CN111262851A - DDOS attack detection method, device, electronic device and storage medium - Google Patents
DDOS attack detection method, device, electronic device and storage mediumDownload PDFInfo
- Publication number
- CN111262851A CN111262851ACN202010035576.7ACN202010035576ACN111262851ACN 111262851 ACN111262851 ACN 111262851ACN 202010035576 ACN202010035576 ACN 202010035576ACN 111262851 ACN111262851 ACN 111262851A
- Authority
- CN
- China
- Prior art keywords
- target
- suspected
- ddos attack
- traffic
- computing node
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
- 238000001514detection methodMethods0.000titleclaimsabstractdescription79
- 238000000034methodMethods0.000claimsabstractdescription20
- 230000007246mechanismEffects0.000claimsabstractdescription16
- 238000001914filtrationMethods0.000claimsdescription5
- 238000012795verificationMethods0.000claimsdescription5
- 238000010586diagramMethods0.000description12
- 238000004458analytical methodMethods0.000description10
- 230000006870functionEffects0.000description9
- 238000012545processingMethods0.000description7
- 238000004891communicationMethods0.000description6
- 238000012360testing methodMethods0.000description5
- 238000005516engineering processMethods0.000description4
- 239000013598vectorSubstances0.000description4
- 230000005540biological transmissionEffects0.000description3
- 238000004140cleaningMethods0.000description3
- 238000004590computer programMethods0.000description3
- 230000008569processEffects0.000description3
- 238000004422calculation algorithmMethods0.000description2
- 238000004364calculation methodMethods0.000description2
- 238000013100final testMethods0.000description2
- 239000004973liquid crystal related substanceSubstances0.000description2
- 238000012986modificationMethods0.000description2
- 230000004048modificationEffects0.000description2
- 230000002159abnormal effectEffects0.000description1
- 230000000694effectsEffects0.000description1
- 238000000802evaporation-induced self-assemblyMethods0.000description1
- 238000012544monitoring processMethods0.000description1
- 238000010606normalizationMethods0.000description1
- 230000003287optical effectEffects0.000description1
- 230000002093peripheral effectEffects0.000description1
- 238000005070samplingMethods0.000description1
- 238000006467substitution reactionMethods0.000description1
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H04L63/1425—Traffic logging, e.g. anomaly detection
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1441—Countermeasures against malicious traffic
- H04L63/1458—Denial of Service
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明实施例涉及IT应用技术领域,特别涉及一种DDOS攻击检测的方法、装置、电子设备及存储介质。Embodiments of the present invention relate to the technical field of IT applications, and in particular, to a method, an apparatus, an electronic device, and a storage medium for DDOS attack detection.
背景技术Background technique
当前的抗分布式拒绝服务(Distributed Denial of Service,DDOS)系统技术方案,对于来自物联网的DDOS攻击检测,重点分析的是被攻击目标的网络态势。所需的数据来自于路由器吐出的Netflow日志。该日志是被集中收集后再送入检测系统分析,属于DFI(深度流量分析)范畴。检测技术方案为对流进某个IP的报文包数或者报文流量,按照每一分钟为单位建立一个阈值,当发现某一类包数或者流量异常增大,超过阈值,则认为受到了来自物联网的DDOS攻击。当检测到攻击后,需要联动对应的清洗设备,进行引流等方式清洗攻击流量。发明人发现,现有技术方案中阈值的生成方式来自经验,实践证明来自经验生成的阈值存在大量误报和漏报的情况而且不能反映网络流量的时序特性;需要3分钟才能判断是否存在DDOS攻击检测,实时性不强;对低速攻击检测能力低下;需要流量清洗设备,清洗过程会严重影响正常业务;Netflow日志的采样比过高,会导致数据严重失真。The current anti-distributed denial of service (DDOS) system technical solutions, for the detection of DDOS attacks from the Internet of Things, focus on analyzing the network situation of the attacked target. The required data comes from the Netflow logs spit out by the router. The log is collected centrally and then sent to the detection system for analysis, which belongs to the category of DFI (Deep Traffic Analysis). The technical solution for detection is to establish a threshold per minute for the number of packets or packet flow that flows into a certain IP. When the number of packets or traffic of a certain type is found to increase abnormally and exceed the threshold, it is considered to be affected. DDOS attacks from IoT. When an attack is detected, the corresponding cleaning device needs to be linked to clean the attack traffic by diverting traffic. The inventor found that the threshold generation method in the prior art solution comes from experience, and practice has proved that the threshold generated from experience has a large number of false positives and false negatives and cannot reflect the timing characteristics of network traffic; it takes 3 minutes to determine whether there is a DDOS attack. The detection is not real-time; the ability to detect low-speed attacks is low; traffic cleaning equipment is required, and the cleaning process will seriously affect normal services; the sampling ratio of Netflow logs is too high, which will cause serious data distortion.
发明内容SUMMARY OF THE INVENTION
本发明实施方式的目的在于提供一种DDOS攻击检测方法、电子设备、装置及计算机可读存储介质,能够直接在近源端部署计算节点进行检测,而且利用区块链技术实现众计算节点安全可信的通信,对初步检测果进行综合的二次分析形成可靠的最终检测结果,提高检测的可靠性。The purpose of the embodiments of the present invention is to provide a DDOS attack detection method, electronic equipment, device and computer-readable storage medium, which can directly deploy computing nodes at the near-source end for detection, and use blockchain technology to realize the security and reliability of computing nodes. Through the communication of the letter, the comprehensive secondary analysis of the preliminary test results forms a reliable final test result and improves the reliability of the test.
为解决上述技术问题,本发明的实施方式提供了一种DDOS攻击检测方法,所述方法包括:In order to solve the above technical problems, embodiments of the present invention provide a DDOS attack detection method, the method includes:
实时获取单位时间内流经所述计算节点对应的边缘路由器的目标IP的流量数据;Acquiring in real time the traffic data of the target IP flowing through the edge router corresponding to the computing node in a unit time;
获取所述目标IP对应的流量基线模型;Obtain the traffic baseline model corresponding to the target IP;
根据获取的流量数据及所述目标IP对应的流量基线模型,确定单位时间内所述目标IP是否出现疑似DDOS攻击的疑似告警;According to the obtained traffic data and the traffic baseline model corresponding to the target IP, determine whether the target IP has a suspected alarm of a suspected DDOS attack within a unit time;
在确定单位时间内所述目标IP出现疑似告警时,利用所述区块链网络的多个计算节点共享机制,更新所述计算节点维护的疑似告警集合;When a suspected alarm occurs on the target IP within a determined unit time, the set of suspected alarms maintained by the computing node is updated by utilizing the sharing mechanism of multiple computing nodes of the blockchain network;
根据更新后的所述计算节点维护的疑似告警集合,利用预设规则确定所述目标IP的最终DDOS攻击检测结果。According to the updated suspected alarm set maintained by the computing node, a preset rule is used to determine the final DDOS attack detection result of the target IP.
优选地,所述获取所述目标IP对应的流量基线模型包括:Preferably, the obtaining the traffic baseline model corresponding to the target IP includes:
在第一目标时间段内每隔单位时间获取流经所述目标IP的多组流量数据;Acquire multiple groups of traffic data flowing through the target IP every unit time within the first target time period;
归一化所述多组流量数据;normalizing the multiple sets of traffic data;
对归一化的多组流量数据进行聚类,得到所述流量基线模型。The normalized multiple groups of traffic data are clustered to obtain the traffic baseline model.
优选地,所述根据获取的流量数据及所述目标IP对应的流量基线模型,确定单位时间内所述目标IP是否出现疑似DDOS攻击的疑似告警包括:Preferably, according to the obtained traffic data and the traffic baseline model corresponding to the target IP, determining whether the target IP has a suspected alarm of a suspected DDOS attack within a unit time includes:
在获取的流量数据能与所述目标IP对应的流量基线模型聚成一类时,则确定单位时间内所述目标IP没有出现疑似告警;When the obtained traffic data can be grouped with the traffic baseline model corresponding to the target IP, it is determined that no suspected alarm occurs on the target IP within a unit time;
在获取的流量数据不能与所述目标IP对应的流量基线模型聚成一类时,则确定单位时间内所述目标IP出现了疑似告警。When the acquired traffic data cannot be grouped with the traffic baseline model corresponding to the target IP, it is determined that a suspected alarm occurs on the target IP within a unit time.
优选地,所述在确定单位时间内所述目标IP出现疑似告警时,利用所述区块链网络的多个计算节点共享机制,更新所述计算节点维护的疑似告警集合包括:Preferably, when a suspected alarm occurs on the target IP within a certain unit time, using the sharing mechanism of multiple computing nodes of the blockchain network, updating the suspected alarm set maintained by the computing node includes:
广播添加疑似告警请求到所述区块链网络中以使区块链网络中的其他计算节点在其维护的疑似告警集合中添加所述目标IP出现的疑似告警。Broadcasting a request for adding a suspected alarm to the blockchain network, so that other computing nodes in the blockchain network add the suspected alarm that the target IP occurs to the suspected alarm set maintained by the blockchain network.
优选地,所述根据更新后的所述计算节点维护的疑似告警集合,利用预设规则确定所述目标IP的最终DDOS攻击检测结果包括:Preferably, determining the final DDOS attack detection result of the target IP by using a preset rule according to the updated suspected alarm set maintained by the computing node includes:
从所述更新后的所述计算节点维护的疑似告警集合中,获取第二目标时间段内所述目标IP的目标疑似告警集合;From the updated suspected alarm set maintained by the computing node, obtain the target suspected alarm set of the target IP within the second target time period;
计算所述目标疑似告警集合中出现目标协议的次数;calculating the number of times the target protocol appears in the target suspected alarm set;
在计算的次数大于次数阈值时,确定所述目标IP受到DDOS攻击。When the calculated number of times is greater than the number of times threshold, it is determined that the target IP is under DDOS attack.
优选地,所述方法还包括:Preferably, the method further includes:
在确定所述目标IP受到DDOS攻击时,获取发起攻击的源IP;When it is determined that the target IP is under DDOS attack, obtain the source IP that initiates the attack;
根据所述源IP确定所述源IP对应的智能设备是否在所述边缘路由器的管辖范围内;Determine whether the smart device corresponding to the source IP is within the jurisdiction of the edge router according to the source IP;
在所述源IP对应的智能设备在所述边缘路由器的管辖范围内时,向所述边缘路由器发送过滤包含所述源IP及/目标协议的过滤指令。When the smart device corresponding to the source IP is within the jurisdiction of the edge router, a filtering instruction including the source IP and/or the target protocol is sent to the edge router.
优选地,所述方法还包括:Preferably, the method further includes:
在所述区块链网络中的其他计算节点中的任一计算节点出现疑似告警时,接收所述任一计算节点发送的添加疑似告警请求的广播;When a suspected alarm occurs on any one of the other computing nodes in the blockchain network, receiving a broadcast of a request for adding a suspected alarm sent by the any computing node;
验证接收的广播中的添加疑似告警请求;Verify the add suspected alarm request in the received broadcast;
在验证通过后,将接收的广播中的疑似告警添加至所述计算节点维护的疑似告警集合。After the verification is passed, the suspected alarm in the received broadcast is added to the suspected alarm set maintained by the computing node.
为了解决上述问题,本发明还提供一种DDOS攻击检测装置,其特征在于,所述装置包括:In order to solve the above problems, the present invention also provides a DDOS attack detection device, characterized in that the device includes:
流量获取模块,用于实时获取单位时间内流经所述计算节点对应的边缘路由器的目标IP的流量数据;a traffic acquisition module, configured to acquire, in real time, the traffic data of the target IP flowing through the edge router corresponding to the computing node in a unit time;
模型获取模块,用于获取所述目标IP对应的流量基线模型;A model acquisition module, used for acquiring the traffic baseline model corresponding to the target IP;
告警确定模块,用于根据获取的流量数据及所述目标IP对应的流量基线模型,确定单位时间内所述目标IP是否出现疑似DDOS攻击的疑似告警;an alarm determination module, configured to determine whether a suspected alarm of a suspected DDOS attack occurs on the target IP within a unit time according to the obtained traffic data and the traffic baseline model corresponding to the target IP;
更新模块,用于在确定单位时间内所述目标IP出现疑似告警时,利用所述区块链网络的多个计算节点共享机制,更新所述计算节点维护的疑似告警集合;an update module, configured to update the set of suspected alarms maintained by the computing nodes by utilizing the sharing mechanism of multiple computing nodes of the blockchain network when a suspected alarm occurs on the target IP within a certain unit time;
所述告警确定模块还用于根据更新后的所述计算节点维护的疑似告警集合,利用预设规则确定所述目标IP的最终DDOS攻击检测结果。The alarm determination module is further configured to determine the final DDOS attack detection result of the target IP by using a preset rule according to the updated suspected alarm set maintained by the computing node.
为了解决上述问题,本发明还提供一种电子设备,所述电子设备包括:In order to solve the above problems, the present invention also provides an electronic device, the electronic device includes:
存储器,存储至少一个指令;及a memory that stores at least one instruction; and
处理器,执行所述存储器中存储的指令以实现上述所述的DDOS攻击检测方法。The processor executes the instructions stored in the memory to implement the above-mentioned DDOS attack detection method.
为了解决上述问题,本发明还提供一种计算机可读存储介质,所述计算机可读存储介质中存储有至少一个指令,所述至少一个指令被电子设备中的处理器执行以实现上述所述的DDOS攻击检测方法。In order to solve the above problems, the present invention also provides a computer-readable storage medium, where at least one instruction is stored in the computer-readable storage medium, and the at least one instruction is executed by a processor in an electronic device to implement the above-mentioned DDOS attack detection method.
本发明实施例利用实时获取单位时间内流经所述计算节点对应的边缘路由器的目标IP的流量数据;将获取的流量数据及所述目标IP对应的流量基线模型,确定单位时间内所述目标IP初次检测结果,再利用区块链技术实现众计算节点安全可信的通信、在确定单位时间内所述目标IP出现疑似告警时,利用所述区块链网络的多个计算节点共享机制,更新所述计算节点维护的疑似告警集合;根据更新后的所述计算节点维护的疑似告警集合,利用预设规则确定所述目标IP的最终DDOS攻击检测结果,从而实现检测结果共享,对初步检测结果进行综合的二次分析形成可靠的最终检测结果,提高检测的可靠性。In the embodiment of the present invention, the traffic data of the target IP flowing through the edge router corresponding to the computing node in a unit time is obtained in real time; the obtained traffic data and the traffic baseline model corresponding to the target IP are used to determine the target IP in a unit time. IP initial detection results, and then use blockchain technology to achieve secure and credible communication among computing nodes. When a suspected alarm occurs on the target IP within a certain unit time, the sharing mechanism of multiple computing nodes in the blockchain network is used. Update the suspected alarm set maintained by the computing node; according to the updated suspected alarm set maintained by the computing node, use a preset rule to determine the final DDOS attack detection result of the target IP, so as to realize the sharing of detection results, and the preliminary detection The results are subjected to comprehensive secondary analysis to form a reliable final detection result and improve the reliability of the detection.
进一步地,单个计算节点得到了正式的告警,同时可以获得发起攻击的智能设备地址以及产生告警流量对应的协议。计算节点判断发起攻击的智能设备是否在自己所连接的边缘路由器的管辖范围内,如果是,则向连接的边缘路由器发出过滤指令。本实施例在近源检测和近源处置恶意流量,无需专有的处置设备,也无需对正常业务造成影响,成本低、影响小。Further, a single computing node gets a formal alarm, and at the same time, it can obtain the address of the smart device that initiated the attack and the protocol corresponding to the traffic generating the alarm. The computing node determines whether the attacking smart device is within the jurisdiction of the edge router to which it is connected, and if so, sends a filtering instruction to the connected edge router. In this embodiment, near-source detection and near-source processing of malicious traffic do not require dedicated processing equipment, nor do they need to affect normal services, and the cost is low and the impact is small.
附图说明Description of drawings
一个或多个实施例通过与之对应的附图中的图片进行示例性说明,这些示例性说明并不构成对实施例的限定,附图中具有相同参考数字标号的元件表示为类似的元件,除非有特别申明,附图中的图不构成比例限制。One or more embodiments are exemplified by the pictures in the corresponding drawings, and these exemplifications do not constitute limitations of the embodiments, and elements with the same reference numerals in the drawings are denoted as similar elements, Unless otherwise stated, the figures in the accompanying drawings do not constitute a scale limitation.
图1为本发明实施例提供的DDOS攻击检测方法的较佳实施例的应用环境图。FIG. 1 is an application environment diagram of a preferred embodiment of a DDOS attack detection method provided by an embodiment of the present invention.
图2为本发明实施例提供的DDOS攻击检测方法的第一较佳实施例的流程示意图;2 is a schematic flowchart of a first preferred embodiment of a DDOS attack detection method provided by an embodiment of the present invention;
图3为本发明实施例提供的图2中S2的细化流程图。FIG. 3 is a detailed flowchart of S2 in FIG. 2 according to an embodiment of the present invention.
图3a为本发明实施例提供流量基线模型示意图。FIG. 3a is a schematic diagram of a traffic baseline model according to an embodiment of the present invention.
图3b为本发明实施例提供流量数据能与流量基线模型聚成一类示意图。FIG. 3b is a schematic diagram showing that traffic data can be aggregated into a class with a traffic baseline model according to an embodiment of the present invention.
图3c为本发明实施例提供流量数据不能与流量基线模型聚成一类型示意图。FIG. 3c is a schematic diagram of a type provided by an embodiment of the present invention that traffic data cannot be aggregated with a traffic baseline model.
图4为本发明实施例提供的图2中S5的细化流程图。FIG. 4 is a detailed flowchart of S5 in FIG. 2 according to an embodiment of the present invention.
图5为实施例提供的DDOS攻击检测方法的第二较佳实施例的流程示意图。FIG. 5 is a schematic flowchart of a second preferred embodiment of the DDOS attack detection method provided by the embodiment.
图6为本发明实施例提供的DDOS攻击检测装置的模块示意图;6 is a schematic diagram of a module of a DDOS attack detection device provided by an embodiment of the present invention;
图7为本发明实施例提供的实现DDOS攻击检测方法的电子设备的内部结构示意图;7 is a schematic diagram of an internal structure of an electronic device for implementing a DDOS attack detection method provided by an embodiment of the present invention;
本发明目的实现、功能特点及优点将结合实施例,参照附图做进一步说明。The object realization, functional features and advantages of the present invention will be further described with reference to the accompanying drawings in conjunction with the embodiments.
具体实施方式Detailed ways
为使本发明实施例的目的、技术方案和优点更加清楚,下面将结合附图对本发明的各实施方式进行详细的阐述。然而,本领域的普通技术人员可以理解,在本发明各实施方式中,为了使读者更好地理解本申请而提出了许多技术细节。但是,即使没有这些技术细节和基于以下各实施方式的种种变化和修改,也可以实现本申请所要求保护的技术方案。In order to make the objectives, technical solutions and advantages of the embodiments of the present invention clearer, the various embodiments of the present invention will be described in detail below with reference to the accompanying drawings. However, those of ordinary skill in the art can appreciate that, in the various embodiments of the present invention, many technical details are set forth in order for the reader to better understand the present application. However, even without these technical details and various changes and modifications based on the following embodiments, the technical solutions claimed in the present application can be realized.
本发明的实施方式涉及一种分布式拒绝服务(Distributed Denial of Service,DDOS)攻击检测方法,本实施方式的核心在于利用实时获取单位时间内流经所述计算节点对应的边缘路由器的目标IP的流量数据;将获取的流量数据及所述目标IP对应的流量基线模型,确定单位时间内所述目标IP初次检测结果,再利用区块链技术实现众计算节点安全可信的通信、在确定单位时间内所述目标IP出现疑似告警时,利用所述区块链网络的多个计算节点共享机制,更新所述计算节点维护的疑似告警集合;根据更新后的所述计算节点维护的疑似告警集合,利用预设规则确定所述目标IP的最终DDOS攻击检测结果,从而实现检测结果共享,对初步检测结果进行综合的二次分析形成可靠的最终检测结果,提高检测的可靠性。下面对本实施方式的DDOS攻击检测实现细节进行具体的说明,以下内容仅为方便理解提供的实现细节,并非实施本方案的必须。The embodiment of the present invention relates to a distributed denial of service (Distributed Denial of Service, DDOS) attack detection method. Traffic data; the obtained traffic data and the traffic baseline model corresponding to the target IP, determine the initial detection result of the target IP per unit time, and then use the blockchain technology to achieve secure and credible communication between the computing nodes, in the determined unit When a suspected alarm occurs on the target IP within the time period, the multiple computing node sharing mechanism of the blockchain network is used to update the suspected alarm set maintained by the computing node; according to the updated suspected alarm set maintained by the computing node , using preset rules to determine the final DDOS attack detection result of the target IP, so as to realize the sharing of detection results, perform comprehensive secondary analysis on the preliminary detection results to form a reliable final detection result, and improve the reliability of detection. The implementation details of the DDOS attack detection in this embodiment will be specifically described below. The following content is only provided for the convenience of understanding, and is not necessary for implementing this solution.
参阅图1所示,是本发明DDOS攻击检测方法的第一较佳实施例的应用环境示意图。本发明所述DDOS攻击检测方法应用在包括计算节点、边缘路由器、智能设备群的网络架构中。所述计算节点、边缘路由、智能设备群之间通过网络进行通信。Referring to FIG. 1 , it is a schematic diagram of the application environment of the first preferred embodiment of the DDOS attack detection method of the present invention. The DDOS attack detection method of the present invention is applied in a network architecture including computing nodes, edge routers, and intelligent device groups. The computing nodes, edge routers, and intelligent device groups communicate through the network.
一个计算节点对应一个边缘路由器,一个边缘路由器对应一组智能设备群,智能设备群包括多个智能设备。One computing node corresponds to one edge router, one edge router corresponds to a group of smart devices, and the smart device group includes multiple smart devices.
计算节点包括但不限于:服务器、计算机等设备。Computing nodes include but are not limited to: servers, computers and other devices.
智能设备包括但不限于:手机、电脑、穿戴式设备、相机、车载电子设备、摄像机等等接入物联网的电子设备。Smart devices include but are not limited to: mobile phones, computers, wearable devices, cameras, in-vehicle electronic devices, video cameras, and other electronic devices connected to the Internet of Things.
每一个接入物联网智能设备群的边缘路由器,会接上一个监测计算节点。每一个计算节点从对应的边缘路由器分得一个流过该路由器的流量的镜像。如此,每个计算节点可以统计路由器所管辖的所有智能设备产生的流量。Each edge router connected to the IoT smart device group will be connected to a monitoring computing node. Each compute node gets a mirror image of the traffic flowing through that router from the corresponding edge router. In this way, each computing node can count the traffic generated by all smart devices managed by the router.
物联网设备由于业务单一,具有其独特的流量特征。如家用摄像头,除了少量的传输控制协议(Transmission Control Protocol TCP)流量(管理信息)外,大多是用户数据报协议(User Datagram Protocol UDP)流量。所以根据数据包中的传输内容,可归纳出数据特征集合的大小是一定的。同时,物联网设备连接到互联网的IP数都很少,一般不超过10个,这使得使用单个计算节点来统计和分析单个智能设备流向某个目标主机的流量以确定目标IP是否受到DDOS攻击。Due to the single business, IoT devices have their unique traffic characteristics. For example, a home camera, except a small amount of Transmission Control Protocol (Transmission Control Protocol TCP) traffic (management information), is mostly User Datagram Protocol (User Datagram Protocol UDP) traffic. Therefore, according to the transmission content in the data packet, it can be concluded that the size of the data feature set is certain. At the same time, the number of IPs connected to the Internet by IoT devices is very small, generally no more than 10, which makes it possible to use a single computing node to count and analyze the traffic of a single smart device to a target host to determine whether the target IP is under DDOS attack.
参阅图2所示,图2是本发明为本发明实施例提供的DDOS攻击检测方法的第一较佳实施例的流程示意图,该流程示意图应用于计算节点中,根据不同的需求,该流程图中步骤的顺序可以改变,某些步骤可以省略。Referring to FIG. 2, FIG. 2 is a schematic flowchart of a first preferred embodiment of a DDOS attack detection method provided by the present invention. The flowchart is applied to a computing node. According to different requirements, the flowchart The order of the steps can be changed and some steps can be omitted.
以下结合图2,详细阐述所述DDOS攻击检测方法,包括:Below in conjunction with Fig. 2, the described DDOS attack detection method is described in detail, including:
S1、实时获取单位时间内流经所述计算节点对应的边缘路由器的目标IP的流量数据。S1. Acquire in real time the traffic data of the target IP flowing through the edge router corresponding to the computing node in a unit time.
在本发明实施例中,每一个计算节点从对应的边缘路由器分得一个流过该路由器的流量的镜像。因此每个计算节点可以统计路由器所管辖的所有智能设备产生的流量。In the embodiment of the present invention, each computing node obtains a mirror image of the traffic flowing through the router from the corresponding edge router. Therefore, each computing node can count the traffic generated by all smart devices under the jurisdiction of the router.
具体地,计算节点获取单位时间内流经所述计算节点对应的边缘路由器的目标IP的数据包,计算节点以“目的IP和三、四层协议”为单位,从获取的数据包中获取单位时间内流经所述计算节点对应的边缘路由器的目标IP的流量数据。Specifically, the computing node obtains the data packets of the target IP flowing through the edge router corresponding to the computing node within a unit time, and the computing node takes "destination IP and Layer 3 and Layer 4 protocols" as the unit, and obtains the unit from the obtained data packet. The traffic data that flows through the target IP of the edge router corresponding to the computing node within a time.
进一步地,单位时间是统计流量数据的一个时间单位,例如以30秒为一个时间单位等等。在实时获取流量数据时,即每隔一个单位时间就可获取一次数据,从而便于后续能可以实时检测出DDOS攻击,从而提高了时效性。Further, the unit time is a time unit for statistical traffic data, for example, 30 seconds are used as a time unit and so on. When the traffic data is acquired in real time, that is, the data can be acquired once every unit time, so that the subsequent performance can detect the DDOS attack in real time, thereby improving the timeliness.
进一步地,获取的数据包包括,但不限于源IP、流量、包速。获取的流量数据是一个包括流量和包速的二维向量。Further, the acquired data packets include, but are not limited to, source IP, traffic, and packet rate. The acquired traffic data is a two-dimensional vector including traffic and packet rate.
例如某个IP为“23.24.198.22”、协议为“TCP”,得到了一段时间内的每30秒统计一次的特征值,即多个2维向量[流量,包速]。For example, a certain IP is "23.24.198.22" and the protocol is "TCP", and the eigenvalues that are counted every 30 seconds for a period of time are obtained, that is, multiple 2-dimensional vectors [traffic, packet rate].
在该实施例中,直接使用未采样的网络数据包分析,从而提高后续检测的可靠性。In this embodiment, unsampled network data packet analysis is directly used, thereby improving the reliability of subsequent detection.
S2、获取所述目标IP对应的流量基线模型。S2. Acquire a traffic baseline model corresponding to the target IP.
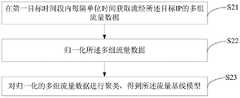
在本发明实施例中,图3为本发明实施例提供的图2中S2的细化流程图。In an embodiment of the present invention, FIG. 3 is a detailed flowchart of S2 in FIG. 2 provided by an embodiment of the present invention.
具体包括:Specifically include:
S21、在第一目标时间段内每隔单位时间获取流经所述目标IP的多组流量数据。S21. Acquire multiple groups of traffic data flowing through the target IP every unit time in the first target time period.
在本发明实施例中,每组流量数据是一个包括流量和包速的二维向量。在第一目标时间段(如2小时)内,获取多组流量数据。In this embodiment of the present invention, each group of traffic data is a two-dimensional vector including traffic and packet rates. During the first target time period (eg, 2 hours), multiple sets of traffic data are acquired.
S22、归一化所述多组流量数据。S22. Normalize the multiple groups of traffic data.
在本发明实施例中,由于每组流量数据的2个维度单位不一样,需要用归一化处理无量纲的二维向量以便于后续的检测计算。In the embodiment of the present invention, since the two dimensional units of each group of flow data are different, it is necessary to use normalization to process a dimensionless two-dimensional vector to facilitate subsequent detection and calculation.
S23、对归一化的多组流量数据进行聚类,得到所述流量基线模型。S23. Clustering the normalized groups of traffic data to obtain the traffic baseline model.
在本发明实施例中,对归一化的多组流量数据进行聚类得到至少一个类别,将包含最多样本数据的类别作为流量基线模型。也就是说包含少数孤立样本的类别。In the embodiment of the present invention, at least one category is obtained by clustering multiple groups of normalized traffic data, and the category containing the most sample data is used as the traffic baseline model. That is, a class that contains a few isolated samples.
如图3a为本发明实施例提供流量基线模型示意图,为排除图3a的右上角的孤立样本类别后的目标IP为“23.24.198.22”的正常态势的流量基线模型。Figure 3a is a schematic diagram of a traffic baseline model according to an embodiment of the present invention, which is a traffic baseline model of a normal situation where the target IP is "23.24.198.22" after excluding the isolated sample category in the upper right corner of Figure 3a.
S3、根据获取的流量数据及所述目标IP对应的流量基线模型,确定单位时间内所述目标IP是否出现疑似DDOS攻击的疑似告警。S3. According to the obtained traffic data and the traffic baseline model corresponding to the target IP, determine whether the target IP has a suspected alarm of a suspected DDOS attack within a unit time.
在本发明实施例中,所述根据获取的流量数据及所述目标IP对应的流量基线模型,确定单位时间内所述目标IP是否出现疑似DDOS攻击的疑似告警包括:In the embodiment of the present invention, according to the obtained traffic data and the traffic baseline model corresponding to the target IP, determining whether the target IP has a suspected alarm of a suspected DDOS attack within a unit time includes:
在获取的流量数据能与所述目标IP对应的流量基线模型聚成一类时,则确定单位时间内所述目标IP没有出现疑似告警;When the obtained traffic data can be grouped with the traffic baseline model corresponding to the target IP, it is determined that no suspected alarm occurs on the target IP within a unit time;
在获取的流量数据不能与所述目标IP对应的流量基线模型聚成一类时,则确定单位时间内所述目标IP出现了疑似告警。When the acquired traffic data cannot be grouped with the traffic baseline model corresponding to the target IP, it is determined that a suspected alarm occurs on the target IP within a unit time.
例如,如图3b为本发明实施例提供流量数据能与流量基线模型聚成一类示意图。将获取的流量数据表示为样本点A,在图3b中样本点A没有被孤立,则表示样本点A表示的流量属于正常流量数据,没有出现疑似告警。For example, as shown in FIG. 3b, it is a schematic diagram that traffic data and a traffic baseline model can be aggregated into one type according to an embodiment of the present invention. The obtained traffic data is represented as sample point A. In Figure 3b, sample point A is not isolated, which means that the traffic represented by sample point A belongs to normal traffic data, and no suspected alarm occurs.
在本发明实施例中,使用了聚类算法进行DDOS攻击的初次检测,可以极大地减少人为经验的干预,提高检测的准确性。In the embodiment of the present invention, the clustering algorithm is used for the initial detection of the DDOS attack, which can greatly reduce the intervention of human experience and improve the detection accuracy.
图3c为本发明实施例提供流量数据不能与流量基线模型聚成一类型示意图。将获取的流量数据表示为样本点A,在图3c中样本点A被孤立,样本点A不能与流量基线模型聚成一类型,则表示样本点A表示的流量不属于正常流量数据,出现疑似告警。FIG. 3c is a schematic diagram of a type provided by an embodiment of the present invention that traffic data cannot be aggregated with a traffic baseline model. The obtained traffic data is represented as sample point A. In Figure 3c, sample point A is isolated, and sample point A cannot be grouped into the same type with the traffic baseline model, which means that the traffic represented by sample point A does not belong to normal traffic data, and a suspected alarm occurs. .
S4、在确定单位时间内所述目标IP出现疑似告警时,利用所述区块链网络的多个计算节点共享机制,更新所述计算节点维护的疑似告警集合。S4. When a suspected alarm occurs on the target IP within a certain unit time, use the sharing mechanism of multiple computing nodes of the blockchain network to update the suspected alarm set maintained by the computing node.
在本发明实施例中,区块链网络中包括多个计算节点,利用区块链共识机制和智能合约实现分布式节点之间安全可信的数据共享分析。单个计算节点发现某个IP有来自智能设备的DDOS攻击告警,只是疑似告警,需要将所有计算节点的初步检测结果整合分析,才能得到最后的检测结果。即单个节点需要共享其他节点的检测结果,才能实现自治。In the embodiment of the present invention, the blockchain network includes multiple computing nodes, and the blockchain consensus mechanism and smart contracts are used to realize safe and reliable data sharing and analysis among distributed nodes. A single computing node finds that a certain IP has a DDOS attack alarm from a smart device, but it is only a suspected alarm. It is necessary to integrate and analyze the preliminary detection results of all computing nodes to obtain the final detection result. That is, a single node needs to share the detection results of other nodes in order to achieve autonomy.
在区块链网络中的智能合约中定义了以IP为单位的疑似告警集合Aip={Vt1,Vt2,Vtn}。其中下标tn是时间戳的含义,Vtn={时间戳,源IP,协议族,30秒内流量总和,30秒内包速总和}。例如,目标IP为“23.24.198.22”的疑似告警集合如:A suspected alarm set Aip = {Vt1 , Vt2 , Vtn } is defined in the smart contract in the blockchain network. The subscript tn is the meaning of the timestamp, and Vtn = {timestamp, source IP, protocol family, total traffic within 30 seconds, total packet rate within 30 seconds}. For example, the set of suspected alarms whose target IP is "23.24.198.22" is as follows:
A23.24.198.22={A23.24.198.22 = {
[1565675160,23.34.56.9,TCP,43254525,3424],[1565675160,23.34.56.9,TCP,43254525,3424],
[1565675190,23.34.56.9,ICMP,27534,563],[1565675190,23.34.56.9,ICMP,27534,563],
[1565675220,23.34.56.1,UDP,768536,24579][1565675220,23.34.56.1,UDP,768536,24579]
}}
在区块链网络中单个计算节点在本地维护一份疑似告警集合Aip。In the blockchain network, a single computing node maintains a suspected alarm set Aip locally.
优选地,在确定单位时间内所述目标IP出现疑似告警时,利用所述区块链网络的多个计算节点共享机制,更新所述计算节点维护的疑似告警集合包括:Preferably, when a suspected alarm occurs on the target IP within a certain unit time, using the sharing mechanism of multiple computing nodes of the blockchain network, updating the suspected alarm set maintained by the computing node includes:
广播添加疑似告警请求到所述区块链网络中以使区块链网络中的其他计算节点在其维护的疑似告警集合中添加所述目标IP出现的疑似告警。Broadcasting a request for adding a suspected alarm to the blockchain network, so that other computing nodes in the blockchain network add the suspected alarm that the target IP occurs to the suspected alarm set maintained by the blockchain network.
具体地,当单个计算节点X通过聚类算法获得疑似告警后,触发智能合约中的添加疑似告警到集合的规则,并广播到全网。在其他节点收到广播后,对添加请求进行验证,验证添加者的数字签名和数据格式。若验证通过,则计算节点X添加该疑似告警到计算节点X在本地维护的集合Aip,同时其他节点也更新其本地集合;若验证不通过,则计算节点X不进行任何更新操作。Specifically, when a single computing node X obtains a suspected alarm through the clustering algorithm, it triggers the rule of adding the suspected alarm to the set in the smart contract, and broadcasts it to the entire network. After other nodes receive the broadcast, the add request is verified, and the digital signature and data format of the adder are verified. If the verification passes, the computing node X adds the suspected alarm to the set Aip maintained locally by the computing node X, and other nodes also update their local sets; if the verification fails, the computing node X does not perform any update operation.
优选地,在其他所述方法还包括:Preferably, the method further comprises:
在所述其他计算节点中的任一计算节点出现疑似告警时,接收所述任一计算节点发送的添加疑似告警请求的广播;When a suspected alarm occurs on any one of the other computing nodes, receiving a broadcast of a request for adding a suspected alarm sent by the any computing node;
验证接收的广播中的添加疑似告警请求;Verify the add suspected alarm request in the received broadcast;
在验证通过后,将接收的广播中的疑似告警添加至所述计算节点维护的疑似告警集合。After the verification is passed, the suspected alarm in the received broadcast is added to the suspected alarm set maintained by the computing node.
同理,在计算计节点在验证所述任一计算节点发送的请求时,也是验证所述任一计算节点数字签名和数据格式。Similarly, when the computing node verifies the request sent by any computing node, it also verifies the digital signature and data format of any computing node.
在上述实施例中,在区块链网络中的单个计算节点受到疑似攻击时,需要将区块链网络中所有计算节点的初步检测结果整合分析,才能得到更新后的疑似告警集合。即单个节点需要共享其他节点的检测结果,才能实现自治,从而提高检测的可靠性。In the above embodiment, when a single computing node in the blockchain network is suspected of being attacked, it is necessary to integrate and analyze the preliminary detection results of all computing nodes in the blockchain network to obtain an updated set of suspected alarms. That is, a single node needs to share the detection results of other nodes in order to achieve autonomy and improve the reliability of detection.
S5、根据更新后的所述计算节点维护的疑似告警集合,利用预设规则确定所述目标IP的最终DDOS攻击检测结果。S5. According to the updated suspected alarm set maintained by the computing node, use a preset rule to determine the final DDOS attack detection result of the target IP.
在本发明实施例中,在智能合约中定义分析疑似告警集合得到DDOS告警的规则。该规则:以某个目标IP的某个协议族为颗粒度,统计在一个时间段里发生异常的次数,该次数超过预先设定的阈值,则认为发生告警。如图4所示,图4为本发明实施例提供的图2中S5的细化流程图。步骤S5具体包括:In the embodiment of the present invention, a rule for analyzing a suspected alarm set to obtain a DDOS alarm is defined in a smart contract. This rule: take a certain protocol family of a target IP as the granularity, count the number of abnormal occurrences in a period of time, if the number of times exceeds the preset threshold, it is considered that an alarm occurs. As shown in FIG. 4 , FIG. 4 is a detailed flowchart of S5 in FIG. 2 according to an embodiment of the present invention. Step S5 specifically includes:
S51、从所述更新后的所述计算节点维护的疑似告警集合中,获取第二目标时间段内所述目标IP的目标疑似告警集合。S51. Acquire a target suspected alarm set of the target IP within the second target time period from the updated suspected alarm set maintained by the computing node.
S52、计算所述目标疑似告警集合中出现目标协议的次数。S52. Calculate the number of times the target protocol appears in the target suspected alarm set.
在本发明实施例中,所述目标协议包括ICMP协议。In this embodiment of the present invention, the target protocol includes an ICMP protocol.
S53、在计算的次数大于次数阈值时,确定所述目标IP受到DDOS攻击。S53. When the calculated times is greater than the times threshold, determine that the target IP is under DDOS attack.
例如,更新后23.24.198.22的目标疑似告警集合如下:For example, the updated target suspected alarm set of 23.24.198.22 is as follows:
[1565675160,23.34.57.1,ICMP,91316521,199931],[1565675160,23.34.57.1,ICMP,91316521,199931],
[1565675160,23.34.56.2,ICMP,92012211,208706],[1565675160,23.34.56.2,ICMP,92012211,208706],
[1565675160,164.34.76.88,TCP,43225,324],[1565675160,164.34.76.88,TCP,43225,324],
[1565675160,23.34.26.9,ICMP,91547018,179915],[1565675160,23.34.26.9,ICMP,91547018,179915],
[1565675160,23.34.36.11,ICMP,89567899,198706],[1565675160,23.34.36.11,ICMP,89567899,198706],
[1565675160,23.34.36.12,ICMP,90612733,181538],[1565675160,23.34.36.12,ICMP,90612733,181538],
[1565675130,164.33.76.18,TCP,23479,132],[1565675130,164.33.76.18,TCP,23479,132],
[1565675100,165.34.56.92,TCP,45279,235][1565675100,165.34.56.92,TCP,45279,235]
在“1565675130-1565675160”的30秒内,出现了5次基于ICMP协议对“23.24.198.22”的疑似DDOS攻击,超过了设定的阈值3次,所以判定产生了正式的DDOS告警。Within 30 seconds of "1565675130-1565675160", there were 5 suspected DDOS attacks on "23.24.198.22" based on the ICMP protocol, which exceeded the set threshold 3 times, so it was determined that a formal DDOS alarm was generated.
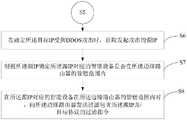
在本实施例中,如图5所示,图5为实施例提供的DDOS攻击检测方法的第二较佳实施例的流程示意图。在S5之后,所述方法还包括:In this embodiment, as shown in FIG. 5 , FIG. 5 is a schematic flowchart of a second preferred embodiment of the DDOS attack detection method provided by the embodiment. After S5, the method further includes:
S6、在确定所述目标IP受到DDOS攻击时,获取发起攻击的源IP。S6. When it is determined that the target IP is under DDOS attack, obtain the source IP that initiates the attack.
在本发明实施例中,从目标疑似告警集合中获取发起攻击的源IP。In this embodiment of the present invention, the source IP that initiates the attack is obtained from the target suspected alarm set.
S7、根据所述源IP确定所述源IP对应的智能设备是否在所述边缘路由器的管辖范围内。S7. Determine, according to the source IP, whether the smart device corresponding to the source IP is within the jurisdiction of the edge router.
S8、在所述源IP对应的智能设备在所述边缘路由器的管辖范围内时,向所述边缘路由器发送过滤包含所述源IP及/目标协议的过滤指令。S8. When the smart device corresponding to the source IP is within the jurisdiction of the edge router, send a filtering instruction including the source IP and/or the target protocol to the edge router.
在该实施例中,单个计算节点得到了正式的告警,同时可以获得发起攻击的智能设备地址以及产生告警流量对应的协议。计算节点判断发起攻击的智能设备是否在自己所连接的边缘路由器的管辖范围内,如果是,则向连接的边缘路由器发出过滤指令。本发明实施例在近源检测和近源处置恶意流量,无需专有的处置设备,也无需对正常业务造成影响,成本低、影响小。In this embodiment, a single computing node gets a formal alarm, and at the same time, it can obtain the address of the smart device that initiated the attack and the protocol corresponding to the traffic generating the alarm. The computing node determines whether the attacking smart device is within the jurisdiction of the edge router to which it is connected, and if so, sends a filtering instruction to the connected edge router. The embodiments of the present invention detect and dispose of malicious traffic near the source, without requiring dedicated processing equipment, and without affecting normal services, with low cost and little impact.
在本发明实施例中,在开始获取数据时,不使用Netflow日志进行分析,直接使用未采样的网络数据包分析,利用众多的分布式节点的计算能力进行精准计算,从而提高了检测的可靠性。In the embodiment of the present invention, when starting to acquire data, the Netflow log is not used for analysis, but the unsampled network data packet is directly used for analysis, and the computing power of many distributed nodes is used for accurate calculation, thereby improving the reliability of detection. .
如图6所示,是本发明DDOS攻击检测装置的功能模块图。As shown in FIG. 6 , it is a functional block diagram of the DDOS attack detection device of the present invention.
本发明所述DDOS攻击检测装置100可以安装于电子设备中。根据实现的功能,所述DDOS攻击检测装置可以包括流量获取模块101、模型获取模块102、告警确定模块103及更新模块104。本发所述模块也可以称之为单元,是指一种能够被电子设备处理器所执行,并且能够完成固定功能的一系列计算机程序段,其存储在电子设备的存储器中。The DDOS
在本实施例中,关于各模块/单元的功能如下:In this embodiment, the functions of each module/unit are as follows:
流量获取模块101,用于实时获取单位时间内流经所述计算节点对应的边缘路由器的目标IP的流量数据;A
模型获取模块102,用于获取所述目标IP对应的流量基线模型;A
告警确定模块103,用于根据获取的流量数据及所述目标IP对应的流量基线模型,确定单位时间内所述目标IP是否出现疑似DDOS攻击的疑似告警;The
更新模块104,用于在确定单位时间内所述目标IP出现疑似告警时,利用所述区块链网络的多个计算节点共享机制,更新所述计算节点维护的疑似告警集合;An
所述告警确定模块103还用于根据更新后的所述计算节点维护的疑似告警集合,利用预设规则确定所述目标IP的最终DDOS攻击检测结果。The
本申请所提供的装置中的模块能够本发明实施例利用实时获取单位时间内流经所述计算节点对应的边缘路由器的目标IP的流量数据;将获取的流量数据及所述目标IP对应的流量基线模型,确定单位时间内所述目标IP初次检测结果,再利用区块链技术实现众计算节点安全可信的通信、在确定单位时间内所述目标IP出现疑似告警时,利用所述区块链网络的多个计算节点共享机制,更新所述计算节点维护的疑似告警集合;根据更新后的所述计算节点维护的疑似告警集合,利用预设规则确定所述目标IP的最终DDOS攻击检测结果,从而实现检测结果共享,对初步检测结果进行综合的二次分析形成可靠的最终检测结果,提高检测的可靠性。其在具体运行时可以取得上述的方法实施例一样的技术效果。The modules in the device provided by the present application can use the embodiment of the present invention to obtain the traffic data of the target IP flowing through the edge router corresponding to the computing node in real time in a unit time; the obtained traffic data and the traffic corresponding to the target IP Baseline model, determine the initial detection result of the target IP within a unit time, and then use blockchain technology to achieve secure and credible communication among computing nodes. The multiple computing nodes of the chain network share a mechanism to update the suspected alarm set maintained by the computing node; according to the updated suspected alarm set maintained by the computing node, use preset rules to determine the final DDOS attack detection result of the target IP , so as to realize the sharing of test results, conduct a comprehensive secondary analysis of the preliminary test results to form a reliable final test result, and improve the reliability of the test. It can achieve the same technical effects as the above-mentioned method embodiments during specific operation.
如图7所示,是本发明实现DDOS攻击检测方法的电子设备的结构示意图。As shown in FIG. 7 , it is a schematic structural diagram of an electronic device implementing the DDOS attack detection method according to the present invention.
所述电子设备1可以包括处理器10、存储器11和总线,还可以包括存储在所述存储器11中并可在所述处理器10上运行的计算机程序,如DDOS攻击检测程序12。所述电子设备1中安装有Web应用的Web防火墙。The electronic device 1 may include a processor 10, a memory 11 and a bus, and may also include a computer program stored in the memory 11 and executable on the processor 10, such as a DDOS attack detection program 12. A web firewall for web applications is installed in the electronic device 1 .
其中,所述存储器11至少包括一种类型的可读存储介质,所述可读存储介质包括闪存、移动硬盘、多媒体卡、卡型存储器(例如:SD或DX存储器等)、磁性存储器、磁盘、光盘等。所述存储器11在一些实施例中可以是电子设备1的内部存储单元,例如该电子设备1的移动硬盘。所述存储器11在另一些实施例中也可以是电子设备1的外部存储设备,例如电子设备1上配备的插接式移动硬盘、智能存储卡(Smart Media Card,SMC)、安全数字(SecureDigital,SD)卡、闪存卡(Flash Card)等。进一步地,所述存储器11还可以既包括电子设备1的内部存储单元也包括外部存储设备。所述存储器11不仅可以用于存储安装于电子设备1的应用软件及各类数据,例如DDOS攻击检测程序的代码等,还可以用于暂时地存储已经输出或者将要输出的数据。Wherein, the memory 11 includes at least one type of readable storage medium, and the readable storage medium includes flash memory, mobile hard disk, multimedia card, card-type memory (for example: SD or DX memory, etc.), magnetic memory, magnetic disk, CD etc. The memory 11 may be an internal storage unit of the electronic device 1 in some embodiments, such as a mobile hard disk of the electronic device 1 . In other embodiments, the memory 11 may also be an external storage device of the electronic device 1, such as a pluggable mobile hard disk, a smart memory card (Smart Media Card, SMC), a secure digital (Secure Digital, SD) card, flash memory card (Flash Card), etc. Further, the memory 11 may also include both an internal storage unit of the electronic device 1 and an external storage device. The memory 11 can not only be used to store application software installed in the electronic device 1 and various data, such as the code of a DDOS attack detection program, etc., but also can be used to temporarily store data that has been output or will be output.
所述处理器10在一些实施例中可以由集成电路组成,例如可以由单个封装的集成电路所组成,也可以是由多个相同功能或不同功能封装的集成电路所组成,包括一个或者多个中央处理器(Central Processing unit,CPU)、微处理器、数字处理芯片、图形处理器及各种控制芯片的组合等。所述处理器10是所述电子设备的控制核心(Control Unit),利用各种接口和线路连接整个电子设备的各个部件,通过运行或执行存储在所述存储器11内的程序或者模块(例如执行DDOS攻击检测程序等),以及调用存储在所述存储器11内的数据,以执行电子设备1的各种功能和处理数据。In some embodiments, the processor 10 may be composed of integrated circuits, for example, may be composed of a single packaged integrated circuit, or may be composed of multiple integrated circuits packaged with the same function or different functions, including one or more integrated circuits. Central processing unit (Central Processing Unit, CPU), microprocessor, digital processing chip, graphics processor and combination of various control chips, etc. The processor 10 is the control core (Control Unit) of the electronic device, and uses various interfaces and lines to connect various components of the entire electronic device, and by running or executing the program or module (for example, executing the program) stored in the memory 11. DDOS attack detection program, etc.), and call the data stored in the memory 11 to execute various functions of the electronic device 1 and process data.
所述总线可以是外设部件互连标准(peripheral component interconnect,简称PCI)总线或扩展工业标准结构(extended industry standard architecture,简称EISA)总线等。该总线可以分为地址总线、数据总线、控制总线等。所述总线被设置为实现所述存储器11以及至少一个处理器10等之间的连接通信。The bus may be a peripheral component interconnect (PCI for short) bus or an extended industry standard architecture (extended industry standard architecture, EISA for short) bus or the like. The bus can be divided into address bus, data bus, control bus and so on. The bus is configured to implement connection communication between the memory 11 and at least one processor 10 and the like.
图7仅示出了具有部件的电子设备,本领域技术人员可以理解的是,图7示出的结构并不构成对所述电子设备1的限定,可以包括比图示更少或者更多的部件,或者组合某些部件,或者不同的部件布置。FIG. 7 only shows an electronic device with components. Those skilled in the art can understand that the structure shown in FIG. 7 does not constitute a limitation on the electronic device 1, and may include fewer or more components than those shown in the drawings. components, or a combination of certain components, or a different arrangement of components.
例如,尽管未示出,所述电子设备1还可以包括给各个部件供电的电源(比如电池),优选地,电源可以通过电源管理装置与所述至少一个处理器10逻辑相连,从而通过电源管理装置实现充电管理、放电管理、以及功耗管理等功能。电源还可以包括一个或一个以上的直流或交流电源、再充电装置、电源故障检测电路、电源转换器或者逆变器、电源状态指示器等任意组件。所述电子设备1还可以包括多种传感器、蓝牙模块、Wi-Fi模块等,在此不再赘述。For example, although not shown, the electronic device 1 may also include a power supply (such as a battery) for powering the various components, preferably, the power supply may be logically connected to the at least one processor 10 through a power management device, so that the power management The device implements functions such as charge management, discharge management, and power consumption management. The power source may also include one or more DC or AC power sources, recharging devices, power failure detection circuits, power converters or inverters, power status indicators, and any other components. The electronic device 1 may further include various sensors, Bluetooth modules, Wi-Fi modules, etc., which will not be repeated here.
进一步地,所述电子设备1还可以包括网络接口,可选地,所述网络接口可以包括有线接口和/或无线接口(如WI-FI接口、蓝牙接口等),通常用于在该电子设备1与其他电子设备之间建立通信连接。Further, the electronic device 1 may also include a network interface, optionally, the network interface may include a wired interface and/or a wireless interface (such as a WI-FI interface, a Bluetooth interface, etc.), which is usually used in the electronic device 1 Establish a communication connection with other electronic devices.
可选地,该电子设备1还可以包括用户接口,用户接口可以是显示器(Display)、输入单元(比如键盘(Keyboard)),可选地,用户接口还可以是标准的有线接口、无线接口。可选地,在一些实施例中,显示器可以是LED显示器、液晶显示器、触控式液晶显示器以及OLED(Organic Light-Emitting Diode,有机发光二极管)触摸器等。其中,显示器也可以适当的称为显示屏或显示单元,用于显示在电子设备1中处理的信息以及用于显示可视化的用户界面。Optionally, the electronic device 1 may further include a user interface, and the user interface may be a display (Display), an input unit (eg, a keyboard (Keyboard)), optionally, the user interface may also be a standard wired interface or a wireless interface. Optionally, in some embodiments, the display may be an LED display, a liquid crystal display, a touch-sensitive liquid crystal display, an OLED (Organic Light-Emitting Diode, organic light-emitting diode) touch device, and the like. The display may also be appropriately called a display screen or a display unit, which is used for displaying information processed in the electronic device 1 and for displaying a visualized user interface.
应该了解,所述实施例仅为说明之用,在专利申请范围上并不受此结构的限制。It should be understood that the embodiments are only used for illustration, and are not limited by this structure in the scope of the patent application.
所述电子设备1中的所述存储器11存储的请求DDOS攻击检测程序12是多个指令的组合,在所述处理器10中运行时,可以实现:The request DDOS attack detection program 12 stored in the memory 11 of the electronic device 1 is a combination of multiple instructions, and when running in the processor 10, it can realize:
实时获取单位时间内流经所述计算节点对应的边缘路由器的目标IP的流量数据;Acquiring in real time the traffic data of the target IP flowing through the edge router corresponding to the computing node in a unit time;
获取所述目标IP对应的流量基线模型;Obtain the traffic baseline model corresponding to the target IP;
根据获取的流量数据及所述目标IP对应的流量基线模型,确定单位时间内所述目标IP是否出现疑似DDOS攻击的疑似告警;According to the obtained traffic data and the traffic baseline model corresponding to the target IP, determine whether the target IP has a suspected alarm of a suspected DDOS attack within a unit time;
在确定单位时间内所述目标IP出现疑似告警时,利用所述区块链网络的多个计算节点共享机制,更新所述计算节点维护的疑似告警集合;When a suspected alarm occurs on the target IP within a determined unit time, the set of suspected alarms maintained by the computing node is updated by utilizing the sharing mechanism of multiple computing nodes of the blockchain network;
根据更新后的所述计算节点维护的疑似告警集合,利用预设规则确定所述目标IP的最终DDOS攻击检测结果。According to the updated suspected alarm set maintained by the computing node, a preset rule is used to determine the final DDOS attack detection result of the target IP.
具体地,所述处理器11对上述指令的具体实现方法对应实施例中相关步骤的描述,在此不赘述。Specifically, the specific implementation method of the above instruction by the processor 11 corresponds to the description of the relevant steps in the embodiment, and is not repeated here.
进一步地,所述电子设备1集成的模块/单元如果以软件功能单元的形式实现并作为独立的产品销售或使用时,可以存储在一个计算机可读取存储介质中。所述计算机可读介质可以包括:能够携带所述计算机程序代码的任何实体或装置、记录介质、U盘、移动硬盘、磁碟、光盘、计算机存储器、只读存储器(ROM,Read-Only Memory)。Further, if the modules/units integrated in the electronic device 1 are implemented in the form of software functional units and sold or used as independent products, they may be stored in a computer-readable storage medium. The computer-readable medium may include: any entity or device capable of carrying the computer program code, a recording medium, a U disk, a removable hard disk, a magnetic disk, an optical disk, a computer memory, a read-only memory (ROM, Read-Only Memory) .
所述计算机可读存储介质上存储有请求DDOS攻击检测程序,所述请求DDOS攻击检测程序可被一个或多个处理器执行,以实现如下操作:A request DDOS attack detection program is stored on the computer-readable storage medium, and the requested DDOS attack detection program can be executed by one or more processors to achieve the following operations:
实时获取单位时间内流经所述计算节点对应的边缘路由器的目标IP的流量数据;Acquiring in real time the traffic data of the target IP flowing through the edge router corresponding to the computing node in a unit time;
获取所述目标IP对应的流量基线模型;Obtain the traffic baseline model corresponding to the target IP;
根据获取的流量数据及所述目标IP对应的流量基线模型,确定单位时间内所述目标IP是否出现疑似DDOS攻击的疑似告警;According to the obtained traffic data and the traffic baseline model corresponding to the target IP, determine whether the target IP has a suspected alarm of a suspected DDOS attack within a unit time;
在确定单位时间内所述目标IP出现疑似告警时,利用所述区块链网络的多个计算节点共享机制,更新所述计算节点维护的疑似告警集合;When a suspected alarm occurs on the target IP within a determined unit time, the set of suspected alarms maintained by the computing node is updated by utilizing the sharing mechanism of multiple computing nodes of the blockchain network;
根据更新后的所述计算节点维护的疑似告警集合,利用预设规则确定所述目标IP的最终DDOS攻击检测结果。According to the updated suspected alarm set maintained by the computing node, a preset rule is used to determine the final DDOS attack detection result of the target IP.
在本发明所提供的几个实施例中,应该理解到,所揭露的设备,装置和方法,可以通过其它的方式实现。例如,以上所描述的装置实施例仅仅是示意性的,例如,所述模块的划分,仅仅为一种逻辑功能划分,实际实现时可以有另外的划分方式。In the several embodiments provided by the present invention, it should be understood that the disclosed apparatus, apparatus and method may be implemented in other manners. For example, the apparatus embodiments described above are only illustrative. For example, the division of the modules is only a logical function division, and there may be other division manners in actual implementation.
所述作为分离部件说明的模块可以是或者也可以不是物理上分开的,作为模块显示的部件可以是或者也可以不是物理单元,即可以位于一个地方,或者也可以分布到多个网络单元上。可以根据实际的需要选择其中的部分或者全部模块来实现本实施例方案的目的。The modules described as separate components may or may not be physically separated, and components shown as modules may or may not be physical units, that is, may be located in one place, or may be distributed to multiple network units. Some or all of the modules may be selected according to actual needs to achieve the purpose of the solution in this embodiment.
另外,在本发明各个实施例中的各功能模块可以集成在一个处理单元中,也可以是各个单元单独物理存在,也可以两个或两个以上单元集成在一个单元中。上述集成的单元既可以采用硬件的形式实现,也可以采用硬件加软件功能模块的形式实现。In addition, each functional module in each embodiment of the present invention may be integrated into one processing unit, or each unit may exist physically alone, or two or more units may be integrated into one unit. The above-mentioned integrated units can be implemented in the form of hardware, or can be implemented in the form of hardware plus software function modules.
对于本领域技术人员而言,显然本发明不限于上述示范性实施例的细节,而且在不背离本发明的精神或基本特征的情况下,能够以其他的具体形式实现本发明。It will be apparent to those skilled in the art that the present invention is not limited to the details of the above-described exemplary embodiments, but that the present invention may be embodied in other specific forms without departing from the spirit or essential characteristics of the invention.
因此,无论从哪一点来看,均应将实施例看作是示范性的,而且是非限制性的,本发明的范围由所附权利要求而不是上述说明限定,因此旨在将落在权利要求的等同要件的含义和范围内的所有变化涵括在本发明内。不应将权利要求中的任何附关联图标记视为限制所涉及的权利要求。Therefore, the embodiments are to be regarded in all respects as illustrative and not restrictive, and the scope of the invention is to be defined by the appended claims rather than the foregoing description, which are therefore intended to fall within the scope of the claims. All changes within the meaning and range of the equivalents of , are included in the present invention. Any reference signs in the claims shall not be construed as limiting the involved claim.
此外,显然“包括”一词不排除其他单元或步骤,单数不排除复数。系统权利要求中陈述的多个单元或装置也可以由一个单元或装置通过软件或者硬件来实现。第二等词语用来表示名称,而并不表示任何特定的顺序。Furthermore, it is clear that the word "comprising" does not exclude other units or steps and the singular does not exclude the plural. Several units or means recited in the system claims can also be realized by one unit or means by means of software or hardware. Second-class terms are used to denote names and do not denote any particular order.
最后应说明的是,以上实施例仅用以说明本发明的技术方案而非限制,尽管参照较佳实施例对本发明进行了详细说明,本领域的普通技术人员应当理解,可以对本发明的技术方案进行修改或等同替换,而不脱离本发明技术方案的精神和范围。Finally, it should be noted that the above embodiments are only used to illustrate the technical solutions of the present invention and not to limit them. Although the present invention has been described in detail with reference to the preferred embodiments, those of ordinary skill in the art should understand that the technical solutions of the present invention can be Modifications or equivalent substitutions can be made without departing from the spirit and scope of the technical solutions of the present invention.
Claims (10)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202010035576.7ACN111262851A (en) | 2020-01-14 | 2020-01-14 | DDOS attack detection method, device, electronic device and storage medium |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202010035576.7ACN111262851A (en) | 2020-01-14 | 2020-01-14 | DDOS attack detection method, device, electronic device and storage medium |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN111262851Atrue CN111262851A (en) | 2020-06-09 |
Family
ID=70952139
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202010035576.7APendingCN111262851A (en) | 2020-01-14 | 2020-01-14 | DDOS attack detection method, device, electronic device and storage medium |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN111262851A (en) |
Cited By (12)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN111917774A (en)* | 2020-07-31 | 2020-11-10 | 平安科技(深圳)有限公司 | Anti-attack method and device for block chain, electronic equipment and medium |
| CN111988306A (en)* | 2020-08-17 | 2020-11-24 | 北京邮电大学 | Method and system for detecting DDoS attack traffic in network based on variational Bayes |
| CN112202771A (en)* | 2020-09-29 | 2021-01-08 | 中移(杭州)信息技术有限公司 | Network flow detection method, system, electronic device and storage medium |
| CN112261019A (en)* | 2020-10-13 | 2021-01-22 | 中移(杭州)信息技术有限公司 | Distributed denial of service attack detection method, device and storage medium |
| CN112887332A (en)* | 2021-03-01 | 2021-06-01 | 山西警察学院 | DDOS attack detection method under cloud environment |
| CN113067804A (en)* | 2021-03-15 | 2021-07-02 | 腾讯科技(深圳)有限公司 | Network attack detection method and device, electronic equipment and storage medium |
| CN114338067A (en)* | 2020-10-09 | 2022-04-12 | 中国移动通信有限公司研究院 | DDoS detection method, device and detection node |
| CN114615002A (en)* | 2020-12-03 | 2022-06-10 | 中国移动通信集团设计院有限公司 | Operator key infrastructure controlled identification method and system |
| CN114745142A (en)* | 2020-12-23 | 2022-07-12 | 腾讯科技(深圳)有限公司 | Abnormal flow processing method and device, computer equipment and storage medium |
| CN115426120A (en)* | 2021-05-14 | 2022-12-02 | 中国移动通信集团浙江有限公司 | Flow data detection method, device and storage medium |
| CN115499230A (en)* | 2022-09-23 | 2022-12-20 | 天翼安全科技有限公司 | Network attack detection method and device, equipment and storage medium |
| CN119599681A (en)* | 2025-02-08 | 2025-03-11 | 四川万网鑫成信息科技有限公司 | Automobile financial transaction safety management method, system and equipment based on blockchain technology |
Citations (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN105262730A (en)* | 2015-09-14 | 2016-01-20 | 北京华青融天技术有限责任公司 | Monitoring method and device based on enterprise domain name safety |
| CN108616534A (en)* | 2018-04-28 | 2018-10-02 | 中国科学院信息工程研究所 | A kind of method and system for protecting internet of things equipment ddos attack based on block chain |
- 2020
- 2020-01-14CNCN202010035576.7Apatent/CN111262851A/enactivePending
Patent Citations (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN105262730A (en)* | 2015-09-14 | 2016-01-20 | 北京华青融天技术有限责任公司 | Monitoring method and device based on enterprise domain name safety |
| CN108616534A (en)* | 2018-04-28 | 2018-10-02 | 中国科学院信息工程研究所 | A kind of method and system for protecting internet of things equipment ddos attack based on block chain |
Cited By (15)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN111917774A (en)* | 2020-07-31 | 2020-11-10 | 平安科技(深圳)有限公司 | Anti-attack method and device for block chain, electronic equipment and medium |
| CN111988306B (en)* | 2020-08-17 | 2021-08-24 | 北京邮电大学 | Intranet DDoS attack traffic detection method and system based on variational Bayes |
| CN111988306A (en)* | 2020-08-17 | 2020-11-24 | 北京邮电大学 | Method and system for detecting DDoS attack traffic in network based on variational Bayes |
| CN112202771A (en)* | 2020-09-29 | 2021-01-08 | 中移(杭州)信息技术有限公司 | Network flow detection method, system, electronic device and storage medium |
| CN114338067A (en)* | 2020-10-09 | 2022-04-12 | 中国移动通信有限公司研究院 | DDoS detection method, device and detection node |
| CN112261019A (en)* | 2020-10-13 | 2021-01-22 | 中移(杭州)信息技术有限公司 | Distributed denial of service attack detection method, device and storage medium |
| CN114615002A (en)* | 2020-12-03 | 2022-06-10 | 中国移动通信集团设计院有限公司 | Operator key infrastructure controlled identification method and system |
| CN114615002B (en)* | 2020-12-03 | 2024-02-27 | 中国移动通信集团设计院有限公司 | Controlled identification method and system for key infrastructure of operator |
| CN114745142A (en)* | 2020-12-23 | 2022-07-12 | 腾讯科技(深圳)有限公司 | Abnormal flow processing method and device, computer equipment and storage medium |
| CN114745142B (en)* | 2020-12-23 | 2023-11-24 | 腾讯科技(深圳)有限公司 | Abnormal flow processing method and device, computer equipment and storage medium |
| CN112887332A (en)* | 2021-03-01 | 2021-06-01 | 山西警察学院 | DDOS attack detection method under cloud environment |
| CN113067804A (en)* | 2021-03-15 | 2021-07-02 | 腾讯科技(深圳)有限公司 | Network attack detection method and device, electronic equipment and storage medium |
| CN115426120A (en)* | 2021-05-14 | 2022-12-02 | 中国移动通信集团浙江有限公司 | Flow data detection method, device and storage medium |
| CN115499230A (en)* | 2022-09-23 | 2022-12-20 | 天翼安全科技有限公司 | Network attack detection method and device, equipment and storage medium |
| CN119599681A (en)* | 2025-02-08 | 2025-03-11 | 四川万网鑫成信息科技有限公司 | Automobile financial transaction safety management method, system and equipment based on blockchain technology |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN111262851A (en) | DDOS attack detection method, device, electronic device and storage medium | |
| US11429625B2 (en) | Query engine for remote endpoint information retrieval | |
| US11070569B2 (en) | Detecting outlier pairs of scanned ports | |
| CN109962891B (en) | Method, apparatus, device and computer storage medium for monitoring cloud security | |
| CN108429651B (en) | Flow data detection method and device, electronic equipment and computer readable medium | |
| CN112448947B (en) | Network anomaly determination method, equipment and storage medium | |
| US20210400073A1 (en) | Malicious port scan detection using source profiles | |
| US11711389B2 (en) | Scanner probe detection | |
| US11770396B2 (en) | Port scan detection using destination profiles | |
| US20220217162A1 (en) | Malicious port scan detection using port profiles | |
| JP2019021294A (en) | SYSTEM AND METHOD OF DETERMINING DDoS ATTACKS | |
| CN116074075A (en) | Method, system and device for analyzing security event correlation behavior based on correlation rules | |
| CN115589310A (en) | Attack detection method, device and related equipment | |
| CN113765850B (en) | Internet of things abnormality detection method and device, computing equipment and computer storage medium | |
| EP3918762B1 (en) | Port scan detection | |
| WO2025175877A1 (en) | Indicator of compromise extraction method and apparatus, medium, and electronic device | |
| EP4274160A1 (en) | System and method for machine learning based malware detection | |
| CN116668080A (en) | A flow anomaly evaluation method and device, electronic equipment and storage medium | |
| CN113515743B (en) | Identification method and device for rebound shell process call chain and electronic device | |
| CN115834183A (en) | Flow detection method and device, electronic equipment and storage medium | |
| CN110162969B (en) | Flow analysis method and device | |
| CN117955725A (en) | Flow monitoring method and device, electronic equipment and storage medium | |
| CN115150108A (en) | DDoS protection system-oriented traffic monitoring method, device and medium | |
| CN119652783A (en) | Channel detection method and device, computer program product, and electronic device | |
| CN114900352A (en) | Bypass blocking methods, apparatus, electronic devices, media and program products |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| RJ01 | Rejection of invention patent application after publication | Application publication date:20200609 | |
| RJ01 | Rejection of invention patent application after publication |