CN111444511A - Safety protection method and system for vehicle-mounted system - Google Patents
Safety protection method and system for vehicle-mounted systemDownload PDFInfo
- Publication number
- CN111444511A CN111444511ACN201811639417.7ACN201811639417ACN111444511ACN 111444511 ACN111444511 ACN 111444511ACN 201811639417 ACN201811639417 ACN 201811639417ACN 111444511 ACN111444511 ACN 111444511A
- Authority
- CN
- China
- Prior art keywords
- vehicle
- defense
- vulnerability
- strategy
- terminal
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/57—Certifying or maintaining trusted computer platforms, e.g. secure boots or power-downs, version controls, system software checks, secure updates or assessing vulnerabilities
- G06F21/577—Assessing vulnerabilities and evaluating computer system security
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/55—Detecting local intrusion or implementing counter-measures
- G06F21/56—Computer malware detection or handling, e.g. anti-virus arrangements
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Hardware Design (AREA)
- General Engineering & Computer Science (AREA)
- Software Systems (AREA)
- Theoretical Computer Science (AREA)
- General Physics & Mathematics (AREA)
- Physics & Mathematics (AREA)
- Virology (AREA)
- Health & Medical Sciences (AREA)
- General Health & Medical Sciences (AREA)
- Computing Systems (AREA)
- Traffic Control Systems (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本发明涉及车辆安全技术领域,具体涉及一种车载系统的安全防护方法及系统。The invention relates to the technical field of vehicle safety, in particular to a safety protection method and system for a vehicle-mounted system.
背景技术Background technique
随着科技及社会的不断发展,各类智能化、自动化车辆的出现极大方便了人们的工作与生活,但同时也催生了许多针对车辆的安全威胁。例如,车辆中的可编程化或可远程控制化的车载系统为非法入侵者提供了新的入侵渠道,从而对人们的财产及生命安全造成了极大的威胁。With the continuous development of technology and society, the emergence of various types of intelligent and automated vehicles has greatly facilitated people's work and life, but at the same time, it has also spawned many security threats to vehicles. For example, the programmable or remotely controllable in-vehicle systems in vehicles provide new intrusion channels for illegal intruders, thus posing a great threat to people's property and life.
为保障车载系统的正常运行,目前通常采用在车机终端部署热补丁等单一的防护措施来实现对车载系统的防护。然而,仅从车机终端一侧对车载系统进行单点防护,无法实现对车载系统的高效完备地防护,防护效果差。In order to ensure the normal operation of the in-vehicle system, a single protection measure such as deploying a hot patch at the in-vehicle terminal is usually adopted to protect the in-vehicle system. However, only single-point protection for the vehicle-mounted system from the side of the vehicle-machine terminal cannot achieve efficient and complete protection of the vehicle-mounted system, and the protection effect is poor.
发明内容SUMMARY OF THE INVENTION
鉴于上述问题,提出了本发明以便提供一种克服上述问题或者至少部分地解决上述问题的车载系统的安全防护方法及系统。In view of the above problems, the present invention is proposed in order to provide a safety protection method and system for an in-vehicle system that overcomes the above problems or at least partially solves the above problems.
根据本发明的一个方面,提供了一种车载系统的安全防护方法,包括:According to one aspect of the present invention, a safety protection method for a vehicle-mounted system is provided, comprising:
安全防护服务端根据获取的漏洞信息生成相应的车机防御策略,并将生成的车机防御策略传递至车辆厂商端;The security protection server generates the corresponding vehicle defense strategy according to the obtained vulnerability information, and transmits the generated vehicle defense strategy to the vehicle manufacturer;
车辆厂商端根据预设的下发规则,为车机终端下发相对应的车机防御策略;The vehicle manufacturer sends the corresponding vehicle defense strategy to the vehicle terminal according to the preset distribution rules;
车机终端利用接收到的车机防御策略进行安全防御。The vehicle-machine terminal uses the received vehicle-machine defense strategy for security defense.
根据本发明的另一方面,提供了一种车载系统的安全防护系统,包括:According to another aspect of the present invention, a safety protection system for a vehicle-mounted system is provided, comprising:
安全防护服务端,适于根据获取的漏洞信息生成相应的车机防御策略,并将生成的车机防御策略传递至车辆厂商端;The security protection server is suitable for generating corresponding vehicle and vehicle defense strategies according to the obtained vulnerability information, and transmitting the generated vehicle and vehicle defense strategies to the vehicle manufacturer;
车辆厂商端,适于根据预设的下发规则,为车机终端下发相对应的车机防御策略;The vehicle manufacturer side is suitable for issuing the corresponding vehicle defense strategy to the vehicle terminal according to the preset distribution rules;
车机终端,适于利用接收到的车机防御策略进行安全防御。The vehicle-machine terminal is suitable for security defense by using the received vehicle-machine defense strategy.
根据本发明的又一方面,提供了一种计算设备,包括:处理器、存储器、通信接口和通信总线,所述处理器、所述存储器和所述通信接口通过所述通信总线完成相互间的通信;According to yet another aspect of the present invention, a computing device is provided, comprising: a processor, a memory, a communication interface, and a communication bus, and the processor, the memory, and the communication interface complete mutual communication through the communication bus. communication;
所述存储器用于存放至少一可执行指令,所述可执行指令使所述处理器执行上述车载系统的安全防护方法对应的操作。The memory is used for storing at least one executable instruction, and the executable instruction enables the processor to perform operations corresponding to the above-mentioned security protection method of the vehicle-mounted system.
根据本发明的再一方面,提供了一种计算机存储介质,所述存储介质中存储有至少一可执行指令,所述可执行指令使处理器执行如上述车载系统的安全防护方法对应的操作。According to yet another aspect of the present invention, a computer storage medium is provided, wherein the storage medium stores at least one executable instruction, and the executable instruction causes the processor to perform operations corresponding to the above-mentioned security protection method for an in-vehicle system.
根据本发明提供的车载系统的安全防护方法及系统,由安全防护服务端根据获取的漏洞信息生成相应的车机防御策略,并将生成的车机防御策略传递至车辆厂商端;进一步由车辆厂商端根据预设的下发规则,为车机终端下发相对应的车机防御策略;车机终端利用接收到的车机防御策略进行安全防御。本方案中通过安全防护服务端、车辆厂商端以及车机终端三方共同来对车载系统进行安全防护,可提高车载系统安全防护的完备性,具有优异的安全防护效果。According to the security protection method and system for an in-vehicle system provided by the present invention, the security protection server generates a corresponding vehicle defense strategy according to the acquired vulnerability information, and transmits the generated vehicle defense strategy to the vehicle manufacturer; further, the vehicle manufacturer generates a corresponding vehicle defense strategy. The terminal issues the corresponding vehicle-machine defense strategy to the vehicle-machine terminal according to the preset distribution rules; the vehicle-machine terminal uses the received vehicle-machine defense strategy for security defense. In this solution, the security protection server, the vehicle manufacturer and the vehicle terminal are used to jointly protect the vehicle system, which can improve the completeness of the vehicle system security protection and has an excellent security protection effect.
上述说明仅是本发明技术方案的概述,为了能够更清楚了解本发明的技术手段,而可依照说明书的内容予以实施,并且为了让本发明的上述和其它目的、特征和优点能够更明显易懂,以下特举本发明的具体实施方式。The above description is only an overview of the technical solutions of the present invention, in order to be able to understand the technical means of the present invention more clearly, it can be implemented according to the content of the description, and in order to make the above and other purposes, features and advantages of the present invention more obvious and easy to understand , the following specific embodiments of the present invention are given.
附图说明Description of drawings
通过阅读下文优选实施方式的详细描述,各种其他的优点和益处对于本领域普通技术人员将变得清楚明了。附图仅用于示出优选实施方式的目的,而并不认为是对本发明的限制。而且在整个附图中,用相同的参考符号表示相同的部件。在附图中:Various other advantages and benefits will become apparent to those of ordinary skill in the art upon reading the following detailed description of the preferred embodiments. The drawings are for the purpose of illustrating preferred embodiments only and are not to be considered limiting of the invention. Also, the same components are denoted by the same reference numerals throughout the drawings. In the attached image:
图1示出了根据本发明一个实施例提供的一种车载系统的安全防护方法的流程示意图;FIG. 1 shows a schematic flowchart of a safety protection method for an in-vehicle system provided according to an embodiment of the present invention;
图2示出了根据本发明另一个实施例提供的一种车载系统的安全防护方法的流程示意图;FIG. 2 shows a schematic flowchart of a safety protection method for an in-vehicle system provided according to another embodiment of the present invention;
图3示出了根据本发明一个实施例提供的一种车载系统的安全防护系统的结构示意图;3 shows a schematic structural diagram of a safety protection system of a vehicle-mounted system provided according to an embodiment of the present invention;
图4示出了根据本发明一个实施例提供的一种计算设备的结构示意图。FIG. 4 shows a schematic structural diagram of a computing device according to an embodiment of the present invention.
具体实施方式Detailed ways
下面将参照附图更详细地描述本公开的示例性实施例。虽然附图中显示了本公开的示例性实施例,然而应当理解,可以以各种形式实现本公开而不应被这里阐述的实施例所限制。相反,提供这些实施例是为了能够更透彻地理解本公开,并且能够将本公开的范围完整的传达给本领域的技术人员。Exemplary embodiments of the present disclosure will be described in more detail below with reference to the accompanying drawings. While exemplary embodiments of the present disclosure are shown in the drawings, it should be understood that the present disclosure may be embodied in various forms and should not be limited by the embodiments set forth herein. Rather, these embodiments are provided so that the present disclosure will be more thoroughly understood, and will fully convey the scope of the present disclosure to those skilled in the art.
图1示出了根据本发明一个实施例提供的一种车载系统的安全防护方法的流程示意图。FIG. 1 shows a schematic flowchart of a security protection method for an in-vehicle system according to an embodiment of the present invention.
其中,本实施例所述的车载系统可以为车载T-box(Telematics Box)系统、车载信息娱乐系统(IVI,In-Vehicle Infotainment)、和/或平视显示系统(HUD,Head UpDisplay)等等。本实施例对车载系统的具体类型等不作限定。如图1所示,该方法包括:The in-vehicle system described in this embodiment may be an in-vehicle T-box (Telematics Box) system, an in-vehicle infotainment system (IVI, In-Vehicle Infotainment), and/or a head-up display system (HUD, Head Up Display) and the like. This embodiment does not limit the specific type and the like of the in-vehicle system. As shown in Figure 1, the method includes:
步骤S110,安全防护服务端根据获取的漏洞信息生成相应的车机防御策略,并将生成的车机防御策略传递至车辆厂商端。In step S110, the security protection server generates a corresponding vehicle-machine defense strategy according to the obtained vulnerability information, and transmits the generated vehicle-machine defense strategy to the vehicle manufacturer.
其中,安全防护服务端为具有车载系统安全分析能力,并且可提供车载系统漏洞解决策略的服务端,其具体可以为至少一台云端服务器。Among them, the security protection server is a server that has the security analysis capability of the in-vehicle system and can provide a solution strategy for the vulnerability of the in-vehicle system, which may specifically be at least one cloud server.
在实际的实施过程中,安全防护服务端对车辆厂商端反馈的信息和/或从安全论坛或网站中获得的有关车载系统的漏洞信息进行分析,根据分析结果确定车机终端可能存在的安全漏洞,该可能存在的安全漏洞即为待防御漏洞。并进一步生成相应的车机防御规则,以此来实现对车载系统的漏洞预测及防御。In the actual implementation process, the security protection server analyzes the information fed back by the vehicle manufacturer and/or the vulnerability information about the vehicle system obtained from the security forum or website, and determines the possible security vulnerabilities in the vehicle terminal according to the analysis results. , the possible security vulnerability is the vulnerability to be defended. And further generate the corresponding vehicle and machine defense rules, so as to realize the vulnerability prediction and defense of the vehicle system.
进一步地,安全防护服务端在生成车机防御策略之后,可将生成的车机防御策略传递至车辆厂商端。其中,本实施例对具体的传递方式不做限定,例如,安全防护服务端可与车辆厂商端建立网络连接,通过http协议等方式将车机防御策略从安全防护服务端传递至车辆厂商端。Further, after generating the vehicle-machine defense policy, the security protection server may transmit the generated vehicle-machine defense policy to the vehicle manufacturer. The specific transmission method is not limited in this embodiment. For example, the security protection server can establish a network connection with the vehicle manufacturer, and transmit the vehicle defense policy from the security server to the vehicle manufacturer through the http protocol.
在一种可选的实施方式中,车辆厂商端可以为多个,不同的车辆厂商端对应于不同的车机终端。则安全防护服务端在将生成的车机防御策略传递至车辆厂商端过程中,可针对于不同的车辆厂商端所对应的车机终端的类别等,为不同的车辆厂商端传递相匹配的车机防御策略,从而在实现为车辆厂商端传递定制化的车机防御策略的同时,还可进一步节省带宽资源。此外,为车辆厂商端仅传递与其相匹配的车机防御策略,可进一步保障安全防护服务端传递的其他车机防御策略的信息安全。In an optional implementation manner, there may be multiple vehicle manufacturer terminals, and different vehicle manufacturer terminals correspond to different vehicle-machine terminals. Then, in the process of transmitting the generated vehicle defense policy to the vehicle manufacturer, the security protection server can deliver matching vehicles for different vehicle manufacturers according to the types of vehicle terminals corresponding to different vehicle manufacturers. In this way, the customized vehicle defense strategy can be delivered to the vehicle manufacturer, and bandwidth resources can be further saved. In addition, only the matching vehicle and vehicle defense strategies are transmitted to the vehicle manufacturer, which can further ensure the information security of other vehicle and vehicle defense strategies transmitted by the security protection server.
步骤S120,车辆厂商端根据预设的下发规则,为车机终端下发相对应的车机防御策略。In step S120, the vehicle manufacturer side issues a corresponding vehicle-machine defense strategy to the vehicle-machine terminal according to a preset distribution rule.
车辆厂商端在接收到安全防护服务端传递的车机防御策略后,可根据车辆厂商端中的预设的下发规则,为车机终端下发相对应的车机防御策略。其中,本实施例对预设的下发规则的具体内容等不作限定,本领域技术人员可根据实际的需求自行设定。After receiving the vehicle defense strategy transmitted by the security protection server, the vehicle manufacturer can issue the corresponding vehicle defense strategy to the vehicle terminal according to the preset delivery rules in the vehicle manufacturer. Wherein, this embodiment does not limit the specific content and the like of the preset delivery rule, and those skilled in the art can set it by themselves according to actual needs.
其中,预设的下发规则中具体包含有车机防御策略下发对象的相关信息。举例来说,车辆厂商端可对接收到的车机防御策略进行分类,例如,可根据车机防御策略所属的系统类别进行分类(如分为linux系统、Android系统、QNX系统等等)。并进一步确定不同系统类别所对应的车机终端,从而为车机终端下发与其系统类别相匹配的车机防御策略,从而有利于提升车载系统的安全防御效果。Wherein, the preset delivery rule specifically includes the relevant information of the delivery object of the vehicle-machine defense strategy. For example, the vehicle manufacturer can classify the received vehicle-machine defense policies, for example, according to the system category to which the vehicle-machine defense policies belong (for example, into linux system, Android system, QNX system, etc.). And further determine the on-board terminals corresponding to different system categories, so as to issue the on-board defense strategies for the on-board terminals that match their system categories, which is beneficial to improve the security defense effect of the on-board system.
在一种可选的实施方式中,预设的下发规则中还包含有车机防御策略具体的下发时机。其中,该具体的下发时机可由车辆厂商端根据其所包含的车机终端的历史行为数据和/或车机防御策略的特性等确定。例如,若车机防御策略无法在车辆行驶过程中运行,则车辆厂商端可在车机终端非行驶过程中进行下发;又或者,通过对某一车机终端历史行为数据的分析发现,该车机终端的用户通常对提示的安全漏洞信息较为重视,则车辆厂商端可在接收到车机防御策略之后,立即下发相应的车机防御策略至该车机终端,等等。In an optional implementation manner, the preset issuing rule further includes the specific issuing timing of the vehicle-machine defense strategy. The specific delivery timing may be determined by the vehicle manufacturer according to the historical behavior data of the vehicle terminal and/or the characteristics of the vehicle defense strategy included in the vehicle manufacturer. For example, if the vehicle-machine defense strategy cannot be run while the vehicle is running, the vehicle manufacturer can issue it during the non-driving process of the vehicle-machine terminal; or, through the analysis of the historical behavior data of a certain vehicle-machine terminal, it is found that the The user of the vehicle terminal usually pays more attention to the security vulnerability information prompted, and the vehicle manufacturer can immediately send the corresponding vehicle defense strategy to the vehicle terminal after receiving the vehicle defense strategy, and so on.
在又一种可选的实施方式中,车机防御策略中携带有待防御漏洞的优先级信息。即为待防御漏洞划定相应的危险级别,如高危漏洞、一般漏洞、低危漏洞等等。则车辆厂商端在根据预设的下发规则,为车机终端下发相对应的车机防御策略过程中,可根据车机防御策略中待防御漏洞的优先级进行车机防御策略的下发。例如,针对于高危漏洞,可实时下发至车机终端;而针对于一般漏洞或低危漏洞等可在车机终端维修或保养等阶段进行下发。In yet another optional implementation manner, the vehicle-machine defense policy carries priority information of the vulnerabilities to be defended. That is, the corresponding danger level is delineated for the vulnerabilities to be defended, such as high-risk vulnerabilities, general vulnerabilities, low-risk vulnerabilities, and so on. In the process of issuing the corresponding vehicle defense strategy to the vehicle terminal according to the preset distribution rules, the vehicle manufacturer can issue the vehicle defense strategy according to the priority of the vulnerabilities to be defended in the vehicle defense strategy. . For example, for high-risk vulnerabilities, it can be delivered to the vehicle terminal in real time; for general vulnerabilities or low-risk vulnerabilities, it can be delivered during the repair or maintenance of the vehicle terminal.
可选的,本实施例还可为车辆厂商端的用户提供配置下发规则的入口,从而车辆厂商端的用户可根据具体的情况配置相应的下发规则,进而提高其灵活性。Optionally, this embodiment can also provide an entry for configuring the issuing rules for the user of the vehicle manufacturer, so that the user of the vehicle manufacturer can configure the corresponding issuing rules according to specific conditions, thereby improving its flexibility.
步骤S130,车机终端利用接收到的车机防御策略进行安全防御。Step S130, the vehicle-machine terminal uses the received vehicle-machine defense strategy to perform security defense.
车机终端在接收到下发的车机防御规则之后,根据下发的车机防御规则进行漏洞防御,从而保障车机终端中车载系统的安全运行。After receiving the issued car-machine defense rules, the car-machine terminal performs vulnerability defense according to the issued car-machine defense rules, thereby ensuring the safe operation of the on-board system in the car-machine terminal.
由此可见,本实施例中由安全防护服务端根据获取的漏洞信息生成相应的车机防御策略,并将生成的车机防御策略传递至车辆厂商端;车辆厂商端根据预设的下发规则,为车机终端下发相对应的车机防御策略;车机终端利用接收到的车机防御策略进行安全防御。本方案中通过安全防护服务端、车辆厂商端以及车机终端来对车载系统进行安全防护,可实现对车载系统的完备的安全防护,具有优异的安全防护效果。It can be seen that, in this embodiment, the security protection server generates a corresponding vehicle defense strategy according to the acquired vulnerability information, and transmits the generated vehicle defense strategy to the vehicle manufacturer; the vehicle manufacturer distributes the rules according to the preset rules. , to issue the corresponding vehicle defense strategy to the vehicle terminal; the vehicle terminal uses the received vehicle defense strategy for security defense. In this solution, the security protection server, vehicle manufacturer and vehicle terminal are used to protect the vehicle system, which can realize complete security protection for the vehicle system, and has excellent security protection effect.
图2示出了根据本发明另一个实施例提供的一种车载系统安全防护方法的流程示意图。如图2所示,该方法包括:FIG. 2 shows a schematic flowchart of a method for safety protection of an in-vehicle system according to another embodiment of the present invention. As shown in Figure 2, the method includes:
步骤S210,车机终端根据预设的攻击检测策略,对车机终端自身进行攻击检测;若检测到攻击行为,则生成相应的告警信息,并将告警信息发送至对应的车辆厂商端。In step S210, the vehicle terminal performs attack detection on the vehicle terminal itself according to a preset attack detection strategy; if an attack is detected, corresponding alarm information is generated, and the alarm information is sent to the corresponding vehicle manufacturer.
在实际的实施过程中,车机终端可通过文件检测和/或行为检测的方式对车机终端自身进行攻击检测。例如,可利用特征匹配的静态文件监测以及实施监控恶意攻击数据或漏洞利用手段的动态恶意行为监测对车机终端自身进行攻击检测。本实施例对具体的文件检测和/或行为检测的方式不做限定,本领域技术人员可根据实际的需求采用相应的攻击检测方法。In the actual implementation process, the vehicle terminal can perform attack detection on the vehicle terminal itself by means of file detection and/or behavior detection. For example, static file monitoring for feature matching and dynamic malicious behavior monitoring for monitoring malicious attack data or vulnerability exploitation methods can be used to detect attacks on the vehicle terminal itself. This embodiment does not limit the specific file detection and/or behavior detection methods, and those skilled in the art can adopt corresponding attack detection methods according to actual requirements.
可选的,为提高车载系统的安全性,降低攻击检测的误报率,本实施例可针对于车载系统中的至少一个层级进行攻击检测。例如,可在车载系统中的应用层、框架层以及内核层等层级中均进行攻击检测,从而可大幅提高攻击检测的覆盖面,降低攻击检测的漏报率。进一步可选的,为提升攻击检测效果,本实施例可针对于不同层级采用相应的攻击检测方式。例如,在内核层通过埋点法的方式检测对内核层的攻击行为,而在框架层,可通过埋点以及云端智能判断的方式确定攻击行为。Optionally, in order to improve the security of the in-vehicle system and reduce the false alarm rate of attack detection, this embodiment may perform attack detection for at least one level in the in-vehicle system. For example, attack detection can be performed at the application layer, framework layer, and kernel layer in the vehicle system, which can greatly improve the coverage of attack detection and reduce the false negative rate of attack detection. Further optionally, in order to improve the attack detection effect, this embodiment may adopt corresponding attack detection methods for different levels. For example, at the kernel layer, the attack behavior on the kernel layer can be detected by the method of burying points, while at the framework layer, the attack behavior can be determined by the method of burying points and intelligent judgment in the cloud.
在车机终端对自身进行攻击检测过程中,若检测到攻击行为,则进一步根据该攻击行为生成相应的告警信息,并将该告警信息发送至与之对应的车辆厂商端。其中,告警信息中携带有攻击行为的具体数据信息。本实施例对告警信息的具体呈现形式以及传输方式等不做限定。During the attack detection process of the vehicle terminal itself, if an attack behavior is detected, corresponding alarm information is further generated according to the attack behavior, and the alarm information is sent to the corresponding vehicle manufacturer terminal. The alarm information carries specific data information of the attack behavior. This embodiment does not limit the specific presentation form and transmission mode of the alarm information.
步骤S220,车辆厂商端将接收到的告警信息传递至安全防护服务端。In step S220, the vehicle manufacturer transmits the received alarm information to the security protection server.
车辆厂商端在接收到车机终端发送的告警信息之后,可进一步地将接收到的告警信息传递至安全防护服务端。After receiving the alarm information sent by the vehicle terminal, the vehicle manufacturer terminal can further transmit the received alarm information to the security protection server.
可选的,为便于安全防护端可准确全面地制定车机防御策略,车辆厂商端可将告警信息对应的车机终端的具体参数等信息与告警信息一并传递至安全防护服务端。Optionally, in order for the security protection terminal to accurately and comprehensively formulate a vehicle-machine defense strategy, the vehicle manufacturer terminal may transmit information such as specific parameters of the vehicle-mounted terminal corresponding to the alarm information to the security protection server together with the alarm information.
可选的,车辆厂商端可在接收到告警信息之后,进一步对告警信息进行验证,待验证通过后再传递至安全防护服务端,以保障整体的信息安全性。其中,本实施例对具体的验证方式不做限定,例如,可验证该告警信息是否来自于合法的车机终端等等。Optionally, after receiving the alarm information, the vehicle manufacturer can further verify the alarm information, and after the verification is passed, it can be transmitted to the security protection server to ensure the overall information security. Wherein, this embodiment does not limit the specific verification method, for example, it can be verified whether the alarm information comes from a legal vehicle terminal and the like.
步骤S230,安全防护服务端根据车辆厂商端传递的告警信息和/或从预设漏洞库中获取的漏洞信息生成相应的车机防御策略;并将车机防御策略传递至车辆厂商端;其中,车机防御策略包括漏洞检测策略以及相对应的漏洞防御策略。Step S230, the security protection server generates a corresponding vehicle defense strategy according to the alarm information transmitted by the vehicle manufacturer and/or the vulnerability information obtained from the preset vulnerability library; and transmits the vehicle defense strategy to the vehicle manufacturer; wherein, Vehicle and machine defense strategies include vulnerability detection strategies and corresponding vulnerability defense strategies.
具体地,安全防护服务端具体是以车辆厂商端传递的告警信息和/或从预设漏洞库中获取的漏洞信息为基础,生成相应的车机防御策略。其中,该预设漏洞库可以为包含漏洞信息的预设网站、预设论坛、预设交流平台等;也可以从预设网站、预设论坛、预设交流平台等获取漏洞信息后集中存储于预设的信息库中,而该信息库即为预设漏洞库。Specifically, the security protection server generates a corresponding vehicle-machine defense strategy based on the alarm information transmitted by the vehicle manufacturer and/or the vulnerability information obtained from the preset vulnerability database. The preset vulnerability library may be a preset website, a preset forum, a preset communication platform, etc. that contain vulnerability information; or the vulnerability information may be obtained from a preset website, a preset forum, a preset communication platform, etc., and then stored in a centralized manner. In the preset information library, and the information library is the preset vulnerability library.
在安全防护服务端生成车机防御策略过程中,首先根据告警信息和/或从预设漏洞库中获取的漏洞信息进行归因处理,确定引起该漏洞的原因,并生成相应的分析报告。可选的,在生成分析报告之后,进一步将生成的分析报告传递至车辆厂商端,以供车辆厂商端获知漏洞成因,从而便于车辆厂商端对车辆维护等策略的调整。在确定引起漏洞的原因之后,进一步生成漏洞检测策略,并将漏洞检测策略传递至车辆厂商端。其中,该漏洞检测策略具体可以为漏洞检测脚本。In the process of generating the vehicle-machine defense strategy by the security protection server, attribution processing is firstly performed according to the alarm information and/or the vulnerability information obtained from the preset vulnerability database, the cause of the vulnerability is determined, and a corresponding analysis report is generated. Optionally, after the analysis report is generated, the generated analysis report is further transmitted to the vehicle manufacturer, so that the vehicle manufacturer can know the cause of the vulnerability, thereby facilitating the vehicle manufacturer to adjust policies such as vehicle maintenance. After determining the cause of the vulnerability, a vulnerability detection strategy is further generated, and the vulnerability detection strategy is transmitted to the vehicle manufacturer. The vulnerability detection strategy may specifically be a vulnerability detection script.
进一步地,在生成漏洞检测策略之后,可制定与该漏洞检测策略相对应的漏洞防御策略,并将漏洞防御策略也传递至车辆厂商端。在此,本领域技术人员应当理解的是,本实施例中车机防御策略中包含的漏洞检测策略以及漏洞防御策略可一并传递至车辆厂商端;也可将漏洞检测策略及漏洞防御策略进行分次传递,从而有利于整体防御效率的提升。Further, after the vulnerability detection strategy is generated, a vulnerability defense strategy corresponding to the vulnerability detection strategy can be formulated, and the vulnerability defense strategy is also transmitted to the vehicle manufacturer. Here, those skilled in the art should understand that the vulnerability detection strategy and the vulnerability defense strategy included in the vehicle-machine defense strategy in this embodiment may be transmitted to the vehicle manufacturer at the same time; It is transmitted in stages, which is beneficial to the improvement of the overall defense efficiency.
可选的,安全防护服务端在生成分析报告、生成漏洞检测策略和/或生成漏洞防御策略均在相应的时间段内完成,从而保障对车机终端中的车载系统的及时防御,Optionally, the generation of the analysis report, the generation of the vulnerability detection strategy and/or the generation of the vulnerability defense strategy by the security protection server is completed within a corresponding time period, so as to ensure the timely defense of the vehicle system in the vehicle terminal.
步骤S240,车辆厂商端根据预设的下发规则,将漏洞检测策略下发至对应的车机终端。In step S240, the vehicle manufacturer side delivers the vulnerability detection strategy to the corresponding vehicle terminal according to the preset delivery rule.
车辆厂商端在接收到安全防护服务端传递的漏洞检测策略之后,可进行漏洞检测策略的部署。并进一步根据预设的下发规则,将漏洞检测策略下发至对应的车机终端。例如,可漏洞检测策略中待防御漏洞所对应的系统类别、车型类别等等,将漏洞检测策略下发至对应的车机终端。After receiving the vulnerability detection strategy transmitted by the security protection server, the vehicle manufacturer can deploy the vulnerability detection strategy. And further according to the preset distribution rules, the vulnerability detection strategy is distributed to the corresponding vehicle terminal. For example, the system category, vehicle type, etc. corresponding to the vulnerability to be defended in the vulnerability detection strategy can be issued, and the vulnerability detection strategy can be delivered to the corresponding vehicle terminal.
步骤S250,车机终端根据接收到的漏洞检测策略进行漏洞检测,并将检测结果上报至车辆厂商端。Step S250, the vehicle terminal performs vulnerability detection according to the received vulnerability detection strategy, and reports the detection result to the vehicle manufacturer.
首先,车机终端在接收到车辆厂商端下发的漏洞检测策略之后,根据接收到的漏洞检测策略进行漏洞检测。可选的,漏洞检测策略中包含有待防御漏洞的位置信息。其中,该位置信息具体为待防御漏洞易发的模块、层级等等。车机终端可根据接收到的漏洞检测策略中待防御漏洞的具体位置快速地进行漏洞检测,以此提升车载系统的漏洞检测效率。First, after receiving the vulnerability detection strategy issued by the vehicle manufacturer, the vehicle terminal performs vulnerability detection according to the received vulnerability detection strategy. Optionally, the vulnerability detection policy includes location information of the vulnerability to be defended. Wherein, the location information is specifically a module, a level, and the like, which are vulnerable to vulnerabilities to be defended against. The in-vehicle terminal can quickly perform vulnerability detection according to the specific position of the vulnerability to be defended in the received vulnerability detection strategy, thereby improving the vulnerability detection efficiency of the in-vehicle system.
在一种可选的实施方式中,可通过文件检测和/或入侵检测的方式来对车机终端进行漏洞检测。例如,可通过恶意攻击文件监测、文件特征串匹配、文件调用序列匹配等文件检测方式来对车机终端进行漏洞监测;也可以通过预设接口参数恶意数据监测、root权限获取方式监测等入侵检测方式来对车机终端进行漏洞检测。或者,也可采用预设渗透测试等方式对车机终端进行漏洞检测。本实施例对具体的漏洞检测方式不做限定。In an optional implementation manner, vulnerability detection may be performed on the vehicle terminal by means of file detection and/or intrusion detection. For example, the vehicle terminal can be monitored for vulnerabilities through file detection methods such as malicious attack file monitoring, file feature string matching, file calling sequence matching, etc.; and intrusion detection such as malicious data monitoring with preset interface parameters and root access monitoring can also be used. The method is used to detect the vulnerability of the vehicle terminal. Alternatively, a preset penetration test or other methods can also be used to detect vulnerabilities on the vehicle terminal. This embodiment does not limit the specific vulnerability detection method.
进一步地,在车机终端进行漏洞检测之后,可将检测结果上报至车辆厂商端。Further, after the vehicle terminal performs vulnerability detection, the detection result may be reported to the vehicle manufacturer.
步骤S250,车辆厂商端根据预设的下发规则以及接收到的检测结果,为车机终端下发相对应的漏洞防御策略。In step S250, the vehicle manufacturer side issues a corresponding vulnerability defense strategy to the vehicle-machine terminal according to the preset delivery rule and the received detection result.
具体地,车辆厂商端根据对车机终端发送的检测结果的分析,确定存在待防御漏洞的车机终端。并进一步根据预设的下发规则为存在待防御漏洞的车机终端下发相对应的漏洞防御策略。Specifically, the vehicle manufacturer side determines, according to the analysis of the detection result sent by the vehicle terminal, the vehicle terminal that has the vulnerability to be defended. And further according to the preset issuing rules, the corresponding vulnerability defense strategy is issued to the vehicle terminal that has the vulnerability to be defended.
步骤S260,车机终端利用接收到的漏洞防御策略进行漏洞防御。Step S260, the vehicle terminal uses the received vulnerability defense strategy to perform vulnerability defense.
其中,漏洞防御策略中包含有文件阻断策略、入侵阻断策略和/或热补丁修复策略等。则车机终端在漏洞防御过程中,可采用文件阻断策略、入侵阻断策略和/或热补丁修复策略进行漏洞的阻断修复。The vulnerability defense strategy includes a file blocking strategy, an intrusion blocking strategy, and/or a hot patch repair strategy, and the like. In the process of vulnerability defense, the vehicle terminal may use a file blocking strategy, an intrusion blocking strategy and/or a hot patch repair strategy to block and repair the vulnerability.
可选的,车机终端在漏洞检测以及漏洞防御过程中,为保障车载系统的安全性及稳定性,本实施例可采用分级检测防御的方式。具体地,首先采用精准度较低,但对系统影响较小的文件检测的方式进行漏洞检测,在确定存在待防御漏洞时,采用文件冻结或删除等方式进行漏洞阻断。其中,该文件检测具体可以为payload文件监控,本实施例对具体的文件检测方式不做限定,例如可通过恶意攻击文件监测、文件特征串匹配和/或文件调用序列匹配等;进一步地,采用入侵检测的方式进行漏洞检测,该种方式检测精度适中,并且对车载系统影响较小。具体可通过接口参数恶意数据监测、Root提权方式监测等方式进行漏洞检测,并采用相应的路径阻断等方式进行阻断;最后,可针对于某些特定的待防御漏洞进行热补丁修复,从而达到使车载系统免疫该漏洞的效果。其中,在采用热补丁的方式进行漏洞修复时,可由安全防护服务端制定相应的热补丁,进而将热补丁传递至车辆厂商端,待车辆厂商端对热补丁进行部署之后,进一步将热补丁下发至对应的车机终端,从而使得车机终端实现对该漏洞的免疫。Optionally, in the process of vulnerability detection and vulnerability defense of the on-board terminal, in order to ensure the security and stability of the on-board system, this embodiment may adopt a method of hierarchical detection and defense. Specifically, the method of file detection with low accuracy but less impact on the system is used to detect vulnerabilities first, and when it is determined that there is a vulnerability to be defended, the method of file freezing or deletion is used to block the vulnerability. Specifically, the file detection may be payload file monitoring, and this embodiment does not limit the specific file detection method, for example, malicious attack file monitoring, file feature string matching and/or file calling sequence matching, etc.; The intrusion detection method is used for vulnerability detection. This method has moderate detection accuracy and little impact on the vehicle system. Specifically, vulnerability detection can be carried out by means of interface parameter malicious data monitoring, root privilege escalation monitoring, etc., and corresponding path blocking and other methods can be used to block them; In order to achieve the effect of making the vehicle system immune to this vulnerability. Among them, when using hot patch to repair the vulnerability, the security protection server can formulate the corresponding hot patch, and then transmit the hot patch to the vehicle manufacturer. After the vehicle manufacturer deploys the hot patch, the hot patch is further downloaded Send it to the corresponding vehicle terminal, so that the vehicle terminal can be immune to the vulnerability.
在一种可选的实施方式中,在步骤S260执行之后,可进一步执行步骤S210,形成针对于车载系统的完整防护生态循环,进而可多方位一体化地实现对车载系统的安全防护。In an optional implementation manner, after step S260 is performed, step S210 may be further performed to form a complete protection ecological cycle for the vehicle-mounted system, thereby realizing the security protection of the vehicle-mounted system in a multi-directional and integrated manner.
由此可见,本实施例由车机终端根据预设的攻击检测策略,对车机终端自身进行攻击检测;若检测到攻击行为,则生成相应的告警信息,并将告警信息发送至对应的车辆厂商端,即实现对车机终端自身的攻击检测;并由车辆厂商端将接收到的告警信息传递至安全防护服务端,供安全防护服务端根据车辆厂商端传递的告警信息和/或从预设漏洞库中获取的漏洞信息生成相应的车机防御策略;并将车机防御策略传递至车辆厂商端,从而实现对漏洞的预测过程;并且,由车辆厂商端根据预设的下发规则,将漏洞检测策略下发至对应的车机终端,在提高车辆厂商端灵活性的同时,进一步保障车机终端的安全性;车机终端根据接收到的漏洞检测策略进行漏洞检测,并将检测结果上报至车辆厂商端,车辆厂商端根据预设的下发规则以及接收到的检测结果,为车机终端下发相对应的漏洞防御策略。本方案中通过安全防护服务端、车辆厂商端以及车机终端来对车载系统进行安全防护,可实现对车载系统的完备的安全防护,具有优异的安全防护效果;并且,可实现漏洞预测、对预测的漏洞进行防御、终端自身攻击检测、以及对终端自身攻击检测的快速响应,从而形成针对于车载系统的完整防护生态循环,进而可多方位一体化地实现对车载系统的安全防护。It can be seen that, in this embodiment, the vehicle terminal performs attack detection on the vehicle terminal itself according to the preset attack detection strategy; if an attack is detected, corresponding alarm information is generated, and the alarm information is sent to the corresponding vehicle The manufacturer side realizes the attack detection on the vehicle terminal itself; and the vehicle manufacturer side transmits the received alarm information to the security protection server, so that the security protection server can use the alarm information transmitted by the vehicle manufacturer and/or from the pre-warning server. Set the vulnerability information obtained in the vulnerability library to generate the corresponding vehicle defense strategy; and transmit the vehicle defense strategy to the vehicle manufacturer, so as to realize the vulnerability prediction process; The vulnerability detection strategy is issued to the corresponding vehicle terminal, which improves the flexibility of the vehicle manufacturer and further ensures the security of the vehicle terminal; the vehicle terminal performs vulnerability detection according to the received vulnerability detection strategy, and reports the detection results. It is reported to the vehicle manufacturer, and the vehicle manufacturer distributes the corresponding vulnerability defense strategy to the vehicle terminal according to the preset distribution rules and the received detection results. In this solution, the security protection server, the vehicle manufacturer and the vehicle terminal are used to protect the vehicle system, which can realize complete security protection for the vehicle system, and has excellent security protection effect; The predicted vulnerabilities are used for defense, terminal self-attack detection, and rapid response to terminal self-attack detection, thus forming a complete protection ecological cycle for the vehicle system, and then realizing the security protection of the vehicle system in a multi-faceted and integrated manner.
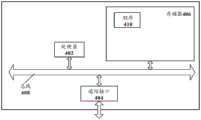
图3示出了根据本发明一个实施例提供的一种车载系统的安全防护系统的结构示意图。如图3所示,该安全防护系统包括:安全防护服务端31、车辆厂商端32、以及车机终端33。FIG. 3 shows a schematic structural diagram of a safety protection system of a vehicle-mounted system provided according to an embodiment of the present invention. As shown in FIG. 3 , the security protection system includes: a
安全防护服务端31,适于根据获取的漏洞信息生成相应的车机防御策略,并将生成的车机防御策略传递至车辆厂商端;The
车辆厂商端32,适于根据预设的下发规则,为车机终端下发相对应的车机防御策略;The
车机终端33,适于利用接收到的车机防御策略进行安全防御。The vehicle-
可选的,车机终端33进一步适于:根据预设的攻击检测策略,对车机终端自身进行攻击检测;若检测到攻击行为,则生成相应的告警信息,并将所述告警信息发送至对应的车辆厂商端;Optionally, the
车辆厂商端32进一步适于:将接收到的告警信息传递至安全防护服务端。The
可选的,安全防护服务端31进一步适于:根据车辆厂商端传递的告警信息和/或从预设漏洞库中获取的漏洞信息生成相应的车机防御策略。Optionally, the
可选的,所述车机防御策略包括:漏洞检测策略以及相对应的漏洞防御策略。Optionally, the vehicle-machine defense strategy includes: a vulnerability detection strategy and a corresponding vulnerability defense strategy.
可选的,安全防护服务端31进一步适于:将所述漏洞检测策略传递至车辆厂商端;Optionally, the
车辆厂商端32进一步适于:根据预设的下发规则,将漏洞检测策略下发至对应的车机终端;The
车机终端33进一步适于:根据接收到的漏洞检测策略进行漏洞检测,并将检测结果上报至车辆厂商端。The
可选的,车辆厂商端32进一步适于:根据预设的下发规则以及接收到的检测结果,为车机终端下发相对应的漏洞防御策略;Optionally, the
车机终端33进一步适于:利用接收到的漏洞防御策略进行漏洞防御。The on-
其中,本实施例所提供的车载系统的安全防护系统中各部分的具体实施过程可参照图1和/或图2所示实施例中相应步骤的描述,本实施例在此不做赘述。For the specific implementation process of each part in the safety protection system of the vehicle-mounted system provided in this embodiment, reference may be made to the description of the corresponding steps in the embodiment shown in FIG. 1 and/or FIG. 2 , which is not repeated in this embodiment.
由此可见,本实施例中由安全防护服务端根据获取的漏洞信息生成相应的车机防御策略,并将生成的车机防御策略传递至车辆厂商端;车辆厂商端根据预设的下发规则,为车机终端下发相对应的车机防御策略;车机终端利用接收到的车机防御策略进行安全防御。本方案中通过安全防护服务端、车辆厂商端以及车机终端来对车载系统进行安全防护,可实现对车载系统的完备的安全防护,具有优异的安全防护效果。It can be seen that, in this embodiment, the security protection server generates a corresponding vehicle defense strategy according to the acquired vulnerability information, and transmits the generated vehicle defense strategy to the vehicle manufacturer; the vehicle manufacturer distributes the rules according to the preset rules. , to issue the corresponding vehicle defense strategy to the vehicle terminal; the vehicle terminal uses the received vehicle defense strategy for security defense. In this solution, the security protection server, vehicle manufacturer and vehicle terminal are used to protect the vehicle system, which can realize complete security protection for the vehicle system, and has excellent security protection effect.
根据本发明一个实施例提供了一种非易失性计算机存储介质,所述计算机存储介质存储有至少一可执行指令,该计算机可执行指令可执行上述任意方法实施例中的车载系统的安全防护方法。According to an embodiment of the present invention, a non-volatile computer storage medium is provided, wherein the computer storage medium stores at least one executable instruction, and the computer executable instruction can execute the security protection of the vehicle-mounted system in any of the above method embodiments method.
图4示出了根据本发明一个实施例提供的一种计算设备的结构示意图,本发明具体实施例并不对计算设备的具体实现做限定。FIG. 4 shows a schematic structural diagram of a computing device according to an embodiment of the present invention. The specific embodiment of the present invention does not limit the specific implementation of the computing device.
如图4所示,该计算设备可以包括:处理器(processor)402、通信接口(Communications Interface)404、存储器(memory)406、以及通信总线408。As shown in FIG. 4 , the computing device may include: a processor (processor) 402 , a communications interface (Communications Interface) 404 , a memory (memory) 406 , and a communication bus 408 .
其中:in:
处理器402、通信接口404、以及存储器406通过通信总线408完成相互间的通信。The processor 402 , the
通信接口404,用于与其它设备比如客户端或其它服务器等的网元通信。The
处理器402,用于执行程序410,具体可以执行上述车载系统的安全防护方法实施例中的相关步骤。The processor 402 is configured to execute the
具体地,程序410可以包括程序代码,该程序代码包括计算机操作指令。Specifically, the
处理器402可能是中央处理器CPU,或者是特定集成电路ASIC(ApplicationSpecific Integrated Circuit),或者是被配置成实施本发明实施例的一个或多个集成电路。计算设备包括的一个或多个处理器,可以是同一类型的处理器,如一个或多个CPU;也可以是不同类型的处理器,如一个或多个CPU以及一个或多个ASIC。The processor 402 may be a central processing unit (CPU), or an application specific integrated circuit (ASIC), or one or more integrated circuits configured to implement embodiments of the present invention. The one or more processors included in the computing device may be the same type of processors, such as one or more CPUs; or may be different types of processors, such as one or more CPUs and one or more ASICs.
存储器406,用于存放程序410。存储器406可能包含高速RAM存储器,也可能还包括非易失性存储器(non-volatile memory),例如至少一个磁盘存储器。The memory 406 is used to store the
程序410具体可以用于使得处理器402执行以下操作:The
安全防护服务端根据获取的漏洞信息生成相应的车机防御策略,并将生成的车机防御策略传递至车辆厂商端;The security protection server generates the corresponding vehicle defense strategy according to the obtained vulnerability information, and transmits the generated vehicle defense strategy to the vehicle manufacturer;
车辆厂商端根据预设的下发规则,为车机终端下发相对应的车机防御策略;The vehicle manufacturer sends the corresponding vehicle defense strategy to the vehicle terminal according to the preset distribution rules;
车机终端利用接收到的车机防御策略进行安全防御。The vehicle-machine terminal uses the received vehicle-machine defense strategy for security defense.
在一种可选的实施方式中,程序410具体可以用于使得处理器402执行以下操作:In an optional implementation manner, the
车机终端根据预设的攻击检测策略,对车机终端自身进行攻击检测;若检测到攻击行为,则生成相应的告警信息,并将所述告警信息发送至对应的车辆厂商端;The vehicle terminal performs attack detection on the vehicle terminal itself according to the preset attack detection strategy; if an attack is detected, corresponding alarm information is generated, and the alarm information is sent to the corresponding vehicle manufacturer;
车辆厂商端将接收到的告警信息传递至安全防护服务端。The vehicle manufacturer transmits the received alarm information to the security protection server.
在一种可选的实施方式中,程序410具体可以用于使得处理器402执行以下操作:In an optional implementation manner, the
安全防护服务端根据车辆厂商端传递的告警信息和/或从预设漏洞库中获取的漏洞信息生成相应的车机防御策略。The security protection server generates a corresponding vehicle-machine defense strategy according to the alarm information transmitted by the vehicle manufacturer and/or the vulnerability information obtained from the preset vulnerability database.
在一种可选的实施方式中,所述车机防御策略包括:漏洞检测策略以及相对应的漏洞防御策略。In an optional implementation manner, the vehicle-machine defense strategy includes: a vulnerability detection strategy and a corresponding vulnerability defense strategy.
在一种可选的实施方式中,程序410具体可以用于使得处理器402执行以下操作:In an optional implementation manner, the
安全防护服务端将所述漏洞检测策略传递至车辆厂商端;The security protection server transmits the vulnerability detection strategy to the vehicle manufacturer;
车辆厂商端根据预设的下发规则,将漏洞检测策略下发至对应的车机终端;The vehicle manufacturer sends the vulnerability detection strategy to the corresponding vehicle terminal according to the preset distribution rules;
车机终端根据接收到的漏洞检测策略进行漏洞检测,并将检测结果上报至车辆厂商端。The vehicle terminal performs vulnerability detection according to the received vulnerability detection strategy, and reports the detection results to the vehicle manufacturer.
在一种可选的实施方式中,程序410具体可以用于使得处理器402执行以下操作:In an optional implementation manner, the
车辆厂商端根据预设的下发规则以及接收到的检测结果,为车机终端下发相对应的漏洞防御策略;The vehicle manufacturer sends the corresponding vulnerability defense strategy to the vehicle terminal according to the preset distribution rules and the received detection results;
车机终端利用接收到的漏洞防御策略进行漏洞防御。The vehicle terminal uses the received vulnerability defense strategy to perform vulnerability defense.
在此提供的算法和显示不与任何特定计算机、虚拟系统或者其它设备固有相关。各种通用系统也可以与基于在此的示教一起使用。根据上面的描述,构造这类系统所要求的结构是显而易见的。此外,本发明也不针对任何特定编程语言。应当明白,可以利用各种编程语言实现在此描述的本发明的内容,并且上面对特定语言所做的描述是为了披露本发明的最佳实施方式。The algorithms and displays provided herein are not inherently related to any particular computer, virtual system, or other device. Various general-purpose systems can also be used with teaching based on this. The structure required to construct such a system is apparent from the above description. Furthermore, the present invention is not directed to any particular programming language. It is to be understood that various programming languages may be used to implement the inventions described herein, and that the descriptions of specific languages above are intended to disclose the best mode for carrying out the invention.
在此处所提供的说明书中,说明了大量具体细节。然而,能够理解,本发明的实施例可以在没有这些具体细节的情况下实践。在一些实例中,并未详细示出公知的方法、结构和技术,以便不模糊对本说明书的理解。In the description provided herein, numerous specific details are set forth. It will be understood, however, that embodiments of the invention may be practiced without these specific details. In some instances, well-known methods, structures and techniques have not been shown in detail in order not to obscure an understanding of this description.
类似地,应当理解,为了精简本公开并帮助理解各个发明方面中的一个或多个,在上面对本发明的示例性实施例的描述中,本发明的各个特征有时被一起分组到单个实施例、图、或者对其的描述中。然而,并不应将该公开的方法解释成反映如下意图:即所要求保护的本发明要求比在每个权利要求中所明确记载的特征更多的特征。更确切地说,如下面的权利要求书所反映的那样,发明方面在于少于前面公开的单个实施例的所有特征。因此,遵循具体实施方式的权利要求书由此明确地并入该具体实施方式,其中每个权利要求本身都作为本发明的单独实施例。Similarly, it is to be understood that in the above description of exemplary embodiments of the invention, various features of the invention are sometimes grouped together into a single embodiment, figure, or its description. This disclosure, however, should not be construed as reflecting an intention that the invention as claimed requires more features than are expressly recited in each claim. Rather, as the following claims reflect, inventive aspects lie in less than all features of a single foregoing disclosed embodiment. Thus, the claims following the Detailed Description are hereby expressly incorporated into this Detailed Description, with each claim standing on its own as a separate embodiment of this invention.
本领域那些技术人员可以理解,可以对实施例中的设备中的模块进行自适应性地改变并且把它们设置在与该实施例不同的一个或多个设备中。可以把实施例中的模块或单元或组件组合成一个模块或单元或组件,以及此外可以把它们分成多个子模块或子单元或子组件。除了这样的特征和/或过程或者单元中的至少一些是相互排斥之外,可以采用任何组合对本说明书(包括伴随的权利要求、摘要和附图)中公开的所有特征以及如此公开的任何方法或者设备的所有过程或单元进行组合。除非另外明确陈述,本说明书(包括伴随的权利要求、摘要和附图)中公开的每个特征可以由提供相同、等同或相似目的的替代特征来代替。Those skilled in the art will understand that the modules in the device in the embodiment can be adaptively changed and arranged in one or more devices different from the embodiment. The modules or units or components in the embodiments may be combined into one module or unit or component, and further they may be divided into multiple sub-modules or sub-units or sub-assemblies. All features disclosed in this specification (including accompanying claims, abstract and drawings) and any method so disclosed may be employed in any combination, unless at least some of such features and/or procedures or elements are mutually exclusive. All processes or units of equipment are combined. Each feature disclosed in this specification (including accompanying claims, abstract and drawings) may be replaced by alternative features serving the same, equivalent or similar purpose, unless expressly stated otherwise.
此外,本领域的技术人员能够理解,尽管在此所述的一些实施例包括其它实施例中所包括的某些特征而不是其它特征,但是不同实施例的特征的组合意味着处于本发明的范围之内并且形成不同的实施例。例如,在权利要求书中,所要求保护的实施例的任意之一都可以以任意的组合方式来使用。Furthermore, those skilled in the art will appreciate that although some of the embodiments described herein include certain features, but not others, included in other embodiments, that combinations of features of different embodiments are intended to be within the scope of the invention within and form different embodiments. For example, in the claims, any of the claimed embodiments may be used in any combination.
本发明的各个部件实施例可以以硬件实现,或者以在一个或者多个处理器上运行的软件模块实现,或者以它们的组合实现。本领域的技术人员应当理解,可以在实践中使用微处理器或者数字信号处理器(DSP)来实现根据本发明实施例中的车载系统的安全防护系统中的一些或者全部部件的一些或者全部功能。本发明还可以实现为用于执行这里所描述的方法的一部分或者全部的设备或者装置程序(例如,计算机程序和计算机程序产品)。这样的实现本发明的程序可以存储在计算机可读介质上,或者可以具有一个或者多个信号的形式。这样的信号可以从因特网网站上下载得到,或者在载体信号上提供,或者以任何其他形式提供。Various component embodiments of the present invention may be implemented in hardware, or in software modules running on one or more processors, or in a combination thereof. Those skilled in the art should understand that a microprocessor or a digital signal processor (DSP) may be used in practice to implement some or all functions of some or all components of the safety protection system of the vehicle-mounted system according to the embodiment of the present invention . The present invention can also be implemented as apparatus or apparatus programs (eg, computer programs and computer program products) for performing part or all of the methods described herein. Such a program implementing the present invention may be stored on a computer-readable medium, or may be in the form of one or more signals. Such signals may be downloaded from Internet sites, or provided on carrier signals, or in any other form.
应该注意的是上述实施例对本发明进行说明而不是对本发明进行限制,并且本领域技术人员在不脱离所附权利要求的范围的情况下可设计出替换实施例。在权利要求中,不应将位于括号之间的任何参考符号构造成对权利要求的限制。单词“包含”不排除存在未列在权利要求中的元件或步骤。位于元件之前的单词“一”或“一个”不排除存在多个这样的元件。本发明可以借助于包括有若干不同元件的硬件以及借助于适当编程的计算机来实现。在列举了若干装置的单元权利要求中,这些装置中的若干个可以是通过同一个硬件项来具体体现。单词第一、第二、以及第三等的使用不表示任何顺序。可将这些单词解释为名称。It should be noted that the above-described embodiments illustrate rather than limit the invention, and that alternative embodiments may be devised by those skilled in the art without departing from the scope of the appended claims. In the claims, any reference signs placed between parentheses shall not be construed as limiting the claim. The word "comprising" does not exclude the presence of elements or steps not listed in a claim. The word "a" or "an" preceding an element does not exclude the presence of a plurality of such elements. The invention can be implemented by means of hardware comprising several different elements and by means of a suitably programmed computer. In a unit claim enumerating several means, several of these means may be embodied by one and the same item of hardware. The use of the words first, second, and third, etc. do not denote any order. These words can be interpreted as names.
本发明公开了:A1.一种车载系统的安全防护方法,包括:The invention discloses: A1. A safety protection method for a vehicle-mounted system, comprising:
安全防护服务端根据获取的漏洞信息生成相应的车机防御策略,并将生成的车机防御策略传递至车辆厂商端;The security protection server generates the corresponding vehicle defense strategy according to the obtained vulnerability information, and transmits the generated vehicle defense strategy to the vehicle manufacturer;
车辆厂商端根据预设的下发规则,为车机终端下发相对应的车机防御策略;The vehicle manufacturer sends the corresponding vehicle defense strategy to the vehicle terminal according to the preset distribution rules;
车机终端利用接收到的车机防御策略进行安全防御。The vehicle-machine terminal uses the received vehicle-machine defense strategy for security defense.
A2.根据A1所述的方法,其中,所述方法还包括:A2. The method according to A1, wherein the method further comprises:
车机终端根据预设的攻击检测策略,对车机终端自身进行攻击检测;若检测到攻击行为,则生成相应的告警信息,并将所述告警信息发送至对应的车辆厂商端;The vehicle terminal performs attack detection on the vehicle terminal itself according to the preset attack detection strategy; if an attack is detected, corresponding alarm information is generated, and the alarm information is sent to the corresponding vehicle manufacturer;
车辆厂商端将接收到的告警信息传递至安全防护服务端。The vehicle manufacturer transmits the received alarm information to the security protection server.
A3.根据A2所述的方法,其中,所述安全防护服务端根据获取的漏洞信息生成相应的车机防御策略进一步包括:A3. The method according to A2, wherein the generation of the corresponding vehicle defense strategy by the security protection server according to the acquired vulnerability information further includes:
安全防护服务端根据车辆厂商端传递的告警信息和/或从预设漏洞库中获取的漏洞信息生成相应的车机防御策略。The security protection server generates a corresponding vehicle-machine defense strategy according to the alarm information transmitted by the vehicle manufacturer and/or the vulnerability information obtained from the preset vulnerability database.
A4.根据A1-A3中任一项所述的方法,其中,所述车机防御策略包括:漏洞检测策略以及相对应的漏洞防御策略。A4. The method according to any one of A1-A3, wherein the vehicle-machine defense strategy includes: a vulnerability detection strategy and a corresponding vulnerability defense strategy.
A5.根据A4所述的方法,其中,所述将生成的车机防御策略传递至车辆厂商端;车辆厂商端根据预设的下发规则,为车机终端下发相对应的车机防御策略;车机终端利用接收到的车机防御策略进行安全防御进一步包括:A5. The method according to A4, wherein the generated vehicle defense strategy is transmitted to the vehicle manufacturer; the vehicle manufacturer issues the corresponding vehicle defense strategy to the vehicle terminal according to a preset issuing rule ; The vehicle-machine terminal uses the received vehicle-machine defense strategy for security defense further including:
安全防护服务端将所述漏洞检测策略传递至车辆厂商端;The security protection server transmits the vulnerability detection strategy to the vehicle manufacturer;
车辆厂商端根据预设的下发规则,将漏洞检测策略下发至对应的车机终端;The vehicle manufacturer sends the vulnerability detection strategy to the corresponding vehicle terminal according to the preset distribution rules;
车机终端根据接收到的漏洞检测策略进行漏洞检测,并将检测结果上报至车辆厂商端。The vehicle terminal performs vulnerability detection according to the received vulnerability detection strategy, and reports the detection results to the vehicle manufacturer.
A6.根据A5所述的方法,其中,所述车辆厂商端根据预设的下发规则,为车机终端下发相对应的车机防御策略进一步包括:车辆厂商端根据预设的下发规则以及接收到的检测结果,为车机终端下发相对应的漏洞防御策略;A6. The method according to A5, wherein, according to the preset issuing rule, the vehicle manufacturer side issues the corresponding vehicle equipment defense strategy to the vehicle equipment terminal further comprising: the vehicle manufacturer side according to the preset delivery rule As well as the received detection results, the corresponding vulnerability defense strategy is issued to the vehicle terminal;
所述车机终端利用接收到的车机防御策略进行安全防御进一步包括:The vehicle-machine terminal utilizing the received vehicle-machine defense strategy for security defense further includes:
车机终端利用接收到的漏洞防御策略进行漏洞防御。The vehicle terminal uses the received vulnerability defense strategy to perform vulnerability defense.
本发明还公开了:B7.一种车载系统的安全防护系统,包括:The invention also discloses: B7. A safety protection system for a vehicle-mounted system, comprising:
安全防护服务端,适于根据获取的漏洞信息生成相应的车机防御策略,并将生成的车机防御策略传递至车辆厂商端;The security protection server is suitable for generating corresponding vehicle and vehicle defense strategies according to the obtained vulnerability information, and transmitting the generated vehicle and vehicle defense strategies to the vehicle manufacturer;
车辆厂商端,适于根据预设的下发规则,为车机终端下发相对应的车机防御策略;The vehicle manufacturer side is suitable for issuing the corresponding vehicle defense strategy to the vehicle terminal according to the preset distribution rules;
车机终端,适于利用接收到的车机防御策略进行安全防御。The vehicle-machine terminal is suitable for security defense by using the received vehicle-machine defense strategy.
B8.根据B7所述的安全防护系统,其中,B8. The safety protection system according to B7, wherein,
所述车机终端进一步适于:根据预设的攻击检测策略,对车机终端自身进行攻击检测;若检测到攻击行为,则生成相应的告警信息,并将所述告警信息发送至对应的车辆厂商端;The in-vehicle terminal is further adapted to: perform attack detection on the in-vehicle terminal itself according to a preset attack detection strategy; if an attack is detected, generate corresponding alarm information, and send the alarm information to the corresponding vehicle manufacturer side;
所述车辆厂商端进一步适于:将接收到的告警信息传递至安全防护服务端。The vehicle manufacturer terminal is further adapted to: transmit the received alarm information to the security protection service terminal.
B9.根据B8所述的安全防护系统,其中,所述安全防护服务端进一步适于:根据车辆厂商端传递的告警信息和/或从预设漏洞库中获取的漏洞信息生成相应的车机防御策略。B9. The security protection system according to B8, wherein the security protection server is further adapted to: generate corresponding vehicle-machine defenses according to the alarm information transmitted by the vehicle manufacturer and/or the vulnerability information obtained from the preset vulnerability library Strategy.
B10.根据B7-B9中任一项所述的安全防护系统,其中,所述车机防御策略包括:漏洞检测策略以及相对应的漏洞防御策略。B10. The security protection system according to any one of B7-B9, wherein the vehicle-machine defense strategy includes: a vulnerability detection strategy and a corresponding vulnerability defense strategy.
B11.根据B10所述的安全防护系统,其中,B11. The safety protection system according to B10, wherein,
所述安全防护服务端进一步适于:将所述漏洞检测策略传递至车辆厂商端;The security protection server is further adapted to: transmit the vulnerability detection strategy to the vehicle manufacturer;
所述车辆厂商端进一步适于:根据预设的下发规则,将漏洞检测策略下发至对应的车机终端;The vehicle manufacturer terminal is further adapted to: deliver the vulnerability detection strategy to the corresponding vehicle terminal according to a preset delivery rule;
所述车机终端进一步适于:根据接收到的漏洞检测策略进行漏洞检测,并将检测结果上报至车辆厂商端。The vehicle terminal is further adapted to: perform vulnerability detection according to the received vulnerability detection strategy, and report the detection result to the vehicle manufacturer.
B12.根据B11所述的安全防护系统,其中,B12. The safety protection system according to B11, wherein,
所述车辆厂商端进一步适于:根据预设的下发规则以及接收到的检测结果,为车机终端下发相对应的漏洞防御策略;The vehicle manufacturer terminal is further adapted to: issue a corresponding vulnerability defense strategy to the vehicle terminal according to the preset issuing rule and the received detection result;
所述车机终端进一步适于:利用接收到的漏洞防御策略进行漏洞防御。The in-vehicle terminal is further adapted to: utilize the received vulnerability defense strategy for vulnerability defense.
本发明还公开了:C13.一种计算设备,包括:处理器、存储器、通信接口和通信总线,所述处理器、所述存储器和所述通信接口通过所述通信总线完成相互间的通信;The present invention also discloses: C13. A computing device, comprising: a processor, a memory, a communication interface and a communication bus, wherein the processor, the memory and the communication interface communicate with each other through the communication bus;
所述存储器用于存放至少一可执行指令,所述可执行指令使所述处理器执行如A1-A6中任一项所述的车载系统的安全防护方法对应的操作。The memory is used to store at least one executable instruction, and the executable instruction causes the processor to perform operations corresponding to the security protection method for an in-vehicle system according to any one of A1-A6.
本发明还公开了:D14.一种计算机存储介质,所述存储介质中存储有至少一可执行指令,所述可执行指令使处理器执行如A1-A6中任一项所述的车载系统的安全防护方法对应的操作。The present invention also discloses: D14. A computer storage medium, wherein at least one executable instruction is stored in the storage medium, and the executable instruction enables a processor to execute the in-vehicle system according to any one of A1-A6. The operation corresponding to the security protection method.
Claims (10)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201811639417.7ACN111444511A (en) | 2018-12-29 | 2018-12-29 | Safety protection method and system for vehicle-mounted system |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201811639417.7ACN111444511A (en) | 2018-12-29 | 2018-12-29 | Safety protection method and system for vehicle-mounted system |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN111444511Atrue CN111444511A (en) | 2020-07-24 |
Family
ID=71626547
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN201811639417.7APendingCN111444511A (en) | 2018-12-29 | 2018-12-29 | Safety protection method and system for vehicle-mounted system |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN111444511A (en) |
Cited By (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN113221106A (en)* | 2021-05-25 | 2021-08-06 | 杭州安恒信息安全技术有限公司 | Vehicle protection method and device and computer readable storage medium |
| CN114157471A (en)* | 2021-11-29 | 2022-03-08 | 阿波罗智联(北京)科技有限公司 | Vehicle abnormity processing method and device, electronic equipment and medium |
| CN114944961A (en)* | 2022-07-01 | 2022-08-26 | 广东瑞普科技股份有限公司 | Network security protection method, device and system and electronic equipment |
Citations (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20050010819A1 (en)* | 2003-02-14 | 2005-01-13 | Williams John Leslie | System and method for generating machine auditable network policies |
| CN101119231A (en)* | 2007-07-19 | 2008-02-06 | 南京联创网络科技有限公司 | Method to centralized manage and automatic download mend of computer security leak base |
| CN103905464A (en)* | 2014-04-21 | 2014-07-02 | 西安电子科技大学 | Network security strategy verification system and method on basis of formalizing method |
| CN106685968A (en)* | 2016-12-29 | 2017-05-17 | 北京安天网络安全技术有限公司 | Automatic vulnerability defense system and method for industrial control equipment |
| CN107547744A (en)* | 2017-08-31 | 2018-01-05 | 广东欧珀移动通信有限公司 | Resource allocation method and Related product |
| CN107634959A (en)* | 2017-09-30 | 2018-01-26 | 北京奇虎科技有限公司 | Vehicle-based protection method, device and system |
- 2018
- 2018-12-29CNCN201811639417.7Apatent/CN111444511A/enactivePending
Patent Citations (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20050010819A1 (en)* | 2003-02-14 | 2005-01-13 | Williams John Leslie | System and method for generating machine auditable network policies |
| CN101119231A (en)* | 2007-07-19 | 2008-02-06 | 南京联创网络科技有限公司 | Method to centralized manage and automatic download mend of computer security leak base |
| CN103905464A (en)* | 2014-04-21 | 2014-07-02 | 西安电子科技大学 | Network security strategy verification system and method on basis of formalizing method |
| CN106685968A (en)* | 2016-12-29 | 2017-05-17 | 北京安天网络安全技术有限公司 | Automatic vulnerability defense system and method for industrial control equipment |
| CN107547744A (en)* | 2017-08-31 | 2018-01-05 | 广东欧珀移动通信有限公司 | Resource allocation method and Related product |
| CN107634959A (en)* | 2017-09-30 | 2018-01-26 | 北京奇虎科技有限公司 | Vehicle-based protection method, device and system |
Cited By (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN113221106A (en)* | 2021-05-25 | 2021-08-06 | 杭州安恒信息安全技术有限公司 | Vehicle protection method and device and computer readable storage medium |
| CN114157471A (en)* | 2021-11-29 | 2022-03-08 | 阿波罗智联(北京)科技有限公司 | Vehicle abnormity processing method and device, electronic equipment and medium |
| CN114944961A (en)* | 2022-07-01 | 2022-08-26 | 广东瑞普科技股份有限公司 | Network security protection method, device and system and electronic equipment |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN107634959B (en) | Vehicle-based protection method, device and system | |
| Kong et al. | Security risk assessment framework for smart car using the attack tree analysis | |
| US12340291B2 (en) | Immutable watermarking for authenticating and verifying AI-generated output | |
| Dibaei et al. | An overview of attacks and defences on intelligent connected vehicles | |
| US10148693B2 (en) | Exploit detection system | |
| CN111447167A (en) | Safety protection method and device for vehicle-mounted system | |
| EP2918057B1 (en) | Methods and nodes for verification of data | |
| US20230336586A1 (en) | System and Method for Surfacing Cyber-Security Threats with a Self-Learning Recommendation Engine | |
| CN105207775B (en) | The read method and device of verification information | |
| CN112653654A (en) | Security monitoring method and device, computer equipment and storage medium | |
| CN112783518A (en) | Vehicle-mounted application containerization isolation framework system based on IPFS and implementation method | |
| CN111444511A (en) | Safety protection method and system for vehicle-mounted system | |
| CN106886211B (en) | Method and device for determining vehicle safety test level | |
| CN112653655A (en) | Automobile safety communication control method and device, computer equipment and storage medium | |
| WO2024002160A1 (en) | Data processing method and apparatus, and electronic device and storage medium | |
| CN110276193B (en) | Risk feature output method, application operation control method, system and device | |
| CN111447166B (en) | Vehicle attack detection method and device | |
| KR20220073657A (en) | Image-based malicious code analysis method and apparatus and artificial intelligence-based endpoint detection and response system using the same | |
| CN112989335A (en) | Automobile protection method, automobile client, cloud server and system | |
| CN112600839A (en) | Method and device for constructing security threat association view based on Internet of vehicles platform | |
| CN117668832B (en) | Verification system and method for cloud primary container defense measures | |
| CN111786938B (en) | Method, system and electronic equipment for preventing malicious resource acquisition | |
| CN112016922A (en) | Information security protection method and equipment applied to blockchain finance and online payment | |
| CN118395412A (en) | Non-inductive man-machine identification safety protection method, device, equipment and medium | |
| Püllen et al. | Ensuring Trustworthy Automated Road Vehicles: A Software Integrity Validation Approach |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| TA01 | Transfer of patent application right | Effective date of registration:20231121 Address after:1739, 17th Floor, 15th Floor, Building 3, No.10 Jiuxianqiao Road, Chaoyang District, Beijing, 100000 Applicant after:Anxinxing (Beijing) Technology Co.,Ltd. Address before:100088 room 112, block D, 28 new street, new street, Xicheng District, Beijing (Desheng Park) Applicant before:BEIJING QIHOO TECHNOLOGY Co.,Ltd. | |
| TA01 | Transfer of patent application right | ||
| RJ01 | Rejection of invention patent application after publication | Application publication date:20200724 | |
| RJ01 | Rejection of invention patent application after publication |