效二维码或长时效二维码, 具体可以包括如下:It is worth mentioning that, in this embodiment, the short-term QR code or the long-term QR code is provided by the first/second host that initiates the cluster activity and/or the slave that participates in the cluster activity. Specifically, it can include the following:
所述处理器51用于判断是否为通过参与所述集群活动的从机提供所述 短时效二维码或长时效二维码;Described
若为通过参与所述集群活动的从机提供所述短时效二维码或长时效二 维码,所述处理器51用于判断当前第一/第二主机是否仍为发起所述集群 活动的第一/第二主机;If the short-term two-dimensional code or long-term two-dimensional code is provided for the slaves participating in the cluster activity, the
若当前第一/第二主机仍为发起所述集群活动的第一/第二主机,所述 处理器51用于提供所述短时效二维码或长时效二维码;若当前第一/第二 主机不再为发起所述集群活动的第一/第二主机,所述处理器51用于停止 提供所述短时效二维码或长时效二维码。If the current first/second host is still the first/second host that initiated the cluster activity, the
容易理解的是,本实施方式在通过非第一/第二主机实现分享活动时, 如果为了避免权限等安全问题,可以通过判断是否相同第一/第二主机的方 式进行鉴定认证,即判断当前第一/第二主机是否为最初发起活动的第一/ 第二主机。It is easy to understand that in this embodiment, when sharing activities are implemented through non-first/second hosts, in order to avoid security issues such as permissions, authentication can be performed by judging whether the first/second hosts are the same, that is, to determine whether the current host is the same. Whether the first/second host is the first/second host that originally initiated the activity.
进一步而言,本实施方式若当前第一/第二主机不再为发起所述集群活 动的第一/第二主机,停止提供所述短时效二维码或长时效二维码之后,所 述处理器51还用于提示向当前第一/第二主机请求更新短时效二维码或长 时效二维码,和/或,所述处理器51用于提供用于实现键入信息进行蓝牙 匹配接入的第二网络入口。Further, in this embodiment, if the current first/second host is no longer the first/second host that initiated the cluster activity, after stopping providing the short-term QR code or long-term QR code, the
容易理解的是,本实施方式在对第一/第二主机进行鉴定之后,可以对 网络入口作进一步的智能提醒,并对二维码进行更新。It is easy to understand that in this embodiment, after the first/second host is authenticated, further intelligent reminders can be made to the network entry, and the two-dimensional code can be updated.
具体而言,本实施方式所述处理器51用于根据所述会话加入路径提供 用于实现可跨设备扫描接入的第一网络入口,具体可以包括如下几种方式:Specifically, the
方式一,所述处理器51用于提供WiFi网络作为所述第一网络入口, 并设置或更新包括标识SSID和密码的入网信息;Mode 1, the
或方式二,所述处理器51用于提供命令传输通道的服务端口为socket 服务端,以作为所述第一网络入口,并设置端口连接请求中携带socket客 户端口,且所述socket客户端口的端口号为预设的非公开端口号;Or the second way, the service port used by the
或方式三,所述处理器51用于提供多媒体数据传输通道的服务端口作 为所述第一网络入口,以用于收发包括有移动终端的网络IP地址的服务信 息。Or mode 3, the
需要补充说明的是,本实施方式所述处理器51用于通过所述集群活动 进行多媒体数据交互Party模式活动,其中,所述多媒体数据包括即时的 音频数据、视频数据、音视频数据。It should be supplemented that the
当然,除了进行音频数据、视频数据、音视频数据的分享之外,还可 以对其他资源数据、文件文档或者用户活动等进行分享,在此不作限定。Of course, in addition to sharing audio data, video data, and audio and video data, other resource data, file documents, or user activities can also be shared, which is not limited here.
此外,本申请还可以提供一种计算机可读存储介质,其用于存储主机 资源配置程序,所述主机资源配置程序在被处理器执行时,以实现包括如 图1及其实施方式所述的主机资源配置方法。In addition, the present application can also provide a computer-readable storage medium for storing a host resource configuration program, when the host resource configuration program is executed by a processor, to achieve the configuration including the configuration described in FIG. 1 and its embodiments. Host resource configuration method.
本实施方式将结合具体应用例进行详细说明。This embodiment will be described in detail with reference to specific application examples.
本实施方式实现的主机资源配置方法可以包括如下步骤流程:The host resource configuration method implemented in this embodiment may include the following steps:
开始;start;
将本地网络设置成点对点模式,根据入网信息生成二维码并显示;Set the local network to point-to-point mode, and generate a QR code according to the network access information and display it;
在接收到终端发送的入驻请求后,建立对应连接;After receiving the entry request sent by the terminal, establish a corresponding connection;
接口连接后,终端向服务器发送服务信息,所述服务信息提供进行多 媒体数据交互服务;After the interface is connected, the terminal sends service information to the server, and the service information provides a multimedia data interaction service;
完成终端与服务器的通信连接;Complete the communication connection between the terminal and the server;
结束。Finish.
在上述实施方式中,其包括如下具体实现方案:In the above-mentioned embodiment, it includes the following specific implementation scheme:
其中,所述本地网络为WiFi网络,所述入网信息包括标识SSID和密 码PWD;和/或,所述提供命令传输通道的服务端口为socket服务端,所述 端口连接请求携带socket客户端口,所述socket客户端口的端口号是预 设的非公开端口号;和/或,所述服务信息包括:所述移动终端的网络IP 地址和提供多媒体数据传输通道的服务端口;Wherein, the local network is a WiFi network, and the network access information includes an identifier SSID and a password PWD; and/or, the service port providing the command transmission channel is a socket server, and the port connection request carries a socket client port, so The port number of the socket client port is a preset non-public port number; and/or the service information includes: the network IP address of the mobile terminal and the service port providing the multimedia data transmission channel;
或者,其中,在所述根据入网信息生成编码图形前,还包括:更新入 网信息;该操作具体包括;随机生成SSID和/或PWD,并相应替换原存储的 SSID和/或PWD;Or, wherein, before described generating the coded graphics according to the network access information, it also includes: updating the network access information; the operation specifically includes: randomly generating the SSID and/or PWD, and correspondingly replacing the original stored SSID and/or PWD;
或者,其中,根据所述入网信息,向所述多媒体播放器发送入网请求 并建立网络连接;向所述多媒体播放器发送端口连接请求,请求与其提供 命令传输通道的服务端口建立端口连接;成功建立端口连接后,向该服务 端口发送服务信息,所述服务信息提供进行多媒体数据交互的服务参数;Or, wherein, according to the network access information, a network access request is sent to the multimedia player and a network connection is established; a port connection request is sent to the multimedia player, and a port connection is requested to be established with the service port that provides the command transmission channel; successfully established After the port is connected, send service information to the service port, where the service information provides service parameters for multimedia data interaction;
或者,其中,在连接完成之后,服务端接收到二维码相关的提示不局 限与二维码的如编码配对,条形码形态等方式配对信息,服务端接收到提 示,人机交互点击是否加入,即可识别快速自主加入队列。Or, after the connection is completed, the server receives a prompt related to the two-dimensional code, which is not limited to pairing information with the two-dimensional code, such as code pairing, barcode form, etc., the server receives the prompt, and the human-computer interaction clicks whether to join, You can identify and join the queue quickly and autonomously.
此外,本实施方式针对不同的分享方式,其可以包括如下几种实施例。In addition, this implementation manner is directed to different sharing manners, which may include the following embodiments.
实施例Example
1.第一/第二主机创建队列,在已生成二维码的功能中添加分享功能, 将此二维码分享至所有参加party的从机partyer;1. The first/second host creates a queue, adds a sharing function to the function that has generated a QR code, and shares this QR code to all partyers participating in the party;
2.已存在共享播放器的partyer直接识别二维码进行加入,迅速开启 共享模式;针对未有安装的partyer,可以收到一个类似蓝牙配对或者WiFi 加入的提醒,选择接受提示,后台自动下载该应用,下载完成后自动加入 第一/第二主机,融入party;2. The partyer with existing shared player directly recognizes the QR code to join, and quickly turns on the sharing mode; for the partyer that has not been installed, you can receive a reminder similar to Bluetooth pairing or WiFi joining, choose to accept the reminder, and the background will automatically download the Application, automatically join the first/second host after the download is completed, and integrate into the party;
3.从机中途退出,二次回来,只要直接识别之前的二维码,随即加入 队列,附近的从机也可以借助打开的二维码进行扫描加入,为第一/第二主 机减轻来回切换的操作。3. The slave machine exits halfway and returns a second time. As long as the previous QR code is directly recognized, it will join the queue immediately. The nearby slaves can also scan and join with the opened QR code, which will ease the switching back and forth for the first/second host. operation.
实施例Example
开始;start;
第一/第二主机创建队列;The first/second host creates a queue;
二维码分享;QR code sharing;
从机加入;Join from the machine;
结束。Finish.
实施例Example
其用于针对应用程序APP进行区别分享的方式。It is used to differentiate the sharing method for the application APP.
实施例四Embodiment 4
本实施方式实现了从机对从机或者第一/第二主机的识别。This embodiment realizes the identification of the slave to the slave or the first/second master.
通过上述具体实施例,本申请实现如下技术效果:Through the above-mentioned specific embodiments, the present application achieves the following technical effects:
1.第一/第二主机确定的情况下,二维码分享,从机随时加入,方便快 捷,避免所有从机逐一去扫描第一/第二主机;1. When the first/second host is determined, the QR code is shared, and the slaves can join at any time, which is convenient and fast, and avoids all slaves to scan the first/second host one by one;
2.无论从机partyer是否存在相同应用,均不受影响,存在者直接识 别加入,也可以就近选择扫描第一/第二主机加入,减少了partyer的束缚 与限制;2. No matter whether the slave partyer has the same application or not, it will not be affected. The existing party directly recognizes and joins, and can also choose to scan the first/second host nearby to join, which reduces the constraints and restrictions of the partyer;
3.从机意外退出,二次加入不用“千里迢迢”去扫描第一/第二主机, 第一/第二主机二维码“永久有效”,一次分享可多次使用,比如可以在第 一/第二主机不变的情况下;3. The slave machine exits unexpectedly, and the second join does not need to scan the first/second host. The QR code of the first/second host is "permanently valid", and one share can be used multiple times. For example, it can be used in the first / When the second host remains unchanged;
4.不是只有第一/第二主机的二维码可以供从机使用扫描,从机也可以 扫描从机的二维码快速加入。4. Not only the QR code of the first/second host can be scanned by the slave, but the slave can also scan the QR code of the slave to join quickly.
需要说明的是,本申请所描述的方法实施方式至少可以部分地是机器 或计算机实现的。一些示例可以包括用指令编码的计算机可读存储介质或 机器可读存储介质,所述指令可用于配置电子设备以执行以上实施方式中 所述的方法。这些方法的实现可以包括代码,例如微码、汇编语言代码或 更高级别的语言代码等。这种代码可以包括用于执行各种方法的计算机可 读指令。该代码可以形成主机资源配置程序产品的一部分。该代码可以有 形地存储在一个或多个易失性、非暂时性或非易失性有形计算机可读介质 上,例如在执行期间或在其它时间。这些有形计算机可读存储介质的示例 可以包括但不限于硬盘、可移动磁盘、可移动光盘(例如,压缩磁盘和数字 视频盘)、磁带盒、存储卡或棒、随机存取存储器(random access memory, 简称RAM)和只读存储器(read only memory,简称ROM)等。It should be noted that, the method implementations described in this application may be implemented at least in part by machines or computers. Some examples may include a computer-readable storage medium or a machine-readable storage medium encoded with instructions that can be used to configure an electronic device to perform the methods described in the above embodiments. Implementations of these methods may include code, such as microcode, assembly language code, or higher level language code, and the like. Such code may include computer readable instructions for performing various methods. The code may form part of a host resource configurator product. The code may be tangibly stored on one or more volatile, non-transitory, or non-volatile tangible computer-readable media, such as during execution or at other times. Examples of such tangible computer-readable storage media may include, but are not limited to, hard disks, removable disks, removable optical disks (eg, compact disks and digital video disks), magnetic tape cartridges, memory cards or sticks, random access memory , referred to as RAM) and read only memory (read only memory, referred to as ROM) and so on.
以上所述,仅是本申请的较佳实施例而已,并非对本申请作任何形式 上的限制,虽然本申请已以较佳实施例揭露如上,然而并非用以限定本申 请,任何熟悉本专业的技术人员,在不脱离本申请技术方案范围内,当可利 用上述揭示的技术内容作出些许更动或修饰为等同变化的等效实施例,但 凡是未脱离本申请技术方案内容,依据本申请的技术实质对以上实施例所 作的任何简单修改、等同变化与修饰,均仍属于本申请技术方案的范围内。The above are only preferred embodiments of the present application, and are not intended to limit the present application in any form. Although the present application has been disclosed above with preferred embodiments, it is not intended to limit the present application. The technical personnel, without departing from the scope of the technical solution of the present application, can make some changes or modifications to equivalent examples of equivalent changes by using the technical content disclosed above, provided that the content of the technical solution of the present application is not departed from, according to the technical solution of the present application. Any simple modifications, equivalent changes and modifications made to the above embodiments by the technical essence still fall within the scope of the technical solutions of the present application.
Claims (11)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202010307435.6ACN111787538A (en) | 2020-04-17 | 2020-04-17 | Host resource configuration apparatus, method, and computer-readable storage medium |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202010307435.6ACN111787538A (en) | 2020-04-17 | 2020-04-17 | Host resource configuration apparatus, method, and computer-readable storage medium |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN111787538Atrue CN111787538A (en) | 2020-10-16 |
Family
ID=72753591
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202010307435.6APendingCN111787538A (en) | 2020-04-17 | 2020-04-17 | Host resource configuration apparatus, method, and computer-readable storage medium |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN111787538A (en) |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN112911559A (en)* | 2021-01-19 | 2021-06-04 | 北京塞宾科技有限公司 | Wireless data communication method, system, equipment and storage medium |
| CN115515204A (en)* | 2022-10-24 | 2022-12-23 | 绥中泰德尔自控设备有限公司 | Network access method of slave equipment and related device |
Citations (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN101031882A (en)* | 2004-06-08 | 2007-09-05 | 达尔特设备公司 | Architecture, Apparatus and Method for Device Group Recruitment and Content Reproduction for Universal Device Interoperability Platform |
| CN203455884U (en)* | 2013-09-04 | 2014-02-26 | 苏州元澄智能科技有限公司 | Access redundancy control system |
| CN103840961A (en)* | 2012-11-23 | 2014-06-04 | 景幂机械(上海)有限公司 | Dual-computer hot backup system |
| CN104679907A (en)* | 2015-03-24 | 2015-06-03 | 新余兴邦信息产业有限公司 | Realization method and system for high-availability and high-performance database cluster |
| US9594598B1 (en)* | 2015-06-12 | 2017-03-14 | Amazon Technologies, Inc. | Live migration for virtual computing resources utilizing network-based storage |
| CN110597664A (en)* | 2019-09-17 | 2019-12-20 | 深信服科技股份有限公司 | High-availability cluster resource deployment method, device and related components |
- 2020
- 2020-04-17CNCN202010307435.6Apatent/CN111787538A/enactivePending
Patent Citations (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN101031882A (en)* | 2004-06-08 | 2007-09-05 | 达尔特设备公司 | Architecture, Apparatus and Method for Device Group Recruitment and Content Reproduction for Universal Device Interoperability Platform |
| CN103840961A (en)* | 2012-11-23 | 2014-06-04 | 景幂机械(上海)有限公司 | Dual-computer hot backup system |
| CN203455884U (en)* | 2013-09-04 | 2014-02-26 | 苏州元澄智能科技有限公司 | Access redundancy control system |
| CN104679907A (en)* | 2015-03-24 | 2015-06-03 | 新余兴邦信息产业有限公司 | Realization method and system for high-availability and high-performance database cluster |
| US9594598B1 (en)* | 2015-06-12 | 2017-03-14 | Amazon Technologies, Inc. | Live migration for virtual computing resources utilizing network-based storage |
| CN110597664A (en)* | 2019-09-17 | 2019-12-20 | 深信服科技股份有限公司 | High-availability cluster resource deployment method, device and related components |
Cited By (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN112911559A (en)* | 2021-01-19 | 2021-06-04 | 北京塞宾科技有限公司 | Wireless data communication method, system, equipment and storage medium |
| CN112911559B (en)* | 2021-01-19 | 2023-01-17 | 北京塞宾科技有限公司 | Wireless data communication method, system, equipment and storage medium |
| CN115515204A (en)* | 2022-10-24 | 2022-12-23 | 绥中泰德尔自控设备有限公司 | Network access method of slave equipment and related device |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US20220361259A1 (en) | Method and apparatus for wi-fi connection using wi-fi protected setup in portable terminal | |
| US10200466B2 (en) | Mass re-formation of groups in a peer-to-peer network | |
| EP3864541B1 (en) | Progressive access to data and device functionality | |
| JP6219501B2 (en) | Access control for wireless docking | |
| JP6066538B1 (en) | Peer-based authentication | |
| US9769732B2 (en) | Wireless network connection establishment method and terminal device | |
| US9565708B2 (en) | Auto-connect in a peer-to-peer network | |
| CN107249174B (en) | Communication connection establishment method and terminal | |
| JP6293874B2 (en) | Wireless docking architecture | |
| US9774583B2 (en) | Providing secure seamless access to enterprise devices | |
| WO2013033999A1 (en) | Method and apparatus for mobile device point-to-point data transmission | |
| KR20110125695A (en) | Method and system for providing Wi-Fi service of Wi-Fi device | |
| WO2018090830A1 (en) | Method and apparatus allowing smart terminal device to access internet | |
| WO2016184267A1 (en) | Method, device, terminal and system for providing specified communication service | |
| CN104125485B (en) | A kind of user profile shared method, equipment and system | |
| KR20160099396A (en) | Using method for communication service and electronic device supporting the same | |
| US9883545B2 (en) | Apparatus and method for selecting channel in wireless communication system | |
| JP2016528753A (en) | Use and configuration of wireless docking environment | |
| US20190297119A1 (en) | Establishing direct secure connection between collaboration devices in a room or space | |
| US10133307B2 (en) | Dock for extending the utility of an electronic device | |
| WO2018233681A1 (en) | Terminal calling method and related equipment | |
| CN111787538A (en) | Host resource configuration apparatus, method, and computer-readable storage medium | |
| US10848969B2 (en) | Authentication based access to wireless devices | |
| CN108712280A (en) | A kind of management method of network function, device, storage medium and intelligent terminal | |
| WO2018205328A1 (en) | System and method for accessing wireless network by device |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination |