CN111262834A - Physical entity authentication, trusted analysis method, device and system - Google Patents
Physical entity authentication, trusted analysis method, device and systemDownload PDFInfo
- Publication number
- CN111262834A CN111262834ACN202010020929.6ACN202010020929ACN111262834ACN 111262834 ACN111262834 ACN 111262834ACN 202010020929 ACN202010020929 ACN 202010020929ACN 111262834 ACN111262834 ACN 111262834A
- Authority
- CN
- China
- Prior art keywords
- user
- signature
- node
- type
- enterprise
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/0807—Network architectures or network communication protocols for network security for authentication of entities using tickets, e.g. Kerberos
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q30/00—Commerce
- G06Q30/018—Certifying business or products
- G06Q30/0185—Product, service or business identity fraud
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/0823—Network architectures or network communication protocols for network security for authentication of entities using certificates
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3247—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving digital signatures
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3263—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving certificates, e.g. public key certificate [PKC] or attribute certificate [AC]; Public key infrastructure [PKI] arrangements
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Business, Economics & Management (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Development Economics (AREA)
- Accounting & Taxation (AREA)
- Entrepreneurship & Innovation (AREA)
- Economics (AREA)
- Finance (AREA)
- Marketing (AREA)
- Strategic Management (AREA)
- Physics & Mathematics (AREA)
- General Business, Economics & Management (AREA)
- General Physics & Mathematics (AREA)
- Theoretical Computer Science (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本申请涉及工业互联网领域,尤其涉及物理实体的认证、可信解析方法、装置及系统。The present application relates to the field of the Industrial Internet, and in particular, to methods, devices and systems for authentication and trusted analysis of physical entities.
背景技术Background technique
“工业互联网(Industri权威企业节点l Internet)”强调利用先进的人工智能、云计算等互联网技术处理工业大数据,提升产业价值;德国提出“工业4.0(Industrie 4.0)”,强调利用物联网(Internet of Things,IoT)、务联网(Internet of Service,IoS)、信息物理融合系统(Cyber Physic权威企业节点lSystem,CPS)等技术打造智能产品和智能工厂,提高生产效率和创造附加价值。"Industry Internet (Industri Authoritative Enterprise Node l Internet)" emphasizes the use of advanced artificial intelligence, cloud computing and other Internet technologies to process industrial big data and enhance industrial value; Germany proposes "Industrie 4.0", emphasizing the use of Internet of Things (Internet of Things, IoT), Internet of Service (IoS), cyber-physical integration system (Cyber Physic authoritative enterprise node lSystem, CPS) and other technologies to create smart products and smart factories, improve production efficiency and create added value.
工业互联网的基础是“连接”,即通过网络将机器、产品、零部件等工业的物理实体连接到虚拟的网络空间中;核心是“数据”,即通过网络基础设施对物理实体的描述、工序、算法、设计图纸、制造流程、状态监控等工业数据实现交换和共享。The basis of the Industrial Internet is "connection", that is, the physical entities of the industry such as machines, products, and components are connected to the virtual cyberspace through the network; the core is "data", that is, the description and process of physical entities through network infrastructure. , algorithms, design drawings, manufacturing processes, status monitoring and other industrial data to achieve exchange and sharing.
工业互联网中物理实体均具有唯一的物理实体标识。在工业互联网中对于物理实体具有认证和可信解析两个方面。其中认证过程可以对物理实体进行编码以用于生成物理实体标识,也即物理实体的“身份证”,以便后续将物理实体产生的工业数据与物理实体标识对应存储。All physical entities in the Industrial Internet have unique physical entity identifiers. In the Industrial Internet, there are two aspects of authentication and trusted analysis for physical entities. The authentication process can encode the physical entity to generate the physical entity identifier, that is, the "identity card" of the physical entity, so that the industrial data generated by the physical entity can be stored correspondingly with the physical entity identifier.
可信解析过程可以利用物理实体标识进行定位和信息查询,即在工业互联网中依托可信解析来访问保存物理实体的原材料、零部件和产品等相关工业数据的服务器,以便于根据查询到的工业数据实现对异主、异地、异构数据的智能关联,为数据交换和共享提供重要支撑。在工业互联网中物理实体标识具有重要作用,所以需要提供一种可以保护物理实体标识的方案,以防止物理实体标识被篡改或盗取。The trusted parsing process can use the physical entity identification for positioning and information query, that is, relying on trusted parsing in the Industrial Internet to access the server that saves the physical entity's raw materials, parts and products and other related industrial data, so as to facilitate the query based on the industrial data. Data realizes the intelligent association of heterogeneous data, different places and heterogeneous data, and provides important support for data exchange and sharing. Physical entity identification plays an important role in the Industrial Internet, so it is necessary to provide a solution that can protect physical entity identification to prevent physical entity identification from being tampered with or stolen.
发明内容SUMMARY OF THE INVENTION
鉴于此,本申请提供一种物理实体的认证、可信解析方法、装置及系统,可以对在认证和可信解析过程中对物体实体标识进行保护,防止物理实体标识被篡改和盗取。In view of this, the present application provides a method, device and system for authentication and trusted analysis of physical entities, which can protect the identification of object entities in the process of authentication and trusted analysis, and prevent the identification of physical entities from being tampered with and stolen.
为了实现上述目的,本发明提供了下述技术特征:In order to achieve the above object, the present invention provides the following technical features:
一种物理实体的认证方法,包括:A method of authentication for a physical entity, including:
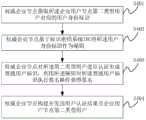
权威企业节点确定待认证的当前用户;The authoritative enterprise node determines the current user to be authenticated;
在所述当前用户为第一类型用户的情况下,权威企业节点接收二级节点发送的企业认证结果,并发送企业认证结果至第一类型用户;其中所述企业认证结果包括二级节点在生成企业前缀标识后利用私钥对所述企业前缀标识进行签名操作所生成的签名;In the case that the current user is a first-type user, the authoritative enterprise node receives the enterprise authentication result sent by the second-level node, and sends the enterprise authentication result to the first-type user; wherein the enterprise authentication result includes that the second-level node is generating A signature generated by performing a signature operation on the enterprise prefix identification with a private key after the enterprise prefix identification;
在所述当前用户为第二类型用户的情况下,权威企业节点对所述第二类型用户进行认证生成普通用户标识,确定与所述第二类型用户对应的签名信息,基于所述普通用户标识和所述签名信息构建用户认证结果,发送用户认证结果至第二类型用户;其中所述用户认证结果包括所述签名信息,以及,利用所述签名信息对所述普通用户标识进行签名操作生成的签名。In the case that the current user is a second type user, the authoritative enterprise node authenticates the second type user to generate a common user identifier, determines the signature information corresponding to the second type user, and determines the signature information corresponding to the second type user based on the common user identifier. The user authentication result is constructed with the signature information, and the user authentication result is sent to the second type of user; wherein the user authentication result includes the signature information, and is generated by using the signature information to perform a signature operation on the common user ID. sign.
可选的,在权威企业节点接收二级节点发送的企业认证结果之前,还包括:Optionally, before the authoritative enterprise node receives the enterprise authentication result sent by the secondary node, it further includes:
权威企业节点发送认证请求至二级节点,所述认证请求包括所述第一类型用户的第一类型用户信息;The authoritative enterprise node sends an authentication request to the secondary node, and the authentication request includes the first-type user information of the first-type user;
二级节点接收认证请求并基于所述认证请求中的第一类型用户信息生成企业前缀标识,利用二级节点的私钥对该企业前缀标识进行签名操作生成签名,构建并存储企业认证结果;The secondary node receives the authentication request and generates an enterprise prefix identifier based on the first type of user information in the authentication request, uses the private key of the secondary node to perform a signature operation on the enterprise prefix identifier to generate a signature, and constructs and stores the enterprise authentication result;
二级节点发送所述企业认证结果至所述权威企业节点,并向国家顶级节点发送所述第一类型用户的第一类型用户标识和二级节点标识的对应关系;The secondary node sends the enterprise authentication result to the authoritative enterprise node, and sends the corresponding relationship between the first-type user identifier of the first-type user and the secondary node identifier to the national top-level node;
国家顶级节点保存所述第一类型用户的第一类型用户标识和二级节点标识的对应关系。The country top-level node saves the correspondence between the first-type user identifier and the second-level node identifier of the first-type user.
可选的,所述权威企业节点集成有标识密码系统,则所述确定与所述第二类型用户对应的签名信息,包括:Optionally, if the authoritative enterprise node is integrated with an identification cryptosystem, the determining the signature information corresponding to the second type of user includes:
获取所述第二类型用户对应的用户身份标识;obtaining the user identity corresponding to the second type of user;
基于标识密码系统将所述用户身份标识作为秘钥,将所述秘钥作为所述签名信息;Based on the identification cryptosystem, the user identity is used as the secret key, and the secret key is used as the signature information;
则所述利用所述签名信息对所述普通用户标识进行签名操作生成的签名包括:利用所述秘钥对所述普通用户标识执行签名操作获得签名。Then, the signature generated by using the signature information to perform a signature operation on the common user identifier includes: using the secret key to perform a signature operation on the common user identifier to obtain a signature.
可选的,所述权威企业节点与第三方认证机构相连,则所述确定与所述第二类型用户对应的签名信息,包括:Optionally, if the authoritative enterprise node is connected to a third-party certification authority, the determining the signature information corresponding to the second type of user includes:
所述权威企业节点发送认证请求至第三方认证机构,所述认证请求包括所述第二类型用户的第二类型用户信息;The authoritative enterprise node sends an authentication request to a third-party authentication agency, and the authentication request includes the second-type user information of the second-type user;
所述权威企业节点接收第三方认证机构针对所述第二类型用户生成并发送的数字证书,将所述数字证书作为所述签名信息;The authoritative enterprise node receives a digital certificate generated and sent by a third-party certification authority for the second type of user, and uses the digital certificate as the signature information;
则所述利用所述签名信息对所述普通用户标识进行签名操作生成的签名包括:利用所述数字证书对所述普通用户标识执行签名操作获得签名。Then, the signature generated by using the signature information to perform a signature operation on the common user identifier includes: using the digital certificate to perform a signature operation on the common user identifier to obtain a signature.
可选的,所述权威企业节点集成有标识密码系统且与第三方认证机构相连,则所述确定与所述第二类型用户对应的签名信息,包括:Optionally, the authoritative enterprise node is integrated with an identification cryptosystem and is connected to a third-party certification authority, then the determining the signature information corresponding to the second type of user includes:
权威企业节点判断所述第二类型用户是否指定第三方认证机构的签名方式;The authoritative enterprise node judges whether the second type of user specifies the signature method of the third-party certification authority;
若所述第二类型用户未指定第三方认证机构的签名方式,则权威企业节点获取所述第二类型用户对应的用户身份标识;基于标识密码系统将所述用户身份标识作为秘钥,将所述秘钥作为所述签名信息;则所述利用所述签名信息对所述普通用户标识进行签名操作生成的签名包括:利用所述秘钥对所述普通用户标识执行签名操作获得签名;If the second type of user does not specify the signature method of the third-party certification authority, the authoritative enterprise node obtains the user identity corresponding to the second type of user; The secret key is used as the signature information; then the signature generated by using the signature information to perform a signature operation on the common user identity includes: using the secret key to perform a signature operation on the common user identity to obtain a signature;
若所述第二类型用户指定第三方认证机构的签名方式,则所述权威企业节点发送认证请求至第三方认证机构,所述认证请求包括所述第二类型用户的第二类型用户信息;接收第三方认证机构针对所述第二类型用户生成并发送的数字证书,将所述数字证书作为所述签名信息;则所述利用所述签名信息对所述普通用户标识进行签名操作生成的签名包括:利用所述数字证书对所述普通用户标识执行签名操作获得签名。If the second-type user specifies the signature method of the third-party certification authority, the authoritative enterprise node sends an authentication request to the third-party certification authority, and the certification request includes the second-type user information of the second-type user; receiving The third-party certification authority uses the digital certificate as the signature information for the digital certificate generated and sent by the second type of user; then the signature generated by using the signature information to perform a signature operation on the common user identifier includes: : use the digital certificate to perform a signature operation on the common user ID to obtain a signature.
可选的,所述用户认证结果还包括签名类型;所述签名类型为第一类型或第二类型;Optionally, the user authentication result further includes a signature type; the signature type is the first type or the second type;
第一类型,用于表示借助于标识密码系统生成的秘钥对普通用户标识进行签名操作的签名方式;The first type is used to represent the signature mode in which the ordinary user ID is signed by means of the secret key generated by the identification cryptosystem;
第二类型,用于表示借助于第三方认证机构生成的数字证书对普通用户标识进行签名操作的签名方式;The second type is used to represent the signature method for performing the signature operation on the common user identity by means of a digital certificate generated by a third-party certification authority;
所述用户认证结果的数据结构包括:The data structure of the user authentication result includes:
签名类型字段,用于存储所述签名类型;a signature type field, used to store the signature type;
数字证书字段,用于存储采用第三方认证机构生成的数字证书,在未采用第三方认证机构生成数字证书的情况下该字段为空;The digital certificate field is used to store the digital certificate generated by the third-party certification authority, and this field is empty when the third-party certification authority is not used to generate the digital certificate;
签名字段,用于存储签名。Signature field, used to store the signature.
一种物理实体的可信解析方法,包括:A trusted resolution method for physical entities, including:
公共递归解析节点接收当前用户发送的可信解析请求;The public recursive parsing node receives the trusted parsing request sent by the current user;
在所述当前用户为第一类型用户的情况下,公共递归解析节点采用递归方式对所述可信解析请求中企业认证结果中的签名进行可信解析操作,获得可信解析结果;In the case that the current user is a user of the first type, the public recursive parsing node performs a trusted parsing operation on the signature in the enterprise authentication result in the trusted parsing request in a recursive manner to obtain a trusted parsing result;
在所述当前用户为第二类型用户情况下,公共递归解析节点对所述可信解析请求中用户认证结果中的签名信息和签名进行可信解析操作,获得可信解析结果。In the case that the current user is a second type user, the public recursive parsing node performs a trusted parsing operation on the signature information and signature in the user authentication result in the trusted parsing request to obtain a trusted parsing result.
可选的,在公共递归解析节点采用递归方式对所述可信解析请求中企业认证结果中的签名进行可信解析操作,获得可信解析结果之前,还包括:Optionally, before the public recursive parsing node performs a trusted parsing operation on the signature in the enterprise authentication result in the trusted parsing request in a recursive manner, and obtains the trusted parsing result, the method further includes:
公共递归解析节点判断本地密码机是否存储有与所述可信解析请求中第一类型用户标识对应的历史可信解析结果;The public recursive parsing node determines whether the local cryptographic machine stores the historical trusted parsing result corresponding to the first type of user ID in the trusted parsing request;
若存储有与所述可信解析请求中第一类型用户标识对应的历史可信解析结果且历史可信解析结果有效,则使用所述历史可信解析结果作为所述可信解析结果;If a historical trusted analysis result corresponding to the first type of user identifier in the trusted analysis request is stored and the historical trusted analysis result is valid, the historical trusted analysis result is used as the trusted analysis result;
若未存储有与所述可信解析请求中第一类型用户标识对应的历史可信解析结果,则执行所述采用递归方式对所述企业认证结果中签名进行可信解析操作,获得可信解析结果的步骤;并且,将所述可信解析结果与所述第一类型用户标识对应存储于所述本地密码机中。If there is no historical trusted resolution result corresponding to the first type of user ID in the trusted resolution request, execute the recursive manner to perform trusted resolution on the signature in the enterprise authentication result to obtain trusted resolution and storing the trusted parsing result in the local cryptographic machine corresponding to the first-type user identifier.
可选的,所述公共递归解析节点采用递归方式对所述可信解析请求中企业认证结果中的签名进行可信解析操作,包括:Optionally, the public recursive parsing node performs a trusted parsing operation on the signature in the enterprise authentication result in the trusted parsing request in a recursive manner, including:
公共递归解析节点向国家顶级节点查询所述第一类型用户的第一类型用户标识;The public recursive parsing node queries the country top-level node for the first-type user identifier of the first-type user;
国家顶级节点若查询到所述第一类型用户标识,则返回与所述第一类型用户标识关联的二级节点的网络地址和二级节点的数字证书;If the country's top-level node queries the first-type user identifier, it returns the network address of the secondary node associated with the first-type user identifier and the digital certificate of the secondary node;
公共递归解析节点向二级节点的网络地址对应的二级节点查询所述第一类型用户标识;The public recursive parsing node queries the second-level node corresponding to the network address of the second-level node for the first-type user identifier;
所述二级节点若查询到所述第一类型用户标识,则返回与第一类型用户标识对应的网络地址和与第一类型用户标识对应的签名;If the secondary node finds the first type of user identification, it returns a network address corresponding to the first type of user identification and a signature corresponding to the first type of user identification;
公共递归解析节点验证企业认证结果中的签名与二级节点返回的第一类型用户标识对应的签名是否一致;The public recursive parsing node verifies whether the signature in the enterprise authentication result is consistent with the signature corresponding to the first-type user ID returned by the secondary node;
若不一致则确定可信解析失败;If it is inconsistent, it is determined that the trusted parsing fails;
若一致则从国家顶级节点查询国家顶级节点的根证书,并采用根证书验证二级节点的数字证书;If they are consistent, query the root certificate of the country's top-level node from the country's top-level node, and use the root certificate to verify the digital certificate of the second-level node;
若验证不通过则确定可信解析失败;If the verification fails, it is determined that the trusted parsing fails;
若验证通过则采用二级节点的数字证书验证企业认证结果中的签名,若验证通过则表示可信解析成功,否则表示可信解析失败;If the verification is passed, the digital certificate of the secondary node is used to verify the signature in the enterprise certification result. If the verification is passed, it means that the trusted analysis is successful, otherwise, it means that the trusted analysis fails;
若可信解析成功,则将二级节点的网络地址、第一类型用户的网络地址和可信解析结果,与,第一类型用户标识对应存储到本地密码机中。If the trusted resolution is successful, the network address of the secondary node, the network address of the first-type user, the trusted resolution result, and the first-type user identifier are stored in the local cryptographic machine correspondingly.
可选的,若用户认证结果采用密码标识系统的签名方式,则所述公共递归解析节点对所述可信解析请求中用户认证结果中的签名信息和签名进行可信解析操作,获得可信解析结果包括:Optionally, if the user authentication result adopts the signature method of the password identification system, the public recursive parsing node performs a trusted parsing operation on the signature information and signature in the user authentication result in the trusted parsing request to obtain a trusted parsing operation. Results include:
公共递归解析节点将所述可信解析请求中的用户身份标识作为公钥;The public recursive parsing node uses the user identity in the trusted parsing request as a public key;
利用所述公钥对所述签名进行解密操作;Decrypt the signature using the public key;
若解密成功则确定可信解析成功,否则确定可信解析失败。If the decryption succeeds, it is determined that the trusted parsing is successful; otherwise, it is determined that the trusted parsing fails.
可选的,若用户认证结果采用第三方认证机构的签名方式,则所述公共递归解析节点对所述可信解析请求中用户认证结果中的签名信息和签名进行可信解析操作,获得可信解析结果包括:Optionally, if the user authentication result adopts the signature method of a third-party authentication agency, the public recursive parsing node performs a trusted parsing operation on the signature information and signature in the user authentication result in the trusted parsing request, and obtains a trusted parsing operation. The analysis results include:
公共递归解析节点将用户认证结果中的数字证书作为公钥;The public recursive parsing node uses the digital certificate in the user authentication result as the public key;
利用所述公钥对所述签名进行解密操作;Decrypt the signature using the public key;
若解密成功则获取第三方认证机构的根证书,若解密失败确定可信解析失败;If the decryption is successful, the root certificate of the third-party certification authority will be obtained. If the decryption fails, the trusted parsing will fail;
利用所述第三方认证机构的根证书对所述数字证书进行验证;Verifying the digital certificate using the root certificate of the third-party certification authority;
若验证成功则确定可信解析成功,否则确定可信解析失败。If the verification is successful, it is determined that the trusted parsing is successful; otherwise, it is determined that the trusted parsing fails.
可选的,用户认证结果包括签名类型字段、数字证书字段和签名字段的情况下,则所述公共递归解析节点对所述可信解析请求中用户认证结果中的签名信息和签名进行可信解析操作,获得可信解析结果包括:Optionally, when the user authentication result includes a signature type field, a digital certificate field, and a signature field, the public recursive parsing node performs trusted parsing on the signature information and signature in the user authentication result in the trusted parsing request. Operation to obtain trusted parsing results includes:
若所述签名类型字段指示为第一类型,则从所述签名字段提取签名,将所述可信解析请求中的用户身份标识作为公钥;利用所述公钥对所述签名进行解密操作;若解密成功则确定可信解析成功,否则确定可信解析失败;If the signature type field indicates the first type, extract a signature from the signature field, and use the user identity in the trusted resolution request as a public key; use the public key to decrypt the signature; If the decryption is successful, it is determined that the trusted parsing is successful, otherwise it is determined that the trusted parsing fails;
若所述签名类型字段指示为第二类型,则从所述签名字段提取签名,从所述数字证书字段提取数字证书;将所述数字证书作为公钥;利用所述公钥对所述签名进行解密操作;若解密成功则获取第三方认证机构的根证书,若解密失败确定可信解析失败;利用所述第三方认证机构的根证书对所述数字证书进行验证;若验证成功则确定可信解析成功,否则确定可信解析失败。If the signature type field indicates the second type, extract the signature from the signature field, and extract the digital certificate from the digital certificate field; use the digital certificate as a public key; use the public key to perform the signature on the signature Decryption operation; if decryption is successful, obtain the root certificate of the third-party certification authority; if decryption fails, determine that the trusted analysis fails; use the root certificate of the third-party certification authority to verify the digital certificate; if the verification is successful, determine the trustworthy The parsing succeeds, otherwise it is determined that the trusted parsing fails.
一种物理实体的认证装置,包括:An authentication device for a physical entity, comprising:
节点确认器,用于权威企业节点确定待认证的当前用户;Node validator, used by authoritative enterprise nodes to determine the current user to be authenticated;
接收器,用于在所述当前用户为第一类型用户的情况下,权威企业节点接收二级节点发送的企业认证结果,并发送企业认证结果至第一类型用户;其中所述企业认证结果包括二级节点在生成企业前缀标识后利用私钥对所述企业前缀标识进行签名操作所生成的签名;a receiver, configured to receive the enterprise authentication result sent by the secondary node when the current user is a first-type user, and send the enterprise authentication result to the first-type user; wherein the enterprise authentication result includes The signature generated by the secondary node using the private key to perform a signature operation on the enterprise prefix identifier after generating the enterprise prefix identifier;
节点认证器,用于在所述当前用户为第二类型用户的情况下,权威企业节点对所述第二类型用户进行认证生成普通用户标识,确定与所述第二类型用户对应的签名信息;a node authenticator, configured to authenticate the second type of user by an authoritative enterprise node to generate a common user identifier when the current user is a second type of user, and to determine signature information corresponding to the second type of user;
认证结果构建器,用于基于所述普通用户标识和所述签名信息构建用户认证结果,发送用户认证结果至第二类型用户;其中所述用户认证结果包括所述签名信息,以及,利用所述签名信息对所述普通用户标识进行签名操作生成的签名。an authentication result builder, configured to construct a user authentication result based on the common user identifier and the signature information, and send the user authentication result to the second type of user; wherein the user authentication result includes the signature information, and, using the The signature information is a signature generated by performing a signature operation on the common user ID.
一种工业互联网系统,包括:An industrial internet system including:
物理实体标识应用系统和物理实体标识服务系统;Physical entity identification application system and physical entity identification service system;
其中,物理实体标识服务系统包括:国际根节点,与国际根节点相连的国家根节点,与国家根节点相连的二级节点,与二级节点相连的权威企业节点,和,与所述国家根节点、二级节点和权威企业节点相连的公共递归解析节点;The physical entity identification service system includes: an international root node, a national root node connected to the international root node, a secondary node connected to the national root node, an authoritative enterprise node connected to the secondary node, and a national root node connected to the national root node. Public recursive parsing nodes connected to nodes, secondary nodes and authoritative enterprise nodes;
所述权威企业节点,用于确定待认证的当前用户;在所述当前用户为第一类型用户的情况下,接收二级节点发送的企业认证结果;其中所述企业认证结果包括二级节点在生成企业前缀标识后利用私钥对所述企业前缀标识进行签名操作所生成的签名;在所述当前用户为第二类型用户的情况下,权威企业节点对所述第二类型用户进行认证生成普通用户标识,确定与所述第二类型用户对应的签名信息,基于所述普通用户标识和所述签名信息构建并发送用户认证结果;其中所述用户认证结果包括所述签名信息,以及,利用所述签名信息对所述普通用户标识进行签名操作生成的签名。The authoritative enterprise node is used to determine the current user to be authenticated; in the case that the current user is a first-type user, receive the enterprise authentication result sent by the secondary node; wherein the enterprise authentication result includes the secondary node in the After the enterprise prefix identification is generated, the signature generated by performing a signature operation on the enterprise prefix identification with a private key; in the case that the current user is a second type user, the authoritative enterprise node authenticates the second type user and generates a common signature. User identification, determine the signature information corresponding to the second type of user, construct and send a user authentication result based on the common user identification and the signature information; wherein the user authentication result includes the signature information, and, using the The signature information is generated by performing a signature operation on the common user ID.
一种物理实体的可信解析装置,包括:A trusted parsing device for a physical entity, comprising:
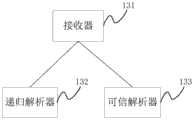
接收器,用于公共递归解析节点接收当前用户发送的可信解析请求;The receiver is used for the public recursive parsing node to receive the trusted parsing request sent by the current user;
递归解析器,用于在所述当前用户为第一类型用户的情况下,公共递归解析节点采用递归方式对所述可信解析请求中企业认证结果中的签名进行可信解析操作,获得可信解析结果;A recursive parser, used for performing trusted parsing operations on the signature in the enterprise authentication result in the trusted parsing request in a recursive manner by the public recursive parsing node to obtain trusted parsing results;
可信解析器,用于在所述当前用户为第二类型用户情况下,公共递归解析节点对所述可信解析请求中用户认证结果中的签名信息和签名进行可信解析操作,获得可信解析结果。A trusted resolver, configured to perform a trusted resolution operation on the signature information and signature in the user authentication result in the trusted resolution request by the public recursive resolution node when the current user is a user of the second type, to obtain a trusted resolution Parse the result.
一种工业互联网系统,包括:An industrial internet system including:
物理实体标识应用系统和物理实体标识服务系统;Physical entity identification application system and physical entity identification service system;
其中,物理实体标识服务系统包括:国际根节点,与国际根节点相连的国家根节点,与国家根节点相连的二级节点,与二级节点相连的权威企业节点,和,与所述国家根节点、二级节点和所述权威企业节点相连的公共递归解析节点;The physical entity identification service system includes: an international root node, a national root node connected to the international root node, a secondary node connected to the national root node, an authoritative enterprise node connected to the secondary node, and a national root node connected to the national root node. a public recursive parsing node connected to the node, the secondary node and the authoritative enterprise node;
所述公共递归解析节点,用于接收当前用户发送的可信解析请求,在所述当前用户为第一类型用户的情况下,公共递归解析节点采用递归方式对所述可信解析请求中企业认证结果中的签名进行可信解析操作,获得可信解析结果;在所述当前用户为第二类型用户情况下,公共递归解析节点对所述可信解析请求中用户认证结果中的签名信息和签名进行可信解析操作,获得可信解析结果。The public recursive parsing node is used to receive a trusted parsing request sent by the current user, and in the case that the current user is a user of the first type, the public recursive parsing node adopts a recursive manner to authenticate the enterprise in the trusted parsing request. Perform a trusted analysis operation on the signature in the result to obtain a trusted analysis result; in the case where the current user is a second type user, the public recursive analysis node interprets the signature information and signature in the user authentication result in the trusted analysis request Perform trusted parsing operations to obtain trusted parsing results.
通过以上技术手段,可以实现以下有益效果:Through the above technical means, the following beneficial effects can be achieved:
由于权威企业节点对第一类型用户和第二类型用户的处理方式不同,为此本发明将当前用户分为第一类型用户和第二类型用户,分别针对不同的当前用户采用不同的保护策略。Because the authoritative enterprise node handles the first type user and the second type user differently, the present invention divides the current user into the first type user and the second type user, and adopts different protection strategies for different current users.
针对第一类型用户而言:权威企业节点的上级节点也即二级节点可以为该第一类型用户进行认证并生成企业前缀标识,为了保护企业前缀标识,二级节点采用二级节点自身的私钥、对企业前缀标识进行签名操作获得签名。这样可以使得二级节点与权威企业节点之间传输加密后的企业前缀标识,从而保护企业前缀标识,防止企业前缀标识被篡改或盗取。For the first type of user: the upper-level node of the authoritative enterprise node, that is, the second-level node, can authenticate the first-type user and generate an enterprise prefix identifier. In order to protect the enterprise prefix identifier, the second-level node uses the private key, and perform a signature operation on the enterprise prefix ID to obtain a signature. In this way, the encrypted enterprise prefix identifier can be transmitted between the secondary node and the authoritative enterprise node, so as to protect the enterprise prefix identifier and prevent the enterprise prefix identifier from being tampered with or stolen.
对于第二类型用户而言:权威企业节点可以接收第二类型用户的认证请求,然后针对第二类型用户进行认证生成普通用户标识,第一类型用户还可以确定与第二类型用户对应的签名信息,并采用签名信息对普通用户标识进行签名操作获得签名。这样可以使得第一类型用户与第二类型用户之间传输加密后的普通用户标识,从而保护普通用户标识,防止普通用户标识被篡改或盗取。For the second type of user: the authoritative enterprise node can receive the authentication request of the second type of user, and then authenticate the second type of user to generate a common user ID, and the first type of user can also determine the signature information corresponding to the second type of user. , and use the signature information to perform a signature operation on the common user ID to obtain a signature. In this way, the encrypted common user ID can be transmitted between the first type user and the second type user, thereby protecting the common user ID and preventing the common user ID from being tampered with or stolen.
附图说明Description of drawings
为了更清楚地说明本申请实施例或现有技术中的技术方案,下面将对实施例或现有技术描述中所需要使用的附图作简单地介绍,显而易见地,下面描述中的附图仅仅是本申请的一些实施例,对于本领域普通技术人员来讲,在不付出创造性劳动的前提下,还可以根据这些附图获得其他的附图。In order to more clearly illustrate the embodiments of the present application or the technical solutions in the prior art, the following briefly introduces the accompanying drawings required for the description of the embodiments or the prior art. Obviously, the drawings in the following description are only These are some embodiments of the present application. For those of ordinary skill in the art, other drawings can also be obtained based on these drawings without any creative effort.
图1a-1c为本申请实施例公开的工业互联网系统的结构示意图;1a-1c are schematic structural diagrams of an industrial Internet system disclosed in an embodiment of the application;
图2为本申请实施例公开的一种物理实体的认证方法的实施例一的流程图;2 is a flowchart of Embodiment 1 of a method for authenticating a physical entity disclosed in an embodiment of the present application;
图3a-3b为本申请实施例公开的一种物理实体的认证方法的实施例二的流程图;3a-3b are flowcharts of Embodiment 2 of a method for authenticating a physical entity disclosed in an embodiment of the application;
图4a-4b为本申请实施例公开的一种物理实体的认证方法的实施例三的流程图;4a-4b are flowcharts of Embodiment 3 of a method for authenticating a physical entity disclosed in an embodiment of the application;
图5a-5b为本申请实施例公开的一种物理实体的认证方法的实施例四的流程图;5a-5b are flowcharts of Embodiment 4 of a method for authenticating a physical entity disclosed in an embodiment of the application;
图6为本申请实施例公开的一种物理实体的认证方法的实施例五的流程图;6 is a flowchart of Embodiment 5 of a method for authenticating a physical entity disclosed in an embodiment of the present application;
图7为本申请实施例公开的一种物理实体的可信解析方法的实施例一的流程图;7 is a flowchart of Embodiment 1 of a method for trusted analysis of physical entities disclosed in an embodiment of the present application;
图8a-8b为本申请实施例公开的一种物理实体的可信解析方法的实施例二的流程图;8a-8b are flowcharts of Embodiment 2 of a method for trusted analysis of physical entities disclosed in the embodiments of the present application;
图9为本申请实施例公开的一种物理实体的可信解析方法的实施例三的流程图;9 is a flowchart of Embodiment 3 of a method for trusted analysis of physical entities disclosed in an embodiment of the present application;
图10为本申请实施例公开的一种物理实体的可信解析方法的实施例四的流程图;10 is a flowchart of Embodiment 4 of a method for trusted analysis of physical entities disclosed in an embodiment of the present application;
图11a为本申请实施例公开的一种物理实体的可信解析方法的实施例五的流程图;11a is a flowchart of Embodiment 5 of a method for trusted analysis of physical entities disclosed in an embodiment of the present application;
图11b为本申请实施例公开的一种物理实体的可信解析方法的实施例六的流程图;11b is a flowchart of Embodiment 6 of a method for trusted analysis of physical entities disclosed in an embodiment of the present application;
图12为本申请实施例公开的一种物理实体的认证装置的结构示意图;12 is a schematic structural diagram of a physical entity authentication apparatus disclosed in an embodiment of the application;
图13为本申请实施例公开的一种工业互联网的可信解析装置的结构示意图。FIG. 13 is a schematic structural diagram of an industrial Internet trusted parsing device disclosed in an embodiment of the present application.
具体实施方式Detailed ways
术语解释:Terminology Explanation:
国际根节点:是指某一标识体系中的最高层级服务节点,不限于特定国家或者地区,而是面向全球范围提供公共的根区数据管理和根解析服务。International root node: refers to the highest-level service node in a certain identification system, which is not limited to a specific country or region, but provides public root zone data management and root resolution services on a global scale.
国家顶级节点:工业互联网可信解析体系的关键,既是对外互联的国际关口,也是对内统筹的核心枢纽。能够面向全国范围提供顶级认证注册和可信解析服务,以及标识备案、标识认证等管理能力。国家顶级节点既要与各种标识体系的国际根节点保持连通,又要连通国内的各种二级及以下其他可信解析服务节点。National top node: The key to the trusted analysis system of the Industrial Internet is not only the international gateway for external interconnection, but also the core hub for internal coordination. It can provide top-level certification registration and trusted analysis services nationwide, as well as management capabilities such as logo filing and logo certification. The national top-level node should not only maintain connection with the international root nodes of various identification systems, but also connect with various domestic second-level and lower trusted resolution service nodes.
二级节点:是指一个行业或者区域内部的可信解析公共服务节点,能够面向行业或区域提供认证注册和可信解析服务,以及完成相关的标识业务管理、标识应用对接等。Secondary node: refers to a trusted resolution public service node within an industry or region, which can provide authentication registration and trusted resolution services for the industry or region, as well as complete related identification business management, identification application docking, etc.
企业节点:是指一个企业内部的可信解析服务节点,能够面向特定企业提供标识注册和可信解析服务。既可以独立部署,也可以作为企业信息系统的组成要素。Enterprise node: refers to a trusted resolution service node within an enterprise, which can provide identity registration and trusted resolution services for a specific enterprise. It can be deployed independently or as a component of an enterprise information system.
第三方认证机构(Certificate authority),用于签发数字证书。A third-party certification authority (Certificate authority), used to issue digital certificates.
标识密码系统IBC(Identity-Based Cryptosystems&Signature Schemes):该系统是在CA认证体系基础上发展起来的,本质上是公钥基础设施的一种;最早由以色列密码学家Shamir提出,主要思想是以用户标识作为公钥,用户私钥由秘钥生产中心KGC(KeyGeneration Center)根据用户标识产生,技术上简化CA中心公钥管理。IBC (Identity-Based Cryptosystems&Signature Schemes): This system is developed on the basis of the CA certification system, and is essentially a kind of public key infrastructure; it was first proposed by the Israeli cryptographer Shamir, and the main idea is to use users The identifier is used as the public key, and the user's private key is generated by the key production center KGC (KeyGeneration Center) according to the user identifier, which technically simplifies the public key management of the CA center.
下面将结合本申请实施例中的附图,对本申请实施例中的技术方案进行清楚、完整地描述,显然,所描述的实施例仅仅是本申请一部分实施例,而不是全部的实施例。基于本申请中的实施例,本领域普通技术人员在没有做出创造性劳动前提下所获得的所有其他实施例,都属于本申请保护的范围。The technical solutions in the embodiments of the present application will be clearly and completely described below with reference to the drawings in the embodiments of the present application. Obviously, the described embodiments are only a part of the embodiments of the present application, but not all of the embodiments. Based on the embodiments in the present application, all other embodiments obtained by those of ordinary skill in the art without creative efforts shall fall within the protection scope of the present application.
为了便于本申请技术人员了解本申请的技术架构,本申请提供一种工业互联网系统的实施例一,参见图1工业互联网系统包括:物理实体标识应用系统100和物理实体标识服务系统200。In order to facilitate the technical personnel of the present application to understand the technical architecture of the present application, the present application provides the first embodiment of an industrial Internet system. Referring to FIG. 1 , the industrial Internet system includes: a physical entity
其中,物理实体标识服务系统200包括:Wherein, the physical entity
国际根节点201,与国际根节点相连201的国家根节点202,与国家根节点202相连的二级节点203,与二级节点203相连的权威企业节点204,和,与所述国家根节点202、二级节点203和所述权威企业节点204相连的公共递归解析节点205。The
可选的,权威企业节点可以集成有标识密码系统IBC,以用于对待认证的用户进行签名操作,具体过程将在后续实施例中进行详细描述,在此暂不详细描述。Optionally, the authoritative enterprise node may be integrated with an identification and cryptography system IBC for performing a signature operation on a user to be authenticated. The specific process will be described in detail in subsequent embodiments, and will not be described in detail here.
本申请提供一种工业互联网系统的实施例二,参见图1b包括:物理实体标识应用系统100,物理实体标识服务系统200和第三方认证机构300。The present application provides a second embodiment of an industrial Internet system. Referring to FIG. 1 b , it includes: a physical entity
其中,物理实体标识服务系统200包括:国际根节点201,与国际根节点相连201的国家根节点202,与国家根节点202相连的二级节点203,与二级节点203相连的权威企业节点204,和,与所述国家根节点202、二级节点203和所述权威企业节点204相连的公共递归解析节点205。The physical entity
可选的,权威企业节点与第三方认证机构300相连,以用于对待认证的用户进行签名操作,具体过程将在后续实施例中进行详细描述,在此暂不详细描述。Optionally, the authoritative enterprise node is connected to the third-
本申请提供一种工业互联网系统的实施例三,参见图1c包括:物理实体标识应用系统100,物理实体标识服务系统200和第三方认证机构300。The present application provides a third embodiment of an industrial Internet system. Referring to FIG. 1 c , it includes: a physical entity
其中,物理实体标识服务系统200包括:国际根节点201,与国际根节点相连201的国家根节点202,与国家根节点202相连的二级节点203,与二级节点203相连的权威企业节点204,和,与所述国家根节点202、二级节点203和所述权威企业节点204相连的公共递归解析节点205。The physical entity
可选的,权威企业节点可以集成有标识密码系统IBC,且,权威企业节点与第三方认证机构300相连,以用于对待认证用户进行签名操作,具体过程将在后续实施例中进行详细描述,在此暂不详细描述。Optionally, the authoritative enterprise node may be integrated with the identification and cryptography system IBC, and the authoritative enterprise node is connected to the third-
在上述图1a-图1c中,国家根节点202、二级节点203和权威企业节点204的数量与实际应用场景有关,图示中仅作为示意性说明,并未真正体现国家根节点202、二级节点203和权威企业节点204的数量。1a-1c, the number of
所述物理实体标识应用系统100包括:工业互联网APP、工业互联网平台、企业信息系统等,对此不再赘述。The physical entity
对于已经在工业互联网系统中认证注册过的企业节点称为权威企业节点。为了保护权威企业节点和工业互联网的安全性,对于想要访问权威企业节点的临时用户进行认证操作和可信解析操作。Enterprise nodes that have been certified and registered in the Industrial Internet system are called authoritative enterprise nodes. In order to protect the security of authoritative enterprise nodes and the industrial Internet, authentication operations and trusted resolution operations are performed for temporary users who want to access authoritative enterprise nodes.
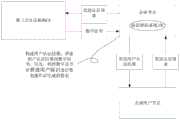
在临时用户被认证过程中会向临时用户分配标识,已认证用户携带已分配标识访问权威企业节点,权威企业节点会借助于公共递归解析节点进行可信解析,在可信解析通过后才允许访问权威企业节点的数据。During the authentication process of the temporary user, an ID will be assigned to the temporary user, and the authenticated user will access the authoritative enterprise node with the assigned ID. The authoritative enterprise node will use the public recursive resolution node to perform trusted resolution, and the access will be allowed after the trusted resolution is passed. Data of authoritative enterprise nodes.
本申请提供一种物理实体的认证方法的实施例一,应用于权威企业节点。参见图2,可以包括以下步骤:The present application provides the first embodiment of an authentication method for a physical entity, which is applied to an authoritative enterprise node. Referring to Figure 2, the following steps may be included:
步骤S201:权威企业节点确定待认证的当前用户。Step S201: The authoritative enterprise node determines the current user to be authenticated.
权威企业节点可以获取第二类型用户发送的认证请求,也可以接收第一类型用户发送的认证请求;所以权威企业节点在获取一个认证请求后,首先确定发送认证请求的临时用户类型,也即待认证的当前用户为第一类型用户还是第二类型用户。The authoritative enterprise node can obtain the authentication request sent by the second type of user, and can also receive the authentication request sent by the first type of user; therefore, after obtaining an authentication request, the authoritative enterprise node first determines the temporary user type that sends the authentication request, that is, the pending user type. Whether the authenticated current user is the first type user or the second type user.
本发明中将想要访问权威企业节点的用户称为临时用户,临时用户可以分为两类:第一类型用户为想要访问本权威企业节点的其它企业终端,第二类型用户为想要访问权威企业节点的普通用户终端。In the present invention, users who want to access an authoritative enterprise node are called temporary users, and temporary users can be divided into two categories: the first type of users are other enterprise terminals that want to access the authoritative enterprise node, and the second type of users are users who want to access the authoritative enterprise node. Ordinary user terminal of authoritative enterprise node.
步骤S202:在所述当前用户为第一类型用户的情况下,权威企业节点接收二级节点发送的企业认证结果,并发送企业认证结果至第一类型用户;其中所述企业认证结果包括二级节点在生成企业前缀标识后利用私钥对所述企业前缀标识进行签名操作所生成的签名。Step S202: In the case that the current user is a first-type user, the authoritative enterprise node receives the enterprise authentication result sent by the second-level node, and sends the enterprise authentication result to the first-type user; wherein the enterprise authentication result includes the second-level user. After generating the enterprise prefix identification, the node uses the private key to perform a signature operation on the enterprise prefix identification to generate a signature.
步骤S203:在所述当前用户为第二类型用户的情况下,权威企业节点对所述第二类型用户进行认证生成普通用户标识,确定与所述第二类型用户对应的签名信息,基于所述普通用户标识和所述签名信息构建用户认证结果,发送用户认证结果至第二类型用户;其中所述用户认证结果包括所述签名信息,以及,利用所述签名信息对所述普通用户标识进行签名操作生成的签名。Step S203: In the case where the current user is a second type user, the authoritative enterprise node authenticates the second type user to generate a common user identifier, determines the signature information corresponding to the second type user, and determines the signature information corresponding to the second type user based on the The common user identification and the signature information construct a user authentication result, and send the user authentication result to the second type of user; wherein the user authentication result includes the signature information, and the common user identification is signed by using the signature information The signature generated by the operation.
通过以上技术手段,可以实现以下有益效果:Through the above technical means, the following beneficial effects can be achieved:
由于权威企业节点对第一类型用户和第二类型用户的处理方式不同,为此本发明将当前用户分为第一类型用户和第二类型用户,分别针对不同的当前用户采用不同的保护策略。Because the authoritative enterprise node handles the first type user and the second type user differently, the present invention divides the current user into the first type user and the second type user, and adopts different protection strategies for different current users.
针对第一类型用户而言:权威企业节点的上级节点也即二级节点可以为该第一类型用户进行认证并生成企业前缀标识,为了保护企业前缀标识,二级节点采用二级节点自身的私钥、对企业前缀标识进行签名操作获得签名。这样可以使得二级节点与权威企业节点之间传输加密后的企业前缀标识,从而保护企业前缀标识,防止企业前缀标识被篡改或盗取。For the first type of user: the upper-level node of the authoritative enterprise node, that is, the second-level node, can authenticate the first-type user and generate an enterprise prefix identifier. In order to protect the enterprise prefix identifier, the second-level node uses the private key, and perform a signature operation on the enterprise prefix ID to obtain a signature. In this way, the encrypted enterprise prefix identifier can be transmitted between the secondary node and the authoritative enterprise node, so as to protect the enterprise prefix identifier and prevent the enterprise prefix identifier from being tampered with or stolen.
对于第二类型用户而言:权威企业节点可以接收第二类型用户的认证请求,然后针对第二类型用户进行认证生成普通用户标识,第一类型用户还可以确定与第二类型用户对应的签名信息,并采用签名信息对普通用户标识进行签名操作获得签名。这样可以使得第一类型用户与第二类型用户之间传输加密后的普通用户标识,从而保护普通用户标识,防止普通用户标识被篡改或盗取。For the second type of user: the authoritative enterprise node can receive the authentication request of the second type of user, and then authenticate the second type of user to generate a common user ID, and the first type of user can also determine the signature information corresponding to the second type of user. , and use the signature information to perform a signature operation on the common user ID to obtain a signature. In this way, the encrypted common user ID can be transmitted between the first type user and the second type user, thereby protecting the common user ID and preventing the common user ID from being tampered with or stolen.
下面对于权威企业节点的认证过程进行详细描述。The authentication process of the authoritative enterprise node is described in detail below.
本申请提供一种物理实体的认证方法的实施例二,应用于图1a-图1c任一个所述的工业互联网系统中的权威企业节点。参见图3a和3b,可以包括以下步骤:The present application provides a second embodiment of an authentication method for a physical entity, which is applied to an authoritative enterprise node in any one of the industrial Internet systems described in FIG. 1a to FIG. 1c. Referring to Figures 3a and 3b, the following steps may be included:
步骤S301~S305为国家顶级节点和二级节点预先执行的过程。在二级节点到国家顶级节点认证后,企业节点可以到二级节点中进行认证,认证成功后变为权威企业节点。认证过程与步骤S306与步骤S309类似。Steps S301 to S305 are processes performed in advance by the country's top-level nodes and second-level nodes. After the second-level node is certified to the national top-level node, the enterprise node can go to the second-level node for certification, and become an authoritative enterprise node after successful certification. The authentication process is similar to steps S306 and S309.
步骤S301:国家顶级节点通过自签名方式获得根证书。Step S301: The top-level node of the country obtains the root certificate by means of self-signature.
国家顶级节点可以根据一定的密钥算法生成公钥和私钥,然后利用私钥对公钥进行加密操作,将加密结果作为国家顶级节点的根证书。The country's top node can generate a public key and a private key according to a certain key algorithm, and then use the private key to encrypt the public key, and use the encryption result as the root certificate of the country's top node.
步骤S302:二级节点向国家顶级节点发送认证请求,认证请求包括二级节点信息和二级节点的公钥。Step S302: The secondary node sends an authentication request to the top-level node in the country, where the authentication request includes the secondary node information and the public key of the secondary node.
二级节点可以根据一定的密钥算法生成公钥和私钥,发送认证请求中包括二级节点的公钥和二级节点的节点信息。The secondary node can generate a public key and a private key according to a certain key algorithm, and send the authentication request including the public key of the secondary node and the node information of the secondary node.
步骤S303:国家顶级节点接收二级节点发送的认证请求,生成二级节点的数字证书和二级节点前缀标识,并对二级节点前缀标识执行签名操作获得签名。Step S303: The national top-level node receives the authentication request sent by the second-level node, generates a digital certificate of the second-level node and the second-level node prefix identification, and performs a signature operation on the second-level node prefix identification to obtain a signature.
国家顶级节点按照一定的规则生成二级节点前缀标识,并利用国家顶级节点的私钥对二级节点前缀标识进行签名操作生成签名。国家顶级节点利用国家顶级节点的私钥对二级节点发送的公钥进行加密操作,将加密结果作为二级节点的数字证书。The national top-level node generates the secondary node prefix identification according to certain rules, and uses the private key of the national top-level node to perform a signature operation on the secondary node prefix identification to generate a signature. The national top-level node uses the private key of the national top-level node to encrypt the public key sent by the second-level node, and uses the encryption result as the digital certificate of the second-level node.
步骤S304:国家顶级节点保存二级节点的数字证书和二级节点的网络地址,发送二级节点的数字证书和签名至二级节点。Step S304: The national top-level node saves the digital certificate of the second-level node and the network address of the second-level node, and sends the digital certificate and signature of the second-level node to the second-level node.
国家顶级节点可以保存二级节点的数字证书和二级节点的网络地址,以便于后续进行可信解析操作时使用。The national top-level node can save the digital certificate of the second-level node and the network address of the second-level node for use in subsequent trusted resolution operations.
步骤S305:二级节点接收并保存国家顶级节点发送的数字证书和签名。Step S305: The second-level node receives and saves the digital certificate and signature sent by the country's top-level node.
以上为国家顶级节点和二级节点之间的处理过程,也为对第一类型用户进行编码标识的预先执行过程。The above is the processing procedure between the country's top-level node and the second-level node, and is also the pre-execution procedure for coding and identifying the first type of user.
下面介绍权威企业节点对第二类型用户的认证过程。The following describes the authentication process for the second type of user by the authoritative enterprise node.
步骤S306:权威企业节点向二级节点发送认证请求,认证请求包括第一类型用户信息。Step S306: The authoritative enterprise node sends an authentication request to the secondary node, where the authentication request includes the first type of user information.
权威企业节点接收其它第一类型用户发送的认证请求后,会转发认证请求至二级节点,由二级节点处理第一类型用户的认证请求。After receiving the authentication request sent by other first-type users, the authoritative enterprise node will forward the authentication request to the second-level node, and the second-level node will process the authentication request of the first-type user.
步骤S307:二级节点生成企业前缀标识,并利用二级节点的私钥对企业前缀标识进行签名操作生成签名,构建并发送企业认证结果至权威企业节点,权威企业节点发送企业认证结果至第一类型用户。Step S307: the secondary node generates an enterprise prefix identifier, and uses the private key of the secondary node to perform a signature operation on the enterprise prefix identifier to generate a signature, constructs and sends the enterprise authentication result to the authoritative enterprise node, and the authoritative enterprise node sends the enterprise authentication result to the first type user.
二级节点按照一定的规则生成企业前缀标识,然后利用二级节点的私钥对企业前缀标识进行签名操作生成签名,构建并发送企业认证结果至权威企业节点。其中企业认证结果即为利用二级节点的私钥对企业前缀标识进行签名操作生成签名。The secondary node generates the enterprise prefix identifier according to certain rules, and then uses the private key of the secondary node to perform a signature operation on the enterprise prefix identifier to generate a signature, and constructs and sends the enterprise authentication result to the authoritative enterprise node. The enterprise authentication result is to use the private key of the secondary node to perform a signature operation on the enterprise prefix identification to generate a signature.
步骤S308:二级节点向国家顶级节点发送第一类型用户标识和二级节点标识的对应关系。Step S308: The second-level node sends the correspondence between the first-type user identifier and the second-level node identifier to the country's top-level node.
步骤S309:国家顶级节点保存第一类型用户标识和二级节点标识的对应关系。Step S309: The country top-level node saves the correspondence between the first-type user identifier and the second-level node identifier.
国家顶级节点可以保存二级节点标识和第一类型用户标识的对应关系,以便后续进行可信解析时使用。The national top-level node can save the corresponding relationship between the second-level node ID and the first-type user ID for subsequent use in trusted resolution.
对于第二类型用户的认证过程本发明提供了三种实现方式。The present invention provides three implementation manners for the authentication process of the second type of user.
第一种实现方式:仅利用标识密码系统IBC进行签名的方式。The first implementation way: only use the identification cryptosystem IBC to sign.
所述权威企业节点集成有标识密码系统IBC,则权威企业节点确定与所述第二类型用户对应的签名信息,包括:获取所述第二类型用户对应的用户身份标识;基于标识密码系统IBC将所述用户身份标识作为秘钥,将所述秘钥作为所述签名信息;The authoritative enterprise node is integrated with the identification cryptography system IBC, and the authoritative enterprise node determines the signature information corresponding to the second type of user, including: obtaining the user identity corresponding to the second type of user; The user identity is used as a secret key, and the secret key is used as the signature information;
则所述利用所述签名信息对所述普通用户标识进行签名操作生成的签名包括:利用所述秘钥对所述普通用户标识执行签名操作获得签名。Then, the signature generated by using the signature information to perform a signature operation on the common user identifier includes: using the secret key to perform a signature operation on the common user identifier to obtain a signature.
本申请提供了一种物理实体的认证方法的实施例三,来介绍第一种实现方式。本实施例应用于图1权威企业节点所示的工业互联网系统中的权威企业节点。参见图4a或4b,可以包括以下步骤:The present application provides Embodiment 3 of an authentication method for a physical entity, to introduce the first implementation manner. This embodiment is applied to the authoritative enterprise node in the industrial Internet system shown by the authoritative enterprise node in FIG. 1 . Referring to Figure 4a or 4b, the following steps may be included:
步骤S401:权威企业节点获取所述第二类型用户对应的用户身份标识。Step S401: The authoritative enterprise node obtains the user identity corresponding to the second type of user.
权威企业节点预先集成标识密码系统IBC,权威企业节点可以接收第二类型用户发送的认证请求;其中所述认证请求包括用户身份标识。The authoritative enterprise node is pre-integrated with the identification and cryptography system IBC, and the authoritative enterprise node can receive the authentication request sent by the second type of user; wherein the authentication request includes the user identity identifier.
步骤S402:权威企业节点基于标识密码系统IBC将所述用户身份标识作为秘钥。也即本实施例中将所述秘钥作为所述签名信息。步骤S403:权威企业节点对所述第二类型用户进行认证生成普通用户标识,利用所述秘钥对所述普通用户标识执行签名操作获得签名。Step S402: The authoritative enterprise node uses the user identity as a secret key based on the identity cryptography system IBC. That is, in this embodiment, the secret key is used as the signature information. Step S403: The authoritative enterprise node authenticates the second type of user to generate a common user identifier, and uses the secret key to perform a signature operation on the common user identifier to obtain a signature.
权威企业节点对所述第二类型用户进行认证生成普通用户标识,关于具体认证过程已为成熟技术,在此不再赘述。The authoritative enterprise node authenticates the user of the second type to generate a common user identifier. The specific authentication process is a mature technology and will not be repeated here.
步骤S404:权威企业节点构建并发送用户认证结果至第二类型用户。Step S404: The authoritative enterprise node constructs and sends the user authentication result to the second type user.
其中所述用户认证结果包括所述签名信息,以及,利用所述签名信息对所述普通用户标识进行签名操作生成的签名。The user authentication result includes the signature information, and a signature generated by using the signature information to perform a signature operation on the common user identifier.
为了保证普通用户标识的安全性,本发明利用标识密码系统IBC的技术思路,将所述用户身份标识作为私钥,以便利用私钥对普通用户标识进行签名操作。由于标识密码系统IBC的技术中私钥与用户身份标识具有强相关性,所以采用用户身份标识可以作为私钥,无需额外生成私钥,非常简单方便。In order to ensure the security of the common user identification, the present invention utilizes the technical idea of the identification cryptosystem IBC, and uses the user identification as a private key, so as to use the private key to perform a signature operation on the common user identification. Due to the strong correlation between the private key and the user ID in the technology of identifying the cryptographic system IBC, the user ID can be used as the private key without additional private key generation, which is very simple and convenient.
由于用户身份标识即为私钥,所以在简单方便之余安全等级不高,所以第一种实现方式较为适用于对于安全性要求不是非常高的第二类型用户。Since the user identification is the private key, the security level is not high in addition to simplicity and convenience, so the first implementation method is more suitable for the second type of users who do not have very high security requirements.
第二种实现方式:仅利用第三方颁发的数字证书进行签名的方式。The second implementation method: only use the digital certificate issued by the third party to sign.
权威企业节点与第三方认证机构相连,则所述确定与所述第二类型用户对应的签名信息,包括:接收第三方认证机构针对所述第二类型用户生成并发送的数字证书,将所述数字证书作为所述签名信息;If the authoritative enterprise node is connected to a third-party certification authority, the determining the signature information corresponding to the second-type user includes: receiving a digital certificate generated and sent by a third-party certification authority for the second-type user, and converting the a digital certificate as the signature information;
则所述利用所述签名信息对所述普通用户标识进行签名操作生成的签名包括:利用所述数字证书对所述普通用户标识执行签名操作获得签名。Then, the signature generated by using the signature information to perform a signature operation on the common user identifier includes: using the digital certificate to perform a signature operation on the common user identifier to obtain a signature.
本申请提供了一种物理实体的认证方法的实施例四,来介绍第二种实现方式:仅利用第三方颁发的数字证书进行签名的方式。本实施例应用于图1b所示的工业互联网系统中的权威企业节点。This application provides Embodiment 4 of an authentication method for a physical entity, to introduce the second implementation manner: a manner of signing only by using a digital certificate issued by a third party. This embodiment is applied to the authoritative enterprise node in the industrial Internet system shown in FIG. 1b.
参见图5a或5b,可以包括以下步骤:Referring to Figure 5a or 5b, the following steps may be included:
步骤S501:权威企业节点接收用户节点发送的认证请求。Step S501: the authoritative enterprise node receives the authentication request sent by the user node.
步骤S502:权威企业节点转发所述认证请求至第三方认证机构。Step S502: The authoritative enterprise node forwards the authentication request to a third-party authentication agency.
步骤S503:权威企业节点接收第三方认证机构对所述第二类型用户生成并发送的数字证书。本实施例中将数字证书作为所述签名信息。Step S503: The authoritative enterprise node receives the digital certificate generated and sent by the third-party certification authority for the second type of user. In this embodiment, a digital certificate is used as the signature information.
步骤S504:权威企业节点对所述第二类型用户进行认证生成普通用户标识,利用所述数字证书对所述普通用户标识执行签名操作获得签名。Step S504: The authoritative enterprise node authenticates the second type of user to generate a common user identifier, and uses the digital certificate to perform a signature operation on the common user identifier to obtain a signature.
权威企业节点对所述第二类型用户进行认证生成普通用户标识,关于具体认证过程已为成熟技术,在此不再赘述。步骤S505:权威企业节点构建并发送用户认证结果至第二类型用户;其中所述用户认证结果包括所述签名信息,以及,利用所述签名信息对所述普通用户标识进行签名操作生成的签名。The authoritative enterprise node authenticates the user of the second type to generate a common user identifier. The specific authentication process is a mature technology and will not be repeated here. Step S505: The authoritative enterprise node constructs and sends the user authentication result to the second type of user; wherein the user authentication result includes the signature information, and a signature generated by using the signature information to perform a signature operation on the common user identifier.
为了保证普通用户标识的安全性,本发明利用第三方认证机构生成数字证书,并利用数字证书作为私钥,以便利用私钥对普通用户标识进行签名操作。由于第三方认证机构生成的数字证书其安全性较高,因此本方式的安全性较高。In order to ensure the security of the common user identification, the present invention uses a third-party certification body to generate a digital certificate, and uses the digital certificate as a private key, so as to use the private key to perform a signature operation on the common user identification. Since the digital certificate generated by the third-party certification body has higher security, this method has higher security.
由于需要采用第三方认证机构生成数字证书,数字证书的签名、更新和存储需要较为繁琐,所以在安全较高之余处理过程较为繁琐,所以第二种实现方式可以适用于对于安全性要求较高的第二类型用户。当然也适用于对安全性要求较低的节点。Since a third-party certification body needs to be used to generate a digital certificate, the signature, update, and storage of the digital certificate need to be cumbersome, so the processing process is cumbersome in addition to higher security, so the second implementation method can be applied to higher security requirements. the second type of users. Of course, it also applies to nodes with lower security requirements.
第三种实现方式:采用标识密码系统IBC进行签名的方式或者利用第三方颁发的数字证书进行签名的方式。The third implementation mode: use the identification cryptosystem IBC to sign or use a digital certificate issued by a third party to sign.
所述权威企业节点集成有标识密码系统IBC,且与第三方认证机构相连,则所述确定与所述第二类型用户对应的签名信息,包括:The authoritative enterprise node is integrated with the identification and cryptography system IBC, and is connected to a third-party certification authority, then the determining the signature information corresponding to the second type of user includes:
权威企业节点判断所述第二类型用户是否指定第三方认证机构的签名方式;The authoritative enterprise node judges whether the second type of user specifies the signature method of the third-party certification authority;
若所述第二类型用户未指定第三方认证机构的签名方式,则获取所述第二类型用户对应的用户身份标识;基于标识密码系统IBC将所述用户身份标识作为秘钥,将所述秘钥作为所述签名信息;则所述利用所述签名信息对所述普通用户标识进行签名操作生成的签名包括:利用所述秘钥对所述普通用户标识执行签名操作获得签名;If the second type of user does not specify the signature method of the third-party certification authority, the user identity corresponding to the second type of user is obtained; based on the identification cryptography system IBC, the user identity is used as a secret key, and the secret The key is used as the signature information; then the signature generated by using the signature information to perform a signature operation on the common user identification includes: using the secret key to perform a signature operation on the common user identification to obtain a signature;
若所述第二类型用户指定第三方认证机构的签名方式,则接收第三方认证机构针对所述第二类型用户生成并发送的数字证书,将所述数字证书作为所述签名信息;则所述利用所述签名信息对所述普通用户标识进行签名操作生成的签名包括:利用所述数字证书对所述普通用户标识执行签名操作获得签名。If the second-type user specifies the signature method of the third-party certification authority, the digital certificate generated and sent by the third-party certification authority for the second-type user is received, and the digital certificate is used as the signature information; then the The signature generated by using the signature information to perform a signing operation on the common user identifier includes: using the digital certificate to perform a signing operation on the common user identifier to obtain a signature.
即为了兼容第一种实现方式和第二种实现方式,本申请提供了一种物理实体的认证方法的实施例五,来介绍第三种实现方式采用标识密码系统IBC进行签名的方式或者利用第三方颁发的数字证书进行签名的方式。本实施例应用于图1c所示的工业互联网系统中的权威企业节点。That is, in order to be compatible with the first implementation manner and the second implementation manner, the present application provides Embodiment 5 of an authentication method for a physical entity, to introduce the third implementation manner in which the signature cryptosystem IBC is used for signing or the third implementation manner is used. The digital certificate issued by the third party to sign. This embodiment is applied to the authoritative enterprise node in the industrial Internet system shown in FIG. 1c.
参见图6,可以包括以下步骤:Referring to Figure 6, the following steps may be included:
步骤S601:判断所述第二类型用户是否指定第三方认证机构的签名方式。Step S601: Determine whether the second type of user specifies a signature method of a third-party certification authority.
步骤S602:若所述第二类型用户未指定第三方认证机构的签名方式,则执行图4a所示的实施例。Step S602: If the second type of user does not specify the signature method of the third-party certification authority, the embodiment shown in FIG. 4a is executed.
步骤S603:若第二类型用户指定第三方认证机构的签名方式,则执行图5a所示的实施例。Step S603: If the second-type user specifies the signature method of the third-party certification authority, the embodiment shown in FIG. 5a is executed.
关于步骤S602可以详见图4权威企业节点所示的实施例,步骤S603可以详见图5a所示的实施例,在此不再赘述。For details about step S602, refer to the embodiment shown in the authoritative enterprise node in FIG. 4, and for step S603, refer to the embodiment shown in FIG. 5a, which will not be repeated here.
由于本实施例中具有两种不同的签名方式,由于签名方式不同后续的解析方式也不同,为了便于后续解析时能够区分两种不同的签名方式,本发明提供了一种用户认证结果的数据结构。Since there are two different signature methods in this embodiment, and since the subsequent analysis methods are also different for different signature methods, in order to facilitate the distinction between the two different signature methods during subsequent analysis, the present invention provides a data structure of a user authentication result .
所述用户认证结果的数据结构可以包括以下字段:The data structure of the user authentication result may include the following fields:
签名类型字段(可以采用HS_TI表示),用于存储所述签名类型。The signature type field (which can be represented by HS_TI) is used to store the signature type.
数字证书字段(可以采用HS_C权威企业节点CERT表示),用于存储采用第三方认证机构生成的数字证书,在未采用第三方认证机构生成的数字证书的情况下该字段为空。The digital certificate field (which can be represented by the HS_C authoritative enterprise node CERT) is used to store the digital certificate generated by the third-party certification authority, and this field is empty when the digital certificate generated by the third-party certification authority is not adopted.
签名字段(可以采用HS_C权威企业节点SIG表示),用于存储签名。The signature field (which can be represented by the HS_C authoritative enterprise node SIG) is used to store the signature.
用户认证结果的详细结构如下:The detailed structure of the user authentication result is as follows:
其中所述签名类型字段的数据值为第一类型或第二类型;Wherein the data value of the signature type field is the first type or the second type;
第一类型,用于表示借助于IBC生成的秘钥对普通用户标识进行签名操作的签名方式;其中,第一类型可以采用HS_SI表示。The first type is used to indicate a signature method for performing a signature operation on a common user identity with the help of the secret key generated by the IBC; wherein, the first type can be represented by HS_SI.
第二类型,用于表示借助于第三方认证机构生成的数字证书对普通用户标识进行签名操作的签名方式;其中第二类型可以采用HS_SIG表示。The second type is used to represent the signature method for performing the signature operation on the common user identity by means of a digital certificate generated by a third-party certification authority; wherein the second type can be represented by HS_SIG.
针对步骤S602中采用图4权威企业节点所示实施例生成的用户认证结果,可以表示为:For the user authentication result generated by adopting the embodiment shown in the authoritative enterprise node in FIG. 4 in step S602, it can be expressed as:
其中,签名类型字段(HS_TI字段),用于存储第一类型也即HS_SI。The signature type field (HS_TI field) is used to store the first type, that is, HS_SI.
数字证书字段(HS_C权威企业节点CERT字段),无数字证书所以为空值;Digital certificate field (HS_C authoritative enterprise node CERT field), there is no digital certificate so it is empty;
签名字段(HS_C权威企业节点SIG字段),用于存储签名数据(采用密码标识系统IBC方式进行签名操作后生成的签名数据)。The signature field (the SIG field of the HS_C authoritative enterprise node) is used to store the signature data (the signature data generated after the signature operation is performed in the IBC method of the cryptographic identification system).
针对步骤S603中采用图5权威企业节点所示实施例生成的用户认证结果,可以表示为:For the user authentication result generated by adopting the embodiment shown in the authoritative enterprise node in FIG. 5 in step S603, it can be expressed as:
其中,签名类型字段(HS_TI字段),用于存储第二类型也即HS_SIG。Among them, the signature type field (HS_TI field) is used to store the second type, that is, HS_SIG.
数字证书字段(HS_C权威企业节点CERT字段),用于存储数字证书数据;Digital certificate field (HS_C authoritative enterprise node CERT field), used to store digital certificate data;
签名字段(HS_C权威企业节点SIG字段),用于存储签名数据(采用第三方认证机构生成的数字证书进行签名操作后生成的签名数据)。The signature field (the SIG field of the HS_C authoritative enterprise node) is used to store the signature data (the signature data generated after the signature operation is performed with the digital certificate generated by the third-party certification authority).
因为在互联网系统中有的第二类型用户需要较高安全性,有的第二类型用户不必采用较高的安全性,所以提供了一种可以兼容第一种实现方式和第二种实现方式的方案。Because some second-type users in the Internet system require higher security, and some second-type users do not have to adopt higher security, a system that is compatible with the first and second implementations is provided. Program.
第三种实现方式中既可以针对需要安全性较高的第二类型用户采用第三方认证机构的方式进行签名,对于安全性不高的第二类型用户可以采用标识密码系统IBC进行签名的方式。In the third implementation manner, a third-party authentication agency can be used to sign for the second type of users who need high security, and the identification cryptosystem IBC can be used to sign for the second type of users with low security.
本方案中利用密码标识系统IBC技术思路,将用户身份标识作为私钥,即用户身份标识与私钥具有强相关性,省去数字证书来构建用户身份标识与私钥的关系,从而节省用来数字证书的存储空间,简化处理流程,提升认证效率。In this scheme, the technical idea of the password identification system IBC is used, and the user identification is used as the private key, that is, the user identification and the private key have a strong correlation, and the digital certificate is omitted to construct the relationship between the user identification and the private key. The storage space for digital certificates simplifies the processing process and improves the authentication efficiency.
对于对安全性要求较高的第二类型用户,也能够兼容在IBC技术思路基础上,兼容第三方认证机构的签名方式,做到针对不同的第二类型用户设置不同的安全级别。For the second type of users with higher security requirements, it can also be compatible with the signature method of the third-party certification agency based on the IBC technical idea, so that different security levels can be set for different second type users.
下面介绍一种物理实体的可信解析方法的实施例一,本实施例互联网系统的中公共递归解析节点205。参见图7,可以包括以下步骤:The following introduces the first embodiment of a method for trusted analysis of physical entities, which is a common
步骤S701:公共递归解析节点接收当前用户发送的可信解析请求。Step S701: The public recursive parsing node receives the trusted parsing request sent by the current user.
在当前用户通过工业互联网体系访问权威企业节点时,为了保证安全性,通常会由公共递归解析节点进行可信解析,待可信解析成功后才允许当前用户访问权威企业节点的数据。When the current user accesses the authoritative enterprise node through the industrial Internet system, in order to ensure security, the public recursive parsing node usually conducts trusted parsing, and the current user is allowed to access the data of the authoritative enterprise node after the trusted parsing is successful.
公共递归解析节点可以接收第一类型用户发送的可信解析请求,也可以接收第二类型用户发送的可信解析请求,所以可信解析请求可以为针对第一类型用户进行解析的企业可信解析请求(其中包含企业认证结果),还可以为针对第二类型用户进行解析的用户可信解析请求(其中包含用户认证结果)。The public recursive parsing node can receive trusted parsing requests sent by users of the first type, and can also receive trusted parsing requests sent by users of the second type. Therefore, the trusted parsing request can be an enterprise trusted parsing request for the first type of users. The request (which contains the enterprise authentication result) may also be a user trusted resolution request (which contains the user authentication result) that is parsed for users of the second type.
步骤S702:在所述当前用户为第一类型用户的情况下,公共递归解析节点采用递归方式对所述可信解析请求中企业认证结果中的签名进行可信解析操作,获得可信解析结果。Step S702: In the case that the current user is a user of the first type, the public recursive parsing node performs a trusted parsing operation on the signature in the enterprise authentication result in the trusted parsing request in a recursive manner to obtain a trusted parsing result.
步骤S703:在所述当前用户为第二类型用户情况下,公共递归解析节点对所述可信解析请求中用户认证结果中的签名信息和签名进行可信解析操作,获得可信解析结果。Step S703: In the case where the current user is a second type user, the public recursive parsing node performs a trusted parsing operation on the signature information and signature in the user authentication result in the trusted parsing request to obtain a trusted parsing result.
在当前用户为第一类型用户,所述可信解析请求包括企业认证结果的情况下对解析过程进行详细说明。本申请提供了一种物理实体的可信解析方法的实施例二。参见图8a或8b,所述包括以下步骤:The parsing process will be described in detail under the condition that the current user is the first type of user and the trusted parsing request includes the enterprise authentication result. The present application provides a second embodiment of a method for trusted analysis of physical entities. Referring to Figure 8a or 8b, the steps described include the following:
步骤S800:公共递归解析节点判断本地密码机是否存储有与所述可信解析请求中第一类型用户标识对应的历史可信解析结果。若是进入步骤S801,若否则进入步骤S802。Step S800: The public recursive parsing node judges whether the local cryptographic machine stores the historical trusted parsing result corresponding to the first type of user identifier in the trusted parsing request. If yes, go to step S801, otherwise go to step S802.
若存储有与所述可信解析请求中历史可信解析结果且历史可信解析结果有效,则使用所述历史可信解析结果作为所述可信解析结果。若未存储有与所述可信解析请求中历史可信解析结果则进入步骤S802。If the historical trusted analysis result in the trusted analysis request is stored and the historical trusted analysis result is valid, the historical trusted analysis result is used as the trusted analysis result. If the historical trusted analysis result in the trusted analysis request is not stored, step S802 is entered.
步骤S801:公共递归解析节点使用所述历史可信解析结果作为所述可信解析结果。Step S801: The public recursive parsing node uses the historical trusted parsing result as the trusted parsing result.
步骤S802:公共递归解析节点向国家顶级节点查询第一类型用户标识,国家顶级节点返回与所述第一类型用户标识关联的二级节点的网络地址和二级节点的数字证书。Step S802: The public recursive parsing node queries the country top-level node for the first-type user ID, and the national top-level node returns the network address of the second-level node associated with the first-type user ID and the digital certificate of the second-level node.
可信解析请求包括第一类型用户标识和企业认证结果,企业认证结果包括签名。公共递归解析节点向国家顶级节点查询第一类型用户标识,以获知该第一类型用户标识在那个二级节点下。The trusted resolution request includes the first type user identifier and the enterprise authentication result, and the enterprise authentication result includes the signature. The public recursive parsing node queries the country top-level node for the first-type user ID, so as to know which second-level node the first-type user ID is under.
步骤S803:公共递归解析节点基于二级节点的网络地址确定二级节点,并在二级节点查询所述第一类型用户标识,二级节点返回第一类型用户的网络地址和与第一类型用户标识对应的签名。Step S803: The public recursive parsing node determines the second-level node based on the network address of the second-level node, and queries the first-type user identifier on the second-level node, and the second-level node returns the network address of the first-type user and the network address of the first-type user. Identifies the corresponding signature.
二级节点反馈第一类型用户的网络地址,以用于从基于网络地址查找到第一类型用户,并从第一类型用户中查询第一类型用户的相关信息以用于实现数据交换和共享。The secondary node feeds back the network address of the first type of user, so as to find the first type of user based on the network address, and query related information of the first type of user from the first type of user for data exchange and sharing.
步骤S804:公共递归解析节点验证企业认证结果中的签名与二级节点返回的第一类型用户标识对应的签名是否一致。若一致则进入步骤S805,若不一致,则确定解析失败。Step S804: The public recursive parsing node verifies whether the signature in the enterprise authentication result is consistent with the signature corresponding to the first-type user ID returned by the secondary node. If they are consistent, go to step S805, and if they are inconsistent, it is determined that the analysis fails.
步骤S805:公共递归解析节点从国家顶级节点查询国家顶级节点的根证书,采用根证书验证二级节点的数字证书,若验证通过则进入步骤S806,若验证不通过则确定解析失败。Step S805: The public recursive parsing node queries the root certificate of the country's top-level node from the country's top-level node, and uses the root certificate to verify the digital certificate of the second-level node.
步骤S806:公共递归解析节点采用二级节点的数字证书验证企业认证结果中的签名,若验证通过则表示解析成功,否则表示解析失败。Step S806: The public recursive parsing node uses the digital certificate of the secondary node to verify the signature in the enterprise authentication result. If the verification passes, it means that the parsing is successful, otherwise, it means that the parsing fails.
步骤S807:将二级节点的网络地址、第一类型用户的网络地址和可信解析结果,与,第一类型用户标识对应存储到本地密码机中。Step S807: Store the network address of the secondary node, the network address of the first type of user, the trusted analysis result, and the first type of user identifier in the local cryptographic machine.
公共递归解析节点将二级节点的网络地址、第一类型用户的网络地址和可信解析结果,与,第一类型用户标识对应存储到本地密码机中,以便下次第一类型用户再次进行可信解析时可以在本地密码机中查找到可信解析结果和二级节点的网络地址、第一类型用户的网络地址,不必在执行可信解析过程,从而可以大大提高解析效率。The public recursive parsing node stores the network address of the second-level node, the network address of the first-type user, and the trusted parsing result, and the first-type user ID in the local cryptographic machine, so that the first-type user can perform the same operation again next time. During letter parsing, the trusted parsing result, the network address of the secondary node, and the network address of the first type of user can be found in the local cryptographic machine, without performing the trusted parsing process, which can greatly improve parsing efficiency.
与图4权威企业节点所示一种物理实体的认证方法的实施例三相对应,本发明提供了一种物理实体的可信解析方法的实施例三。参见图9所述包括以下步骤:Corresponding to the third embodiment of the authentication method for a physical entity shown in the authoritative enterprise node in FIG. 4 , the present invention provides the third embodiment of a trusted analysis method for a physical entity. Referring to Figure 9, the following steps are included:
步骤S901:接收当前用户发送的可信解析请求。本实施例中当前用户为第二类型用户。Step S901: Receive a trusted resolution request sent by the current user. In this embodiment, the current user is the second type of user.
步骤S902:在所述可信解析请求包括用户认证结果的情况下,将所述可信解析请求中的用户身份标识作为公钥。Step S902: In the case that the trusted resolution request includes a user authentication result, use the user identity in the trusted resolution request as a public key.
在图4权威企业节点对应的实施例中,采用的是用户身份标识进行签名操作,所以在可信解析过程中采用用户身份标识作为公钥,以用于对签名进行解密操作。In the embodiment corresponding to the authoritative enterprise node in FIG. 4 , the user identity is used for the signature operation, so the user identity is used as the public key in the trusted resolution process to decrypt the signature.
步骤S903:利用所述公钥对所述签名进行解密操作。Step S903: Decrypt the signature by using the public key.
步骤S904:若解密成功则确定可信解析成功,若解密失败则确定可信解析失败。Step S904: If the decryption succeeds, it is determined that the trusted parsing is successful, and if the decryption fails, it is determined that the trusted parsing fails.
与图5权威企业节点所示一种物理实体的认证方法的实施例四相对应,本发明提供了一种物理实体的可信解析方法的实施例四。参见图10所述包括以下步骤:Corresponding to Embodiment 4 of an authentication method for a physical entity shown in an authoritative enterprise node in FIG. 5 , the present invention provides Embodiment 4 of a method for authenticating a physical entity. Referring to Figure 10, the following steps are included:
步骤S1001:接收当前用户发送的可信解析请求。Step S1001: Receive a trusted resolution request sent by the current user.
步骤S1002:在所述可信解析请求包括用户认证结果的情况下,将所述数字证书作为公钥。Step S1002: in the case that the trusted resolution request includes a user authentication result, use the digital certificate as a public key.
步骤S1003:利用所述公钥对所述签名进行解密操作。Step S1003: Decrypt the signature by using the public key.
步骤S1004:若解密失败确定可信解析失败。Step S1004: If the decryption fails, it is determined that the trusted analysis fails.
步骤S1005:若解密成功则获取第三方认证机构的根证书。Step S1005: If the decryption is successful, obtain the root certificate of the third-party certification authority.
步骤S1006:利用所述第三方认证机构的根证书对所述数字证书进行验证。Step S1006: Use the root certificate of the third-party certification authority to verify the digital certificate.
步骤S1007:若验证成功则确定可信解析成功,否则确定可信解析失败。Step S1007: If the verification is successful, it is determined that the trusted parsing is successful; otherwise, it is determined that the trusted parsing fails.
与图6所示一种物理实体的认证方法的实施例五相对应,本发明提供了一种物理实体的可信解析方法的实施例五。参见图11a,所述包括以下步骤:Corresponding to Embodiment 5 of a method for authenticating a physical entity shown in FIG. 6 , the present invention provides Embodiment 5 of a method for authenticating a physical entity. Referring to Fig. 11a, the description includes the following steps:
步骤S1101:接收当前用户发送的可信解析请求。Step S1101: Receive a trusted resolution request sent by the current user.
步骤S1102:在所述可信解析请求包括用户认证结果的情况下,判断是否指定采用数字证书的方式执行可信解析操作;若是则进入步骤S1103,若否则进入步骤S1107。Step S1102: In the case that the trusted resolution request includes a user authentication result, determine whether to specify to use a digital certificate to perform the trusted resolution operation; if so, go to step S1103; otherwise, go to step S1107.
用户认证结果包括签名类型字段、数字证书字段和签名字段。其中所述签名类型字段的数据值为第一类型或第二类型。The user authentication result includes a signature type field, a digital certificate field, and a signature field. The data value of the signature type field is the first type or the second type.
第一类型,用于表示借助于IBC生成的秘钥对普通用户标识进行签名操作的签名方式;其中,第一类型可以采用HS_SI表示。The first type is used to indicate a signature method for performing a signature operation on a common user identity with the help of the secret key generated by the IBC; wherein, the first type can be represented by HS_SI.
第二类型,用于表示借助于第三方认证机构生成的数字证书对普通用户标识进行签名操作的签名方式;其中第二类型可以采用HS_SIG表示。The second type is used to represent the signature method for performing the signature operation on the common user identity by means of a digital certificate generated by a third-party certification authority; wherein the second type can be represented by HS_SIG.
因此若用户认证结果中签名类型为第一类型,则进入步骤S1103;若为第二类型则进入步骤S1107。Therefore, if the signature type in the user authentication result is the first type, go to step S1103; if it is the second type, go to step S1107.
步骤S1103:从所述签名字段提取签名。Step S1103: Extract the signature from the signature field.
步骤S1104:将所述可信解析请求中的用户身份标识作为公钥。Step S1104: Use the user identity in the trusted resolution request as the public key.
步骤S1105:利用所述公钥对所述签名进行解密操作;Step S1105: use the public key to decrypt the signature;
步骤S1106:若解密成功则确定可信解析成功,否则确定可信解析失败。Step S1106: If the decryption is successful, it is determined that the trusted parsing is successful; otherwise, it is determined that the trusted parsing fails.
步骤S1107:从所述签名字段提取签名,从所述数字证书字段提取数字证书。Step S1107: Extract the signature from the signature field, and extract the digital certificate from the digital certificate field.
步骤S1108:将所述数字证书作为公钥,利用所述公钥对所述签名进行解密操作;若解密失败确定可信解析失败。Step S1108: Take the digital certificate as a public key, and use the public key to decrypt the signature; if the decryption fails, it is determined that the trusted parsing fails.
步骤S1109:若解密成功则获取第三方认证机构的根证书。Step S1109: If the decryption is successful, obtain the root certificate of the third-party certification authority.
步骤S1110:利用所述第三方认证机构的根证书对所述数字证书进行验证。Step S1110: Use the root certificate of the third-party certification authority to verify the digital certificate.
步骤S1111:若验证成功则确定可信解析成功,否则确定可信解析失败。Step S1111: If the verification is successful, it is determined that the trusted parsing is successful; otherwise, it is determined that the trusted parsing fails.
可以理解的是,认证和可信解析是一对对应的过程。It can be understood that authentication and trusted resolution are a pair of corresponding processes.
若在认证过程中采用用户身份标识作为秘钥进行签名的方式,在解析时也对应的采用用户身份标识作为公钥进行解析的方式。If the user identity is used as the secret key for signature in the authentication process, the user identity as the public key is also used for parsing during parsing.
若在认证过程中采用指定第三方认证机构提供的数字证书作为秘钥进行签名的方式,在解析时也采用数字证书作为公钥进行解析的方式。If the digital certificate provided by the designated third-party certification authority is used as the key for signature in the authentication process, the digital certificate is also used as the public key for analysis during parsing.
与图6所示一种物理实体的认证方法的实施例五相对应,本发明提供了一种物理实体的可信解析方法的实施例六。参见图11b,所述包括以下步骤:Corresponding to Embodiment 5 of a method for authenticating a physical entity shown in FIG. 6 , the present invention provides Embodiment 6 of a method for authenticating a physical entity. Referring to Fig. 11b, the description includes the following steps:
步骤S0:接收第二类型用户发送的可信解析请求。Step S0: Receive a trusted resolution request sent by the second type of user.
步骤S1:判断可信解析请求中是否有HS_TI类型的数据。若是则进入步骤S2,若否则进入步骤S4。Step S1: Determine whether there is HS_TI type data in the trusted resolution request. If yes, go to step S2, otherwise go to step S4.
步骤S2:将所述可信解析请求中的用户身份标识作为公钥验证签名HS_C权威企业节点SIG。Step S2: Use the user identity in the trusted resolution request as the public key to verify the signature HS_C authoritative enterprise node SIG.
步骤S3:判断是否验证成功。若是则确定可信解析成功;若否则确定可信解析失败。Step S3: Determine whether the verification is successful. If so, it is determined that the trusted parsing is successful; otherwise, it is determined that the trusted parsing fails.
步骤S4:判断可信解析请求中是否有HS_TI类型的数据且有HS_C权威企业节点CERT类型的数据,若否则确定可信解析失败,若是则进入步骤S5。Step S4: Determine whether there is HS_TI type data and HS_C authoritative enterprise node CERT type data in the trusted analysis request, if otherwise, it is determined that the trusted analysis fails, and if so, go to step S5.
步骤S5:采用HS_C权威企业节点CERT类型的数据作为公钥验证签名HS_C权威企业节点SIG。Step S5: Use the data of the HS_C authoritative enterprise node CERT type as the public key to verify the signature HS_C authoritative enterprise node SIG.
步骤S6:判断是否验证成功,若是则进入步骤S7。若否则确定可信解析失败。Step S6: Determine whether the verification is successful, and if so, go to Step S7. Otherwise, it is determined that the trusted parsing fails.
步骤S7:获取第三方认证机构的根证书,并利用根证书验证HS_C权威企业节点CERT类型的数据。Step S7: Obtain the root certificate of the third-party certification authority, and use the root certificate to verify the data of the CERT type of the HS_C authoritative enterprise node.
步骤S8:判断是否验证通过;若是则确定可信解析成功,若否则确定可信解析失败。Step S8 : determine whether the verification is passed; if yes, it is determined that the trusted analysis is successful; otherwise, it is determined that the trusted analysis fails.
参见图12,一种物理实体的认证装置,包括:Referring to Figure 12, an authentication device for a physical entity, including:
节点确认器121,用于权威企业节点确定待认证的当前用户;
接收器122,用于在所述当前用户为第一类型用户的情况下,权威企业节点接收二级节点发送的企业认证结果,并发送企业认证结果至第一类型用户;其中所述企业认证结果包括二级节点在生成企业前缀标识后利用私钥对所述企业前缀标识进行签名操作所生成的签名;The
节点认证器123,用于在所述当前用户为第二类型用户的情况下,权威企业节点对所述第二类型用户进行认证生成普通用户标识,确定与所述第二类型用户对应的签名信息;The
认证结果构建器124,用于基于所述普通用户标识和所述签名信息构建用户认证结果,发送用户认证结果至第二类型用户;其中所述用户认证结果包括所述签名信息,以及,利用所述签名信息对所述普通用户标识进行签名操作生成的签名。The
参见图13,本申请提供了一种物理实体的可信解析装置,包括:Referring to FIG. 13, the present application provides a trusted parsing device for physical entities, including:
接收器131,用于公共递归解析节点接收当前用户发送的可信解析请求;The
递归解析器132,用于在所述当前用户为第一类型用户的情况下,公共递归解析节点采用递归方式对所述可信解析请求中企业认证结果中的签名进行可信解析操作,获得可信解析结果;The
可信解析器133,用于在所述当前用户为第二类型用户情况下,公共递归解析节点对所述可信解析请求中用户认证结果中的签名信息和签名进行可信解析操作,获得可信解析结果。The trusted
参见图1a,本申请提供了一种工业互联网系统,包括:Referring to Figure 1a, the present application provides an industrial Internet system, including:
物理实体标识应用系统和物理实体标识服务系统;Physical entity identification application system and physical entity identification service system;
其中,物理实体标识服务系统包括:国际根节点,与国际根节点相连的国家根节点,与国家根节点相连的二级节点,与二级节点相连的权威企业节点,和,与所述国家根节点、二级节点和权威企业节点相连的公共递归解析节点;The physical entity identification service system includes: an international root node, a national root node connected to the international root node, a secondary node connected to the national root node, an authoritative enterprise node connected to the secondary node, and a national root node connected to the national root node. Public recursive parsing nodes connected to nodes, secondary nodes and authoritative enterprise nodes;
所述权威企业节点,用于确定待认证的当前用户;在所述当前用户为第一类型用户的情况下,接收二级节点发送的企业认证结果;其中所述企业认证结果包括二级节点在生成企业前缀标识后利用私钥对所述企业前缀标识进行签名操作所生成的签名;在所述当前用户为第二类型用户的情况下,权威企业节点对所述第二类型用户进行认证生成普通用户标识,确定与所述第二类型用户对应的签名信息,基于所述普通用户标识和所述签名信息构建并发送用户认证结果;其中所述用户认证结果包括所述签名信息,以及,利用所述签名信息对所述普通用户标识进行签名操作生成的签名。The authoritative enterprise node is used to determine the current user to be authenticated; in the case that the current user is a first-type user, receive the enterprise authentication result sent by the secondary node; wherein the enterprise authentication result includes the secondary node in the After the enterprise prefix identification is generated, the signature generated by performing a signature operation on the enterprise prefix identification with a private key; in the case that the current user is a second type user, the authoritative enterprise node authenticates the second type user and generates a common signature. User identification, determine the signature information corresponding to the second type of user, construct and send a user authentication result based on the common user identification and the signature information; wherein the user authentication result includes the signature information, and, using the The signature information is generated by performing a signature operation on the common user ID.
参见图1a,权威企业节点集成有标识密码系统IBC,则所述确定与所述第二类型用户对应的签名信息,包括:Referring to Fig. 1a, the authoritative enterprise node is integrated with the identification and cryptography system IBC, then the determining of the signature information corresponding to the second type of user includes:
获取所述第二类型用户对应的用户身份标识;obtaining the user identity corresponding to the second type of user;
基于标识密码系统IBC将所述用户身份标识作为秘钥,将所述秘钥作为所述签名信息;则所述利用所述签名信息对所述普通用户标识进行签名操作生成的签名包括:利用所述秘钥对所述普通用户标识执行签名操作获得签名。Based on the identification cryptography system IBC, the user identity is used as the secret key, and the secret key is used as the signature information; then the signature generated by using the signature information to perform a signature operation on the ordinary user identity includes: using the The secret key performs a signature operation on the common user ID to obtain a signature.
参见图1b,所述系统与权威企业节点相连的第三方认证机构,则所述确定与所述第二类型用户对应的签名信息,包括:Referring to Fig. 1b, if the system is connected to a third-party certification authority of an authoritative enterprise node, the determining the signature information corresponding to the second type of user includes:
接收第三方认证机构针对所述第二类型用户生成并发送的数字证书,将所述数字证书作为所述签名信息;receiving a digital certificate generated and sent by a third-party certification authority for the second type of user, and using the digital certificate as the signature information;
则所述利用所述签名信息对所述普通用户标识进行签名操作生成的签名包括:利用所述数字证书对所述普通用户标识执行签名操作获得签名。Then, the signature generated by using the signature information to perform a signature operation on the common user identifier includes: using the digital certificate to perform a signature operation on the common user identifier to obtain a signature.
所述物理实体标识应用系统包括:The physical entity identification application system includes:
与所述权威企业节点相连的企业应用APP;An enterprise application APP connected to the authoritative enterprise node;
与所述权威企业节点相连的多个第二类型用户。a plurality of users of the second type connected to the authoritative enterprise node.
参见图1c,所述权威企业节点集成有标识密码系统IBC,且,所述系统还包括与权威企业节点相连的第三方认证机构,则所述确定与所述第二类型用户对应的签名信息,包括:Referring to Fig. 1c, the authoritative enterprise node is integrated with an identification and cryptography system IBC, and the system further includes a third-party certification authority connected to the authoritative enterprise node, then the determining the signature information corresponding to the second type of user, include:
判断所述第二类型用户是否指定第三方认证机构的签名方式;Judging whether the second type of user specifies the signature method of the third-party certification authority;
若所述第二类型用户未指定第三方认证机构的签名方式,则获取所述第二类型用户对应的用户身份标识;基于标识密码系统IBC将所述用户身份标识作为秘钥,将所述秘钥作为所述签名信息;则所述利用所述签名信息对所述普通用户标识进行签名操作生成的签名包括:利用所述秘钥对所述普通用户标识执行签名操作获得签名;If the second type of user does not specify the signature method of the third-party certification authority, the user identity corresponding to the second type of user is obtained; based on the identification cryptography system IBC, the user identity is used as a secret key, and the secret The key is used as the signature information; then the signature generated by using the signature information to perform a signature operation on the common user identification includes: using the secret key to perform a signature operation on the common user identification to obtain a signature;
若所述第二类型用户指定第三方认证机构的签名方式,则接收第三方认证机构针对所述第二类型用户生成并发送的数字证书,将所述数字证书作为所述签名信息;则所述利用所述签名信息对所述普通用户标识进行签名操作生成的签名包括:利用所述数字证书对所述普通用户标识执行签名操作获得签名。If the second-type user specifies the signature method of the third-party certification authority, the digital certificate generated and sent by the third-party certification authority for the second-type user is received, and the digital certificate is used as the signature information; then the The signature generated by using the signature information to perform a signing operation on the common user identifier includes: using the digital certificate to perform a signing operation on the common user identifier to obtain a signature.
参见图1a,本申请提供一种工业互联网系统,包括:Referring to Figure 1a, the present application provides an industrial Internet system, including:
物理实体标识应用系统100和物理实体标识服务系统200;Physical entity
其中,物理实体标识服务系统包括:国际根节点,与国际根节点相连的国家根节点,与国家根节点相连的二级节点,与二级节点相连的权威企业节点,和,与所述国家根节点、二级节点和权威企业节点相连的公共递归解析节点。The physical entity identification service system includes: an international root node, a national root node connected to the international root node, a secondary node connected to the national root node, an authoritative enterprise node connected to the secondary node, and a national root node connected to the national root node. A common recursive parsing node connecting nodes, secondary nodes and authoritative enterprise nodes.
所述公共递归解析节点,用于接收当前用户发送的可信解析请求;The public recursive parsing node is used to receive a trusted parsing request sent by the current user;
在所述当前用户为第一类型用户的情况下,采用递归方式对所述可信解析请求中企业认证结果中的签名进行可信解析操作,获得可信解析结果;In the case that the current user is a user of the first type, perform a trusted analysis operation on the signature in the enterprise authentication result in the trusted analysis request in a recursive manner to obtain a trusted analysis result;
在所述当前用户为第二类型用户情况下,对所述可信解析请求中用户认证结果中的签名信息和签名进行可信解析操作,获得可信解析结果。In the case that the current user is the second type of user, a trusted analysis operation is performed on the signature information and signature in the user authentication result in the trusted analysis request to obtain a trusted analysis result.
参见图1a,所述公共递归解析节点集成有密码机,用于将第一类型用户标识和历史可信解析结果对应存储;Referring to Fig. 1a, the public recursive parsing node is integrated with a cryptographic machine, which is used to store the first-type user identifier and the historical trusted parsing result correspondingly;
则所述公共递归解析节点在采用递归方式对所述可信解析请求中企业认证结果中签名进行可信解析操作,获得可信解析结果之前,还用于:Then the public recursive parsing node performs trusted parsing operations on the signature in the enterprise authentication result in the trusted parsing request in a recursive manner, and before obtaining the trusted parsing result, is also used for:
判断本地密码机是否存储有与所述可信解析请求中第一类型用户标识对应的历史可信解析结果;judging whether the local cryptographic machine stores the historical trusted resolution result corresponding to the first type of user ID in the trusted resolution request;
若存储有与所述可信解析请求中第一类型用户标识对应的历史可信解析结果且历史可信解析结果有效,则使用所述历史可信解析结果作为所述可信解析结果;If a historical trusted analysis result corresponding to the first type of user identifier in the trusted analysis request is stored and the historical trusted analysis result is valid, the historical trusted analysis result is used as the trusted analysis result;
若未存储有与所述可信解析请求中第一类型用户标识对应的历史可信解析结果,则执行所述采用递归方式对所述企业认证结果中签名进行可信解析操作,获得可信解析结果的步骤;并且,将所述可信解析结果与所述第一类型用户标识对应存储于所述本地密码机中。If there is no historical trusted resolution result corresponding to the first type of user ID in the trusted resolution request, execute the recursive manner to perform trusted resolution on the signature in the enterprise authentication result to obtain trusted resolution and storing the trusted parsing result in the local cryptographic machine corresponding to the first-type user identifier.
参见图1a,所述权威企业节点集成有标识密码系统IBC,若用户认证结果采用密码标识系统IBC的签名方式,则所述公共递归解析节点中对所述用户认证结果中的签名信息和签名进行可信解析操作,获得可信解析结果的过程具体包括:Referring to Fig. 1a, the authoritative enterprise node is integrated with the identification cryptography system IBC, if the user authentication result adopts the signature method of the cryptographic identification system IBC, the signature information and signature in the user authentication result are performed in the public recursive parsing node. For trusted parsing operations, the process of obtaining trusted parsing results includes:
将所述可信解析请求中的用户身份标识作为公钥;Using the user identity in the trusted resolution request as the public key;
利用所述公钥对所述签名进行解密操作;Decrypt the signature using the public key;
若解密成功则确定可信解析成功,否则确定可信解析失败。If the decryption succeeds, it is determined that the trusted parsing is successful; otherwise, it is determined that the trusted parsing fails.
参见图1b,权威企业节点与第三方认证机构相连,若用户认证结果采用第三方认证机构的签名方式则所述公共递归解析节点中所述对所述用户认证结果中的签名信息和签名进行可信解析操作,获得可信解析结果的过程具体包括:Referring to Fig. 1b, the authoritative enterprise node is connected to the third-party certification authority. If the user certification result adopts the signature method of the third-party certification authority, the signature information and signature in the user certification result can be checked as described in the public recursive parsing node. Trust parsing operation, the process of obtaining trusted parsing results includes:
将所述数字证书作为公钥;use the digital certificate as a public key;
利用所述公钥对所述签名进行解密操作;Decrypt the signature using the public key;
若解密成功则获取第三方认证机构的根证书,若解密失败确定可信解析失败;If the decryption is successful, the root certificate of the third-party certification authority will be obtained. If the decryption fails, the trusted parsing will fail;
利用所述第三方认证机构的根证书对所述数字证书进行验证;Verifying the digital certificate using the root certificate of the third-party certification authority;
若验证成功则确定可信解析成功,否则确定可信解析失败。If the verification is successful, it is determined that the trusted parsing is successful; otherwise, it is determined that the trusted parsing fails.
参见图1c,所述权威企业节点集成有标识密码系统IBC,且与第三方认证机构相连,则所述公共递归解析节点中在所述用户认证结果包括签名类型字段、数字证书字段和签名字段的情况下,则所述对所述用户认证结果中的签名信息和签名进行可信解析操作,获得可信解析结果的过程具体包括:Referring to Fig. 1c, the authoritative enterprise node is integrated with the identification cryptography system IBC, and is connected to a third-party certification authority, then the user authentication result in the public recursive parsing node includes a signature type field, a digital certificate field, and a signature field. In this case, the process of performing trusted analysis on the signature information and signature in the user authentication result, and the process of obtaining the trusted analysis result specifically includes:
若所述签名类型字段指示为第一类型,则从所述签名字段提取签名,将所述可信解析请求中的用户身份标识作为公钥;利用所述公钥对所述签名进行解密操作;若解密成功则确定可信解析成功,否则确定可信解析失败;If the signature type field indicates the first type, extract a signature from the signature field, and use the user identity in the trusted resolution request as a public key; use the public key to decrypt the signature; If the decryption is successful, it is determined that the trusted parsing is successful, otherwise it is determined that the trusted parsing fails;
若所述签名类型字段指示为第二类型,则从所述签名字段提取签名,从所述数字证书字段提取数字证书;将所述数字证书作为公钥;利用所述公钥对所述签名进行解密操作;若解密成功则获取第三方认证机构的根证书,若解密失败确定可信解析失败;利用所述第三方认证机构的根证书对所述数字证书进行验证;若验证成功则确定可信解析成功,否则确定可信解析失败。If the signature type field indicates the second type, extract the signature from the signature field, and extract the digital certificate from the digital certificate field; use the digital certificate as a public key; use the public key to perform the signature on the signature Decryption operation; if decryption is successful, obtain the root certificate of the third-party certification authority; if decryption fails, determine that the trusted analysis fails; use the root certificate of the third-party certification authority to verify the digital certificate; if the verification is successful, determine the trustworthy The parsing succeeds, otherwise it is determined that the trusted parsing fails.
本实施例方法所述的功能如果以软件功能单元的形式实现并作为独立的产品销售或使用时,可以存储在一个计算设备可读取存储介质中。基于这样的理解,本申请实施例对现有技术做出贡献的部分或者该技术方案的部分可以以软件产品的形式体现出来,该软件产品存储在一个存储介质中,包括若干指令用以使得一台计算设备(可以是个人计算机,服务器,移动计算设备或者网络设备等)执行本申请各个实施例所述方法的全部或部分步骤。而前述的存储介质包括:U盘、移动硬盘、只读存储器(ROM,Read-Only Memory)、随机存取存储器(RAM,Random access Memory)、磁碟或者光盘等各种可以存储程序代码的介质。If the functions described in the method of this embodiment are implemented in the form of software functional units and sold or used as independent products, they may be stored in a readable storage medium of a computing device. Based on this understanding, the part of the embodiments of the present application that contribute to the prior art or the part of the technical solution may be embodied in the form of a software product, and the software product is stored in a storage medium and includes several instructions to make a A computing device (which may be a personal computer, a server, a mobile computing device or a network device, etc.) executes all or part of the steps of the methods described in the various embodiments of the present application. The aforementioned storage medium includes: U disk, removable hard disk, Read-Only Memory (ROM, Read-Only Memory), Random Access Memory (RAM, Random Access Memory), magnetic disk or optical disk and other media that can store program codes .
本说明书中各个实施例采用递进的方式描述,每个实施例重点说明的都是与其它实施例的不同之处,各个实施例之间相同或相似部分互相参见即可。The various embodiments in this specification are described in a progressive manner, and each embodiment focuses on the differences from other embodiments, and the same or similar parts between the various embodiments may be referred to each other.
对所公开的实施例的上述说明,使本领域专业技术人员能够实现或使用本申请。对这些实施例的多种修改对本领域的专业技术人员来说将是显而易见的,本文中所定义的一般原理可以在不脱离本申请的精神或范围的情况下,在其它实施例中实现。因此,本申请将不会被限制于本文所示的这些实施例,而是要符合与本文所公开的原理和新颖特点相一致的最宽的范围。The above description of the disclosed embodiments enables any person skilled in the art to make or use the present application. Various modifications to these embodiments will be readily apparent to those skilled in the art, and the generic principles defined herein may be implemented in other embodiments without departing from the spirit or scope of the present application. Therefore, this application is not intended to be limited to the embodiments shown herein, but is to be accorded the widest scope consistent with the principles and novel features disclosed herein.
Claims (16)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202010020929.6ACN111262834B (en) | 2020-01-09 | 2020-01-09 | Authentication and credibility analysis method, device and system for physical entity |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202010020929.6ACN111262834B (en) | 2020-01-09 | 2020-01-09 | Authentication and credibility analysis method, device and system for physical entity |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN111262834Atrue CN111262834A (en) | 2020-06-09 |
| CN111262834B CN111262834B (en) | 2022-03-29 |
Family
ID=70948598
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202010020929.6AActiveCN111262834B (en) | 2020-01-09 | 2020-01-09 | Authentication and credibility analysis method, device and system for physical entity |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN111262834B (en) |
Cited By (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN114285595A (en)* | 2021-11-12 | 2022-04-05 | 珠海大横琴科技发展有限公司 | Data processing method and device |
| CN114448729A (en)* | 2022-04-07 | 2022-05-06 | 中国信息通信研究院 | Client Identity Authentication Method and Device in Industrial Internet |
| CN115208580A (en)* | 2022-07-14 | 2022-10-18 | 北京泰尔英福科技有限公司 | Credible service positioning method and system based on industrial internet identification analysis |
| CN116319070A (en)* | 2023-05-11 | 2023-06-23 | 中国电子信息产业集团有限公司第六研究所 | Industrial Internet identification analysis system, method, electronic equipment and storage medium |
Citations (16)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN1545243A (en)* | 2003-11-24 | 2004-11-10 | 华中科技大学 | Method and system for identity authentication |
| KR101294805B1 (en)* | 2012-12-21 | 2013-08-08 | (주)씽크에이티 | 2-channel authentication method and system based on authentication application |
| CN104135365A (en)* | 2013-05-03 | 2014-11-05 | 阿里巴巴集团控股有限公司 | A method, a server, and a client for verifying an access request |
| US20160063235A1 (en)* | 2014-08-28 | 2016-03-03 | Kevin Alan Tussy | Facial Recognition Authentication System Including Path Parameters |
| CN106686152A (en)* | 2016-04-01 | 2017-05-17 | 北京泰尔英福网络科技有限责任公司 | A method for distributing identity verification information |
| US20180004930A1 (en)* | 2015-01-21 | 2018-01-04 | Fusionpipe Software Solutions | Enhanced security authentication methods, systems and media |
| CN107633402A (en)* | 2017-09-14 | 2018-01-26 | 深圳市华付信息技术有限公司 | A kind of method and its system for being used to polymerize certification |
| CN107995197A (en)* | 2017-12-04 | 2018-05-04 | 中国电子科技集团公司第三十研究所 | A kind of method for realizing across management domain identity and authority information is shared |
| CN108566272A (en)* | 2018-01-02 | 2018-09-21 | 甘肃万维信息技术有限责任公司 | Method for pushing is recognized each other in Public Key Infrastructure mutual trust based on E-Government |
| CN109617698A (en)* | 2019-01-09 | 2019-04-12 | 腾讯科技(深圳)有限公司 | Provide the method for digital certificate, digital certificate issues center and medium |
| CN109726571A (en)* | 2018-12-25 | 2019-05-07 | 航天信息股份有限公司 | Electronic signature method, device, storage medium and the electronic equipment of document |
| EP3481004A4 (en)* | 2016-06-29 | 2019-05-08 | Prosper Creative Co., Ltd. | COMMUNICATION SYSTEM, COMMUNICATION DEVICE USED THEREIN, MANAGEMENT DEVICE, AND INFORMATION TERMINAL |
| CN109861975A (en)* | 2018-12-26 | 2019-06-07 | 中国科学院计算机网络信息中心 | Industrial Internet-oriented identification registration information query method and system |
| CN109922039A (en)* | 2019-01-14 | 2019-06-21 | 湘潭大学 | A kind of identity management method of half centralization based on block chain technology |
| CN109918878A (en)* | 2019-04-24 | 2019-06-21 | 中国科学院信息工程研究所 | A blockchain-based industrial IoT device identity authentication and secure interaction method |
| CN110298610A (en)* | 2019-05-05 | 2019-10-01 | 江苏一乙生态农业科技有限公司 | A kind of Express Logistics block catenary system and its operation method |
- 2020
- 2020-01-09CNCN202010020929.6Apatent/CN111262834B/enactiveActive
Patent Citations (16)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN1545243A (en)* | 2003-11-24 | 2004-11-10 | 华中科技大学 | Method and system for identity authentication |
| KR101294805B1 (en)* | 2012-12-21 | 2013-08-08 | (주)씽크에이티 | 2-channel authentication method and system based on authentication application |
| CN104135365A (en)* | 2013-05-03 | 2014-11-05 | 阿里巴巴集团控股有限公司 | A method, a server, and a client for verifying an access request |
| US20160063235A1 (en)* | 2014-08-28 | 2016-03-03 | Kevin Alan Tussy | Facial Recognition Authentication System Including Path Parameters |
| US20180004930A1 (en)* | 2015-01-21 | 2018-01-04 | Fusionpipe Software Solutions | Enhanced security authentication methods, systems and media |
| CN106686152A (en)* | 2016-04-01 | 2017-05-17 | 北京泰尔英福网络科技有限责任公司 | A method for distributing identity verification information |
| EP3481004A4 (en)* | 2016-06-29 | 2019-05-08 | Prosper Creative Co., Ltd. | COMMUNICATION SYSTEM, COMMUNICATION DEVICE USED THEREIN, MANAGEMENT DEVICE, AND INFORMATION TERMINAL |
| CN107633402A (en)* | 2017-09-14 | 2018-01-26 | 深圳市华付信息技术有限公司 | A kind of method and its system for being used to polymerize certification |
| CN107995197A (en)* | 2017-12-04 | 2018-05-04 | 中国电子科技集团公司第三十研究所 | A kind of method for realizing across management domain identity and authority information is shared |
| CN108566272A (en)* | 2018-01-02 | 2018-09-21 | 甘肃万维信息技术有限责任公司 | Method for pushing is recognized each other in Public Key Infrastructure mutual trust based on E-Government |
| CN109726571A (en)* | 2018-12-25 | 2019-05-07 | 航天信息股份有限公司 | Electronic signature method, device, storage medium and the electronic equipment of document |
| CN109861975A (en)* | 2018-12-26 | 2019-06-07 | 中国科学院计算机网络信息中心 | Industrial Internet-oriented identification registration information query method and system |
| CN109617698A (en)* | 2019-01-09 | 2019-04-12 | 腾讯科技(深圳)有限公司 | Provide the method for digital certificate, digital certificate issues center and medium |
| CN109922039A (en)* | 2019-01-14 | 2019-06-21 | 湘潭大学 | A kind of identity management method of half centralization based on block chain technology |
| CN109918878A (en)* | 2019-04-24 | 2019-06-21 | 中国科学院信息工程研究所 | A blockchain-based industrial IoT device identity authentication and secure interaction method |
| CN110298610A (en)* | 2019-05-05 | 2019-10-01 | 江苏一乙生态农业科技有限公司 | A kind of Express Logistics block catenary system and its operation method |
Non-Patent Citations (2)
| Title |
|---|
| XINWEN ZHANG等: ""Towards name-based trust and security for content-centric network"", 《 2011 19TH IEEE INTERNATIONAL CONFERENCE ON NETWORK PROTOCOLS》* |
| 张钰雯等: ""工业互联网标识解析体系发展趋势"", 《信息通信技术与政策》* |
Cited By (7)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN114285595A (en)* | 2021-11-12 | 2022-04-05 | 珠海大横琴科技发展有限公司 | Data processing method and device |
| CN114448729A (en)* | 2022-04-07 | 2022-05-06 | 中国信息通信研究院 | Client Identity Authentication Method and Device in Industrial Internet |
| CN114448729B (en)* | 2022-04-07 | 2022-06-07 | 中国信息通信研究院 | Client Identity Authentication Method and Device in Industrial Internet |
| CN115208580A (en)* | 2022-07-14 | 2022-10-18 | 北京泰尔英福科技有限公司 | Credible service positioning method and system based on industrial internet identification analysis |
| CN115208580B (en)* | 2022-07-14 | 2024-05-24 | 北京泰尔英福科技有限公司 | Trusted service positioning method and system based on industrial Internet identification analysis |
| CN116319070A (en)* | 2023-05-11 | 2023-06-23 | 中国电子信息产业集团有限公司第六研究所 | Industrial Internet identification analysis system, method, electronic equipment and storage medium |
| CN116319070B (en)* | 2023-05-11 | 2023-08-11 | 中国电子信息产业集团有限公司第六研究所 | Industrial Internet identification analysis system, method, electronic equipment and storage medium |
Also Published As
| Publication number | Publication date |
|---|---|
| CN111262834B (en) | 2022-03-29 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN109714167B (en) | Identity authentication and key agreement method and equipment suitable for mobile application signature | |
| US8510556B2 (en) | Authentication method, system, server, and user node | |
| Xue et al. | A distributed authentication scheme based on smart contract for roaming service in mobile vehicular networks | |
| CN111262834B (en) | Authentication and credibility analysis method, device and system for physical entity | |
| CN101453476B (en) | Cross domain authentication method and system | |
| CN111447187A (en) | A cross-domain authentication method for heterogeneous IoT | |
| Al-Janabi et al. | Public-key cryptography enabled kerberos authentication | |
| Chen et al. | Quantum identity authentication scheme of vehicular ad-hoc networks | |
| WO2022135391A1 (en) | Identity authentication method and apparatus, and storage medium, program and program product | |
| Ullah et al. | A secure NDN framework for Internet of Things enabled healthcare | |
| CN113382002A (en) | Data request method, request response method, data communication system, and storage medium | |
| CN114938280A (en) | Authentication method and system based on non-interactive zero-knowledge proof and intelligent contract | |
| CN114696999A (en) | Identity authentication method and device | |
| CN114401153B (en) | Authentication method and system for smart manhole cover equipment | |
| Liu et al. | LBRAKA: Lattice-Based Robust Authenticated Key Agreement for VANETs | |
| Songshen et al. | Hash-based signature for flexibility authentication of IoT devices | |
| WO2022135379A1 (en) | Identity authentication method and apparatus | |
| CN103916372B (en) | A kind of third party's log-on message trustship method and system | |
| CN118802143A (en) | Data transmission method, device and electronic equipment | |
| CN114760032A (en) | Identity authentication method and device | |
| CN105577606A (en) | A method and device for realizing authenticator registration | |
| CN114760044A (en) | Identity authentication method and device | |
| Omori et al. | Extended inter-device digital rights sharing and transfer based on device-owner equality verification using homomorphic encryption | |
| WO2022135384A1 (en) | Identity authentication method and apparatus | |
| CN114760042A (en) | Identity authentication method and device |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |