CN109412866B - Active detection method for multi-tenant cloud platform security isolation - Google Patents
Active detection method for multi-tenant cloud platform security isolationDownload PDFInfo
- Publication number
- CN109412866B CN109412866BCN201811473272.8ACN201811473272ACN109412866BCN 109412866 BCN109412866 BCN 109412866BCN 201811473272 ACN201811473272 ACN 201811473272ACN 109412866 BCN109412866 BCN 109412866B
- Authority
- CN
- China
- Prior art keywords
- node
- tenant
- detection
- security isolation
- nodes
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Active
Links
- 238000002955isolationMethods0.000titleclaimsabstractdescription130
- 238000001514detection methodMethods0.000titleclaimsabstractdescription125
- 238000000034methodMethods0.000claimsabstractdescription40
- 239000011159matrix materialSubstances0.000claimsdescription30
- 230000008569processEffects0.000claimsdescription25
- 238000012217deletionMethods0.000claimsdescription15
- 230000037430deletionEffects0.000claimsdescription15
- 238000010586diagramMethods0.000claimsdescription14
- 238000003780insertionMethods0.000claimsdescription12
- 230000037431insertionEffects0.000claimsdescription12
- 238000013507mappingMethods0.000claimsdescription12
- 238000011895specific detectionMethods0.000claimsdescription10
- 238000012360testing methodMethods0.000claims1
- 238000011897real-time detectionMethods0.000abstractdescription2
- 238000005516engineering processMethods0.000description9
- 238000004458analytical methodMethods0.000description5
- 101100491335Caenorhabditis elegans mat-2 geneProteins0.000description4
- 230000007123defenseEffects0.000description4
- 230000007246mechanismEffects0.000description4
- 230000007812deficiencyEffects0.000description2
- 238000011161developmentMethods0.000description2
- 241000322338LoeseliastrumSpecies0.000description1
- 101150096185PAAS geneProteins0.000description1
- 102100033121Transcription factor 21Human genes0.000description1
- 239000008186active pharmaceutical agentSubstances0.000description1
- 230000004888barrier functionEffects0.000description1
- 230000008859changeEffects0.000description1
- 230000002708enhancing effectEffects0.000description1
- 238000011156evaluationMethods0.000description1
- 238000007689inspectionMethods0.000description1
- 238000012986modificationMethods0.000description1
- 230000004048modificationEffects0.000description1
- -1pod2Proteins0.000description1
- 238000011176poolingMethods0.000description1
- 230000003449preventive effectEffects0.000description1
- 230000000246remedial effectEffects0.000description1
- 238000005067remediationMethods0.000description1
- 238000005728strengtheningMethods0.000description1
- 101150109289tcf21 geneProteins0.000description1
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L41/00—Arrangements for maintenance, administration or management of data switching networks, e.g. of packet switching networks
- H04L41/14—Network analysis or design
- H04L41/145—Network analysis or design involving simulating, designing, planning or modelling of a network
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/02—Network architectures or network communication protocols for network security for separating internal from external traffic, e.g. firewalls
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/10—Network architectures or network communication protocols for network security for controlling access to devices or network resources
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/10—Network architectures or network communication protocols for network security for controlling access to devices or network resources
- H04L63/105—Multiple levels of security
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1441—Countermeasures against malicious traffic
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/20—Network architectures or network communication protocols for network security for managing network security; network security policies in general
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本发明属于云安全技术领域,尤其涉及一种多租户云平台中安全隔离的检测方法。The invention belongs to the technical field of cloud security, and in particular relates to a detection method for security isolation in a multi-tenant cloud platform.
背景技术Background technique
云作为近年来发展最为迅速的技术之一,已逐渐成为IT基础设施的发展趋势,被越来越广泛的应用。它通过提出一种资源(包括计算资源、网络资源、存储资源等)池化技术,使基础设施可以被多个租户共享使用,从而实现了一种方便的、按需的服务方式。Cloud, as one of the most rapidly developing technologies in recent years, has gradually become the development trend of IT infrastructure and is being used more and more widely. By proposing a resource (including computing resources, network resources, storage resources, etc.) pooling technology, the infrastructure can be shared and used by multiple tenants, thereby realizing a convenient and on-demand service mode.
然而,云平台中多租户技术打破了物理设备之间的壁垒,在提高资源的利用率的同时,也不可避免的带来了严峻的安全问题。一方面,云服务提供商需要提供相应的租户隔离机制,保障特定资源不被非授权访问;另一方面,若共享环境中隔离失效,云中恶意租户打破隔离机制,发起非授权访问,将使其他租户的数据资产面临巨大的安全风险。However, the multi-tenant technology in the cloud platform breaks the barriers between physical devices, which inevitably brings serious security problems while improving the utilization of resources. On the one hand, cloud service providers need to provide a corresponding tenant isolation mechanism to ensure that specific resources are not unauthorized access; Data assets of other tenants face huge security risks.
因此,在多租户云平台中,安全隔离显得尤为重要,如何提高云平台的安全能力,是目前需要本领域技术人员迫切解决的一个技术问题。目前,针对安全隔离的问题,相关解决方案包括三大类:事前防御、事后追溯以及运行时检查。Therefore, in a multi-tenant cloud platform, security isolation is particularly important, and how to improve the security capability of the cloud platform is a technical problem that needs to be urgently solved by those skilled in the art. At present, for the problem of security isolation, relevant solutions include three categories: pre-defense, post-event traceability, and runtime inspection.
事前防御的方案主要通过加强访问控制、增强安全模块等手段,事先限制访问能力。经过对现有专利的检索发现,中国专利文献号CN104580505A公开(公告)日2015.04.29,公开了一种租户隔离方法及虚拟交换机,包括:虚拟交换机为各物理主机上的各虚拟机分配相应的用于标识租户报文的虚拟局域网标签;虚拟交换机为各租户分配相应的虚拟租户网络(VTN)标识符,生成各租户相应的虚拟网络。The pre-defense solution mainly restricts access capabilities in advance by strengthening access control and enhancing security modules. After searching for existing patents, it was found that Chinese Patent Document No. CN104580505A was published (announcement) on 2015.04.29, which discloses a tenant isolation method and a virtual switch, including: the virtual switch allocates corresponding virtual machines to each virtual machine on each physical host. A virtual local area network label used to identify tenant packets; the virtual switch allocates a corresponding virtual tenant network (VTN) identifier to each tenant, and generates a corresponding virtual network for each tenant.
事后追溯的方案通过对一段时间内的采集的数据进行挖掘和关联,在事后分析追溯云内已存在的攻击路径后,实施补救措施。经过对现有专利的检索发现,中国专利文献号CN107566369A公开(公告)日2018.01.09,公开了一种针对工控基础设施进行安全隔离与防御有效性评价方法,该方法同样可以作用于基于云的IT基础设施。包括:建立一个隔离与防御技术模型;基于技术模型对信息进行搜集;根据采集的数据信息进行算法分析;通过分析业务系统受到攻击时抵御各种攻击的能力,然后评估安全隔离措施的效用。The post-event traceability solution mines and correlates the collected data over a period of time, and implements remedial measures after post-event analysis and traceability of the existing attack paths in the cloud. After searching for existing patents, it was found that Chinese Patent Document No. CN107566369A was published (announcement) on 2018.01.09, which disclosed a method for security isolation and defense effectiveness evaluation for industrial control infrastructure, which can also be used for cloud-based IT infrastructure. Including: establishing a technical model of isolation and defense; collecting information based on the technical model; performing algorithm analysis based on the collected data information; analyzing the ability of the business system to resist various attacks when attacked, and then evaluating the effectiveness of security isolation measures.
以上两类解决方案虽然也是云安全防护体系中必不可少的一部分,但其不足在于,前者无法应对云平台运行过程中发生的意外情况,如漏洞、错误配置等;后者只能对云内已发生的安全威胁进行分析和补救,无法起到防范作用。Although the above two types of solutions are also an indispensable part of the cloud security protection system, their shortcomings are that the former cannot deal with unexpected situations that occur during the operation of the cloud platform, such as loopholes and misconfigurations; the latter can only Analysis and remediation of security threats that have occurred cannot play a preventive role.
第三类方案通过在运行时进行检查,可使得即使云平台正在运转过程中,也可以主动的发现潜在的安全隔离威胁,从而弥补前两种方案的不足。现有针对租户级别的安全隔离实时检测方法包括:(1)通过标记网络数据包,实现对流的实时追踪和分析。但该方法不能检查潜在失效威胁;(2)通过求解布尔可满足性问题,对云中网络进行验证。该方法存储开销小,但实时性较差。(3)通过对云平台进行信息采集,建立图模型,实施实时更新和模型分析。这方面工作主要集中在依据提供商API检测云基础设施的配置合规性。该方法实时性强,但未针对多租户云平台的安全隔离问题进一步提出可拓展的检测方案。The third type of scheme can proactively discover potential security isolation threats even when the cloud platform is running by checking at runtime, thereby making up for the shortcomings of the first two schemes. Existing real-time detection methods for security isolation at the tenant level include: (1) Real-time tracking and analysis of flows are realized by marking network data packets. However, this method cannot check potential failure threats; (2) the network in the cloud is verified by solving the Boolean satisfiability problem. This method has low storage overhead, but poor real-time performance. (3) By collecting information on the cloud platform, establishing a graph model, and implementing real-time update and model analysis. Work in this area mainly focuses on detecting cloud infrastructure configuration compliance against provider APIs. This method has strong real-time performance, but does not further propose a scalable detection scheme for the security isolation problem of multi-tenant cloud platforms.
现有技术存在可拓展性较弱、时效性不强的问题。本发明提出一种安全隔离检测方法,可及时检测出动态变化的云环境中可能存在的潜在的隔离失效威胁,从而弥补现有方法的不足,提高多租户云平台的安全能力。The existing technology has the problems of weak scalability and poor timeliness. The invention proposes a security isolation detection method, which can timely detect potential isolation failure threats that may exist in a dynamically changing cloud environment, thereby making up for the deficiencies of the existing methods and improving the security capability of the multi-tenant cloud platform.
发明内容SUMMARY OF THE INVENTION
本发明的目的是解决现有多租户云平台安全隔离技术的不足,因此,提出一种对云内配置进行主动安全检测的方法,发现多租户云平台中可能存在的隔离失效威胁。该方法具有可扩展性强、时效性高的特点。The purpose of the present invention is to solve the shortcomings of the existing multi-tenant cloud platform security isolation technology. Therefore, a method for active security detection of cloud configuration is proposed to discover possible isolation failure threats in the multi-tenant cloud platform. This method has the characteristics of strong scalability and high timeliness.
为实现上述目的,本发明采取以下方法,包括:To achieve the above object, the present invention adopts the following methods, including:
(1)定义图模型:定义包含多租户云平台中各个节点的图模型G=(V,E,C),V表示云平台中所有提供服务的节点的集群,集群中任一节点满足vi∈V;E表示各节点之间的边,集群中存在任一条边ei,j即表示节点vi可访问另一节点vj,ei,j∈E;C表示节点之间的连通关系,ci,j表示节点vi与vj之间的连通关系,ci,j∈C。i,j表示两个节点的标识。(1) Define a graph model: define a graph model G=(V, E, C) that includes each node in the multi-tenant cloud platform, where V represents the cluster of all nodes that provide services in the cloud platform, and any node in the cluster satisfiesvi ∈V; E represents the edge between nodes, and any edge ei, j in the cluster means that node vi can access another node vj , ei, j∈ E; C represents the connectivity between nodes , ci, j represent the connectivity between nodes vi and vj , ci, j ∈ C. i, j represent the identities of the two nodes.
构建图模型时,若ci,j=1,则认为图模型G中vi与vj之间存在边ei,j,若ci,j=0,则vi与vj之间不存在边ei,j。上述图模型G以二维邻接矩阵的形式存储,记为:When constructing a graph model, if ci, j = 1, it is considered that there is an edge ei, j between vi and vj in the graph model G; if ci, j = 0, then there is no edge between vi and vj . Edges ei,j exist. The above graph model G is stored in the form of a two-dimensional adjacency matrix, denoted as:
(2)定义检测基准:在多租户云平台中,存在多个租户,由管理员管理,属于不同租户的节点之间不可发起非法访问;每个租户内部,存在多个用户组,由管理员或租户管理员管理,属于不同用户组的节点不可发起非法访问。因此,安全隔离包含两类场景:一是不同租户之间的安全隔离,需验证各个租户之间是否存在非法访问的潜在威胁;二是同一租户内不同用户组之间的安全隔离,需验证同一租户内不同用户组之间是否存在非法访问的潜在威胁。针对以上场景,分别定义基于租户安全隔离的检测基准和基于用户组安全隔离的检测基准。(2) Define the detection benchmark: In the multi-tenant cloud platform, there are multiple tenants, which are managed by the administrator, and illegal access cannot be initiated between nodes belonging to different tenants; within each tenant, there are multiple user groups, which are managed by the administrator Or managed by tenant administrators, and nodes belonging to different user groups cannot initiate illegal access. Therefore, security isolation includes two scenarios: one is the security isolation between different tenants, and it is necessary to verify whether there is a potential threat of illegal access between each tenant; the other is the security isolation between different user groups in the same tenant, it is necessary to verify the same Whether there is a potential threat of illegal access between different user groups within the tenant. For the above scenarios, define the detection benchmark based on tenant security isolation and the detection benchmark based on user group security isolation.
(21)基于租户安全隔离的检测基准:当攻击者获得管理员权限或多租户云平台内部存在恶意管理员时,多租户云平台的配置可被恶意篡改,使原本属于不同租户的节点之间可以发起非法访问,租户安全隔离被破坏。因此,建立租户与节点的正确映射关系 f,作为租户安全隔离的检测基准。若n表示节点的标识,tenentn表示标识为n的节点所属租户的标识,将映射关系记为:(21) Detection benchmark based on tenant security isolation: When an attacker obtains administrator privileges or there is a malicious administrator inside the multi-tenant cloud platform, the configuration of the multi-tenant cloud platform can be maliciously tampered with, causing nodes that originally belong to different tenants to be tampered with. Illegal access can be initiated, and tenant security isolation is broken. Therefore, the correct mapping relationship f between tenants and nodes is established as the detection benchmark for tenant security isolation. If n represents the identifier of the node, tenantn represents the identifier of the tenant to which the node with identifier n belongs, and the mapping relationship is recorded as:
f(n)=tenentn。f(n)=tenentn .
(22)基于用户组安全隔离的检测基准:针对多租户云平台中属于同一租户的用户组,定义L为用户组等级,L值可以为uppr、normal或lower。L值为uppr的用户组可访问非uppr的所有用户组,不可被其他用户组访问;L值为normal的用户组可与L值同为normal且标记值同为x的用户组互访,x为大于零的整数;L值为lower的用户组可被所有用户组访问,不可发起访问。对于用户组内的节点,若n表示节点的标识,leveln表示标识为n的节点的标记值,则节点n的标记值leveln定义为:(22) Detection benchmark based on user group security isolation: For user groups belonging to the same tenant in the multi-tenant cloud platform, define L as the user group level, and the L value can be uppr, normal, or lower. A user group whose L value is uppr can access all user groups that are not uppr, and cannot be accessed by other user groups; a user group whose L value is normal can exchange access with user groups whose L value is normal and whose tag value is the same as x. It is an integer greater than zero; the user group whose L value is lower can be accessed by all user groups and cannot initiate access. For the nodes in the user group, if n represents the identifier of the node, and leveln represents the tag value of the node whose identifier is n, then the tag value leveln of the node n is defined as:
当攻击者获得管理员或租户管理员权限,以及多租户云平台内部存在恶意管理员或恶意租户管理员时,用户组的等级配置可被恶意篡改,使不同等级的用户组的节点之间可发起非法访问,用户组安全隔离被破坏。因此,建立同一租户内各个用户组与节点的正确映射关系y,作为用户组安全隔离的检测基准,将映射关系记为:When an attacker obtains administrator or tenant administrator rights, and there are malicious administrators or malicious tenant administrators in the multi-tenant cloud platform, the level configuration of user groups can be maliciously tampered with, so that nodes of different levels of user groups can be tampered with. Illegal access is initiated, and the security isolation of user groups is destroyed. Therefore, the correct mapping relationship y between each user group and node in the same tenant is established as the detection benchmark for user group security isolation, and the mapping relationship is recorded as:
y(n)=leveln。y(n)=leveln .
(3)初始状态生成:采集初始状态下多租户云平台中所有节点的配置数据。依据步骤(1)中所定义的图模型G=(V,E,C),遍历配置数据并记录当前遍历节点vi与其他节点vj的连通关系ci,j∈C。若vi与vj连通,则ci,j=1,否则ci,j=0,然后以步骤(1) 所述定义构建初始状态图模型Ginit。(3) Initial state generation: collect configuration data of all nodes in the multi-tenant cloud platform in the initial state. According to the graph model G=(V, E, C) defined in step (1), the configuration data is traversed and the connectivity relationship ci, j ∈ C of the current traversed node vi and other nodes vj is recorded. If vi and vj are connected, then ci,j =1, otherwise ci,j =0, and then construct the initial state diagram model Ginit according to the definition in step (1).
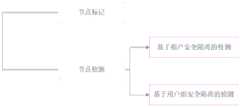
(4)初始隔离检测:依据步骤(2)中所述检测基准,检测步骤(3)中所述初始状态图模型Ginit是否满足安全隔离,检测过程包括初始化节点标记和初始化节点检测两个阶段:(4) Initial isolation detection: According to the detection benchmark described in step (2), to detect whether the initial state graph model Ginit described in step (3) satisfies security isolation, the detection process includes two stages: initialization node marking and initialization node detection :
(41)初始化节点标记过程为:依次遍历步骤(3)所述初始状态图模型Ginit中的所有节点。遍历过程中,将当前访问节点标记为待检测节点,并从尾端插入待检测队列Detect。(41) The initial node marking process is: traverse all the nodes in the initial state graph model Ginit in step (3) in sequence. During the traversal process, the current access node is marked as the node to be detected, and the queue Detect to be detected is inserted from the end.
(42)初始化节点检测过程为:从待检测队列Detect头端依次读取节点直至队列为空,将当前读取节点记为vdet。检测vdet是否符合安全隔离需求,并在检测完成后将vdet从头端移出待检测队列Detect。具体检测内容包括:基于检测基准(21)执行的租户安全隔离检测,基于检测基准(22)执行的用户组安全隔离检测。(42) The initial node detection process is: read nodes sequentially from the head end of the queue Detect to be detected until the queue is empty, and record the current read node as vdet . Check whether the vdet meets the security isolation requirements, and remove the vdet from the headend to be detected from the queue Detect after the detection is complete. The specific detection contents include: tenant security isolation detection performed based on the detection benchmark (21), and user group security isolation detection performed based on the detection benchmark (22).
(5)运行时隔离检测:将当前运行时刻记为time,若在time时刻,管理员或租户管理员对云平台实施配置操作导致初始状态图模型状态将发生更新,则将当前状态图模型记为Gtime,并依据步骤(2)中所述检测基准,在更新时检测Gtime是否满足安全隔离需求,检测过程包括更新时节点标记和更新时节点检测两个阶段:(5) Runtime isolation detection: record the current runtime as time. If the administrator or tenant administrator performs configuration operations on the cloud platform at time, the initial state diagram model state will be updated, and the current state diagram model will be recorded as time. is Gtime , and according to the detection benchmark described in step (2), it is detected whether Gtime meets the security isolation requirements during update. The detection process includes two stages: node marking during update and node detection during update:
(51)更新时节点标记过程为:步骤(5)中所述配置操作包括创建实例、删除实例、创建安全策略、删除安全策略。当云平台中的管理员或租户管理员实施上述操作时,对当前状态图模型Gtime进行增量更新,并将被更新节点标记为待检测节点,从尾端插入待检测队列Detect。(51) The node marking process when updating is as follows: the configuration operations described in step (5) include creating an instance, deleting an instance, creating a security policy, and deleting a security policy. When the administrator or tenant administrator in the cloud platform performs the above operations, incremental update is performed on the current state graph model Gtime , and the updated node is marked as the node to be detected, and the queue to be detected is inserted into the queue Detect from the end.
(52)更新时节点检测过程为:从待检测队列Detect头端依次读取节点直至队列为空,将当前读取节点记为vdet。检测vdet是否符合安全隔离需求,并在检测完成后将vdet从头端移出待检测队列Detect。具体检测内容包括:基于检测基准(21)执行的租户安全隔离检测,基于检测基准(22)执行的用户组安全隔离检测。(52) The node detection process during update is: read nodes sequentially from the head end of the queue Detect to be detected until the queue is empty, and record the current read node as vdet . Check whether the vdet meets the security isolation requirements, and remove the vdet from the headend to be detected from the queue Detect after the detection is complete. The specific detection contents include: tenant security isolation detection performed based on the detection benchmark (21), and user group security isolation detection performed based on the detection benchmark (22).
进一步的,根据所述的多租户云平台安全隔离的主动检测方法,其特征在于:步骤(51)中所述增量更新,实施时具体可以包含以下四类情况:Further, according to the active detection method for security isolation of a multi-tenant cloud platform, it is characterized in that: the incremental update in step (51) can specifically include the following four types of situations during implementation:
边插入:当创建或删除新的安全策略使步骤(5)所述当前状态图模型Gtime中的节点vi可访问vj时,设置步骤(1)中所述连通关系ci,j=1,使二维邻接矩阵A[i][j]=1,从而执行边插入。Edge insertion: when a new security policy is created or deleted so that node vi in the current state graph model Gtime described in step (5) can access vj , set the connectivity relationship ci,j = 1, making the two-dimensional adjacency matrix A[i][j]=1, thereby performing edge insertion.
边删除:当创建或删除新的安全策略使步骤(5)所述当前状态图模型Gtime中的节点vi不可访问vj时,设置步骤(1)中所述连通关系ci,j=0,使二维邻接矩阵A[i][j]=0,从而执行边删除。Edge deletion: when the creation or deletion of a new security policy makes the node vi in the current state graph model Gtime in step (5) inaccessible to vj , set the connection relationship ci,j = 0, making the two-dimensional adjacency matrix A[i][j]=0, thereby performing edge deletion.
点插入:当创建新实例时,在步骤(5)所述当前状态图模型Gtime中插入新节点,记为vnew,new表示节点标识。若记Gtime中其他节点的标识为k,初始化步骤(1)中所述二维邻接矩阵A,使二维邻接矩阵A[new][k]=0且A[k][new]=0。当节点vnew可访问vk时,设置步骤(1)中所述连通关系cnew,k=1,使二维邻接矩阵A[new][k]=1;当节点vk可访问vnew时,设置连通关系ck,new=1,使二维邻接矩阵A[k][new]=1。从而执行点插入。Point insertion: when a new instance is created, a new node is inserted into the current state graph model Gtime described in step (5), denoted as vnew , and new represents the node identifier. If the identifier of other nodes in Gtime is denoted as k, initialize the two-dimensional adjacency matrix A in step (1), so that the two-dimensional adjacency matrix A[new][k]=0 and A[k][new]=0 . When the node vnew can access vk , set the connectivity relationship cnew in step (1), k =1, so that the two-dimensional adjacency matrix A[new][k]=1; when the node vk can access vnew When , set the connectivity relationshipck, new =1, and make the two-dimensional adjacency matrix A[k][new]=1. Thereby, point insertion is performed.
点删除:当删除新实例时,在步骤(5)所述当前状态图模型Gtime中定位该实例对应的节点,记为vdel,del表示节点标识。此时通过设置del=-1将节点vdel标记为失效,不参与检测。从而执行点删除。Point deletion: when deleting a new instance, locate the node corresponding to the instance in the current state graph model Gtime described in step (5), denoted as vdel , where del represents the node identifier. At this time, the node vdel is marked as invalid by settingdel =-1, and does not participate in the detection. Thereby, point deletion is performed.
进一步的,根据所述的多租户云平台安全隔离的主动检测方法,其特征在于:步骤(42)、(52)中所述租户安全隔离检测,是依据步骤(2)中所述基于租户安全隔离的检测基准,检测步骤(42)、(52)中所述待检测队列Detect头端读取到的节点vdet是否满足租户安全隔离。Further, according to the active detection method for security isolation of a multi-tenant cloud platform, it is characterized in that: the tenant security isolation detection in steps (42) and (52) is based on the tenant security described in step (2). The isolation detection benchmark is to detect whether the node vdet read by the head end of the to-be-detected queue Detect in steps (42) and (52) satisfies the tenant security isolation.
针对节点vdet的具体检测过程包括:遍历步骤(3)中所述初始状态图模型Ginit或步骤(5)中所述当前状态图模型Gtime中的所有节点,将当前遍历到的节点记为vk,k表示节点标识。此时,若步骤(1)中所述二维邻接矩阵A[k][det]=1,则当且仅当步骤(2) 中所述f(det)=f(k)时,可认定节点vdet满足租户安全隔离。The specific detection process for the node vdet includes: traversing all nodes in the initial state graph model Ginit described in step (3) or the current state graph model Gtime described in step (5), and recording the currently traversed node as a record. is vk , k represents the node identification. At this time, if the two-dimensional adjacency matrix A[k][det]=1 in step (1), then if and only if f(det)=f(k) in step (2), it can be determined that Node vdet satisfies tenant security isolation.
进一步的,根据所述的多租户云平台安全隔离的主动检测方法,其特征在于:步骤(42)、(52)中所述用户组安全隔离检测,是依据步骤(2)中所述基于用户组安全隔离的检测基准,检测步骤(42)、(52)中所述待检测队列Detect头端读取到的节点vdet是否满足用户组安全隔离。Further, according to the active detection method for security isolation of a multi-tenant cloud platform, it is characterized in that: the detection of user group security isolation in steps (42) and (52) is based on the user group security isolation detection described in step (2). The detection benchmark for group security isolation is to detect whether the node vdet read by the head end of the to-be-detected queue Detect in steps (42) and (52) satisfies the user group security isolation.
针对节点vdet的具体检测过程包括:遍历步骤(3)中所述初始状态图模型Ginit或步骤(5)中所述当前状态图模型Gtime中的所有节点,将当前遍历到的节点记为vk,k表示节点标识。此时,若步骤(1)中所述二维邻接矩阵A[k][det]=1,则仅当步骤(2)中所述y(k)=y(det)>0或y(k)=1且y(det)!=1或y(k)!=0且y(det)=0时,可认定节点vdet满足用户组安全隔离。The specific detection process for the node vdet includes: traversing all nodes in the initial state graph model Ginit described in step (3) or the current state graph model Gtime described in step (5), and recording the currently traversed node as a record. is vk , k represents the node identification. At this time, if the two-dimensional adjacency matrix A[k][det]=1 in step (1), then only if y(k)=y(det)>0 or y(k) in step (2) )=1 and y(det)! =1 or y(k)! =0 and y(det)=0, it can be determined that the node vdet satisfies the user group security isolation.
本发明采取以上技术方案,其具有以下特点:The present invention adopts the above technical scheme, and it has the following characteristics:
(1)本方法以图的形式对多租户云平台的配置状态进行组织建模,并建立了基于租户安全隔离的检测基准和基于用户组安全隔离的检测基准,然后实施安全隔离检测,以及时发现潜在隔离失效威胁对云内租户造成的危害。(1) This method organizes the modeling of the configuration state of the multi-tenant cloud platform in the form of a graph, and establishes a detection benchmark based on tenant security isolation and a detection benchmark based on user group security isolation, and then implements security isolation detection, timely Discover the harm that potential isolation failures threaten to in-cloud tenants.
(2)通过本发明提出的安全隔离检的主动测方法,可检测出动态变化的云环境中可能存在的潜在的隔离失效威胁,从而弥补现有方法的不足,提高多租户云平台的安全能力。(2) Through the active detection method of security isolation detection proposed by the present invention, potential isolation failure threats that may exist in a dynamically changing cloud environment can be detected, thereby making up for the deficiencies of the existing methods and improving the security capability of the multi-tenant cloud platform .
附图说明Description of drawings
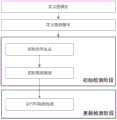
图1示出本发明提供的一种多租户云平台安全隔离的主动检测方法流程图;1 shows a flowchart of an active detection method for security isolation of a multi-tenant cloud platform provided by the present invention;
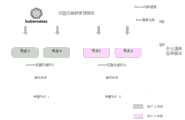
图2示出本发明实施例提供的系统平台架构示意图;2 shows a schematic diagram of a system platform architecture provided by an embodiment of the present invention;
图3示出本发明实施例提供的一种多租户云平台安全隔离的主动检测方法的实施框架图。FIG. 3 shows an implementation framework diagram of an active detection method for security isolation of a multi-tenant cloud platform provided by an embodiment of the present invention.
具体实施方式Detailed ways
为了使本发明的目标、技术方案及优点更加清楚明白,以下将结合本发明实施例中的附图对本发明进行进一步详细说明。应当理解为,此处所描述的具体实施例仅仅用以解释本发明,并不用于限定本发明。基于本发明中的实施例,本领域技术人员在没有做出创造性劳动前提下所获得的所有其它实施例,都属于本发明保护的范围。In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings in the embodiments of the present invention. It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention. Based on the embodiments of the present invention, all other embodiments obtained by those skilled in the art without creative efforts shall fall within the protection scope of the present invention.
目前,随着IT基础设施相关技术的快速发展和更迭,基于轻量级虚拟化技术的容器引擎Docker被各行业越来越多的公司使用。容器(Container)是一种新型虚拟化技术,使用Linux内核本身支持的namespace和cgroup等机制实现环境和资源的隔离,具有灵活性高、部署方便的特点。通过整合以kubernetes为代表的分布式容器集群管理方案,可基于容器技术建设以提供服务为目标的PaaS云。At present, with the rapid development and change of IT infrastructure-related technologies, Docker, a container engine based on lightweight virtualization technology, is used by more and more companies in various industries. Container (Container) is a new type of virtualization technology. It uses the namespace and cgroup supported by the Linux kernel to isolate environments and resources. It has the characteristics of high flexibility and convenient deployment. By integrating the distributed container cluster management solution represented by kubernetes, a PaaS cloud can be built based on container technology to provide services.
本实施例基于容器引擎docker搭建云平台,由kubernetes管理容器集群,calico三层网络方案管理容器集群网络,结合kubernetes平台提供的命名空间标签与NetworkPolicy机制,实现云平台的租户网络隔离需求,并部署一致性仓库etcd使平台各节点协同工作。This embodiment builds a cloud platform based on the container engine docker, manages the container cluster by kubernetes, and manages the container cluster network with the calico three-layer network solution. Combined with the namespace label and NetworkPolicy mechanism provided by the kubernetes platform, the tenant network isolation requirements of the cloud platform are realized and deployed. The consistency repository etcd enables the nodes of the platform to work together.
基于上述实施环境,本发明实施例将所提出的隔离检测方法应用于容器云平台,并针对租户网络进行安全隔离检测。在本实施例中,云内所有用户在管理粒度上被分到若干组内,每组称为一个租户(tenant),租户又可以包含用户组。因此,云内用户可以分为三类:包括云平台管理员用户,租户管理员用户和普通用户。Based on the above implementation environment, the embodiment of the present invention applies the proposed isolation detection method to the container cloud platform, and performs security isolation detection for the tenant network. In this embodiment, all users in the cloud are divided into several groups in terms of management granularity, each group is called a tenant (tenant), and the tenant may include user groups. Therefore, in-cloud users can be divided into three categories: cloud platform administrator users, tenant administrator users, and ordinary users.
图2为本发明实施例的平台架构示意图。本实施例包括5个步骤,如图 1 所示 。FIG. 2 is a schematic diagram of a platform architecture according to an embodiment of the present invention. This embodiment includes 5 steps, as shown in FIG. 1 .
(1)定义图模型。在kubernetes集群搭建的PAAS云环境下,虚拟节点被称之为POD,因此将POD作为云平台管理的基本节点单位,然后构建云平台中各个用户节点状态的图模型G:(1) Define the graph model. In the PAAS cloud environment built by the kubernetes cluster, the virtual node is called POD, so POD is used as the basic node unit of cloud platform management, and then the graph model G of the status of each user node in the cloud platform is constructed:
G=(V,E,C)G=(V, E, C)
V表示云平台中所有提供服务的节点的集群,集群中任一节点满足vi∈V;E表示各节点之间的边,集群中存在任一条边ei,j即表示节点vi可访问另一节点vj,ei,j∈E;C表示节点之间的连通关系,ci,j表示节点vi与vj之间的连通关系,ci,j∈C。i,j表示两个节点的标识。V represents the cluster of all nodes that provide services in the cloud platform, and any node in the cluster satisfies vi ∈ V; E represents the edge between each node, and if any edge ei exists in the cluster,j means that the node vi can be accessed Another node vj , ei, j ∈ E; C represents the connection relationship between nodes, ci,j represents the connection relationship between nodes vi and vj , ci, j ∈ C. i, j represent the identities of the two nodes.
构建图模型时,若ci,j=1,则认为图模型G中vi与vj之间存在边ei,j,若ci,j=0,则vi与vj之间不存在边ei,j。上述图模型G以二维邻接矩阵的形式存储,记为:When constructing a graph model, if ci, j = 1, it is considered that there is an edge ei, j between vi and vj in the graph model G; if ci, j = 0, then there is no edge between vi and vj . Edges ei,j exist. The above graph model G is stored in the form of a two-dimensional adjacency matrix, denoted as:
(2)定义检测基准:在多租户云平台中,存在多个租户,由管理员管理,属于不同租户的节点之间不可发起非法访问;每个租户内部,存在多个用户组,由管理员或租户管理员管理,属于不同用户组的节点不可发起非法访问。因此,安全隔离包含两类场景:一是不同租户之间的安全隔离,需验证各个租户之间是否存在非法访问的潜在威胁;二是同一租户内不同用户组之间的安全隔离,需验证同一租户内不同用户组之间是否存在非法访问的潜在威胁。针对以上场景,分别定义基于租户安全隔离的检测基准和基于用户组安全隔离的检测基准。(2) Define the detection benchmark: In the multi-tenant cloud platform, there are multiple tenants, which are managed by the administrator, and illegal access cannot be initiated between nodes belonging to different tenants; within each tenant, there are multiple user groups, which are managed by the administrator Or managed by tenant administrators, and nodes belonging to different user groups cannot initiate illegal access. Therefore, security isolation includes two scenarios: one is the security isolation between different tenants, and it is necessary to verify whether there is a potential threat of illegal access between each tenant; the other is the security isolation between different user groups in the same tenant, it is necessary to verify the same Whether there is a potential threat of illegal access between different user groups within the tenant. For the above scenarios, define the detection benchmark based on tenant security isolation and the detection benchmark based on user group security isolation.
(21)基于租户安全隔离的检测基准:当攻击者获得管理员权限或多租户云平台内部存在恶意管理员时,多租户云平台的配置可被恶意篡改,使原本属于不同租户的节点之间可以发起非法访问,租户安全隔离被破坏。因此,建立租户与节点的正确映射关系 f,作为租户安全隔离的检测基准。若n表示节点的标识,tenentn表示标识为n的节点所属租户的标识,将映射关系记为:(21) Detection benchmark based on tenant security isolation: When an attacker obtains administrator privileges or there is a malicious administrator inside the multi-tenant cloud platform, the configuration of the multi-tenant cloud platform can be maliciously tampered with, causing nodes that originally belong to different tenants to be tampered with. Illegal access can be initiated, and tenant security isolation is broken. Therefore, the correct mapping relationship f between tenants and nodes is established as the detection benchmark for tenant security isolation. If n represents the identifier of the node, tenantn represents the identifier of the tenant to which the node with identifier n belongs, and the mapping relationship is recorded as:
f(n)=tenentn。f(n)=tenentn .
(22)基于用户组安全隔离的检测基准:针对多租户云平台中属于同一租户的用户组,定义L为用户组等级,L值可以为uppr、normal或lower。L值为uppr的用户组可访问非uppr的所有用户组,不可被其他用户组访问;L值为normal的用户组可与L值同为normal且标记值同为x的用户组互访,x为大于零的整数;L值为lower的用户组可被所有用户组访问,不可发起访问。对于用户组内的节点,若n表示节点的标识,leveln表示标识为n的节点的标记值,则节点n的标记值leveln定义为:(22) Detection benchmark based on user group security isolation: For user groups belonging to the same tenant in the multi-tenant cloud platform, define L as the user group level, and the L value can be uppr, normal, or lower. A user group whose L value is uppr can access all user groups that are not uppr, and cannot be accessed by other user groups; a user group whose L value is normal can exchange access with user groups whose L value is normal and whose tag value is the same as x. It is an integer greater than zero; the user group whose L value is lower can be accessed by all user groups and cannot initiate access. For the nodes in the user group, if n represents the identifier of the node, and leveln represents the tag value of the node whose identifier is n, then the tag value leveln of the node n is defined as:
当攻击者获得管理员或租户管理员权限,以及多租户云平台内部存在恶意管理员或恶意租户管理员时,用户组的等级配置可被恶意篡改,使不同等级的用户组的节点之间可发起非法访问,用户组安全隔离被破坏。因此,建立同一租户内各个用户组与节点的正确映射关系y,作为用户组安全隔离的检测基准,将映射关系记为:When an attacker obtains administrator or tenant administrator rights, and there are malicious administrators or malicious tenant administrators in the multi-tenant cloud platform, the level configuration of user groups can be maliciously tampered with, so that nodes of different levels of user groups can be tampered with. Illegal access is initiated, and the security isolation of user groups is destroyed. Therefore, the correct mapping relationship y between each user group and node in the same tenant is established as the detection benchmark for user group security isolation, and the mapping relationship is recorded as:
y(n)=leveln。y(n)=leveln .
(3)初始状态生成:采集初始状态下多租户云平台中所有节点的配置数据。依据步骤(1)中所定义的图模型G=(V,E,C),遍历配置数据并记录当前遍历节点vi与其他节点vj的连通关系ci,j∈C。若vi与vj连通,则ci,j=1,否则ci,j=0,然后以步骤(1) 所述定义构建初始状态图模型Ginit。(3) Initial state generation: collect configuration data of all nodes in the multi-tenant cloud platform in the initial state. According to the graph model G=(V, E, C) defined in step (1), the configuration data is traversed and the connectivity relationship ci, j ∈ C of the current traversed node vi and other nodes vj is recorded. If vi and vj are connected, then ci,j =1, otherwise ci,j =0, and then construct the initial state diagram model Ginit according to the definition in step (1).
在本实施例中,数据来源为容器云集群中的各个节点,具体采集数据包括:节点的命名空间标签;节点的Role标签;节点Role标签对应的隔离策略;当前网络状态所对应时间戳。In this embodiment, the data source is each node in the container cloud cluster, and the specific collected data includes: the node's namespace label; the node's Role label; the isolation policy corresponding to the node's Role label; and the timestamp corresponding to the current network state.
最终得到的数据集如表1示,给出了多租户云平台节点配置数据样例。The final data set is shown in Table 1, which gives a sample of multi-tenant cloud platform node configuration data.
表1多租户云平台节点配置数据样例Table 1 Example of multi-tenant cloud platform node configuration data
表1中Namespace属性的配置由kubernetes平台中Namespace隔离机制提供接口,Role属性的设定由kubernetes平台中Network Policy机制提供接口。The configuration of the Namespace attribute in Table 1 is provided by the Namespace isolation mechanism in the kubernetes platform, and the setting of the Role attribute is provided by the Network Policy mechanism in the kubernetes platform.
则可构建初始状态图模型Ginit,并得到二维邻接矩阵:Then the initial state graph model Ginit can be constructed, and the two-dimensional adjacency matrix can be obtained:
(4)初始隔离检测:依据步骤(2)中所述检测基准,检测步骤(3)中所述初始状态图模型Ginit是否满足安全隔离,检测过程包括初始化节点标记和初始化节点检测两个阶段:(4) Initial isolation detection: According to the detection benchmark described in step (2), to detect whether the initial state graph model Ginit described in step (3) satisfies security isolation, the detection process includes two stages: initialization node marking and initialization node detection :
(41)初始化节点标记过程为:依次遍历步骤(3)所述初始状态图模型Ginit中的所有节点。遍历过程中,将当前访问节点标记为待检测节点,并从尾端插入待检测队列Detect。(41) The initial node marking process is: traverse all the nodes in the initial state graph model Ginit in step (3) in sequence. During the traversal process, the current access node is marked as the node to be detected, and the queue Detect to be detected is inserted from the end.
Detect={pod1,pod2,pod3}Detect={pod1, pod2, pod3}
(42)初始化节点检测过程为:从待检测队列Detect头端依次读取节点直至队列为空,将当前读取节点记为vdet。检测vdet是否符合安全隔离需求,并在检测完成后将vdet从头端移出待检测队列Detect。具体检测内容包括:基于检测基准(21)执行的租户安全隔离检测,基于检测基准(22)执行的用户组安全隔离检测。(42) The initial node detection process is: read nodes sequentially from the head end of the queue Detect to be detected until the queue is empty, and record the current read node as vdet . Check whether the vdet meets the security isolation requirements, and remove the vdet from the headend to be detected from the queue Detect after the detection is complete. The specific detection contents include: tenant security isolation detection performed based on the detection benchmark (21), and user group security isolation detection performed based on the detection benchmark (22).
首先执行租户安全隔离检测:遍历步骤(3)中所述初始状态图模型Ginit中的所有节点,将当前遍历到的节点记为vk,k表示节点标识。此时,若步骤(1)中所述二维邻接矩阵A中A[k][det]=1,则当且仅当步骤(2)中所述f(det)=f(k)时,可认定节点vdet满足租户安全隔离;First, perform tenant security isolation detection: traverse all nodes in the initial state graph model Ginit described in step (3), and record the currently traversed node as vk , where k represents the node identifier. At this time, if A[k][det]=1 in the two-dimensional adjacency matrix A in step (1), then if and only if f(det)=f(k) in step (2), It can be determined that the node vdet satisfies the tenant security isolation;
然后执行基于区域安全域的状态检测:遍历步骤(3)中所述初始状态图模型Ginit中的所有节点,将当前遍历到的节点记为vk,k表示节点标识。此时,若步骤(1)中所述二维邻接矩阵A[k][det]=1,则仅当步骤(2)中所述y(k)=y(det)>0或y(k)=1且y(det)!=1或y(k)!=0且y(det)=0时,可认定节点vdet满足用户组安全隔离。Then perform the state detection based on the regional security domain: traverse all the nodes in the initial state graph model Ginit described in step (3), record the currently traversed node as vk , and k represents the node identifier. At this time, if the two-dimensional adjacency matrix A[k][det]=1 in step (1), then only if y(k)=y(det)>0 or y(k) in step (2) )=1 and y(det)! =1 or y(k)! =0 and y(det)=0, it can be determined that the node vdet satisfies the user group security isolation.
(5)运行时隔离检测:将当前运行时刻记为time,若在time时刻,管理员或租户管理员对云平台实施配置操作导致初始状态图模型状态将发生更新,则将当前状态图模型记为Gtime,并依据步骤(2)中所述检测基准,在更新时检测Gtime是否满足安全隔离需求,检测过程包括更新时节点标记和更新时节点检测两个阶段:(5) Runtime isolation detection: record the current runtime as time. If the administrator or tenant administrator performs configuration operations on the cloud platform at time, the initial state diagram model state will be updated, and the current state diagram model will be recorded as time. is Gtime , and according to the detection benchmark described in step (2), it is detected whether Gtime meets the security isolation requirements during update. The detection process includes two stages: node marking during update and node detection during update:
(51)更新时节点标记过程为:步骤(5)中所述配置操作包括创建实例、删除实例、创建安全策略、删除安全策略。当云平台中的管理员或租户管理员实施上述操作时,对当前状态图模型Gtime进行增量更新。所述增量更新,实施时具体可以包含以下四类情况:(51) The node marking process when updating is as follows: the configuration operations described in step (5) include creating an instance, deleting an instance, creating a security policy, and deleting a security policy. When the administrator in the cloud platform or the tenant administrator implements the above operations, incremental update is performed on the current state diagram model Gtime . The incremental update can specifically include the following four situations during implementation:
边插入:当创建或删除新的安全策略使步骤(5)所述当前状态图模型Gtime中的节点vi可访问vj时,设置步骤(1)中所述连通关系ci,j=1,使二维邻接矩阵A[i][j]=1,从而执行边插入。Edge insertion: when a new security policy is created or deleted so that node vi in the current state graph model Gtime described in step (5) can access vj , set the connectivity relationship ci,j = 1, making the two-dimensional adjacency matrix A[i][j]=1, thereby performing edge insertion.
边删除:当创建或删除新的安全策略使步骤(5)所述当前状态图模型Gtime中的节点vi不可访问vj时,设置步骤(1)中所述连通关系ci,j=0,使二维邻接矩阵A[i][j]=0,从而执行边删除。Edge deletion: when the creation or deletion of a new security policy makes the node vi in the current state graph model Gtime in step (5) inaccessible to vj , set the connection relationship ci,j = 0, making the two-dimensional adjacency matrix A[i][j]=0, thereby performing edge deletion.
点插入:当创建新实例时,在步骤(5)所述当前状态图模型Gtime中插入新节点,记为vnew,new表示节点标识。若记Gtime中其他节点的标识为k,初始化步骤(1)中所述二维邻接矩阵A,使A[new][k]=0且A[k][new]=0。当节点vnew可访问vk时,设置步骤(1)中所述连通关系cnew,k=1,使二维邻接矩阵A[new][k]=1;当节点vk可访问 vnew时,设置连通关系ck,new=1,使二维邻接矩阵A[k][new]=1。从而执行点插入。Point insertion: when a new instance is created, a new node is inserted into the current state graph model Gtime described in step (5), denoted as vnew , and new represents the node identifier. If the identifiers of other nodes in Gtime are denoted as k, initialize the two-dimensional adjacency matrix A in step (1) so that A[new][k]=0 and A[k][new]=0. When the node vnew can access vk , set the connectivity relationship cnew in step (1), k =1, so that the two-dimensional adjacency matrix A[new][k]=1; when the node vk can access vnew When , set the connectivity relationshipck, new =1, and make the two-dimensional adjacency matrix A[k][new]=1. Thereby, point insertion is performed.
点删除:当删除新实例时,在步骤(5)所述当前状态图模型Gtime中定位该实例对应的节点,记为vdel,del表示节点标识。此时通过设置del=-1将节点vdel标记为失效,不参与检测。从而执行点删除。Point deletion: when deleting a new instance, locate the node corresponding to the instance in the current state graph model Gtime described in step (5), denoted as vdel , where del represents the node identifier. At this time, the node vdel is marked as invalid by settingdel =-1, and does not participate in the detection. Thereby, point deletion is performed.
例如,若租户管理员修改表1中pod3对应Ingress属性为“{}”,则此时Gtime对应二维邻接矩阵表示为:For example, if the tenant administrator modifies the Ingress attribute corresponding to pod3 in Table 1 to "{}", then the two-dimensional adjacency matrix corresponding to Gtime is expressed as:
然后,将被更新节点从尾端插入待检测队列Detect。此时,由于pod3被更新,则标记为待检测节点,加入Detect队列。Then, the updated node is inserted into the queue to be detected Detect from the end. At this time, since pod3 is updated, it is marked as a node to be detected and added to the Detect queue.
Detect={pod3}Detect={pod3}
(52)更新时节点检测过程为:从待检测队列Detect头端依次读取节点直至队列为空,将当前读取节点记为vdet。检测vdet是否符合安全隔离需求,并在检测完成后将vdet从头端移出待检测队列Detect。具体检测内容包括:基于检测基准(21)执行的租户安全隔离检测,基于检测基准(22)执行的用户组安全隔离检测。(52) The node detection process during update is: read nodes sequentially from the head end of the queue Detect to be detected until the queue is empty, and record the current read node as vdet . Check whether the vdet meets the security isolation requirements, and remove the vdet from the headend to be detected from the queue Detect after the detection is complete. The specific detection contents include: tenant security isolation detection performed based on the detection benchmark (21), and user group security isolation detection performed based on the detection benchmark (22).
首先执行租户安全隔离检测:遍历步骤(3)中所述当前状态图模型Gtime中的所有节点,将当前遍历到的节点记为vk,k表示节点标识。此时,若步骤(1)中所述二维邻接矩阵A[k][det]=1,则当且仅当步骤(2)中所述f(det)=f(k)时,可认定节点vdet满足租户安全隔离;First, perform tenant security isolation detection: traverse all nodes in the current state graph model Gtime described in step (3), and record the currently traversed node as vk , where k represents a node identifier. At this time, if the two-dimensional adjacency matrix A[k][det]=1 in step (1), then if and only if f(det)=f(k) in step (2), it can be determined that Node vdet satisfies tenant security isolation;
然后执行基于区域安全域的状态检测:遍历步骤(3)中所述当前状态图模型Gtime中的所有节点,将当前遍历到的节点记为vk,k表示节点标识。此时,若步骤(1)中所述二维邻接矩阵A[k][det]=1,则仅当步骤(2)中所述y(k)=y(det)>0或y(k)= 1且y(det)!=1或y(k)!=0且y(det)=0时,可认定节点vdet满足用户组安全隔离。Then perform the state detection based on the regional security domain: traverse all the nodes in the current state graph model Gtime described in step (3), record the currently traversed node as vk , and k represents the node identifier. At this time, if the two-dimensional adjacency matrix A[k][det]=1 in step (1), then only if y(k)=y(det)>0 or y(k) in step (2) ) = 1 and y(det)! =1 or y(k)! =0 and y(det)=0, it can be determined that the node vdet satisfies the user group security isolation.
提供以上实施例仅仅是为了描述本发明的目的,而并非要限制本发明的范围。本发明的范围由所附权利要求限定。不脱离本发明的精神和原理而做出的各种等同替换和修改,均应涵盖在本发明的范围之内。The above embodiments are provided for the purpose of describing the present invention only, and are not intended to limit the scope of the present invention. The scope of the invention is defined by the appended claims. Various equivalent replacements and modifications made without departing from the spirit and principle of the present invention should be included within the scope of the present invention.
Claims (4)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201811473272.8ACN109412866B (en) | 2018-12-04 | 2018-12-04 | Active detection method for multi-tenant cloud platform security isolation |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201811473272.8ACN109412866B (en) | 2018-12-04 | 2018-12-04 | Active detection method for multi-tenant cloud platform security isolation |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN109412866A CN109412866A (en) | 2019-03-01 |
| CN109412866Btrue CN109412866B (en) | 2020-07-28 |
Family
ID=65456980
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN201811473272.8AActiveCN109412866B (en) | 2018-12-04 | 2018-12-04 | Active detection method for multi-tenant cloud platform security isolation |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN109412866B (en) |
Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US8839345B2 (en)* | 2008-03-17 | 2014-09-16 | International Business Machines Corporation | Method for discovering a security policy |
| CN104092565A (en)* | 2014-06-24 | 2014-10-08 | 复旦大学 | A Multitenant Policy-Driven Software-Defined Networking Approach for Cloud Data Centers |
| CN107104963A (en)* | 2017-04-25 | 2017-08-29 | 华中科技大学 | Towards the trusted controller framework and its operating method of cloud environment multi-tenant network |
| CN107689953A (en)* | 2017-08-18 | 2018-02-13 | 中国科学院信息工程研究所 | A kind of vessel safety monitoring method and system towards multi-tenant cloud computing |
Family Cites Families (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN106569895B (en)* | 2016-10-24 | 2020-12-22 | 华南理工大学 | A container-based multi-tenant big data platform construction method |
| US10345046B2 (en)* | 2017-05-25 | 2019-07-09 | Northeastern University | Fault diagnosis device based on common information and special information of running video information for electric-arc furnace and method thereof |
- 2018
- 2018-12-04CNCN201811473272.8Apatent/CN109412866B/enactiveActive
Patent Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US8839345B2 (en)* | 2008-03-17 | 2014-09-16 | International Business Machines Corporation | Method for discovering a security policy |
| CN104092565A (en)* | 2014-06-24 | 2014-10-08 | 复旦大学 | A Multitenant Policy-Driven Software-Defined Networking Approach for Cloud Data Centers |
| CN107104963A (en)* | 2017-04-25 | 2017-08-29 | 华中科技大学 | Towards the trusted controller framework and its operating method of cloud environment multi-tenant network |
| CN107689953A (en)* | 2017-08-18 | 2018-02-13 | 中国科学院信息工程研究所 | A kind of vessel safety monitoring method and system towards multi-tenant cloud computing |
Non-Patent Citations (1)
| Title |
|---|
| 《面向多租户应用的云数据隐私保护机制研究》;张坤;《山东大学博士论文》;20131231;全文* |
Also Published As
| Publication number | Publication date |
|---|---|
| CN109412866A (en) | 2019-03-01 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN115039098B (en) | Fuzzy network detection pattern matching | |
| US10956566B2 (en) | Multi-point causality tracking in cyber incident reasoning | |
| Fan et al. | An improved network security situation assessment approach in software defined networks | |
| US10630703B1 (en) | Methods and system for identifying relationships among infrastructure security-related events | |
| Khan et al. | Cloud log forensics: Foundations, state of the art, and future directions | |
| US11941054B2 (en) | Iterative constraint solving in abstract graph matching for cyber incident reasoning | |
| US10630716B1 (en) | Methods and system for tracking security risks over infrastructure | |
| US20200120118A1 (en) | Endpoint inter-process activity extraction and pattern matching | |
| US10193929B2 (en) | Methods and systems for improving analytics in distributed networks | |
| US9619260B2 (en) | Policy enforcement in a virtualized environment | |
| US20210176260A1 (en) | Characterizing user behavior in a computer system by automated learning of intention embedded in a system-generated event graph | |
| US10630704B1 (en) | Methods and systems for identifying infrastructure attack progressions | |
| US8898269B2 (en) | Reconciling network management data | |
| US9246774B2 (en) | Sample based determination of network policy violations | |
| CN106888106A (en) | The extensive detecting system of IT assets in intelligent grid | |
| CN110728575A (en) | WEB security depth monitoring method for electric power transaction platform | |
| US12250230B2 (en) | Lateral movement analysis using certificate private keys | |
| CN103888304A (en) | Abnormity detection method of multi-node application and related apparatus | |
| CN105339925A (en) | Passive monitoring of virtual systems using agent-less, near-real-time indexing | |
| Dwaraki et al. | GitFlow: Flow revision management for software-defined networks | |
| CN117650948B (en) | Network attack and defense simulation method based on discrete event model | |
| US20250086271A1 (en) | Realtime identity attack detection and remediation | |
| Khan et al. | Towards an applicability of current network forensics for cloud networks: A SWOT analysis | |
| CN103023704B (en) | Virtual network service equipment access method and system | |
| US20240143737A1 (en) | Automated generation of labeled training data |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |