CN111343128A - Network security monitoring equipment and network security monitoring system applied to motor vehicles - Google Patents
Network security monitoring equipment and network security monitoring system applied to motor vehiclesDownload PDFInfo
- Publication number
- CN111343128A CN111343128ACN201811549788.6ACN201811549788ACN111343128ACN 111343128 ACN111343128 ACN 111343128ACN 201811549788 ACN201811549788 ACN 201811549788ACN 111343128 ACN111343128 ACN 111343128A
- Authority
- CN
- China
- Prior art keywords
- network traffic
- network
- module
- motor vehicle
- security monitoring
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H04L63/1425—Traffic logging, e.g. anomaly detection
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H04L63/1416—Event detection, e.g. attack signature detection
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Alarm Systems (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本申请涉及车载设备技术领域,更具体地说,涉及一种应用于机动车辆的网络安全监控设备及网络安全监控系统。The present application relates to the technical field of in-vehicle equipment, and more particularly, to a network security monitoring device and a network security monitoring system applied to motor vehicles.
背景技术Background technique
随着车联网(Internet of Vehicles)技术的不断发展,具有网络互连和以太网等功能的机动车辆不断涌现。With the continuous development of Internet of Vehicles (Internet of Vehicles) technology, motor vehicles with functions such as network interconnection and Ethernet continue to emerge.
但是在实现机动车辆智能化的同时,由于机动车辆网络的开放性,导致机动车辆的网络安全问题也不断出现。特别是近些年来,国内外已经先后出现了多起针对智能联网机动车辆的网络破解和网络攻击事件,在这些网络安全事件中,机动车辆和整车厂却无法对机动车辆的网络使用状况实现有效的监控。However, while realizing the intelligentization of motor vehicles, due to the openness of the motor vehicle network, the network security problems of motor vehicles are also emerging. Especially in recent years, there have been many network cracking and network attack incidents against intelligent networked motor vehicles at home and abroad. In these network security incidents, motor vehicles and OEMs cannot realize the network usage status of motor vehicles effective monitoring.
发明内容SUMMARY OF THE INVENTION
为解决上述技术问题,本申请提供了一种应用于机动车辆的网络安全监控设备及网络安全监控系统,以实现对机动车辆的网络流量报文信息进行监控的目的,进而实现对机动车辆的网络使用状况的有效监控。In order to solve the above technical problems, the present application provides a network security monitoring device and a network security monitoring system applied to a motor vehicle, so as to realize the purpose of monitoring the network traffic message information of the motor vehicle, and then realize the network security monitoring of the motor vehicle. Effective monitoring of usage.
为实现上述技术目的,本申请实施例提供了如下技术方案:To achieve the above technical purpose, the embodiments of the present application provide the following technical solutions:
一种应用于机动车辆的网络安全监控设备,所述应用于机动车辆的车载网络监控设备包括:获取模块、匹配模块和日志模块;其中,A network security monitoring device applied to a motor vehicle, the in-vehicle network monitoring device applied to the motor vehicle includes: an acquisition module, a matching module and a log module; wherein,
所述获取模块,用于获取机动车辆的网络流量报文;The obtaining module is used to obtain the network traffic message of the motor vehicle;
所述匹配模块,用于将获取的所述网络流量报文与预设数据库中存储的预设规则进行匹配,并在所述网络流量报文与所述预设规则匹配一致时,生成包含与所述预设规则匹配一致的网络流量报文信息的预警日志;The matching module is configured to match the acquired network traffic packet with the preset rule stored in the preset database, and when the network traffic packet matches the preset rule, generate a packet containing the same value as the preset rule. The preset rule matches an early warning log of consistent network traffic message information;
所述日志模块,用于存储所述预警日志。The log module is used to store the warning log.
可选的,还包括:人机交互模块,用于根据所述日志模块存储的预警日志,生成安全状态报告。Optionally, it further includes: a human-computer interaction module, configured to generate a security status report according to the warning log stored by the log module.
可选的,所述人机交互模块还用于显示最近生成的安全状态报告;Optionally, the human-computer interaction module is also used to display the recently generated security status report;
或用于根据接收的显示指令,显示与所述显示指令对应的安全状态报告。Or used to display the security status report corresponding to the display instruction according to the received display instruction.
可选的,所述预设规则包括:网络接口规则、入侵检测规则、深度检测规则和应用行为规则中的至少一项。Optionally, the preset rules include: at least one of network interface rules, intrusion detection rules, in-depth detection rules, and application behavior rules.
可选的,所述网络接口规则包括所述网络流量报文的接口地址与预设地址是否一致;Optionally, the network interface rule includes whether the interface address of the network traffic packet is consistent with the preset address;
所述入侵检测规则包括所述网络流量报文是否包含外部入侵行为;The intrusion detection rule includes whether the network traffic packet contains external intrusion behavior;
所述深度检测规则包括组包后的网络流量报文的开放式通信设备互联参考OSI模型的应用层数据是否与深度包检测规则一致;The deep detection rule includes whether the open communication device interconnection of the packetized network traffic message refers to whether the application layer data of the OSI model is consistent with the deep packet detection rule;
所述应用行为规则包括所述网络流量报文中是否包括异常应用行为。The application behavior rule includes whether the network traffic packet includes abnormal application behavior.
可选的,所述匹配模块还用于对与所述网络流量报文进行阻断处理或放行处理。Optionally, the matching module is further configured to block or release the network traffic message.
可选的,所述预设数据库还用于根据接收的规则更新指令,更新所述预设规则。Optionally, the preset database is further configured to update the preset rule according to the received rule update instruction.
一种应用于机动车辆的网络安全监控系统,包括云控制平台和与所述云控制平台无线连接的至少一个应用于机动车辆的网络安全监控设备,所述应用于机动车辆的网络安全监控设备为上述任一项所述的应用于机动车辆的网络安全监控设备;A network security monitoring system applied to a motor vehicle, comprising a cloud control platform and at least one network security monitoring device applied to the motor vehicle wirelessly connected to the cloud control platform, the network security monitoring device applied to the motor vehicle is The network security monitoring device applied to a motor vehicle according to any one of the above;
所述云控制平台用于获取所述应用于机动车辆的网络安全监控设备的获取模块获取的网络流量报文以及与所述网络流量报文对应的标识信息,所述标识信息为获取所述网络流量报文的应用于机动车辆的网络安全监控设备搭载的机动车辆的身份信息,并根据获取的网络流量报文以及所述标识信息生成安全报告信息。The cloud control platform is used to acquire the network traffic message obtained by the acquisition module of the network security monitoring device applied to the motor vehicle and the identification information corresponding to the network traffic message, and the identification information is to obtain the network traffic message. The traffic message is applied to the identity information of the motor vehicle carried by the network security monitoring device of the motor vehicle, and the security report information is generated according to the acquired network traffic message and the identification information.
可选的,所述云控制平台包括:数据存储模块、事件分析模块、审计模块、管理模块和配置模块;其中,Optionally, the cloud control platform includes: a data storage module, an event analysis module, an audit module, a management module and a configuration module; wherein,
所述数据存储模块用于获取所述应用于机动车辆的网络安全监控设备的获取模块获取的网络流量报文,以及与所述网络流量报文对应的标识信息,并判断获取的网络流量报文是否与任意一项所述预设规则匹配一致,如果是,则将与所述预设规则匹配一致的网络流量报文传输给所述审计模块,如果否,则将所述网络流量报文传输给所述事件分析模块;The data storage module is used to acquire the network traffic message obtained by the acquisition module of the network security monitoring device applied to the motor vehicle, and the identification information corresponding to the network traffic message, and determine the acquired network traffic message. Whether it is consistent with any one of the preset rules, if so, transmit the network traffic packets that match the preset rules to the audit module, if not, transmit the network traffic packets to the event analysis module;
所述审计模块用于根据接收的网络流量报文和与所述网络流量报文对应的标识信息进行审计分析,以获得第一安全报告并传输给所述事件分析模块;The audit module is configured to perform audit analysis according to the received network traffic message and the identification information corresponding to the network traffic message, so as to obtain a first security report and transmit it to the event analysis module;
所述事件分析模块用于对接收的网络流量报文和第一安全报告进行统计分析,并在分析结果异常时,生成第二安全报告;The event analysis module is used to perform statistical analysis on the received network traffic message and the first security report, and generate a second security report when the analysis result is abnormal;
所述管理模块用于根据同一标识信息生成的第一安全报告和第二安全报告,生成与所述标识信息对应的预设规则,并向获取与所述标识信息对应的网络流量报文的应用于机动车辆的网络安全监控设备发送更新指令,所述更新指令包含所述管理模块生成的预设规则的更新信息。The management module is configured to generate a preset rule corresponding to the identification information according to the first security report and the second security report generated by the same identification information, and to obtain the application of the network traffic message corresponding to the identification information. An update instruction is sent to the network security monitoring device of the motor vehicle, and the update instruction includes the update information of the preset rule generated by the management module.
从上述技术方案可以看出,本申请实施例提供了一种应用于机动车辆的网络安全监控设备及网络安全监控系统,其中,所述应用于机动车辆的网络安全监控设备对获取的机动车辆的网络流量报文进行预设规则的匹配,并且在当网络流量报文与预设规则匹配一致时,生成预警日志进行预警,以实现对网络流量报文信息进行监控的目的,而网络流量报文记载着搭载该设备的机动车辆的网络使用状态,因此也实现了对机动车辆的网络使用状态的有效监控。It can be seen from the above technical solutions that the embodiments of the present application provide a network security monitoring device applied to a motor vehicle and a network security monitoring system, wherein the network security monitoring device applied to a motor vehicle has an effect on the acquired data of the motor vehicle. The network traffic packets are matched with the preset rules, and when the network traffic packets match the preset rules, an early warning log is generated for early warning, so as to monitor the network traffic packet information. The network usage status of the motor vehicle equipped with the device is recorded, so the effective monitoring of the network usage status of the motor vehicle is also realized.
附图说明Description of drawings
为了更清楚地说明本申请实施例或现有技术中的技术方案,下面将对实施例或现有技术描述中所需要使用的附图作简单地介绍,显而易见地,下面描述中的附图仅仅是本申请的实施例,对于本领域普通技术人员来讲,在不付出创造性劳动的前提下,还可以根据提供的附图获得其他的附图。In order to more clearly illustrate the embodiments of the present application or the technical solutions in the prior art, the following briefly introduces the accompanying drawings required for the description of the embodiments or the prior art. Obviously, the drawings in the following description are only It is an embodiment of the present application. For those of ordinary skill in the art, other drawings can also be obtained according to the provided drawings without any creative effort.
图1为本申请的一个实施例提供的一种应用于机动车辆的网络安全监控设备的结构示意图;1 is a schematic structural diagram of a network security monitoring device applied to a motor vehicle according to an embodiment of the present application;
图2为本申请的另一个实施例提供的一种应用于机动车辆的网络安全监控设备的结构示意图;2 is a schematic structural diagram of a network security monitoring device applied to a motor vehicle according to another embodiment of the present application;
图3为本申请的一个实施例提供的对网络流量报文进行预设规则匹配的流程示意图;3 is a schematic flowchart of performing preset rule matching on network traffic packets according to an embodiment of the present application;
图4为本申请的一个实施例提供的一种应用于机动车辆的网络安全监控系统的结构示意图;4 is a schematic structural diagram of a network security monitoring system applied to a motor vehicle according to an embodiment of the present application;
图5为本申请的另一个实施例提供的一种应用于机动车辆的网络安全监控系统的结构示意图;5 is a schematic structural diagram of a network security monitoring system applied to a motor vehicle according to another embodiment of the present application;
图6为本申请的一个实施例提供的云控制平台对网络流量报文进行处理的流程示意图。FIG. 6 is a schematic flowchart of processing a network traffic packet by a cloud control platform according to an embodiment of the present application.
具体实施方式Detailed ways
下面将结合本申请实施例中的附图,对本申请实施例中的技术方案进行清楚、完整地描述,显然,所描述的实施例仅仅是本申请一部分实施例,而不是全部的实施例。基于本申请中的实施例,本领域普通技术人员在没有做出创造性劳动前提下所获得的所有其他实施例,都属于本申请保护的范围。The technical solutions in the embodiments of the present application will be clearly and completely described below with reference to the drawings in the embodiments of the present application. Obviously, the described embodiments are only a part of the embodiments of the present application, but not all of the embodiments. Based on the embodiments in the present application, all other embodiments obtained by those of ordinary skill in the art without creative efforts shall fall within the protection scope of the present application.
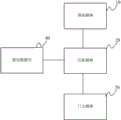
本申请实施例提供了一种应用于机动车辆的网络安全监控设备,如图1所示,包括:获取模块10、匹配模块20和日志模块30;其中,An embodiment of the present application provides a network security monitoring device applied to a motor vehicle, as shown in FIG. 1 , including: an
所述获取模块10,用于获取机动车辆的网络流量报文;The obtaining
所述匹配模块20,用于将获取的所述网络流量报文与预设数据库40中存储的预设规则进行匹配,并在所述网络流量报文与所述预设规则匹配一致时,生成包含与所述预设规则匹配一致的网络流量报文信息的预警日志;The matching
所述日志模块30,用于存储所述预警日志。The
需要说明的是,所述获取模块10获取的网络流量报文包括机动车辆与远程服务提供商(Telemetric Service Provider,TSP)后台通信的所有网络流量报文,以及机动车辆内部的以太网(Ethernet)通信的所有网络流量报文。It should be noted that the network traffic packets acquired by the acquiring
在本实施例中,当获取的网络流量报文与预设规则匹配一致时,则认为该网络流量报文异常,需要生成包含该网络流量报文信息的预警日志进行预警,从而实现对网络流量报文信息进行监控的目的,而网络流量报文记载着搭载该设备的机动车辆的网络使用状态,因此也实现了对机动车辆的网络使用状态的有效监控。In this embodiment, when the acquired network traffic packet matches the preset rule, it is considered that the network traffic packet is abnormal, and an early warning log containing the information of the network traffic packet needs to be generated for early warning, so as to realize the monitoring of network traffic. The purpose of monitoring the message information, and the network traffic message records the network usage status of the motor vehicle equipped with the device, so it also realizes the effective monitoring of the network usage status of the motor vehicle.
还需要说明的是,所述应用于机动车辆的网络安全监控设备可以以机动车辆的车辆联网网关控制单元(如TBOX、Gateway或承担车辆联网功能、中央网关功能的电控单元)为终端载体实现。It should also be noted that the network security monitoring device applied to the motor vehicle can be realized by using the vehicle networking gateway control unit of the motor vehicle (such as TBOX, Gateway or the electronic control unit that undertakes the vehicle networking function and the central gateway function) as the terminal carrier. .
在上述实施例的基础上,在本申请的一个实施例中,如图2所示,所述应用于机动车辆的网络安全监控设备还包括:人机交互模块50,用于根据所述日志模块30存储的预警日志,生成安全状态报告。On the basis of the above-mentioned embodiment, in an embodiment of the present application, as shown in FIG. 2 , the network security monitoring device applied to a motor vehicle further includes: a human-
所述安全状态报告以图形化的方式呈现预警日志的内容,可选的,所述人机交互模块50还用于显示最近生成的安全状态报告;The security status report presents the content of the warning log in a graphical manner, and optionally, the human-
或用于根据接收的显示指令,显示与所述显示指令对应的安全状态报告。Or used to display the security status report corresponding to the display instruction according to the received display instruction.
在本实施例中,当最近生成了一个安全状态报告后,可以通过车载终端的屏幕或仪表盘等显示设备进行该安全状态报告的提示,以提醒驾驶员机动车辆的网络安全的最近动态;另外,驾驶员还可以通过车载系统向人机交互模块50输入显示指令,以使人机交互模块50按照事件、日期等类别进行安全状态报告的显示。In this embodiment, when a security status report is recently generated, a prompt of the security status report can be made through a display device such as a screen or a dashboard of the vehicle terminal, so as to remind the driver of the latest developments in the network security of the motor vehicle; in addition, , the driver can also input a display instruction to the human-
当需要按照事件进行安全状态报告的显示时,所述显示指令中需要携带与事件对应的指令信息;同样的,当需要按照时间进行安全状态报告的显示时,所述显示指令中需要携带与日期对应的指令信息。例如,当驾驶员需要查看9月1日生成的安全状态报告时,需要通过车载系统的触摸屏或按键等输入设备实现包括9月1日这一日期的指令信息的显示指令的输入,以使所述人机交互模块50将9月1日这一日期生成的安全状态报告进行显示。When the security status report needs to be displayed according to the event, the display instruction needs to carry the instruction information corresponding to the event; similarly, when the security status report needs to be displayed according to the time, the display instruction needs to carry the date and time. corresponding command information. For example, when the driver needs to view the safety status report generated on September 1, it is necessary to input the display instruction including the instruction information of the date of September 1 through the input device such as the touch screen or button of the in-vehicle system, so that all The human-
在上述实施例的基础上,在本申请的另一个实施例中,所述预设规则包括:网络接口规则、入侵检测规则、深度检测规则和应用行为规则中的至少一项。On the basis of the above embodiment, in another embodiment of the present application, the preset rule includes at least one of a network interface rule, an intrusion detection rule, a deep detection rule, and an application behavior rule.
其中,可选的,所述网络接口规则包括所述网络流量报文的接口地址与预设地址是否一致;Wherein, optionally, the network interface rule includes whether the interface address of the network traffic packet is consistent with the preset address;
所述入侵检测规则包括所述网络流量报文是否包含外部入侵行为;The intrusion detection rule includes whether the network traffic packet contains external intrusion behavior;
所述深度检测规则包括组包后的网络流量报文的开放式通信设备互联参考OSI模型的应用层数据是否与深度包检测规则一致;The deep detection rule includes whether the open communication device interconnection of the packetized network traffic message refers to whether the application layer data of the OSI model is consistent with the deep packet detection rule;
所述应用行为规则包括所述网络流量报文中是否包括异常应用行为。The application behavior rule includes whether the network traffic packet includes abnormal application behavior.
其中,所述预设地址可以为MAC地址或IP地址等;Wherein, the preset address may be a MAC address or an IP address, etc.;
所述外部入侵行为可以是DOS攻击或端口探测等外部入侵行为;The external intrusion behavior may be an external intrusion behavior such as DOS attack or port detection;
所述深度检测规则主要针对采用Http协议传输数据的网络流量报文进行匹配,对这些类型的网络流量报文进行组包,获取开放式通信设备互联参考(Open SystemInterconnection Reference Model,OSI)模型的应用层的整个数据,根据预设的深度包检测规则进行匹配。The in-depth detection rules are mainly used to match network traffic packets using the Http protocol to transmit data, and package these types of network traffic packets to obtain the application of the Open System Interconnection Reference Model (OSI) model. The entire data of the layer is matched according to the preset deep packet inspection rules.
所述应用行为规则主要用于对异常应用行为进行监控,例如TSP后台发送的车门开启的车控指令的网络流量报文进行监控,当这个网络流量报文符合定义好的异常状态阈值,则认为与应用行为规则匹配一致,输入车辆应用行为层发送网络安全事件。The application behavior rules are mainly used to monitor abnormal application behaviors. For example, the network traffic message of the vehicle control command for door opening sent by the TSP background is monitored. When the network traffic message meets the defined abnormal state threshold, it is considered that Consistent with the application behavior rules, enter the vehicle application behavior layer to send network security events.
在本申请的一个优选实施例中,所述预设规则包括:网络接口规则、入侵检测规则、深度检测规则和应用行为规则。相应的,所述匹配模块20对网络流量报文与预设规则进行匹配的过程参考图3,在本实施例中,对网络流量报文分层进行检测,其中,在网络接口层进行网络流量报文与网络接口规则的匹配,在入侵检测层进行网络流量报文与入侵检测规则的匹配,在深度包检测层进行网络流量报文与深度检测规则的匹配,最后在应用行为层进行网络流量报文与应用行为规则的匹配;其中,应用行为规则存储在应用行为层中。In a preferred embodiment of the present application, the preset rules include: network interface rules, intrusion detection rules, deep detection rules, and application behavior rules. Correspondingly, the process of matching the network traffic packets with the preset rules by the
在上述实施例的基础上,在本申请的又一个实施例中,所述匹配模块20还用于对所述网络流量报文进行阻断处理或放行处理。On the basis of the above embodiment, in another embodiment of the present application, the
在本实施例中,当所述网络流量报文与预设规则匹配一致时,所述匹配模块20除了生成预警日志进行预警之外,还可以根据与预设规则匹配的结果判断是否需要进行阻断处理,例如对于携带有DOS攻击行为或端口探测行为的网络流量报文,需要进行阻断处理,以避免对机动车辆的网络安全造成损害。而在当所述网络流量报文与预设规则匹配不一致时,则需要对网络流量报文进行放行处理,保证车载终端正常的联网功能。In this embodiment, when the network traffic packet matches the preset rule, the
在上述实施例的基础上,在本申请的一个可选实施例中,所述预设数据库40还用于根据接收的规则更新指令,更新所述预设规则。On the basis of the foregoing embodiment, in an optional embodiment of the present application, the
所述规则更新指令可以是用户输入给所述预设数据库40的指令,也可以是云服务器等与应用于机动车辆的网络安全监控设备能够进行通信的设备发送的包含新的预设规则的指令。The rule update instruction may be an instruction input by the user to the
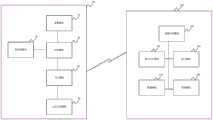
相应的,本申请实施例还提供了一种应用于机动车辆的网络安全监控系统,如图4所示,包括云控制平台200和与所述云控制平台200无线连接的至少一个应用于机动车辆的网络安全监控设备100,所述应用于机动车辆的网络安全监控设备100为上述任一实施例所述的应用于机动车辆的网络安全监控设备100;Correspondingly, an embodiment of the present application also provides a network security monitoring system applied to a motor vehicle, as shown in FIG. 4 , comprising a
所述云控制平台200用于获取所述应用于机动车辆的网络安全监控设备100的获取模块10获取的网络流量报文以及与所述网络流量报文对应的标识信息,所述标识信息为获取所述网络流量报文的应用于机动车辆的网络安全监控设备100搭载的机动车辆的身份信息,并根据获取的网络流量报文以及所述标识信息生成安全报告信息。The
在本实施例中,所述云控制平台200可以综合多个应用于机动车辆的网络安全监控设备100发送的网络流量报文实现分车型、时间、事件类型等的数据分析和统计,以实现对可疑网络流量报文的监控,并感知预测安全发展趋势。In this embodiment, the
在上述实施例的基础上,在本申请的一个可选实施例中,如图5所示,所述云控制平台200包括:数据存储模块210、事件分析模块220、审计模块230、管理模块250和配置模块240;其中,On the basis of the above embodiment, in an optional embodiment of the present application, as shown in FIG. 5 , the
所述数据存储模块210用于获取所述应用于机动车辆的网络安全监控设备100的获取模块10获取的网络流量报文,以及与所述网络流量报文对应的标识信息,并判断获取的网络流量报文是否与任意一项所述预设规则匹配一致,如果是,则将与所述预设规则匹配一致的网络流量报文传输给所述审计模块230,如果否,则将所述网络流量报文传输给所述事件分析模块220;The
所述审计模块230用于根据接收的网络流量报文和与所述网络流量报文对应的标识信息进行审计分析,以获得第一安全报告并传输给所述事件分析模块220;The
所述事件分析模块220用于对接收的网络流量报文和第一安全报告进行统计分析,并在分析结果异常时,生成第二安全报告;The
所述管理模块250用于根据同一标识信息生成的第一安全报告和第二安全报告,生成与所述标识信息对应的预设规则,并向获取与所述标识信息对应的网络流量报文的应用于机动车辆的网络安全监控设备100发送更新指令,所述更新指令包含所述管理模块250生成的预设规则的更新信息。The
具体地,所述数据存储模块210与所述应用于机动车辆的网络安全监控设备100之间的数据传输需要加密进行,以避免数据泄露;所述数据存储模块210负责采集各个应用于机动车辆的网络安全监控设备100的网络流量报文,并进行解密和存储;Specifically, the data transmission between the
所述审计模块230负责对网络流量报文和表示信息进行的审计分析包括根据车型、时间、事件类型、安全等级等进行区分处理,并完成威胁分析和资产评估;例如A车型在B地点,某一个连续的时间段内,受到SYN_Flood类型的洪水DOS攻击,导致车端的网络无法正常进行通信,后台根据定义判断该类事件对用户正常使用车辆产生极大影响即对用户资产存在较大威胁,后台对该安全事件产生相应的安全报表,进行审计分析。The
所述事件分析模块220对网络流量报文和第一安全报告进行的统计分析包括,将审计模块230的处理结果,按照需求以态势感知呈现安全状况,同时监控可疑数据,并感知预测安全发展趋势。其中,态势感知是一种基于环境的、动态、整体地洞悉安全风险的能力,是以安全数据为基础,从全局视角提升对安全威胁的发现识别、理解分析、响应处置能力的一种方式,最终是为了决策与行动,是安全能力的落地。其具体实现形式可以是对所有的车型的网络安全事件按事件类型进行统计,以可视化的图形形式呈现。例如云控制平台200检测某台车联网流量,与该车历史流量非同一数量级或与同一款车型当前流量相比异常不同,则平台态势呈现会有明显大幅变化,同时管理模块250根据事件的安全等级推送相应负责人进行决策处理,最终根据决策结果实现终端车辆预设规则的配置更新,进行终端防御的策略更新。The statistical analysis performed by the
本申请的一个具体实施提供了一种云控制平台对网络流量报文的具体处理过程,如图6所示,首先对解密后的网络流量报文从规则安全事件和可疑事件两方面处理。如为预设规则定义的安全事件,则分车型、时间、地理位置、安全事件类型进行分类处理,进行资产、威胁、稳定性的安全审计分析;A specific implementation of the present application provides a specific process of the cloud control platform for processing network traffic packets. As shown in FIG. 6 , firstly, the decrypted network traffic packets are processed from two aspects: rule security events and suspicious events. If it is a security event defined by preset rules, it will be classified and processed by vehicle type, time, geographic location, and security event type, and security audit analysis of assets, threats, and stability will be performed;
如为预设规则定义的可疑事件,则将可疑事件以态势呈现出车辆整体的网络安全情形,If it is a suspicious event defined by the preset rules, the suspicious event will be presented as a situation to present the overall network security situation of the vehicle.
例如平台检测某台车联网流量,与该车历史流量非同一数量级或与同一款车型当前流量相比异常不同,则在云控制平台200中的态势呈现会有明显大幅变化,同时管理模块250根据事件的安全等级推送相应负责人进行决策处理,最终根据决策结果实现终端车辆预设规则的配置更新,进行终端防御的策略更新。For example, if the platform detects that the traffic of a certain vehicle network is not of the same order of magnitude as the historical traffic of the vehicle or is abnormally different from the current traffic of the same vehicle, the situation in the
综上所述,本申请实施例提供了一种应用于机动车辆的网络安全监控设备100及应用于机动车辆的网络安全监控系统,其中,所述应用于机动车辆的网络安全监控设备100对获取的机动车辆的网络流量报文进行预设规则的匹配,并且在当网络流量报文与预设规则匹配一致时,生成预警日志进行预警,以实现对网络流量报文信息进行监控的目的,而网络流量报文记载着搭载该设备的机动车辆的网络使用状态,因此也实现了对机动车辆的网络使用状态的有效监控。To sum up, the embodiments of the present application provide a network
本说明书所提及的“实施例”或类似用语表示与实施例有关的特性、结构或特征,包括在本发明的至少一实施例中。因此,本说明书所出现的用语“在一实施例中”、“在实施例中”以及类似用语可能但不必然都指向相同实施例。Reference in this specification to an "embodiment" or similar terms refers to a characteristic, structure, or characteristic associated with the embodiment, which is included in at least one embodiment of the present invention. Thus, appearances of the phrases "in an embodiment," "in an embodiment," and similar phrases in this specification may, but do not necessarily, all refer to the same embodiment.
再者,本发明所述特性、结构或特征可以以任何方式结合在一个或多个实施例中。上文中的说明提供了许多特定的细节,比如编程序、软件模块、用户选择、网络交易、数据库查询、数据库结构、硬件模块、硬件电路、硬件芯片等例子,以提供对本发明实施例的了解。然而相关领域的普通技术人员将看出本发明,即使没有利用其中一个或多个特定细节,或利用其它方法、组件、材料等亦可实施。另一方面,为避免混淆本发明,公知的结构、材料或操作并没有详细描述。Furthermore, the described features, structures or characteristics of the present invention may be combined in any manner in one or more embodiments. The above description provides many specific details, such as examples of programming, software modules, user selections, network transactions, database queries, database structures, hardware modules, hardware circuits, hardware chips, etc., to provide an understanding of embodiments of the present invention. One of ordinary skill in the relevant art will recognize, however, that the present invention may be practiced without one or more of the specific details, or with other methods, components, materials, and the like. In other instances, well-known structures, materials, or operations have not been described in detail in order to avoid obscuring the present invention.
本说明书中各个实施例采用递进的方式描述,每个实施例重点说明的都是与其他实施例的不同之处,各个实施例之间相同相似部分互相参见即可。The various embodiments in this specification are described in a progressive manner, and each embodiment focuses on the differences from other embodiments, and the same and similar parts between the various embodiments can be referred to each other.
对所公开的实施例的上述说明,使本领域专业技术人员能够实现或使用本申请。对这些实施例的多种修改对本领域的专业技术人员来说将是显而易见的,本文中所定义的一般原理可以在不脱离本申请的精神或范围的情况下,在其它实施例中实现。因此,本申请将不会被限制于本文所示的这些实施例,而是要符合与本文所公开的原理和新颖特点相一致的最宽的范围。The above description of the disclosed embodiments enables any person skilled in the art to make or use the present application. Various modifications to these embodiments will be readily apparent to those skilled in the art, and the generic principles defined herein may be implemented in other embodiments without departing from the spirit or scope of the present application. Therefore, this application is not intended to be limited to the embodiments shown herein, but is to be accorded the widest scope consistent with the principles and novel features disclosed herein.
Claims (9)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201811549788.6ACN111343128A (en) | 2018-12-18 | 2018-12-18 | Network security monitoring equipment and network security monitoring system applied to motor vehicles |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201811549788.6ACN111343128A (en) | 2018-12-18 | 2018-12-18 | Network security monitoring equipment and network security monitoring system applied to motor vehicles |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN111343128Atrue CN111343128A (en) | 2020-06-26 |
Family
ID=71187911
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN201811549788.6APendingCN111343128A (en) | 2018-12-18 | 2018-12-18 | Network security monitoring equipment and network security monitoring system applied to motor vehicles |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN111343128A (en) |
Cited By (9)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN111865724A (en)* | 2020-07-28 | 2020-10-30 | 公安部第三研究所 | Video surveillance equipment information collection control implementation method |
| CN111885060A (en)* | 2020-07-23 | 2020-11-03 | 上海交通大学 | Non-destructive information security vulnerability detection system and method for Internet of Vehicles |
| CN112104608A (en)* | 2020-08-17 | 2020-12-18 | 华人运通(上海)云计算科技有限公司 | Vehicle information safety protection method, system and storage medium |
| CN114338234A (en)* | 2022-02-28 | 2022-04-12 | 北京经纬恒润科技股份有限公司 | Method and device for processing message |
| CN114867050A (en)* | 2022-04-29 | 2022-08-05 | 中国第一汽车股份有限公司 | A vehicle flow detection method, device, system, equipment and storage medium |
| CN114945148A (en)* | 2021-02-07 | 2022-08-26 | 广州汽车集团股份有限公司 | A kind of vehicle communication terminal information security intrusion detection method and system |
| CN115150782A (en)* | 2022-06-29 | 2022-10-04 | 中国第一汽车股份有限公司 | Service quality monitoring method, device, monitoring platform, server and storage medium for Internet of Vehicles cloud service |
| CN115277061A (en)* | 2022-06-13 | 2022-11-01 | 盈适慧众(上海)信息咨询合伙企业(有限合伙) | Network security service management system and method |
| CN115297141A (en)* | 2022-07-28 | 2022-11-04 | 东风汽车集团股份有限公司 | Vehicle-mounted network IDPS joint defense linkage method and system |
Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN107634959A (en)* | 2017-09-30 | 2018-01-26 | 北京奇虎科技有限公司 | Vehicle-based protection method, device and system |
| CN108173856A (en)* | 2017-12-28 | 2018-06-15 | 北京奇虎科技有限公司 | Vehicle communication data security detection method, device and vehicle terminal |
| US20180262466A1 (en)* | 2017-03-09 | 2018-09-13 | Argus Cyber Security Ltd | System and method for providing cyber security to an in-vehicle network |
| CN108961473A (en)* | 2018-08-07 | 2018-12-07 | 长安大学 | A kind of vehicle-state assessment method for early warning based on intelligent network connection automobile control centre |
- 2018
- 2018-12-18CNCN201811549788.6Apatent/CN111343128A/enactivePending
Patent Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20180262466A1 (en)* | 2017-03-09 | 2018-09-13 | Argus Cyber Security Ltd | System and method for providing cyber security to an in-vehicle network |
| CN107634959A (en)* | 2017-09-30 | 2018-01-26 | 北京奇虎科技有限公司 | Vehicle-based protection method, device and system |
| CN108173856A (en)* | 2017-12-28 | 2018-06-15 | 北京奇虎科技有限公司 | Vehicle communication data security detection method, device and vehicle terminal |
| CN108961473A (en)* | 2018-08-07 | 2018-12-07 | 长安大学 | A kind of vehicle-state assessment method for early warning based on intelligent network connection automobile control centre |
Non-Patent Citations (1)
| Title |
|---|
| 丰斓,李文国: "管理信息系统教程", 《管理信息系统教程》* |
Cited By (13)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN111885060A (en)* | 2020-07-23 | 2020-11-03 | 上海交通大学 | Non-destructive information security vulnerability detection system and method for Internet of Vehicles |
| CN111885060B (en)* | 2020-07-23 | 2021-08-03 | 上海交通大学 | Non-destructive information security vulnerability detection system and method for Internet of Vehicles |
| CN111865724B (en)* | 2020-07-28 | 2022-02-08 | 公安部第三研究所 | Information acquisition control implementation method for video monitoring equipment |
| CN111865724A (en)* | 2020-07-28 | 2020-10-30 | 公安部第三研究所 | Video surveillance equipment information collection control implementation method |
| CN112104608A (en)* | 2020-08-17 | 2020-12-18 | 华人运通(上海)云计算科技有限公司 | Vehicle information safety protection method, system and storage medium |
| CN114945148A (en)* | 2021-02-07 | 2022-08-26 | 广州汽车集团股份有限公司 | A kind of vehicle communication terminal information security intrusion detection method and system |
| CN114338234B (en)* | 2022-02-28 | 2023-07-14 | 北京经纬恒润科技股份有限公司 | A method and device for processing messages |
| CN114338234A (en)* | 2022-02-28 | 2022-04-12 | 北京经纬恒润科技股份有限公司 | Method and device for processing message |
| CN114867050A (en)* | 2022-04-29 | 2022-08-05 | 中国第一汽车股份有限公司 | A vehicle flow detection method, device, system, equipment and storage medium |
| CN114867050B (en)* | 2022-04-29 | 2024-12-27 | 中国第一汽车股份有限公司 | Vehicle flow detection method, device, system, equipment and storage medium |
| CN115277061A (en)* | 2022-06-13 | 2022-11-01 | 盈适慧众(上海)信息咨询合伙企业(有限合伙) | Network security service management system and method |
| CN115150782A (en)* | 2022-06-29 | 2022-10-04 | 中国第一汽车股份有限公司 | Service quality monitoring method, device, monitoring platform, server and storage medium for Internet of Vehicles cloud service |
| CN115297141A (en)* | 2022-07-28 | 2022-11-04 | 东风汽车集团股份有限公司 | Vehicle-mounted network IDPS joint defense linkage method and system |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN111343128A (en) | Network security monitoring equipment and network security monitoring system applied to motor vehicles | |
| EP3588905B1 (en) | Configuring a firewall system in a vehicle network | |
| EP3220605B1 (en) | Method and system for dynamically adapting privacy and security for internet of things (iot) communication | |
| JP7641900B2 (en) | Intrusion route analysis device and intrusion route analysis method | |
| CN110958262A (en) | Ubiquitous Internet of Things security protection gateway system, method and deployment architecture for power industry | |
| CN110610092B (en) | In-vehicle network system, gateway device, and abnormality detection method | |
| KR101327317B1 (en) | Apparatus and method for sap application traffic analysis and monitoring, and the information protection system thereof | |
| CN105991587B (en) | An intrusion detection method and system | |
| CN115147956B (en) | Data processing method, device, electronic equipment and storage medium | |
| CN108111510A (en) | A kind of in-vehicle network intrusion detection method and system | |
| US20090019531A1 (en) | System and method for wireless local area network monitoring and intrusion detection | |
| US20070198529A1 (en) | Management computer and communication system | |
| Ring et al. | Survey on vehicular attacks-building a vulnerability database | |
| CN112738121B (en) | Cryptographic security situational awareness method, apparatus, device and readable storage medium | |
| CN112615858B (en) | Internet of things equipment monitoring method, device and system | |
| CN109076081B (en) | Method for monitoring the safety of a communication connection of a vehicle | |
| JP7428222B2 (en) | In-vehicle security devices, in-vehicle security methods, and security systems | |
| CN113382076A (en) | Internet of things terminal security threat analysis method and protection method | |
| CN117425149A (en) | Wireless network data security management system | |
| EP3562105B1 (en) | System and method for monitoring traffic of applications in a local computing device | |
| CN111277538A (en) | System and method for protecting data security of data exchange process of big data platform | |
| CN115801441A (en) | A security protection system and method for a train communication network | |
| CN112565202A (en) | Internet of things access gateway for video network system | |
| CN113836564B (en) | Block chain-based network-connected automobile information security system | |
| CN103139056A (en) | Secure gateway and network data interactive method |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| TA01 | Transfer of patent application right | Effective date of registration:20221213 Address after:No. 203, Shanghai Songjiang Road, No. 201563, Pudong New Area Applicant after:SAIC Motor Corp.,Ltd. Applicant after:Shanghai automotive industry (Group) Co.,Ltd. Address before:201203 Room 509, Building No. 1, 563 Songtao Road, Zhangjiang High-tech Park, Pudong New Area, Shanghai Applicant before:SAIC Motor Corp.,Ltd. | |
| TA01 | Transfer of patent application right | ||
| RJ01 | Rejection of invention patent application after publication | Application publication date:20200626 | |
| RJ01 | Rejection of invention patent application after publication |