CN111711637A - A security system for improving network communication technology - Google Patents
A security system for improving network communication technologyDownload PDFInfo
- Publication number
- CN111711637A CN111711637ACN202010600311.7ACN202010600311ACN111711637ACN 111711637 ACN111711637 ACN 111711637ACN 202010600311 ACN202010600311 ACN 202010600311ACN 111711637 ACN111711637 ACN 111711637A
- Authority
- CN
- China
- Prior art keywords
- module
- security
- management module
- data
- network
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
- 230000006854communicationEffects0.000titleclaimsabstractdescription58
- 238000004891communicationMethods0.000titleclaimsabstractdescription56
- 238000005516engineering processMethods0.000titleclaimsabstractdescription16
- 238000001514detection methodMethods0.000claimsabstractdescription10
- 230000002155anti-virotic effectEffects0.000claimsabstractdescription7
- 230000002265preventionEffects0.000claimsabstractdescription6
- 238000002955isolationMethods0.000claimsabstractdescription4
- 238000007726management methodMethods0.000claimsdescription80
- 238000013500data storageMethods0.000claimsdescription11
- 238000012550auditMethods0.000claimsdescription10
- 238000007405data analysisMethods0.000claimsdescription10
- 238000013523data managementMethods0.000claimsdescription10
- 238000013475authorizationMethods0.000claimsdescription8
- 238000012544monitoring processMethods0.000claimsdescription8
- 230000001681protective effectEffects0.000claimsdescription6
- 238000004458analytical methodMethods0.000claimsdescription5
- 238000007619statistical methodMethods0.000claimsdescription4
- 238000000034methodMethods0.000description5
- 230000005540biological transmissionEffects0.000description4
- 241000700605VirusesSpecies0.000description2
- 230000009286beneficial effectEffects0.000description1
- 238000011161developmentMethods0.000description1
- 238000010586diagramMethods0.000description1
- 238000012986modificationMethods0.000description1
- 230000004048modificationEffects0.000description1
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/20—Network architectures or network communication protocols for network security for managing network security; network security policies in general
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/02—Network architectures or network communication protocols for network security for separating internal from external traffic, e.g. firewalls
- H04L63/0209—Architectural arrangements, e.g. perimeter networks or demilitarized zones
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1441—Countermeasures against malicious traffic
- H04L63/145—Countermeasures against malicious traffic the attack involving the propagation of malware through the network, e.g. viruses, trojans or worms
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Health & Medical Sciences (AREA)
- General Health & Medical Sciences (AREA)
- Virology (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
- Computer And Data Communications (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明涉及网络通讯技术领域,更具体为一种网络通讯技术的提升安全保障系统。The present invention relates to the technical field of network communication, and more particularly to an improved security guarantee system of network communication technology.
背景技术Background technique
网络是用物理链路将各个孤立的工作站或主机相连在一起,组成数据链路,从而达到资源共享和通信的目的。通信是人与人之间通过某种媒体进行的信息交流与传递。网络通信是通过网络将各个孤立的设备进行连接,通过信息交换实现人与人,人与计算机,计算机与计算机之间的通信。The network uses physical links to connect isolated workstations or hosts together to form data links, so as to achieve the purpose of resource sharing and communication. Communication is the exchange and transmission of information between people through a certain medium. Network communication is to connect various isolated devices through the network, and realize the communication between people, people and computers, and computers and computers through information exchange.
网络通信中最重要的就是网络通信协议。当今网络协议有很多,局域网中最常用的有三个网络协议:MICROSOFT的NETBEUI、NOVELL的IPX/SPX和TCP/IP协议。应根据需要来选择合适的网络协议。The most important thing in network communication is the network communication protocol. There are many network protocols today. There are three most commonly used network protocols in local area network: NETBEUI of MICROSOFT, IPX/SPX of NOVELL and TCP/IP protocol. The appropriate network protocol should be selected according to the needs.
通俗地说,网络协议就是网络之间沟通、交流的桥梁,只有相同网络协议的计算机才能进行信息的沟通与交流。这就好比人与人之间交流所使用的各种语言一样,只有使用相同语言才能正常、顺利地进行交流。从专业角度定义,网络协议是计算机在网络中实现通信时必须遵守的约定,也就是通信协议。主要是对信息传输的速率、传输代码、代码结构、传输控制步骤、出错控制等作出规定并制定出标准。In layman's terms, a network protocol is a bridge for communication and exchange between networks. Only computers with the same network protocol can communicate and exchange information. This is like the various languages used for communication between people. Only by using the same language can we communicate normally and smoothly. From a professional point of view, a network protocol is a contract that a computer must abide by when implementing communication in a network, that is, a communication protocol. It mainly stipulates and formulates standards for the rate of information transmission, transmission code, code structure, transmission control steps, error control, etc.
目前,近年来,计算机技术和网络技术高速发展计算机已经成为人们日常工作和生活中必不可少的工具,随着科技的发展,计算机通过网络连接后,在使用的过程中存在一定的安全隐患,各种蹭网软件日渐增多、网络信息被窃取、网络病毒的传播等都使得区域网的安全性得不到保证。因此,需要提供一种新的技术方案给予解决。At present, in recent years, with the rapid development of computer technology and network technology, computers have become an indispensable tool in people's daily work and life. The increasing number of various network rubbing software, the theft of network information, and the spread of network viruses all make the security of the local area network not guaranteed. Therefore, it is necessary to provide a new technical solution to solve it.
发明内容SUMMARY OF THE INVENTION
本发明的目的在于提供一种网络通讯技术的提升安全保障系统,解决了现有技术中计算机通过网络连接后,在使用的过程中存在一定的安全隐患,各种蹭网软件日渐增多、网络信息被窃取、网络病毒的传播等都使得区域网的安全性得不到保证的问题。The purpose of the present invention is to provide a security system for improving network communication technology, which solves the problems of certain security risks in the process of using the computer after the computer is connected through the network in the prior art, the increasing number of various network rubbing software, the increasing number of network information Theft, the spread of network viruses, etc. all make the security of the local area network not guaranteed.
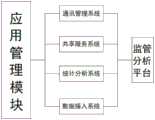
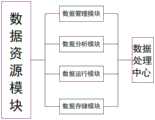
为实现上述目的,本发明提供如下技术方案:一种网络通讯技术的提升安全保障系统,包括:网络通讯系统,所述网络通讯系统中包括标准规范体系和安全保障系统,所述标准规范体系和安全保障系统中包括应用管理模块、平台管理模块、数据资源模块、基础设施模块和设备管理模块,所述安全保障系统内包括网络基础设施、应用与数据防护模块、系统风险管理模块,所述网络基础设施包括防火墙、网络密码机、防病毒网关、入侵检测系统和综合安全网关,所述应用与数据防护模块内包括入侵防护系统、安全隔离网闸和安全接入网关,所述入侵防护系统与入侵检测系统之间相连接,所述安全接入网关与综合安全网关之间相连接,所述系统风险管理模块内设有安全管理系统,所述安全管理系统内包括内网安全管理模块、安全审计管理模块、文件保密管理模块和应用监控管理模块,所述应用管理模块内设有通讯管理模块、共享服务系统、统计分析系统和数据接入系统,所述通讯管理模块、共享服务系统、统计分析系统和数据接入系统与监管分析平台之间相连接,所述平台管理模块内包括用户管理模块和服务管理模块,所述用户管理模块包括用户认证模块、用户授权模块、用户控管模块和用户审计模块,所述服务管理模块内部包括存储服务模块、日志服务模块、监控服务模块、配置服务模块和认证服务模块,所述认证服务模块与用户认证模块和用户授权模块相连接,所述基础设施模块内包括软件设施、资源库和硬件设置,所述数据资源模块内包括数据管理模块、数据分析模块、数据运行模块和数据存储模块,所述数据管理模块、数据分析模块、数据运行模块和数据存储模块与数据处理中心之间相连接,所述数据管理模块、数据分析模块、数据运行模块和数据存储模块与资源库之间相连接。In order to achieve the above purpose, the present invention provides the following technical solutions: a security system for improving network communication technology, comprising: a network communication system, wherein the network communication system includes a standard specification system and a security guarantee system, and the standard specification system and The security assurance system includes an application management module, a platform management module, a data resource module, an infrastructure module and a device management module, and the security assurance system includes a network infrastructure, an application and data protection module, and a system risk management module. The infrastructure includes firewalls, network encryption machines, antivirus gateways, intrusion detection systems, and comprehensive security gateways. The application and data protection modules include intrusion prevention systems, security isolation gatekeepers, and security access gateways. The intrusion detection systems are connected, the security access gateway is connected with the integrated security gateway, the system risk management module is provided with a security management system, and the security management system includes an intranet security management module, a security Audit management module, file security management module and application monitoring management module, the application management module is provided with a communication management module, a shared service system, a statistical analysis system and a data access system, the communication management module, the shared service system, the statistical The analysis system and the data access system are connected with the supervision and analysis platform, the platform management module includes a user management module and a service management module, and the user management module includes a user authentication module, a user authorization module, a user control module and The user audit module, the service management module includes a storage service module, a log service module, a monitoring service module, a configuration service module and an authentication service module, and the authentication service module is connected with the user authentication module and the user authorization module. The facility module includes software facilities, resource libraries and hardware settings, the data resource module includes a data management module, a data analysis module, a data operation module and a data storage module, the data management module, data analysis module, data operation module and The data storage module is connected with the data processing center, and the data management module, the data analysis module, the data operation module and the data storage module are connected with the resource library.
作为本发明的一种优选实施方式,所述软件设施包括操作系统、数据库和地理信息系统。As a preferred embodiment of the present invention, the software facility includes an operating system, a database and a geographic information system.
作为本发明的一种优选实施方式,所述资源库内包括计算资源、存储资源和网络资源,所述资源库通过网络与云端相连接,所述数据库与存储资源之间相连接。As a preferred embodiment of the present invention, the resource library includes computing resources, storage resources and network resources, the resource library is connected to the cloud through a network, and the database is connected to the storage resources.
作为本发明的一种优选实施方式,所述硬件设置包括服务器、存储设备和网络设备,所述操作系统与服务器和网络设备相连接。As a preferred embodiment of the present invention, the hardware setup includes a server, a storage device and a network device, and the operating system is connected to the server and the network device.
作为本发明的一种优选实施方式,所述存储设备包括硬件存和云端存储。As a preferred embodiment of the present invention, the storage device includes hardware storage and cloud storage.
作为本发明的一种优选实施方式,所述设备管理模块内包括门户网站、电脑终端、移动设备和扫描设备,所述移动设备可以是收集、平板电脑或个人终端中的一种,所述门户网站、电脑终端、移动设备和扫描设备均与用户全体相连接。As a preferred embodiment of the present invention, the device management module includes a portal website, a computer terminal, a mobile device and a scanning device, and the mobile device may be one of a collection, tablet computer or personal terminal, and the portal Websites, computer terminals, mobile devices and scanning devices are all connected to the user population.
作为本发明的一种优选实施方式,所述防护墙可以是强五防火墙、超五防护墙或精五防火墙中的一种,所述安全接入网关包括运营商安全接入网关、企业级安全接入网关和SMB安全接入网关中的一种。As a preferred embodiment of the present invention, the protective wall may be one of a strong five firewall, a super five protective wall or a fine five firewall, and the security access gateway includes an operator security access gateway, an enterprise-level security One of Access Gateway and SMB Secure Access Gateway.
与现有技术相比,本发明的有益效果如下:Compared with the prior art, the beneficial effects of the present invention are as follows:
(1)、本发明在网络通讯系统中添加了标准规范体系和安全保障系统,以增加了信息交流中的安全性,同时规范用户操作,使用户文明使用网络通讯系统。(1) The present invention adds a standard specification system and a security guarantee system to the network communication system to increase the security in information exchange, and at the same time standardize user operations, so that users can use the network communication system in a civilized manner.
(2)、本发明在安全保障系统的网络基础设施中设置防火墙、网络密码机、防病毒网关、入侵检测系统和综合安全网关,以提高网络通讯时的安全性,同时设置应用与数据防护模块和系统风险管理模块,增加了网络基础设施的操作性。(2), the present invention sets firewalls, network ciphers, antivirus gateways, intrusion detection systems and comprehensive security gateways in the network infrastructure of the security guarantee system to improve the security during network communication, and sets application and data protection modules simultaneously and system risk management module, which increases the operability of the network infrastructure.
(3)、本发明的标准规范体系中设置应用管理模块、平台管理模块、数据资源模块、基础设施模块和设备管理模块,其中包括了大部分的网络通讯技术中的操作规范,以提高网络通讯中的安全性和规范性。(3), set application management module, platform management module, data resource module, infrastructure module and equipment management module in the standard specification system of the present invention, which includes most of the operation specifications in the network communication technology, to improve network communication security and compliance in .
附图说明Description of drawings
图1为本发明整体流程示意图;Fig. 1 is the overall flow schematic diagram of the present invention;
图2为本发明安全保障系统流程示意图;Fig. 2 is the schematic flow chart of the safety guarantee system of the present invention;
图3为本发明应用管理模块流程示意图;3 is a schematic flowchart of an application management module of the present invention;
图4为本发明平台管理模块流程示意图;4 is a schematic flow chart of the platform management module of the present invention;
图5为本发明数据资源模块流程示意图;Fig. 5 is the schematic flow chart of the data resource module of the present invention;
图6为本发明基础设施模块流程示意图;Fig. 6 is the schematic flow chart of the infrastructure module of the present invention;
图7为本发明设备管理模块流程示意图。FIG. 7 is a schematic flowchart of a device management module of the present invention.
具体实施方式Detailed ways
下面将结合本发明实施例中的附图,对本发明实施例中的技术方案进行清楚、完整地描述,显然,所描述的实施例仅仅是本发明一部分实施例,而不是全部的实施例。基于本发明中的实施例,本领域普通技术人员在没有做出创造性劳动前提下所获得的所有其他实施例,都属于本发明保护的范围。The technical solutions in the embodiments of the present invention will be clearly and completely described below with reference to the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are only a part of the embodiments of the present invention, but not all of the embodiments. Based on the embodiments of the present invention, all other embodiments obtained by those of ordinary skill in the art without creative efforts shall fall within the protection scope of the present invention.
请参阅图1-7,本发明提供一种技术方案:一种网络通讯技术的提升安全保障系统,包括:网络通讯系统,所述网络通讯系统中包括标准规范体系和安全保障系统,在网络通讯系统中添加了标准规范体系和安全保障系统,以增加了信息交流中的安全性,同时规范用户操作,使用户文明使用网络通讯系统,标准规范体系和安全保障系统中包括应用管理模块、平台管理模块、数据资源模块、基础设施模块和设备管理模块,安全保障系统内包括网络基础设施、应用与数据防护模块、系统风险管理模块,网络基础设施包括防火墙、网络密码机、防病毒网关、入侵检测系统和综合安全网关,在安全保障系统的网络基础设置中设置防火墙、网络密码机、防病毒网关、入侵检测系统和综合安全网关,增加了网络通讯过程中的安全性,应用与数据防护模块内包括入侵防护系统、安全隔离网闸和安全接入网关,入侵防护系统与入侵检测系统之间相连接,安全接入网关与综合安全网关之间相连接,系统风险管理模块内设有安全管理系统,安全管理系统内包括内网安全管理模块、安全审计管理模块、文件保密管理模块和应用监控管理模块,系统风险管理模块中设置的安全审计管理模块、文件保密管理模块和应用监控管理模块,可以有效的对网络通讯中的数据进行监控,保证了数据的安全性,应用管理模块内设有通讯管理模块、共享服务系统、统计分析系统和数据接入系统,通讯管理模块、共享服务系统、统计分析系统和数据接入系统与监管分析平台之间相连接,平台管理模块内包括用户管理模块和服务管理模块,用户管理模块包括用户认证模块、用户授权模块、用户控管模块和用户审计模块,服务管理模块内部包括存储服务模块、日志服务模块、监控服务模块、配置服务模块和认证服务模块,认证服务模块与用户认证模块和用户授权模块相连接,平台管理模块中的用户管理模块内设置户认证模块、用户授权模块、用户控管模块和用户审计模块,严格控制用户的通讯操作规范,以保证用户信息的有效性和安全性,基础设施模块内包括软件设施、资源库和硬件设置,数据资源模块内包括数据管理模块、数据分析模块、数据运行模块和数据存储模块,数据管理模块、数据分析模块、数据运行模块和数据存储模块与数据处理中心之间相连接,数据管理模块、数据分析模块、数据运行模块和数据存储模块与资源库之间相连接,通过数据管理模块、数据分析模块、数据运行模块和数据存储模块对通讯中的数据流进行分析和管理,以保证网络通讯过程中的流畅性。Please refer to FIGS. 1-7 , the present invention provides a technical solution: an improved security guarantee system for network communication technology, including: a network communication system, wherein the network communication system includes a standard specification system and a security guarantee system. A standard specification system and a security assurance system are added to the system to increase the security in information exchange, and at the same time standardize user operations to enable users to use the network communication system in a civilized manner. The standard specification system and security assurance system include application management modules and platform management. module, data resource module, infrastructure module and equipment management module, the security system includes network infrastructure, application and data protection module, system risk management module, network infrastructure includes firewall, network encryption machine, anti-virus gateway, intrusion detection System and integrated security gateway, set firewall, network encryption machine, anti-virus gateway, intrusion detection system and integrated security gateway in the network infrastructure of the security assurance system, which increases the security in the process of network communication. Including intrusion prevention system, security isolation gatekeeper and security access gateway, connection between intrusion prevention system and intrusion detection system, connection between security access gateway and comprehensive security gateway, system risk management module with security management system , the security management system includes an intranet security management module, a security audit management module, a file security management module and an application monitoring management module, and the security audit management module, file security management module and application monitoring management module set in the system risk management module can be Effectively monitor the data in the network communication to ensure the security of the data, the application management module is equipped with a communication management module, a shared service system, a statistical analysis system and a data access system, a communication management module, a shared service system, and a statistical The analysis system and the data access system are connected with the supervision and analysis platform. The platform management module includes a user management module and a service management module. The user management module includes a user authentication module, a user authorization module, a user control module and a user audit module. The service management module includes a storage service module, a log service module, a monitoring service module, a configuration service module and an authentication service module. The authentication service module is connected with the user authentication module and the user authorization module, and the user management module in the platform management module sets up user accounts. The authentication module, user authorization module, user control module and user audit module strictly control the user's communication operation specifications to ensure the validity and security of user information. The infrastructure module includes software facilities, resource libraries and hardware settings, data The resource module includes a data management module, a data analysis module, a data operation module and a data storage module. The data management module, the data analysis module, the data operation module and the data storage module are connected with the data processing center. The module, data operation module and data storage module are connected with the resource library, and the data flow in the communication is analyzed and managed through the data management module, data analysis module, data operation module and data storage module to ensure the network communication process. of fluency.
进一步改进地,如图6所示:所述软件设施包括操作系统、数据库和地理信息系统,软件设施包括的操作系统方便用户操作,且数据库用于存储数据,且地理信息系统用于定位。Further improved, as shown in FIG. 6 : the software facility includes an operating system, a database and a geographic information system, the operating system included in the software facility is convenient for users to operate, the database is used for storing data, and the geographic information system is used for positioning.
进一步改进地,如图6所示:所述资源库内包括计算资源、存储资源和网络资源,所述资源库通过网络与云端相连接,所述数据库与存储资源之间相连接,资源库的中各种资源方便数据的查找比对。Further improved, as shown in Figure 6: the resource library includes computing resources, storage resources and network resources, the resource library is connected with the cloud through the network, the database is connected with the storage resources, and the resource library is connected to the cloud. A variety of resources are available to facilitate data search and comparison.
进一步改进地,如图6所示:所述存储设备包括硬件存和云端存储,多种存储方式增加了数据的安全性。Further improved, as shown in FIG. 6 , the storage device includes hardware storage and cloud storage, and multiple storage methods increase the security of data.
进一步改进地,如图7所示:所述设备管理模块内包括门户网站、电脑终端、移动设备和扫描设备,所述移动设备可以是收集、平板电脑或个人终端中的一种,所述门户网站、电脑终端、移动设备和扫描设备均与用户全体相连接。Further improved, as shown in Figure 7: the device management module includes a portal website, a computer terminal, a mobile device and a scanning device, and the mobile device can be one of a collection, a tablet computer or a personal terminal, and the portal Websites, computer terminals, mobile devices and scanning devices are all connected to the user population.
进一步改进地,如图2所示:所述防护墙可以是强五防火墙、超五防护墙或精五防火墙中的一种,所述安全接入网关包括运营商安全接入网关、企业级安全接入网关和SMB安全接入网关中的一种。Further improved, as shown in FIG. 2: the protective wall can be one of a strong five firewall, a super five protective wall or a fine five firewall, and the security access gateway includes an operator security access gateway, an enterprise-level security One of Access Gateway and SMB Secure Access Gateway.
本发明在网络通讯系统中添加了标准规范体系和安全保障系统,以增加了信息交流中的安全性,同时规范用户操作,使用户文明使用网络通讯系统,在安全保障系统的网络基础设置中设置防火墙、网络密码机、防病毒网关、入侵检测系统和综合安全网关,增加了网络通讯过程中的安全性,系统风险管理模块中设置的安全审计管理模块、文件保密管理模块和应用监控管理模块,可以有效的对网络通讯中的数据进行监控,保证了数据的安全性,平台管理模块中的用户管理模块内设置户认证模块、用户授权模块、用户控管模块和用户审计模块,严格控制用户的通讯操作规范,以保证用户信息的有效性和安全性,通过数据管理模块、数据分析模块、数据运行模块和数据存储模块对通讯中的数据流进行分析和管理,以保证网络通讯过程中的流畅性。The present invention adds a standard specification system and a security guarantee system to the network communication system, so as to increase the security in information exchange, and at the same time regulate user operations, so that users can use the network communication system in a civilized manner. Firewall, network encryption machine, antivirus gateway, intrusion detection system and comprehensive security gateway increase the security in the process of network communication. The security audit management module, file security management module and application monitoring management module set in the system risk management module, It can effectively monitor the data in the network communication and ensure the security of the data. The user management module in the platform management module is equipped with a user authentication module, a user authorization module, a user control module and a user audit module to strictly control the user's Communication operation specification to ensure the validity and security of user information, analyze and manage the data flow in the communication through the data management module, data analysis module, data operation module and data storage module to ensure the smoothness of the network communication process sex.
最后应说明的是:以上所述仅为本发明的优选实施例而已,并不用于限制本发明,尽管参照前述实施例对本发明进行了详细的说明,对于本领域的技术人员来说,其依然可以对前述各实施例所记载的技术方案进行修改,或者对其中部分技术特征进行等同替换。凡在本发明的精神和原则之内,所作的任何修改、等同替换、改进等,均应包含在本发明的保护范围之内。Finally, it should be noted that the above are only preferred embodiments of the present invention, and are not intended to limit the present invention. Although the present invention has been described in detail with reference to the foregoing embodiments, for those skilled in the art, it is still The technical solutions described in the foregoing embodiments may be modified, or some technical features thereof may be equivalently replaced. Any modification, equivalent replacement, improvement, etc. made within the spirit and principle of the present invention shall be included within the protection scope of the present invention.
Claims (7)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202010600311.7ACN111711637A (en) | 2020-06-28 | 2020-06-28 | A security system for improving network communication technology |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202010600311.7ACN111711637A (en) | 2020-06-28 | 2020-06-28 | A security system for improving network communication technology |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN111711637Atrue CN111711637A (en) | 2020-09-25 |
Family
ID=72544215
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202010600311.7APendingCN111711637A (en) | 2020-06-28 | 2020-06-28 | A security system for improving network communication technology |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN111711637A (en) |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN112565256A (en)* | 2020-12-05 | 2021-03-26 | 星极实业(深圳)有限公司 | Industrial control system intrusion detection system capable of intercepting and alarming in real time |
| CN113420084A (en)* | 2021-06-07 | 2021-09-21 | 广东辰宜信息科技有限公司 | Block chain system |
Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2007124206A2 (en)* | 2006-03-03 | 2007-11-01 | Reflex Security, Inc. | System and method for securing information in a virtual computing environment |
| US20090106234A1 (en)* | 2007-09-07 | 2009-04-23 | Alexander Siedlecki | Apparatus and methods for web marketing tools and digital archives - web portal advertising arts |
| CN206650691U (en)* | 2017-03-08 | 2017-11-17 | 北京中核瑞思科技有限公司 | A kind of Network Security Device |
| CN108600178A (en)* | 2018-03-28 | 2018-09-28 | 深圳市银之杰科技股份有限公司 | A kind of method for protecting and system, reference platform of collage-credit data |
- 2020
- 2020-06-28CNCN202010600311.7Apatent/CN111711637A/enactivePending
Patent Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2007124206A2 (en)* | 2006-03-03 | 2007-11-01 | Reflex Security, Inc. | System and method for securing information in a virtual computing environment |
| US20090106234A1 (en)* | 2007-09-07 | 2009-04-23 | Alexander Siedlecki | Apparatus and methods for web marketing tools and digital archives - web portal advertising arts |
| CN206650691U (en)* | 2017-03-08 | 2017-11-17 | 北京中核瑞思科技有限公司 | A kind of Network Security Device |
| CN108600178A (en)* | 2018-03-28 | 2018-09-28 | 深圳市银之杰科技股份有限公司 | A kind of method for protecting and system, reference platform of collage-credit data |
Non-Patent Citations (4)
| Title |
|---|
| 孙亮等: "基于STK卡的移动警务安全保障系统研究", 《微计算机信息》* |
| 张微微: "高职院校授权认证管理系统研究与设计", 《软件导刊》* |
| 潘耘等: "高校财会信息安全保障体系的研究", 《实验室研究与探索》* |
| 董煜等: "基于专网的移动警务安全保障系统设计与研究", 《计算机工程与设计》* |
Cited By (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN112565256A (en)* | 2020-12-05 | 2021-03-26 | 星极实业(深圳)有限公司 | Industrial control system intrusion detection system capable of intercepting and alarming in real time |
| CN113420084A (en)* | 2021-06-07 | 2021-09-21 | 广东辰宜信息科技有限公司 | Block chain system |
| CN113420084B (en)* | 2021-06-07 | 2023-09-26 | 广东辰宜信息科技有限公司 | Block chain system |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US20220368689A1 (en) | Integrated identity provider | |
| US10972461B2 (en) | Device aware network communication management | |
| EP2852913B1 (en) | Method and apparatus for determining malicious program | |
| CN113536258A (en) | Terminal access control method and device, storage medium and electronic equipment | |
| US10313386B1 (en) | Systems and methods for assessing security risks of users of computer networks of organizations | |
| US11140142B2 (en) | Method and system for authentication | |
| US8677446B2 (en) | Centrally managed impersonation | |
| WO2022257226A1 (en) | Cyberspace mapping-based honeypot recognition method and apparatus, device, and medium | |
| CN114024764A (en) | Monitoring method, monitoring system, equipment and storage medium for abnormal access of database | |
| CN111711637A (en) | A security system for improving network communication technology | |
| CN116956083A (en) | Data processing methods and devices | |
| CN106326736A (en) | Data processing method and system | |
| CN107528820A (en) | For the encipher-decipher method of application program, device and method for auditing safely and platform | |
| CN105007269B (en) | A kind of restoration methods of user cipher | |
| TW201911101A (en) | Server and firewall rule management therefof | |
| CN114760083B (en) | Method, device and storage medium for issuing attack detection file | |
| CN110955890A (en) | Method and device for detecting malicious batch access behaviors and computer storage medium | |
| JP2024107176A (en) | Analytical device, analytical method, and analytical program | |
| CN104753774A (en) | A Distributed Enterprise Integrated Access Gateway | |
| KR102508418B1 (en) | Method and system for providing in-house security management solution | |
| CN115396142A (en) | Information access method, device, computer equipment and medium based on zero trust | |
| CN118802149A (en) | Access processing method and device based on zero-trust network, electronic device, and medium | |
| CN111131152B (en) | Automatic verification method and system for cross-platform remote login protection system | |
| CN114615055A (en) | Access request processing method, data uploading method and device | |
| Liu et al. | MQueez: Specification-Driven Fuzzing for MQTT Broker (Registered Report) |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| RJ01 | Rejection of invention patent application after publication | Application publication date:20200925 | |
| RJ01 | Rejection of invention patent application after publication |