CN110852187A - A method and system for identifying perimeter intrusion events - Google Patents
A method and system for identifying perimeter intrusion eventsDownload PDFInfo
- Publication number
- CN110852187A CN110852187ACN201911005085.1ACN201911005085ACN110852187ACN 110852187 ACN110852187 ACN 110852187ACN 201911005085 ACN201911005085 ACN 201911005085ACN 110852187 ACN110852187 ACN 110852187A
- Authority
- CN
- China
- Prior art keywords
- intrusion
- network model
- time
- identifying
- signals
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F2218/00—Aspects of pattern recognition specially adapted for signal processing
- G06F2218/02—Preprocessing
- G06F2218/04—Denoising
- G06F2218/06—Denoising by applying a scale-space analysis, e.g. using wavelet analysis
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06N—COMPUTING ARRANGEMENTS BASED ON SPECIFIC COMPUTATIONAL MODELS
- G06N3/00—Computing arrangements based on biological models
- G06N3/02—Neural networks
- G06N3/04—Architecture, e.g. interconnection topology
- G06N3/045—Combinations of networks
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06N—COMPUTING ARRANGEMENTS BASED ON SPECIFIC COMPUTATIONAL MODELS
- G06N3/00—Computing arrangements based on biological models
- G06N3/02—Neural networks
- G06N3/08—Learning methods
- G—PHYSICS
- G08—SIGNALLING
- G08B—SIGNALLING OR CALLING SYSTEMS; ORDER TELEGRAPHS; ALARM SYSTEMS
- G08B13/00—Burglar, theft or intruder alarms
- G08B13/18—Actuation by interference with heat, light, or radiation of shorter wavelength; Actuation by intruding sources of heat, light, or radiation of shorter wavelength
- G08B13/181—Actuation by interference with heat, light, or radiation of shorter wavelength; Actuation by intruding sources of heat, light, or radiation of shorter wavelength using active radiation detection systems
- G08B13/183—Actuation by interference with heat, light, or radiation of shorter wavelength; Actuation by intruding sources of heat, light, or radiation of shorter wavelength using active radiation detection systems by interruption of a radiation beam or barrier
- G08B13/186—Actuation by interference with heat, light, or radiation of shorter wavelength; Actuation by intruding sources of heat, light, or radiation of shorter wavelength using active radiation detection systems by interruption of a radiation beam or barrier using light guides, e.g. optical fibres
Landscapes
- Engineering & Computer Science (AREA)
- Physics & Mathematics (AREA)
- Theoretical Computer Science (AREA)
- General Physics & Mathematics (AREA)
- General Engineering & Computer Science (AREA)
- Artificial Intelligence (AREA)
- Evolutionary Computation (AREA)
- Computing Systems (AREA)
- Computational Linguistics (AREA)
- Data Mining & Analysis (AREA)
- Biomedical Technology (AREA)
- General Health & Medical Sciences (AREA)
- Molecular Biology (AREA)
- Biophysics (AREA)
- Life Sciences & Earth Sciences (AREA)
- Mathematical Physics (AREA)
- Software Systems (AREA)
- Health & Medical Sciences (AREA)
- Computer Vision & Pattern Recognition (AREA)
- Signal Processing (AREA)
- Geophysics And Detection Of Objects (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明涉及光纤周界安防领域,更具体地说,涉及一种周界入侵事件的识别方法,以及一种周界入侵事件的识别系统。The invention relates to the field of optical fiber perimeter security, and more particularly, to a method for identifying perimeter intrusion events, and a system for identifying perimeter intrusion events.
背景技术Background technique
光纤周界安防通常具备抗电磁干扰,耐腐蚀以及灵敏度高,结构简单以及安全可靠等效果,一般用于基站,主要目的是为了阻止在复杂环境下的非法入侵的行为,提高系统对人为入侵事件的识别准确率,同时提高对非人为入侵的准确率。因而,在博物馆安全领域、政府利害部门、航空以及军事领域都获得很高的重视。Optical fiber perimeter security usually has the effects of anti-electromagnetic interference, corrosion resistance, high sensitivity, simple structure, safety and reliability, and is generally used in base stations. The recognition accuracy rate is improved, and the accuracy rate of non-human intrusion is improved. Therefore, it has received high attention in the field of museum security, government stakeholders, aviation and military fields.
现有技术中,中国发明专利申请201611266625.8公开了一种分布式光纤围栏振动入侵识别系统中,但其技术方案需要计算分帧处理,计算分帧的过零率和过零率,需要对有用信号的截取,对信号处理不灵敏,实时性差,计算量冗余。In the prior art, Chinese invention patent application 201611266625.8 discloses a distributed optical fiber fence vibration intrusion identification system, but its technical solution needs to calculate frame-by-frame processing, calculate the zero-crossing rate and zero-crossing rate of the frame, and need to detect useful signals. The interception is not sensitive to signal processing, the real-time performance is poor, and the amount of calculation is redundant.
中国发明专利申请201410494088.7公开了一种光纤预警及模式识别方法,但其技术方案中,系统光路复杂,存在着样本过于简单,对复杂环境下入侵事件的特征没法进行提取,只能仅限于理想环境中的入侵信号,存在着不切合工程实际应用的场合。Chinese invention patent application 201410494088.7 discloses an optical fiber early warning and pattern recognition method, but in its technical solution, the optical path of the system is complex, and there are samples that are too simple, so it is impossible to extract the characteristics of intrusion events in complex environments, and can only be limited to ideal There are occasions where the intrusion signals in the environment are not suitable for practical engineering applications.
发明内容SUMMARY OF THE INVENTION
本发明的目的在于克服现有技术的不足,提供一种周界入侵事件的识别方法,以及一种周界入侵事件的识别系统,实现对复杂环境下的人为入侵和非人为入侵事件的模式识别,并能够实现低误报率和低漏报率。The purpose of the present invention is to overcome the deficiencies of the prior art, to provide a method for identifying perimeter intrusion events, and a system for identifying perimeter intrusion events, so as to realize pattern recognition of man-made and non-artificial intrusion events in complex environments , and can achieve low false positive rate and low false negative rate.
本发明的技术方案如下:The technical scheme of the present invention is as follows:
一种周界入侵事件的识别方法,步骤如下:A method for identifying a perimeter intrusion event, the steps are as follows:
1)选定适用于已知类型的入侵信号进行识别的网络模型;1) Select a network model suitable for identification of known types of intrusion signals;
2)利用包含多种噪音的已知类型的入侵信号组成的训练集,利用选定的网络模型进行训练,利用训练完成的网络模型对实时采集的入侵信号进行识别;2) using a training set consisting of known types of intrusion signals containing multiple noises, using the selected network model for training, and using the trained network model to identify the intrusion signals collected in real time;
步骤1)中,选择适用的网络模型的方法如下:In step 1), the method of selecting the applicable network model is as follows:
1.1)采集一定数量的已知类型的入侵信号作为训练样本与测试样本,并采用小波变换对训练样本与测试样本进行滤波,再进行短时傅里叶变换,获得对应的时频图;1.1) Collect a certain number of known types of intrusion signals as training samples and test samples, and use wavelet transform to filter the training samples and test samples, and then perform short-time Fourier transform to obtain the corresponding time-frequency diagram;
1.2)利用时频图的图像特征,分别通过不同的网络模型对训练样本进行训练;1.2) Use the image features of the time-frequency map to train the training samples through different network models;
1.3)利用网络模型对测试样本进行识别;1.3) Use the network model to identify the test samples;
1.4)计算在不同的网络模型网络中,训练样本的运算时间、对训练样本的训练时间总和,以及对每个测试样本的识别时间,选定运算时间、训练时间总和、识别时间最短的网络模型。1.4) Calculate the computing time of training samples, the total training time of training samples, and the recognition time of each test sample in different network model networks, and select the network model with the shortest computing time, total training time and recognition time. .
作为优选,步骤1.1)中,比较用于短时傅里叶变换的不同的窗函数和窗宽,选择适配已知类型的入侵信号的窗函数和窗宽。Preferably, in step 1.1), different window functions and window widths for short-time Fourier transform are compared, and a window function and window width that are adapted to known types of intrusion signals are selected.
作为优选,步骤1.2)中,通过网络模型对训练样本进行训练之前,先选择深度学习优化器,并设定批次大小、迭代次数,初始化网络模型的权值w与偏置值b;然后计算输出值存在的偏差,再计算损失值;根据损失值优化权值w与偏置值b,直至偏差符合要求。Preferably, in step 1.2), before training the training samples through the network model, first select a deep learning optimizer, set the batch size and the number of iterations, and initialize the weight w and bias value b of the network model; then calculate The deviation of the output value is calculated, and then the loss value is calculated; the weight w and the bias value b are optimized according to the loss value until the deviation meets the requirements.
作为优选,已知类型的入侵信号包括人为入侵信号、非人为人侵信号;其中,人为入侵信号包括敲击、摇晃,非人为人侵信号包括刮风、下雨。Preferably, known types of intrusion signals include human intrusion signals and non-human intrusion signals; wherein, the artificial intrusion signals include knocking and shaking, and the non-artificial intrusion signals include windy and raining.
作为优选,选定的网络模型为Inception-v2结构的卷积神经网络模型。Preferably, the selected network model is a convolutional neural network model of Inception-v2 structure.
一种周界入侵事件的识别系统,包括光源、多模光纤、光电二极管、数据采集卡,光源信号经多模光纤、光电二极管后,通过数据采集卡进行数据采集;通过多模光纤感应入侵信号,在入侵信号的影响下采集的数据,基于所述的识别方法进行识别。An identification system for perimeter intrusion events, comprising a light source, a multimode optical fiber, a photodiode, and a data acquisition card. After the light source signal passes through the multimode optical fiber and the photodiode, data acquisition is performed through the data acquisition card; the intrusion signal is sensed through the multimode optical fiber. , the data collected under the influence of the intrusion signal are identified based on the identification method.
作为优选,多模光纤包括依次耦合的前单模光纤段、多模光纤段、后单模光纤段。Preferably, the multimode optical fiber includes a front single-mode optical fiber segment, a multi-mode optical fiber segment, and a rear single-mode optical fiber segment that are coupled in sequence.
作为优选,将多模光纤缠绕固定在围成周界的围网上,用于感应入侵信号。Preferably, the multimode optical fiber is wound and fixed on a perimeter fence for sensing intrusion signals.
本发明的有益效果如下:The beneficial effects of the present invention are as follows:
本发明所述的周界入侵事件的识别方法与系统,利用特征结构的多模光纤感应入侵信号,基于入侵信号经通过小波变换对其滤波、进行短时傅里叶变换获取时频图,基于训练样本与测试样本,根据工程应用指标选择合适的网络模型;再利用选定的网络模型对入侵信号进行识别。本发明能够在对复杂环境下的人为入侵和非人为入侵事件进行模式识别,对人为入侵信号和非人为入侵信号进行区分,并能够减小误报率和漏报率,并提高了多模光纤在周界防区的监测领域以及在工程领域中的应用。The method and system for identifying a perimeter intrusion event according to the present invention utilize a multi-mode optical fiber with a characteristic structure to sense the intrusion signal, filter the intrusion signal through wavelet transform, and perform short-time Fourier transform to obtain a time-frequency diagram, based on the For training samples and test samples, select the appropriate network model according to the engineering application indicators; then use the selected network model to identify the intrusion signal. The invention can perform pattern recognition on man-made intrusion and non-artificial intrusion events in complex environment, distinguish man-made intrusion signals and non-artificial intrusion signals, can reduce the false alarm rate and the false alarm rate, and improve the multi-mode fiber In the monitoring field of the perimeter defense area and the application in the engineering field.
附图说明Description of drawings
图1是本发明所述的方法的流程示意图;Fig. 1 is the schematic flow sheet of the method of the present invention;
图2是本发明所述的系统的原理示意图;Fig. 2 is the principle schematic diagram of the system of the present invention;
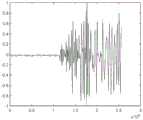
图3是入侵信号(敲击)的时频图;Figure 3 is a time-frequency diagram of an intrusion signal (knocking);
图4是入侵信号(摇晃)的时频图;Figure 4 is a time-frequency diagram of an intrusion signal (shaking);
图5是入侵信号(刮风)的时频图;Figure 5 is a time-frequency diagram of an intrusion signal (windy);
图6是入侵信号(下雨)的时频图;Figure 6 is a time-frequency diagram of an intrusion signal (raining);
图中:10是多模光纤,11是前单模光纤段,12是多模光纤段,13是后单模光纤段。In the figure: 10 is a multi-mode fiber, 11 is a front single-mode fiber segment, 12 is a multi-mode fiber segment, and 13 is a rear single-mode fiber segment.
具体实施方式Detailed ways
以下结合附图及实施例对本发明进行进一步的详细说明。The present invention will be further described in detail below with reference to the accompanying drawings and embodiments.
本发明为了解决现有技术存在的不足,提供一种周界入侵事件的识别方法,以及一种周界入侵事件的识别系统。其中,本发明所述的周界入侵事件的识别方法,如图1所示,步骤如下:In order to solve the shortcomings of the prior art, the present invention provides a method for identifying a perimeter intrusion event, and a system for identifying a perimeter intrusion event. Wherein, the method for identifying a perimeter intrusion event according to the present invention, as shown in Figure 1, has the following steps:
1)选定适用于已知类型的入侵信号进行识别的网络模型;1) Select a network model suitable for identification of known types of intrusion signals;
2)利用包含多种噪音的已知类型的入侵信号组成的训练集,利用选定的网络模型进行训练,利用训练完成的网络模型对实时采集的入侵信号进行识别。2) Using a training set consisting of known types of intrusion signals containing multiple noises, using the selected network model for training, and using the trained network model to identify the intrusion signals collected in real time.
为了简化识别过程,并减小误报率和漏报率,本发明需要筛选出与某些特定类型的入侵信号最适配的网络模型,本实施例中,步骤1)中,选择适用的网络模型的方法如下:In order to simplify the identification process and reduce the false alarm rate and the false alarm rate, the present invention needs to screen out the network model that is most suitable for some specific types of intrusion signals. In this embodiment, in step 1), select the applicable network The method of the model is as follows:
1.1)采集一定数量的已知类型的入侵信号作为训练样本与测试样本,并采用小波变换对训练样本与测试样本进行滤波,再进行短时傅里叶变换,获得对应的时频图;1.1) Collect a certain number of known types of intrusion signals as training samples and test samples, and use wavelet transform to filter the training samples and test samples, and then perform short-time Fourier transform to obtain the corresponding time-frequency diagram;
其中,为了选定适配已知类型的入侵信号的窗函数和窗宽,则在步骤1.1)中,比较用于短时傅里叶变换的不同的窗函数和窗宽,选择适配已知类型的入侵信号的窗函数和窗宽;Wherein, in order to select the window function and window width that adapt to the known type of intrusion signal, then in step 1.1), compare different window functions and window widths for short-time Fourier transform, and select to adapt to known types of intrusion signals. The window function and window width of the type of intrusion signal;
1.2)利用时频图的图像特征,分别通过不同的网络模型对训练样本进行训练;1.2) Use the image features of the time-frequency map to train the training samples through different network models;
其中,为了选择最合适的网络参数,则在步骤1.2)中,通过网络模型对训练样本进行训练之前,先选择深度学习优化器,并设定批次大小、迭代次数,初始化网络模型的权值w与偏置值b;然后计算输出值存在的偏差,再计算损失值;根据损失值优化权值w与偏置值b,直至偏差符合要求;Among them, in order to select the most suitable network parameters, in step 1.2), before training the training samples through the network model, first select the deep learning optimizer, and set the batch size, the number of iterations, and initialize the weights of the network model. w and bias value b; then calculate the deviation of the output value, and then calculate the loss value; optimize the weight w and the bias value b according to the loss value until the deviation meets the requirements;
1.3)利用网络模型对测试样本进行识别;1.3) Use the network model to identify the test samples;
1.4)计算在不同的网络模型网络中,训练样本的运算时间、对训练样本的训练时间总和,以及对每个测试样本的识别时间,选定运算时间、训练时间总和、识别时间最短的网络模型。1.4) Calculate the computing time of training samples, the total training time of training samples, and the recognition time of each test sample in different network model networks, and select the network model with the shortest computing time, total training time and recognition time. .
本实施例中,已知类型的入侵信号包括人为入侵信号、非人为人侵信号;其中,人为入侵信号包括敲击、摇晃,非人为人侵信号包括刮风、下雨。进而,选定的网络模型为Inception-v2结构的卷积神经网络模型。In this embodiment, known types of intrusion signals include human intrusion signals and non-human intrusion signals; wherein, the artificial intrusion signals include knocking and shaking, and the non-human intrusion signals include windy and raining. Furthermore, the selected network model is the convolutional neural network model of the Inception-v2 structure.
基于所述的识别方法,本发明还提供一种周界入侵事件的识别系统,如图2所示,包括光源、多模光纤10、光电二极管、数据采集卡,光源信号经多模光纤10、光电二极管后,通过数据采集卡进行数据采集;通过多模光纤10感应入侵信号,在入侵信号的影响下采集的数据,基于所述的识别方法进行识别。Based on the identification method, the present invention also provides an identification system for perimeter intrusion events, as shown in FIG. 2 , including a light source, a multimode
本实施例中,多模光纤10包括依次耦合的前单模光纤段11、多模光纤段12、后单模光纤段13。其中,前单模光纤段11与多模光纤段12的熔接处,损耗为0.02db,后单模光纤段13与多模光纤段12的熔接处,损耗为0.01db。In this embodiment, the multimode
实施时,将多模光纤10缠绕固定在围成周界的围网上,用于感应入侵信号。具体地,整条多模光纤10长度为300米,将其缠绕在铁丝网上,并用铁箍锁住,则所述的敲击为铁棒子敲击铁丝网,摇晃为使用手摇晃的铁丝网。During implementation, the multimode
本实施例采用的光源为激光器,其波长为1550nm,强度为13dbm,用耦合器连接到前单模光纤段的熔接点处。数据采集卡采用为16位25MSPS的1601B数据采集卡,采样深度设置为256k,采样率设置为100khz。The light source used in this embodiment is a laser with a wavelength of 1550 nm and an intensity of 13 dbm, which is connected to the fusion point of the front single-mode fiber segment by a coupler. The data acquisition card is a 1601B data acquisition card with 16-bit 25MSPS, the sampling depth is set to 256k, and the sampling rate is set to 100khz.
本实施例中,对每个类型的入侵信号采集300次,作为样本,四类信号一共有1200个样本。将这些样本分为训练集和测试集,其中训练集为1020个信号,测试集为180个信号,测试比例为0.15。In this embodiment, each type of intrusion signal is collected 300 times, and as a sample, there are a total of 1200 samples of the four types of signals. These samples are divided into training set and test set, where the training set is 1020 signals, the test set is 180 signals, and the test scale is 0.15.
本实施例中,进行小波变换时,选择db8小波基,并使用10层分解。选定的用于短时傅里叶变换的窗函数为旁瓣为0.5的凯塞窗窗函数,窗宽为4800,在傅里叶变换中窗口与窗口之间的重叠数为4200,采样率为10000hz。In this embodiment, when performing wavelet transformation, the db8 wavelet base is selected, and 10 layers of decomposition are used. The selected window function for the short-time Fourier transform is a Kaiser window function with a side lobe of 0.5, the window width is 4800, the overlap between the windows in the Fourier transform is 4200, and the sampling rate is 4200. is 10000hz.
其中,短时傅里叶变换公式为Among them, the short-time Fourier transform formula is
本实施例中,损失值采用交叉熵函数进行计算。深度学习优化器采用adam优化器其中,学习率设置为0.0003,batch_size设置为16,epoch设置为8,迭代次数为383次。In this embodiment, the loss value is calculated by using the cross entropy function. The deep learning optimizer adopts the adam optimizer, where the learning rate is set to 0.0003, the batch_size is set to 16, the epoch is set to 8, and the number of iterations is 383.
具体实施时,预先选择了三种经典的卷积网络结构Inception-v2,Inception-v3,Resnet,通过工程应用指标选择实际应用参数,挑选出的有利于本实施例实际应用的卷积神经网络模型为Inception-v2结构。During the specific implementation, three classical convolutional network structures Inception-v2, Inception-v3, and Resnet are pre-selected, and the practical application parameters are selected through engineering application indicators, and the convolutional neural network model that is beneficial to the practical application of this embodiment is selected. For the Inception-v2 structure.
选定网络模型后,步骤2)中,制作含有大量噪声的数据集,分为训练集和测试集。该训练集包括含有每类信号高斯噪声为30db、40db、50db、60db、70db五种入侵信号,一共为6000个样本,将这6000个样本用于训练,然后另外设计12组测试样本,每组测试样本为4类信号各50个样本,这50个样本中包含了5类噪声各10个。将训练集在inception-v2结构的网络模型中进行训练。After the network model is selected, in step 2), a data set containing a lot of noise is made and divided into a training set and a test set. The training set includes five intrusion signals with Gaussian noise of 30db, 40db, 50db, 60db and 70db for each type of signal, with a total of 6000 samples. These 6000 samples are used for training, and then 12 sets of test samples are designed. The test samples are 50 samples of each of the 4 types of signals, and these 50 samples contain 10 of each of the 5 types of noise. The training set is trained in the network model of the inception-v2 structure.
采集恶劣环境下的入侵信号,制作成时频图,如图3至图6所示,放入到该网络模型中进行测试。经过实测,本发明对恶劣环境下的于敲击、摇晃、刮风、下雨等入侵信号的识别率可以达到93.83%、99.49%、95.93%和99.83%,满足对不同的入侵信号进行识别。Collect intrusion signals in harsh environments, make time-frequency diagrams, as shown in Figure 3 to Figure 6, and put them into the network model for testing. After actual measurement, the invention can achieve 93.83%, 99.49%, 95.93% and 99.83% of the recognition rate of intrusion signals in harsh environments such as knocking, shaking, windy, raining, etc., which satisfies the identification of different intrusion signals.
上述实施例仅是用来说明本发明,而并非用作对本发明的限定。只要是依据本发明的技术实质,对上述实施例进行变化、变型等都将落在本发明的权利要求的范围内。The above-mentioned embodiments are only used to illustrate the present invention, but not to limit the present invention. As long as it is in accordance with the technical essence of the present invention, changes, modifications, etc. to the above-described embodiments will fall within the scope of the claims of the present invention.
Claims (8)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201911005085.1ACN110852187B (en) | 2019-10-22 | 2019-10-22 | Method and system for identifying perimeter intrusion event |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201911005085.1ACN110852187B (en) | 2019-10-22 | 2019-10-22 | Method and system for identifying perimeter intrusion event |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN110852187Atrue CN110852187A (en) | 2020-02-28 |
| CN110852187B CN110852187B (en) | 2023-04-07 |
Family
ID=69597748
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN201911005085.1AActiveCN110852187B (en) | 2019-10-22 | 2019-10-22 | Method and system for identifying perimeter intrusion event |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN110852187B (en) |
Cited By (8)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN111597994A (en)* | 2020-05-15 | 2020-08-28 | 华侨大学 | A method for constructing an optical fiber perimeter security intrusion event recognition model and a security system |
| CN111738073A (en)* | 2020-05-16 | 2020-10-02 | 北京信息科技大学 | A system and method for optical fiber signal identification |
| CN111951505A (en)* | 2020-08-25 | 2020-11-17 | 青岛大学 | Fence vibration intrusion location and pattern recognition method based on distributed optical fiber system |
| CN112257533A (en)* | 2020-10-14 | 2021-01-22 | 吉林大学 | Perimeter intrusion detection and identification method |
| CN112419635A (en)* | 2020-12-10 | 2021-02-26 | 武汉理工光科股份有限公司 | Perimeter alarm method integrating grating and video |
| CN114093106A (en)* | 2021-11-29 | 2022-02-25 | 上海微波技术研究所(中国电子科技集团公司第五十研究所) | Intrusion signal alarm method and system based on Efficinet classified network |
| CN114925722A (en)* | 2022-05-06 | 2022-08-19 | 广西师范大学 | Perimeter security intrusion signal detection method based on generalized S transformation and transfer learning |
| CN117496650A (en)* | 2024-01-02 | 2024-02-02 | 浙江省白马湖实验室有限公司 | Distributed optical fiber intrusion early warning method and system based on environment embedding |
Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2017036363A1 (en)* | 2015-09-02 | 2017-03-09 | 同方威视技术股份有限公司 | Optical fiber perimeter intrusion signal identification method and device, and perimeter intrusion alarm system |
| CN106503642A (en)* | 2016-10-18 | 2017-03-15 | 长园长通新材料股份有限公司 | A kind of model of vibration method for building up for being applied to optical fiber sensing system |
| CN106600870A (en)* | 2016-12-31 | 2017-04-26 | 上海华魏光纤传感技术有限公司 | Distributed optical fiber fence vibration invasion identifying system |
- 2019
- 2019-10-22CNCN201911005085.1Apatent/CN110852187B/enactiveActive
Patent Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2017036363A1 (en)* | 2015-09-02 | 2017-03-09 | 同方威视技术股份有限公司 | Optical fiber perimeter intrusion signal identification method and device, and perimeter intrusion alarm system |
| CN106503642A (en)* | 2016-10-18 | 2017-03-15 | 长园长通新材料股份有限公司 | A kind of model of vibration method for building up for being applied to optical fiber sensing system |
| CN106600870A (en)* | 2016-12-31 | 2017-04-26 | 上海华魏光纤传感技术有限公司 | Distributed optical fiber fence vibration invasion identifying system |
Non-Patent Citations (1)
| Title |
|---|
| 朱程辉等: "光纤入侵行为融合特征的集成识别", 《光电工程》* |
Cited By (12)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN111597994A (en)* | 2020-05-15 | 2020-08-28 | 华侨大学 | A method for constructing an optical fiber perimeter security intrusion event recognition model and a security system |
| CN111597994B (en)* | 2020-05-15 | 2023-03-07 | 华侨大学 | Optical fiber perimeter security intrusion event identification model construction method and security system |
| CN111738073A (en)* | 2020-05-16 | 2020-10-02 | 北京信息科技大学 | A system and method for optical fiber signal identification |
| CN111951505A (en)* | 2020-08-25 | 2020-11-17 | 青岛大学 | Fence vibration intrusion location and pattern recognition method based on distributed optical fiber system |
| CN112257533A (en)* | 2020-10-14 | 2021-01-22 | 吉林大学 | Perimeter intrusion detection and identification method |
| CN112257533B (en)* | 2020-10-14 | 2022-04-12 | 吉林大学 | A perimeter intrusion detection and identification method |
| CN112419635A (en)* | 2020-12-10 | 2021-02-26 | 武汉理工光科股份有限公司 | Perimeter alarm method integrating grating and video |
| CN112419635B (en)* | 2020-12-10 | 2022-10-04 | 武汉理工光科股份有限公司 | Perimeter alarm method integrating grating and video |
| CN114093106A (en)* | 2021-11-29 | 2022-02-25 | 上海微波技术研究所(中国电子科技集团公司第五十研究所) | Intrusion signal alarm method and system based on Efficinet classified network |
| CN114925722A (en)* | 2022-05-06 | 2022-08-19 | 广西师范大学 | Perimeter security intrusion signal detection method based on generalized S transformation and transfer learning |
| CN117496650A (en)* | 2024-01-02 | 2024-02-02 | 浙江省白马湖实验室有限公司 | Distributed optical fiber intrusion early warning method and system based on environment embedding |
| CN117496650B (en)* | 2024-01-02 | 2024-03-26 | 浙江省白马湖实验室有限公司 | Distributed optical fiber intrusion early warning method and system based on environment embedding |
Also Published As
| Publication number | Publication date |
|---|---|
| CN110852187B (en) | 2023-04-07 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN110852187B (en) | Method and system for identifying perimeter intrusion event | |
| CN111104891B (en) | A method for pattern recognition of perturbation signal in optical fiber sensing based on BiLSTM | |
| CN111157099B (en) | Distributed optical fiber sensor vibration signal classification method and identification classification system | |
| CN106225907B (en) | It is a kind of based on Φ-OTDR technique fiber-optic vibration identifying system and method | |
| Cao et al. | An open dataset of φ-OTDR events with two classification models as baselines | |
| US20210064972A1 (en) | Intelligent fodas system and method based on ai chip | |
| CN114857504A (en) | Pipeline safety monitoring method based on distributed optical fiber sensors and deep learning | |
| CN105261136B (en) | The method and device of weather interference is shielded in a kind of fiber-optic monitoring warning system | |
| CN105023379B (en) | A kind of signal recognition method of airport optical fiber perimeter early warning system | |
| CN104240455A (en) | Method for identifying disturbance event in distributed type optical fiber pipeline security early-warning system | |
| CN103196465B (en) | Method for separating noise of sensing signal and extracting signal of phase-sensitive optical time domain reflectometer | |
| CN103116957B (en) | A kind of method of optical fiber perimeter security and protection system shielding climate impact | |
| CN116805061B (en) | Leakage event judging method based on optical fiber sensing | |
| CN102045120A (en) | Vibration signal identification method for optical fiber perimeter system | |
| CN106530544A (en) | Fiber grating array perimeter intrusion system | |
| CN104217513B (en) | The method improving phase sensitive optical time domain reflectometer identification intrusion event accuracy rate | |
| CN111597994B (en) | Optical fiber perimeter security intrusion event identification model construction method and security system | |
| CN105606198A (en) | Fiber vibration sensing system two-order signal feature extraction and determining method | |
| CN114093106B (en) | Intrusion signal alarm method and system based on EfficientNET classification network | |
| CN114510960A (en) | Method for recognizing distributed optical fiber sensor system mode | |
| CN108538011B (en) | Laser radar fire detection method | |
| CN118884511A (en) | A rapid earthquake identification method based on deep learning and distributed fiber optic acoustic wave sensing system | |
| CN117972372A (en) | An intelligent DAS and its aliased signal directional target separation method | |
| CN111951505B (en) | Fence vibration intrusion positioning and mode identification method based on distributed optical fiber system | |
| CN116933127A (en) | Distributed optical fiber sensing system mode identification method based on residual error network |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |