CN107465702B - Method and device for early warning based on wireless network intrusion - Google Patents
Method and device for early warning based on wireless network intrusionDownload PDFInfo
- Publication number
- CN107465702B CN107465702BCN201710944307.0ACN201710944307ACN107465702BCN 107465702 BCN107465702 BCN 107465702BCN 201710944307 ACN201710944307 ACN 201710944307ACN 107465702 BCN107465702 BCN 107465702B
- Authority
- CN
- China
- Prior art keywords
- network
- preset
- early warning
- access
- wireless network
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Active
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1433—Vulnerability analysis
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1441—Countermeasures against malicious traffic
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1441—Countermeasures against malicious traffic
- H04L63/1466—Active attacks involving interception, injection, modification, spoofing of data unit addresses, e.g. hijacking, packet injection or TCP sequence number attacks
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1441—Countermeasures against malicious traffic
- H04L63/1491—Countermeasures against malicious traffic using deception as countermeasure, e.g. honeypots, honeynets, decoys or entrapment
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Telephonic Communication Services (AREA)
- Small-Scale Networks (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明涉及网络通信技术领域,具体涉及一种基于无线网络入侵的预警 方法及装置。The present invention relates to the technical field of network communication, in particular to an early warning method and device based on wireless network intrusion.
背景技术Background technique
随着通信技术的不断发展,互联网已经融入了生活的方方面面。然而, 黑客技术作为互联网发展的衍生物,也变得无孔不入,日益严峻地威胁着网 络安全。With the continuous development of communication technology, the Internet has been integrated into all aspects of life. However, as a derivative of the development of the Internet, hacking technology has also become pervasive, threatening network security more and more severely.
以无线网络为例而言,虽然无线网络以其便于接入的优势赢得了越来越 多的用户。但是,通过入侵无线网络而实现黑客攻击的事件也日益高发。为 此,出现了各种各样的防御手段来应对黑客的入侵。在传统的防御方式中, 主要通过增强无线网络本身的安全性来实现防御,例如,将无线网络的密码 重置为不易破解的内容;又如,在网络接入环节,加强针对接入设备的验证, 以防非法设备的恶意接入等。Take wireless network as an example, although wireless network has won more and more users with its advantages of easy access. However, the incidence of hacker attacks by compromising wireless networks is also increasing. For this reason, various defensive measures have emerged to deal with the hacker's intrusion. In traditional defense methods, defense is mainly achieved by enhancing the security of the wireless network itself, for example, resetting the password of the wireless network to something that is not easy to crack; another example, in the network access link, strengthening the security of access devices. Verification to prevent malicious access of illegal devices, etc.
但是,发明人在实现本发明的过程中,发现现有技术中的上述方式至少 存在如下问题:现有的方式主要通过入侵之前的被动防御方式实现,即:在 电子设备试图接入无线网络之前,制造障碍以阻挠非法电子设备的恶意接入。 但是,一旦防御失败,入侵无线网络的电子设备即可肆意实施恶意行为,而 现有的方式则无法针对入侵无线网络的电子设备进行有效预警。However, in the process of implementing the present invention, the inventor found that the above-mentioned methods in the prior art have at least the following problems: the existing methods are mainly implemented by passive defense methods before intrusion, that is: before the electronic device attempts to access the wireless network , creating barriers to prevent malicious access to illegal electronic devices. However, once the defense fails, the electronic devices that invade the wireless network can arbitrarily carry out malicious acts, and the existing methods cannot provide effective early warning for the electronic devices that invade the wireless network.
发明内容SUMMARY OF THE INVENTION
鉴于上述问题,提出了本发明以便提供一种克服上述问题或者至少部分 地解决上述问题的基于无线网络入侵的预警方法及装置。In view of the above problems, the present invention is proposed to provide a wireless network intrusion-based early warning method and device that overcomes the above problems or at least partially solves the above problems.
依据本发明的一个方面,提供了一种基于无线网络入侵的预警方法,包 括:According to one aspect of the present invention, a kind of early warning method based on wireless network intrusion is provided, comprising:
获取入侵无线网络的电子设备产生的网络流量信息;Obtain network traffic information generated by electronic devices that invade the wireless network;
针对所述网络流量信息进行分析,根据分析结果确定所述电子设备的网 络访问行为;Analyze the network traffic information, and determine the network access behavior of the electronic device according to the analysis result;
判断所述电子设备的网络访问行为是否符合预设的预警规则,若是,则 生成用于预警的入侵预警信号。It is judged whether the network access behavior of the electronic device complies with the preset early warning rules, and if so, an intrusion warning signal for early warning is generated.
根据本发明的另一方面,提供了一种基于无线网络入侵的预警装置,包 括:According to another aspect of the present invention, a kind of early warning device based on wireless network intrusion is provided, comprising:
获取模块,适于获取入侵无线网络的电子设备产生的网络流量信息;an acquisition module, adapted to acquire network traffic information generated by electronic devices that invade the wireless network;
分析模块,适于针对所述网络流量信息进行分析,根据分析结果确定所 述电子设备的网络访问行为;an analysis module, adapted to analyze the network traffic information, and determine the network access behavior of the electronic device according to the analysis result;
预警模块,适于判断所述电子设备的网络访问行为是否符合预设的预警 规则,若是,则生成用于预警的入侵预警信号。The early warning module is suitable for judging whether the network access behavior of the electronic equipment complies with the preset early warning rules, and if so, generates an intrusion warning signal for early warning.
根据本发明的再一个方面,提供了一种电子设备,包括:处理器、存储 器、通信接口和通信总线,所述处理器、所述存储器和所述通信接口通过所 述通信总线完成相互间的通信;According to yet another aspect of the present invention, an electronic device is provided, comprising: a processor, a memory, a communication interface and a communication bus, the processor, the memory and the communication interface complete mutual communication through the communication bus communication;
所述存储器用于存放至少一可执行指令,所述可执行指令使所述处理器 执行上述基于无线网络入侵的预警方法对应的操作。The memory is used for storing at least one executable instruction, and the executable instruction causes the processor to perform the operations corresponding to the above-mentioned wireless network intrusion-based early warning method.
根据本发明的再一个方面,提供了一种计算机存储介质,所述存储介质 中存储有至少一可执行指令,所述可执行指令使处理器执行上述基于无线网 络入侵的预警方法对应的操作。According to another aspect of the present invention, a computer storage medium is provided, wherein the storage medium stores at least one executable instruction, and the executable instruction causes the processor to perform the operations corresponding to the above-mentioned wireless network intrusion-based early warning method.
在本发明提供的基于无线网络入侵的预警方法及装置中,首先,获取入 侵无线网络的电子设备产生的网络流量信息;然后,针对该网络流量信息进 行分析,根据分析结果确定电子设备的网络访问行为;最后,判断电子设备 的网络访问行为是否符合预设的预警规则,若是,则生成用于预警的入侵预 警信号。由此可见,本发明能够根据获取到的入侵无线网络的电子设备产生 的网络流量信息来确定是否预警,以实现有针对性地防护。In the method and device for early warning based on wireless network intrusion provided by the present invention, first, network traffic information generated by an electronic device that invades the wireless network is obtained; then, the network traffic information is analyzed, and the network access of the electronic device is determined according to the analysis result. Finally, it is judged whether the network access behavior of the electronic device complies with the preset warning rules, and if so, an intrusion warning signal for early warning is generated. It can be seen that the present invention can determine whether to give an early warning according to the acquired network traffic information generated by the electronic device that invades the wireless network, so as to realize targeted protection.
上述说明仅是本发明技术方案的概述,为了能够更清楚了解本发明的技 术手段,而可依照说明书的内容予以实施,并且为了让本发明的上述和其它 目的、特征和优点能够更明显易懂,以下特举本发明的具体实施方式。The above description is only an overview of the technical solutions of the present invention, in order to be able to understand the technical means of the present invention more clearly, it can be implemented according to the content of the description, and in order to make the above and other purposes, features and advantages of the present invention more obvious and easy to understand , the following specific embodiments of the present invention are given.
附图说明Description of drawings
通过阅读下文优选实施方式的详细描述,各种其他的优点和益处对于本 领域普通技术人员将变得清楚明了。附图仅用于示出优选实施方式的目的, 而并不认为是对本发明的限制。而且在整个附图中,用相同的参考符号表示 相同的部件。在附图中:Various other advantages and benefits will become apparent to those of ordinary skill in the art upon reading the following detailed description of the preferred embodiments. The drawings are for the purpose of illustrating preferred embodiments only and are not to be considered limiting of the invention. Also, the same components are denoted by the same reference numerals throughout the drawings. In the attached image:
图1示出了本发明一个实施例提供的基于无线网络入侵的预警方法的流 程图;Fig. 1 shows the flow chart of the early warning method based on wireless network intrusion provided by an embodiment of the present invention;
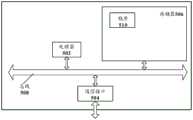
图2示出了一种无线网络入侵检测系统的结构图;Fig. 2 shows a structure diagram of a wireless network intrusion detection system;
图3示出了无线网络入侵检测系统中的多层环的结构示意图;3 shows a schematic structural diagram of a multi-layer ring in the wireless network intrusion detection system;
图4示出了本发明一个实施例提供的基于无线网络入侵的预警装置的结 构图;4 shows a structural diagram of an early warning device based on wireless network intrusion provided by an embodiment of the present invention;
图5示出了根据本发明一个实施例提供的电子设备的结构示意图。FIG. 5 shows a schematic structural diagram of an electronic device provided according to an embodiment of the present invention.
具体实施方式Detailed ways
下面将参照附图更详细地描述本公开的示例性实施例。虽然附图中显示 了本公开的示例性实施例,然而应当理解,可以以各种形式实现本公开而不 应被这里阐述的实施例所限制。相反,提供这些实施例是为了能够更透彻地 理解本公开,并且能够将本公开的范围完整的传达给本领域的技术人员。Exemplary embodiments of the present disclosure will be described in more detail below with reference to the accompanying drawings. While exemplary embodiments of the present disclosure are shown in the drawings, it should be understood that the present disclosure may be embodied in various forms and should not be limited by the embodiments set forth herein. Rather, these embodiments are provided so that the present disclosure will be more thoroughly understood, and will fully convey the scope of the present disclosure to those skilled in the art.
图1示出了本发明一个实施例提供的一种基于无线网络入侵的预警方法 的流程图。如图1所示,该方法包括以下步骤:Fig. 1 shows a flowchart of an early warning method based on wireless network intrusion provided by an embodiment of the present invention. As shown in Figure 1, the method includes the following steps:
步骤S110:获取入侵无线网络的电子设备产生的网络流量信息。Step S110: Acquire network traffic information generated by the electronic device that invades the wireless network.
具体地,当无线网络中包含多个预设设备时,为了准确地获取电子设备 与每个预设设备之间产生的网络流量信息,在本步骤中,分别获取电子设备 入侵无线网络后针对无线网络中的各个预设设备产生的点对点网络流量信 息,并将该点对点网络流量信息提供给对应的预设设备;其中,各个预设设 备以桥接方式接入无线网络。其中,本实施例中提到的预设设备可以为入侵 检测模块等各类设备。Specifically, when the wireless network includes a plurality of preset devices, in order to accurately obtain the network traffic information generated between the electronic device and each preset device, in this step, after the electronic device invades the wireless network, the The peer-to-peer network traffic information generated by each preset device in the network, and the peer-to-peer network traffic information is provided to the corresponding preset device; wherein, each preset device is connected to the wireless network in a bridging manner. Wherein, the preset device mentioned in this embodiment may be various devices such as an intrusion detection module.
步骤S120:针对该网络流量信息进行分析,根据分析结果确定电子设备 的网络访问行为。Step S120: Analyze the network traffic information, and determine the network access behavior of the electronic device according to the analysis result.
通过对网络流量信息进行分析,能够确定电子设备打开了哪些网页、发 送了哪些网络访问请求等各类网络访问行为,从而能够推测电子设备的动机。 其中,分析网络流量信息的具体实现方式可由本领域技术人员灵活选择,本 发明对此不做限定。另外,网络访问行为包括但不限于以下行为:使用扫描 工具进行扫描的行为、针对预设设备发送访问请求的行为等。By analyzing the network traffic information, it is possible to determine which web pages the electronic device has opened, which network access requests have been sent, and other network access behaviors, so as to speculate on the motives of the electronic device. The specific implementation manner of analyzing the network traffic information can be flexibly selected by those skilled in the art, which is not limited in the present invention. In addition, network access behaviors include, but are not limited to, the following behaviors: scanning using scanning tools, sending access requests to preset devices, etc.
步骤S130:确定当前的网络安全等级,选择与当前的网络安全等级相匹 配的预警规则。Step S130: Determine the current network security level, and select an early warning rule matching the current network security level.
其中,本步骤为一个可选的步骤,当预设的预警规则仅为一种时,也可 以省略本步骤。Wherein, this step is an optional step, and when there is only one preset warning rule, this step can also be omitted.
例如,在本实施例中,可以将网络安全等级预先划分为高级、中级、低 级三种,相应地,可以根据系统当前执行的任务或运行的环境等信息来确定 系统当前所处的网络安全等级,进而选择与当前的网络安全等级相匹配的预 警规则。For example, in this embodiment, the network security level can be pre-divided into three types: high level, medium level, and low level. Correspondingly, the current network security level of the system can be determined according to information such as tasks currently performed by the system or operating environment. , and then select the warning rule that matches the current network security level.
步骤S140:判断该电子设备的网络访问行为是否符合预设的预警规则, 若是,则生成用于预警的入侵预警信号。Step S140: Determine whether the network access behavior of the electronic device complies with a preset early warning rule, and if so, generate an intrusion early warning signal for early warning.
其中,预设的预警规则可以包括以下规则中的至少一个:The preset early warning rules may include at least one of the following rules:
当监测到通过预设扫描工具实施扫描行为时进行预警的规则;A rule for alerting when a scanning behavior is detected by a preset scanning tool;
当监测到针对无线网络内的预设设备实施试探性连接的行为时进行预警 的规则;以及Rules for alerting when a tentative connection to a preset device within a wireless network is detected; and
当监测到针对无线网络内的预设设备连接成功的行为时进行预警的规 则。A rule for alerting when a successful connection to a preset device in the wireless network is detected.
上述的几种规则既可以单独使用,也可以结合使用。并且,上述的几种 规则可以分别对应于不同的网络安全等级。相应地,在本步骤中,根据当前 的网络安全等级所对应的预警规则确定电子设备的网络访问行为是否符合预 设的预警规则,若是,则生成用于预警的入侵预警信号。The above-mentioned rules can be used individually or in combination. Moreover, the above-mentioned several kinds of rules may correspond to different network security levels respectively. Correspondingly, in this step, it is determined whether the network access behavior of the electronic device complies with the preset early warning rules according to the early warning rules corresponding to the current network security level, and if so, an intrusion early warning signal for early warning is generated.
另外,可选地,为了获取到电子设备的更多信息,本发明中获取入侵无 线网络的电子设备产生的网络流量信息的步骤之后,还可以进一步包括步骤: 根据电子设备产生的网络流量信息,拦截电子设备发送的网站访问请求,在 拦截到的网站访问请求中插入用于访问预设网站的预设访问脚本;接收与预 设网站相对应的访问结果数据,根据该访问结果数据确定电子设备的设备属 性信息。相应地,在生成用于预警的入侵预警信号的步骤之后,进一步包括 步骤:根据设备属性信息定位该电子设备。其中,预设网站可以是预设的社交网站,相应地,访问结果数据可能包括用户的社交账号信息及密码信息等。In addition, optionally, in order to obtain more information about the electronic device, after the step of obtaining the network traffic information generated by the electronic device that invades the wireless network in the present invention, it may further include the step of: according to the network traffic information generated by the electronic device, Intercept the website access request sent by the electronic device, insert a preset access script for accessing the preset website into the intercepted website access request; receive the access result data corresponding to the preset website, and determine the electronic device according to the access result data device attribute information. Correspondingly, after the step of generating an intrusion warning signal for early warning, the method further includes the step of: locating the electronic device according to the device attribute information. The preset website may be a preset social networking website, and accordingly, the access result data may include the user's social account information and password information, and the like.
由此可见,本发明能够根据获取到的入侵无线网络的电子设备产生的网 络流量信息来确定是否预警,以实现有针对性地防护。It can be seen that the present invention can determine whether to give an early warning according to the acquired network traffic information generated by the electronic device that invades the wireless network, so as to realize targeted protection.
为了便于理解本发明,图2示出了本发明提供的一种具体的无线网络入 侵检测系统的结构示意图,相应地,本发明中的基于无线网络入侵的预警方 法可基于该系统实现。如图2所示,该系统包括:无线接入模块21、网络传 输模块22、第一入侵检测模块23、以及第二入侵检测模块24。其中,图2所 示的第二入侵检测模块24的数量为多个,实际情况中,第二入侵检测模块24 的数量也可以仅为一个。并且,在本发明其他的实施例中,第一入侵检测模 块23的数量也可以为多个。In order to facilitate understanding of the present invention, Fig. 2 shows a schematic structural diagram of a specific wireless network intrusion detection system provided by the present invention, and accordingly, the early warning method based on wireless network intrusion in the present invention can be implemented based on this system. As shown in Figure 2, the system includes: a
在本实施例中,无线网络入侵检测系统主要用于诱使攻击者接入,监视 并记录攻击者的设备信息及攻击行为,相应地,可以实现有针对性地防御措 施,也可以在必要时实施报警,还可以针对攻击者进行溯源追踪等。因此, 本实施例中的无线网络入侵检测系统也可以理解为通过蜜罐技术实现的蜜罐 系统,该蜜罐系统能够实现多种功能。下面分别介绍该系统中的各个模块的 具体结构和工作原理:In this embodiment, the wireless network intrusion detection system is mainly used to induce attackers to access, monitor and record the attacker's device information and attack behaviors. Accordingly, targeted defense measures can be implemented, or when necessary Implement alarms, and trace the source of attackers. Therefore, the wireless network intrusion detection system in this embodiment can also be understood as a honeypot system realized by a honeypot technology, and the honeypot system can realize various functions. The specific structure and working principle of each module in the system are introduced as follows:
一、无线接入模块1. Wireless access module
系统的最外层为无线接入模块21。无线接入模块21适于监测是否存在通 过预设的网络漏洞入侵无线网络的电子设备;当监测结果为是时,获取该电 子设备的设备标识以及与该设备标识相对应的设备接入信息;可选的,还可 以针对该设备接入信息进行分析,根据分析结果对该电子设备进行定位。由 此可见,无线接入模块21主要具备两方面的功能:一方面,主动设置网络漏 洞,以便诱使攻击者接入;另一方面,一旦发现接入无线网络的电子设备则 记录该电子设备的设备标识以及设备接入信息。The outermost layer of the system is the
首先,介绍设置网络漏洞的具体实现方式:具体地,无线接入模块21在 预设的无线接入设备中设置网络漏洞,以供外部的电子设备接入无线网络。 其中,无线接入设备可以为路由器等各类能够用于接入无线网络的接入点。 具体地,设置网络漏洞时,可以通过开启无线网络端口、和/或弱化无线网络 密码等多种方式实现。其中,网络漏洞也可以理解为陷阱,主要用于诱骗攻 击者接入。本发明对设置网络漏洞的具体实现方式不做限定。First, the specific implementation method of setting network loopholes is introduced: Specifically, the
然后,介绍记录电子设备的设备标识以及设备接入信息的具体实现方式。 其中,设备标识可以是各种能够唯一标识一台电子设备的信息,以便于在后 续过程中根据设备标识对该电子设备的相关信息进行追踪。设备接入信息是 指:能够在设备接入无线网络的过程中获取到的与该设备相关的信息。相应 地,无线接入模块21记录连接该无线网络的设备名称、IP地址、MAC地址 等设备接入信息,以便定位攻击者的物理位置,使攻击者一接入无线网络就 处于被监视状态。可选的,为了迫使攻击者泄露更多的信息,在本实施例中,无线接入模块21在获取该电子设备的设备标识以及与该设备标识相对应的设 备接入信息时,还可以进一步向电子设备推送预设网页,获取该电子设备针 对预设网页产生的访问结果,根据访问结果确定该电子设备的设备接入信息。 其中,预设网页包括:通过社交账号登录的社交网页或其他需要通过个人信 息而登录的页面,相应地,电子设备的设备接入信息进一步包括:根据针对 社交网页产生的访问结果确定的社交账号信息,例如,微博账号及密码信息、 QQ账号及密码信息等。除此之外,在电子设备访问网页的过程中,还可以进 一步获取到其他的设备接入信息,例如,浏览器版本、操作系统版本、设备 屏幕分辨率、以及浏览器插件信息等设备接入信息。无线接入模块21将该电 子设备的设备接入信息与该电子设备的设备标识关联存储到预设的设备接入 表中,以备后续查询。Then, the specific implementation of recording the device identification of the electronic device and the device access information is introduced. Wherein, the device identifier can be various pieces of information that can uniquely identify an electronic device, so that the related information of the electronic device can be tracked according to the device identifier in the subsequent process. Device access information refers to the information related to the device that can be acquired during the process of the device accessing the wireless network. Correspondingly, the
由此可见,无线接入模块主要用于诱使攻击者接入并获取相应的设备接 入信息,以便实现定位或预警等功能。It can be seen that the wireless access module is mainly used to induce attackers to access and obtain the corresponding device access information in order to realize functions such as positioning or early warning.
二、网络传输模块2. Network transmission module
系统的次外层为网络传输模块22。网络传输模块22适于获取电子设备接 入无线网络后产生的网络流量信息,并将获取到的网络流量信息提供给第一 入侵检测模块23进行后续分析。另外,网络传输模块22还适于确定电子设 备接入无线网络后产生的网络流量信息中是否包含由符合预设预警规则的访 问行为触发的网络流量,若是,则生成入侵预警信号。具体实施时,网络传 输模块22获取入侵无线网络的电子设备产生的网络流量信息;针对该网络流 量信息进行分析,根据分析结果确定电子设备的网络访问行为;判断该电子设备的网络访问行为是否符合预设的预警规则,若是,则生成用于预警的入 侵预警信号。The second outer layer of the system is the
其中,网络传输模块主要通过网络抓包等方式获取电子设备接入无线网 络后的网络流量信息。另外,发明人在实现本发明的过程中发现:传统的网 络抓包方式只能获取到电子设备通过无线网络访问外部网站的流量,而无法 获取到电子设备与无线网络内部的各个设备之间的流量。例如,在本实施例 中,由于无线网络中包含第一入侵检测模块以及多个第二入侵检测模块等多 个预设设备,因此,为了更加准确地获取电子设备针对每个入侵检测模块产 生的网络流量信息,在本实施例中,将各个第一入侵检测模块以及第二入侵 检测模块以桥接方式接入无线网络,相应地,网络传输模块分别获取电子设 备入侵无线网络后针对无线网络中的各个预设设备(即:第一入侵检测模块 以及第二入侵检测模块)产生的点对点网络流量信息,并将该点对点网络流 量信息提供给对应的预设设备。例如,针对获取到的电子设备访问第一入侵 检测模块的网络流量信息,将该部分网络流量信息提供给第一入侵检测模块 进行后续分析处理。由此可见,本发明通过桥接方式能够准确获取到电子设 备与各个入侵检测模块之间的点对点流量信息,从而便于确定电子设备分别 针对每个入侵检测模块实施的网络行为。Among them, the network transmission module mainly obtains network traffic information after the electronic device is connected to the wireless network through network packet capture and other methods. In addition, the inventor found in the process of implementing the present invention: the traditional network packet capture method can only obtain the traffic of the electronic device accessing external websites through the wireless network, but cannot obtain the traffic between the electronic device and each device inside the wireless network. flow. For example, in this embodiment, since the wireless network includes multiple preset devices such as a first intrusion detection module and a plurality of second intrusion detection modules, in order to more accurately obtain the information generated by the electronic device for each intrusion detection module Network traffic information. In this embodiment, each of the first intrusion detection modules and the second intrusion detection modules are connected to the wireless network in a bridged manner. The peer-to-peer network traffic information generated by each preset device (ie: the first intrusion detection module and the second intrusion detection module), and the peer-to-peer network traffic information is provided to the corresponding preset device. For example, for the obtained network traffic information of the electronic device accessing the first intrusion detection module, the part of the network traffic information is provided to the first intrusion detection module for subsequent analysis and processing. It can be seen that the present invention can accurately obtain the point-to-point traffic information between the electronic device and each intrusion detection module through the bridging method, so as to facilitate the determination of the network behavior performed by the electronic device for each intrusion detection module.
通过分析上述获取到的网络流量信息,能够获知电子设备的网络访问行 为(例如,打开的网页数量和网页地址等)。可选的,在本实施例中,网络 传输模块还能够根据预设的预警规则确定是否针对电子设备的网络访问行为 触发预警信号,从而实现预警作用。预警规则包括多个网络安全等级的预警 规则,相应地,网络传输模块首先要确定当前的网络安全等级,然后,选择 与当前的网络安全等级相匹配的预警规则。例如,可以将网络安全等级分为 三个安全等级:高安全等级、中安全等级、以及低安全等级,相应地,分别 为每种安全等级设定对应的预警规则。系统运营人员可以根据当前业务的需 求设置网络安全等级。相应地,预警规则可以包括以下三种规则中的至少一 个:By analyzing the above-obtained network traffic information, the network access behavior of the electronic device (for example, the number of opened web pages and web page addresses, etc.) can be known. Optionally, in this embodiment, the network transmission module can also determine whether to trigger an early warning signal for the network access behavior of the electronic device according to a preset early warning rule, so as to realize the early warning effect. The early warning rules include early warning rules of multiple network security levels. Correspondingly, the network transmission module should first determine the current network security level, and then select the early warning rules that match the current network security level. For example, the network security level can be divided into three security levels: high security level, medium security level, and low security level. Accordingly, corresponding early warning rules are set for each security level. System operators can set network security levels according to current business needs. Correspondingly, an early warning rule can include at least one of the following three rules:
第一种预警规则为:当监测到通过预设扫描工具实施扫描行为时进行预 警的规则。其中,网络传输模块可以预先获取黑客常用的扫描工具,并将获 取到的扫描工具存储到黑客工具列表中,一旦根据网络流量信息监测到电子 设备利用黑客工具列表中的扫描工具实施扫描的行为则进行预警。其中,黑 客工具列表中存储的扫描工具可以包括:NMAP、SQLMAP、WVS等。第二 种预警规则为:当监测到针对无线网络内的预设设备实施试探性连接的行为 时进行预警的规则。该规则可应用于高安全等级的网络设置中,通过该规则, 只要发现试图连接入侵检测模块等预设设备的行为则进行预警。第三种预警 规则为:当监测到针对无线网络内的预设设备连接成功的行为时进行预警的 规则。该规则可应用于中安全等级或低安全等级的网络设置中,通过该规则, 只有发现连接成功的行为时才进行预警。例如,当检测到针对入侵检测模块 触发的访问请求时则触发预警。The first type of early warning rule is a rule for early warning when the scanning behavior implemented by the preset scanning tool is detected. Among them, the network transmission module can obtain the scanning tools commonly used by hackers in advance, and store the obtained scanning tools in the hacking tool list. Make an early warning. The scanning tools stored in the hacking tool list may include: NMAP, SQLMAP, WVS, and the like. The second type of early warning rule is: a rule for early warning when the behavior of implementing tentative connection to a preset device in the wireless network is detected. This rule can be applied to network settings with high security level, through this rule, an early warning will be given whenever an attempt to connect to a preset device such as an intrusion detection module is found. The third type of early warning rule is: a rule for performing early warning when a behavior of successful connection to a preset device in the wireless network is detected. This rule can be applied to network settings with medium security level or low security level. Through this rule, an early warning will be given only when a successful connection is found. For example, an alert is triggered when an access request triggered by an intrusion detection module is detected.
由此可见,网络传输层能够监测全网范围内的网络流量信息,并根据监 测结果进行预警,以提升系统的安全性。其中,预警规则可由本领域技术人 员灵活设置,本发明对此不做限定。It can be seen that the network transport layer can monitor the network traffic information in the whole network, and give early warning according to the monitoring results to improve the security of the system. Wherein, the early warning rules can be flexibly set by those skilled in the art, which is not limited in the present invention.
可选的,为了获取到电子设备的更多信息,在本实施例中,网络传输模 块还可以进一步实施以下操作:根据电子设备产生的网络流量信息,拦截电 子设备发送的网站访问请求,在拦截到的网站访问请求中插入用于访问预设 网站的预设访问脚本;接收与预设网站相对应的访问结果数据,根据该访问 结果数据确定电子设备的设备属性信息。相应地,网络传输模块也可以进一 步根据设备属性信息定位电子设备。具体实施时,首先,预先设置待拦截的 网站访问请求的类型,例如,可以设置为针对百度等搜索类网站的访问请求进行拦截等。然后,在拦截到的网站访问请求中插入用于访问预设网站的预 设访问脚本。其中,该预设访问脚本可由第一入侵检测模块负责生成并维护, 网络传输模块只需调用该脚本即可。该预设访问脚本可以通过JS脚本或URL 网址实现,用于访问人人网、微博等社交类型的网站。最后,接收与预设网 站相对应的访问结果数据,根据该访问结果数据确定电子设备的设备属性信 息,其中,确定设备属性信息的操作可由第一入侵检测模块实现,相应地, 网络传输模块将接收到的预设网站反馈的访问结果数据发送给第一入侵检测 模块,以供第一入侵检测模块结合该访问结果数据确定电子设备的设备属性 信息。由此可见,网络传输模块在上述过程中主要实现了以下功能:一方面, 代替用户向预设网站的服务器发送针对预设网站的访问请求;另一方面,代 替用户接收服务器返回的访问结果。因此,网络传输模块可以在入侵无线网 络的电子设备的用户毫不知情的情况下访问预设网站并获取访问结果,进而 获取电子设备的相关信息。其中,设备属性信息与设备接入信息的主要区别 在于:二者获取的时机以及获取的主体不同。具体地,设备接入信息在接入 阶段由无线接入模块获取,而设备属性信息则在电子设备渗透到无线网络中 并访问第一入侵检测模块时,由第一入侵检测模块获取,用于反映设备的属 性信息。实际情况中,设备接入信息与设备属性信息的内容可以存在交叉。Optionally, in order to obtain more information of the electronic device, in this embodiment, the network transmission module may further perform the following operations: according to the network traffic information generated by the electronic device, intercept the website access request sent by the electronic device, and then intercept the request for accessing the website sent by the electronic device. Insert a preset access script for accessing the preset website into the received website access request; receive access result data corresponding to the preset website, and determine the device attribute information of the electronic device according to the access result data. Correspondingly, the network transmission module may further locate the electronic device according to the device attribute information. During specific implementation, first, the type of the website access request to be intercepted is preset, for example, it can be set to intercept the access request of search websites such as Baidu. Then, insert a preset access script for accessing the preset website into the intercepted website access request. The preset access script can be generated and maintained by the first intrusion detection module, and the network transmission module only needs to call the script. The preset access script can be implemented through a JS script or a URL, and is used to access social websites such as Renren and Weibo. Finally, the access result data corresponding to the preset website is received, and the device attribute information of the electronic device is determined according to the access result data, wherein the operation of determining the device attribute information can be realized by the first intrusion detection module, and correspondingly, the network transmission module will The received access result data fed back by the preset website is sent to the first intrusion detection module, so that the first intrusion detection module can determine the device attribute information of the electronic device in combination with the access result data. It can be seen that the network transmission module mainly realizes the following functions in the above process: on the one hand, it sends an access request for the preset website to the server of the preset website on behalf of the user; on the other hand, it replaces the user to receive the access result returned by the server. Therefore, the network transmission module can access the preset website and obtain the access result without the user of the electronic device intruding into the wireless network, and then obtain the relevant information of the electronic device. Among them, the main difference between the device attribute information and the device access information is that the timing and the main body of the acquisition are different. Specifically, the device access information is acquired by the wireless access module in the access phase, and the device attribute information is acquired by the first intrusion detection module when the electronic device penetrates into the wireless network and accesses the first intrusion detection module, and is used for Reflects the attribute information of the device. In an actual situation, the content of the device access information and the device attribute information may overlap.
三、第一入侵检测模块3. The first intrusion detection module
第一入侵检测模块位于网络传输层与第二入侵检测模块之间,用于分析 网络传输模块提供的网络流量信息,根据分析结果确定电子设备的设备属性 信息。具体实施时,第一入侵检测模块可通过多种实现方式实现,例如,可 以利用蜜罐技术通过虚拟机或沙箱来实现。蜜罐技术本质上是一种对攻击者 进行欺骗的技术,通过布置一些作为诱饵的主机、网络服务或者信息,诱使 攻击者对它们实施攻击,从而可以对攻击行为进行捕获和分析,了解攻击者 所使用的工具与方法,推测攻击意图和动机,能够让防御方清晰地了解自身 所面对的安全威胁,并通过技术和管理手段来增强实际系统的安全防护能力。 在本实施例中,第一入侵检测模块为web型蜜罐(即:服务型蜜罐),并且, 第一入侵检测模块的交互性低于第二入侵检测模块,因此,也可以将第一入 侵检测模块称作Web型低交互性入侵检测模块。在下文中,为了描述方便, 将第一入侵检测模块称作Web型低交互性蜜罐。The first intrusion detection module is located between the network transmission layer and the second intrusion detection module, and is used to analyze the network traffic information provided by the network transmission module, and determine the device attribute information of the electronic device according to the analysis result. During specific implementation, the first intrusion detection module can be implemented in a variety of implementation manners, for example, it can be implemented through a virtual machine or a sandbox using the honeypot technology. Honeypot technology is essentially a technology to deceive attackers. By arranging some hosts, network services or information as bait to induce attackers to attack them, the attack behavior can be captured and analyzed to understand the attack. The tools and methods used by the attacker, inferring the intention and motivation of the attack, can allow the defender to clearly understand the security threats they face, and enhance the security protection capability of the actual system through technical and management means. In this embodiment, the first intrusion detection module is a web-type honeypot (ie, a service-type honeypot), and the interactivity of the first intrusion detection module is lower than that of the second intrusion detection module. Therefore, the first intrusion detection module can also be The intrusion detection module is called a Web-type low-interaction intrusion detection module. Hereinafter, for the convenience of description, the first intrusion detection module will be referred to as a Web-type low-interaction honeypot.
Web型低交互性蜜罐能够获取入侵无线网络的电子设备所产生的网络流 量信息;针对该网络流量信息进行分析,根据分析结果确定电子设备的设备 标识以及与该设备标识相对应的设备属性信息。可选的,Web型低交互性蜜 罐还能够根据设备属性信息检测电子设备的位置信息,以便对电子设备进行 定位或溯源。由此可见,Web型低交互性蜜罐主要用于进一步收集攻击者的 信息。具体地,可供收集的设备属性信息包括但不限于:浏览器版本、操作 系统版本、设备屏幕分辨率、浏览器插件信息、社交账号信息、设备指纹、 插件信息、时区信息、GPU信息、以及设备语言信息等。The web-type low-interaction honeypot can obtain network traffic information generated by electronic devices that invade the wireless network; analyze the network traffic information, and determine the device identification of the electronic device and the device attribute information corresponding to the device identification according to the analysis results. . Optionally, the web-type low-interaction honeypot can also detect the location information of the electronic device according to the device attribute information, so as to locate or trace the source of the electronic device. It can be seen that the web-type low-interaction honeypot is mainly used to further collect the attacker's information. Specifically, the device attribute information available for collection includes but is not limited to: browser version, operating system version, device screen resolution, browser plug-in information, social account information, device fingerprint, plug-in information, time zone information, GPU information, and Device language information, etc.
另外,为了便于收集更多信息,Web型低交互性蜜罐进一步用于:预先 生成用于访问预设网站的预设访问脚本;其中,预设访问脚本用于插入拦截 到的电子设备发送的网站访问请求中。相应地,Web型低交互性蜜罐根据分 析结果确定电子设备的设备标识以及与该设备标识相对应的设备属性信息 时,结合获取到的与预设网站相对应的访问结果数据确定电子设备的设备属 性信息。其中,预设网站包括:通过社交账号登录的社交网站等,该预设访 问脚本可以通过JS脚本或URL网址实现,用于访问人人网、微博等预设网 站。相应地,电子设备的设备属性信息包括:根据针对社交网站产生的访问 结果确定的社交账号信息。也就是说,Web型低交互性蜜罐负责维护预设访 问脚本,以供网络传输模块调用;并且,Web型低交互性蜜罐进一步用于分 析网络传输模块得到的网络流量信息以及访问结果数据等,以便确定电子设 备的设备属性信息。由此可见,通过Web型低交互性蜜罐以及网络传输模块 的相互配合,能够在电子设备的使用者毫无察觉的情况下自动访问预设网站 并获取相关信息,为后续的攻击者定位及溯源等操作提供了更多有价值的信 息。In addition, in order to facilitate the collection of more information, the web-type low-interaction honeypot is further used to: generate a preset access script for accessing a preset website in advance; wherein, the preset access script is used to insert the intercepted information sent by the electronic device. Website access request. Correspondingly, when the web-type low-interactivity honeypot determines the device identification of the electronic device and the device attribute information corresponding to the device identification according to the analysis result, it is combined with the obtained access result data corresponding to the preset website to determine the device identification of the electronic device. Device attribute information. The preset website includes: a social networking website logged in through a social account, and the like, and the preset access script can be implemented through a JS script or a URL, and is used to access preset websites such as Renren and Weibo. Correspondingly, the device attribute information of the electronic device includes: social account account information determined according to the access result generated for the social networking site. That is to say, the web-type low-interaction honeypot is responsible for maintaining preset access scripts for the network transmission module to call; and the web-type low-interaction honeypot is further used to analyze the network traffic information and access result data obtained by the network transmission module etc., in order to determine the device attribute information of the electronic device. It can be seen that, through the cooperation of the web-type low-interaction honeypot and the network transmission module, the user of the electronic device can automatically access the preset website and obtain relevant information without the user of the electronic device being aware of it, so as to locate and obtain relevant information for subsequent attackers. Operations such as traceability provide more valuable information.
四、第二入侵检测模块Fourth, the second intrusion detection module
第二入侵检测模块位于整个系统的最内层,用于获取电子设备的行为特 征信息,当确定行为特征信息符合预设报警规则时,生成入侵报警信号。具 体实施时,第二入侵检测模块也可通过多种实现方式实现,例如,可以利用 蜜罐技术通过虚拟机或沙箱来实现。在本实施例中,第二入侵检测模块的交 互性高于第一入侵检测模块,因此,也可以将第二入侵检测模块称作高交互 性入侵检测模块。另外,第二入侵检测模块既可以应用于Windows系统,也 可以应用于Linux系统,相应地,第二入侵检测模块的种类可以分为两种,分 别是Windows型高交互性蜜罐和Linux型高交互性蜜罐。在本实施例中,主 要以Windows型高交互性蜜罐为例进行介绍。The second intrusion detection module is located in the innermost layer of the whole system, and is used to obtain the behavior characteristic information of the electronic equipment, and when it is determined that the behavior characteristic information conforms to the preset alarm rules, an intrusion alarm signal is generated. During specific implementation, the second intrusion detection module can also be implemented in a variety of implementation manners, for example, it can be implemented through a virtual machine or a sandbox using the honeypot technology. In this embodiment, the interactivity of the second intrusion detection module is higher than that of the first intrusion detection module. Therefore, the second intrusion detection module may also be referred to as a high-interactivity intrusion detection module. In addition, the second intrusion detection module can be applied to both Windows systems and Linux systems. Correspondingly, the second intrusion detection module can be divided into two types, namely, Windows-type high-interaction honeypots and Linux-type high-interaction honeypots. Interactive honeypot. In this embodiment, a Windows-type high-interactivity honeypot is mainly used as an example for introduction.
具体地,Windows型高交互性蜜罐获取到的电子设备的行为特征信息可 以包括多种,相应地,预设报警规则也可以包括多种规则:Specifically, the behavior feature information of the electronic device obtained by the Windows-type high-interactivity honeypot can include multiple types, and correspondingly, the preset alarm rules can also include multiple types of rules:
第一种规则为:确定行为特征信息是否与预设黑名单中存储的恶意命令 匹配,若是,则生成入侵报警信号(也叫行为入侵报警信号)。具体地,Windows 型高交互性蜜罐监视系统活动以及电子设备的各项行为,若监测到电子设备 执行了预设黑名单中存储的恶意命令时,则触发入侵报警信号。其中,预设 黑名单用于存储预先确定的黑客常用的各项攻击命令。表1、表2和表3示出 了黑名单中存储的部分恶意命令的示意图。The first rule is: determine whether the behavior feature information matches the malicious command stored in the preset blacklist, and if so, generate an intrusion alarm signal (also called behavior intrusion alarm signal). Specifically, the Windows-type high-interaction honeypot monitors system activities and various behaviors of electronic devices, and triggers an intrusion alarm signal if the electronic device executes malicious commands stored in the preset blacklist. Among them, the preset blacklist is used to store predetermined attack commands commonly used by hackers. Table 1, Table 2 and Table 3 show schematic diagrams of some malicious commands stored in the blacklist.
表1Table 1
表2Table 2
表3table 3
第二种规则为:将电子设备操作过的文件记录到预设的操作文件列表中, 将与操作文件列表中的文件存在预设关联关系的文件记录到预设的可疑文件 列表中,通过监测操作文件列表以及可疑文件列表中的文件来确定是否生成 入侵报警信号(也叫文件入侵报警信号)。例如,当监测到可疑文件列表中 的文件被执行时,生成文件入侵报警信号。该规则也可以称作污点追踪技术, 主要思想在于:持续监测并追踪与电子设备有关的所有文件,并在发现可疑 情况时报警。The second rule is: record the files operated by the electronic device in the preset operation file list, record the files that have a preset association relationship with the files in the operation file list in the preset suspicious file list, and monitor the files in the preset suspicious file list. The files in the file list and the suspicious file list are manipulated to determine whether to generate an intrusion alarm signal (also called a file intrusion alarm signal). For example, when a file in the suspicious file list is detected to be executed, a file intrusion alarm signal is generated. This rule can also be called taint tracking technology. The main idea is to continuously monitor and track all files related to electronic equipment, and alert the police when suspicious situations are found.
例如,可以监视文件的创建、修改、删除等各类操作,将这些文件全部 作为电子设备操作过的文件记录到预设的操作文件列表中。由此可见,操作 文件列表用于记录电子设备直接操作过的所有文件,操作类型包括多种类型。 另外,进一步确定与操作文件列表中的文件存在预设关联关系的文件。其中, 存在预设关联关系的文件包括但不限于:与操作文件列表中的文件存在捆绑 关系的文件。举例而言,若电子设备在创建文件A的同时,进一步创建了文 件A的捆绑文件A’,相应地,将文件A记录到操作文件列表中,将文件A’ 记录到可疑文件列表中。并且,在后续过程中,持续针对操作文件列表以及 可疑文件列表进行监测。一旦监测到可疑文件列表中的文件被执行则立刻报 警。也就是说,操作文件列表中的文件时电子设备直接操作的文件,而可疑 文件列表中的文件则是电子设备尚未操作或尚未直接操作(可能间接操作或 隐含操作)的文件。将这两类文件分别存储在不同的列表中,便于根据每种 文件的特点分别为其设定不同的监测方式及报警方式。例如,电子设备之所以要创建捆绑文件,其目的往往是为了规避针对操作文件列表的监测操作, 通常,捆绑文件不出现在桌面系统中,并非真实的文件,只在内存中存在, 因此,具有更强的隐蔽性,但是,一旦该类文件得以执行则会对系统造成危 害。为此,在本实施例中将捆绑文件、隐藏文件等关联文件单独存储到可疑 文件列表中,便于对该部分文件实施更强监控力度的监控,以防止其实施恶 意行为。For example, various operations such as file creation, modification, and deletion can be monitored, and all these files can be recorded in the preset operation file list as the files operated by the electronic device. It can be seen that the operation file list is used to record all the files directly operated by the electronic device, and the operation types include multiple types. In addition, a file that has a preset association relationship with the file in the operation file list is further determined. The files that have a preset association relationship include, but are not limited to: files that have a binding relationship with the files in the operation file list. For example, if the electronic device further creates the bundled file A' of the file A while creating the file A, correspondingly, the file A is recorded in the operation file list, and the file A' is recorded in the suspicious file list. And, in the subsequent process, the operation file list and the suspicious file list are continuously monitored. Once a file in the suspicious file list is detected to be executed, it will immediately report to the police. That is to say, the files in the file list are manipulated directly by the electronic device, while the files in the suspicious file list are the files that the electronic device has not yet manipulated or directly manipulated (possibly indirectly or implicitly manipulated). The two types of files are stored in different lists, so that different monitoring and alarm modes can be set for each file according to the characteristics of each file. For example, the reason why electronic devices create bundled files is often to avoid the monitoring operation for the operation file list. Usually, bundled files do not appear in the desktop system, and are not real files, but only exist in memory. Therefore, with Stronger concealment, however, once this type of file is executed, it will cause harm to the system. For this reason, in this embodiment, associated files such as bundled files and hidden files are separately stored in the suspicious file list, so as to facilitate the monitoring of the part of the files with stronger monitoring strength, so as to prevent them from carrying out malicious behaviors.
除此之外,Windows型高交互性蜜罐还可以进一步监视进程的创建,并 对可疑进程注入monitor.dll(用于监视进程的动态链接库),以跟踪进程行为。 而且,还可以设置进程黑名单,例如,将非系统级进程全部列入进程黑名单 中,对进程黑名单中的各个进程进行持续监测,一旦发现危险进程的创建操 作则触发报警。另外,Windows型高交互性蜜罐还可以监视注册表操作,以 便于发现危险行为。In addition, Windows-type high-interaction honeypots can further monitor the creation of processes, and inject monitor.dll (dynamic link library for monitoring processes) into suspicious processes to track process behavior. In addition, you can also set a process blacklist. For example, all non-system-level processes can be included in the process blacklist, and each process in the process blacklist can be continuously monitored. Once the creation of a dangerous process is found, an alarm will be triggered. In addition, Windows-based high-interaction honeypots can monitor registry operations for risky behavior.
另外,每个Windows型高交互性蜜罐还可以进行日志、报警信息的处理, 并且,还可以实现与第一入侵检测模块或其他Windows型高交互性蜜罐之间 的通信,以实现整个系统的联动处理。为此,无线接入模块进一步适于:将 电子设备的设备接入信息与电子设备的设备标识关联存储;且第一入侵检测 模块进一步适于:将电子设备的设备属性信息与电子设备的设备标识关联存 储;则第二入侵检测模块进一步适于:当确定行为特征信息符合预设的报警 行为规则时,获取并分析与该电子设备的设备标识关联存储的设备接入信息以及设备属性信息等。也就是说,在本系统中,每个模块针对电子设备获取 到的相关信息(包括设备接入信息、设备属性信息以及行为特征信息等)都 与该电子设备的设备标识关联存储,相应地,各个模块能够通过设备标识获 取到与该设备标识关联存储的全部信息。即:每个模块不仅能够获取到自身 确定的信息,还能够获取到其他模块确定的信息,从而实现信息的共享。相 应地,第一入侵检测模块和/或第二入侵检测模块还可以进一步适于:根据电 子设备的设备接入信息、设备属性信息和/或行为特征信息确定与电子设备相 对应的用户标识以及用户特征信息,以便根据用户标识以及用户特征信息进 行溯源。In addition, each Windows-type high-interaction honeypot can also process logs and alarm information, and can also realize communication with the first intrusion detection module or other Windows-type high-interaction honeypots, so as to realize the whole system. linkage processing. To this end, the wireless access module is further adapted to: store the device access information of the electronic device in association with the device identification of the electronic device; and the first intrusion detection module is further adapted to: associate the device attribute information of the electronic device with the device identification of the electronic device The identifier is stored in association; the second intrusion detection module is further adapted to: when it is determined that the behavior feature information conforms to the preset alarm behavior rule, acquire and analyze the device access information and device attribute information stored in association with the device identifier of the electronic device, etc. . That is to say, in this system, the relevant information (including device access information, device attribute information and behavior feature information, etc.) obtained by each module for the electronic device is stored in association with the device identification of the electronic device, and accordingly, Each module can obtain all the information stored in association with the device identification through the device identification. That is, each module can not only obtain the information determined by itself, but also obtain the information determined by other modules, so as to realize the sharing of information. Correspondingly, the first intrusion detection module and/or the second intrusion detection module may be further adapted to: determine the user identity corresponding to the electronic device according to the device access information, device attribute information and/or behavior feature information of the electronic device; User characteristic information, so as to trace the source according to the user identification and user characteristic information.
由此可见,第一入侵检测模块和/或第二入侵检测模块主要用于给攻击者 留下突破口,使攻击者有机会登录到系统中;然后,记录攻击者的系统活动, 对危险行为进行报警,并捕获恶意行为所对应的样本,以便利用沙箱技术进 行分析。It can be seen that the first intrusion detection module and/or the second intrusion detection module are mainly used to leave a breakthrough for the attacker, so that the attacker has the opportunity to log in to the system; Alerts and captures samples corresponding to malicious behavior for analysis using sandbox technology.
另外,本系统实质上利用了多层环来实现对入侵设备的全面监控,图3 示出了本系统中的多层环的结构示意图。如图3所示,本系统从外到内共分 为三层环,位于最外层的环3主要由无线接入模块构成,位于中间的环2主 要由第一入侵检测模块构成,位于最内层的环1主要由第二入侵检测模块构 成。网络传输模块介于环3与环2之间。由此可见,本系统通过多层环的设 计方式诱使攻击者逐环渗入,并泄露更多的信息;并且,各环内收集到的信 息可以联动查询。In addition, the system essentially utilizes the multi-layer ring to realize the comprehensive monitoring of the intrusion device. FIG. 3 shows a schematic diagram of the structure of the multi-layer ring in the system. As shown in Figure 3, the system is divided into three layers of rings from the outside to the inside. The outermost ring 3 is mainly composed of wireless access modules, and the middle ring 2 is mainly composed of the first intrusion detection module. The inner ring 1 is mainly composed of the second intrusion detection module. The network transmission module is between ring 3 and ring 2. It can be seen that this system induces attackers to infiltrate and leak more information through the design of multi-layer rings; moreover, the information collected in each ring can be linked and queried.
另外,环2和环3中的第一入侵检测模块以及第二入侵检测模块均为安 装有真实操作系统的虚拟机,以便于更好的收集信息。并且,为了防止入侵 的电子设备识破蜜罐机制,虚拟机的指纹特征信息通过运行于系统层的预设 程序插件进行管理;其中,指纹特征信息包括:网卡信息、注册表信息和/或 键值信息等。其中,指纹特征信息属于环境特征信息的一种。并且,该程序 插件运行于系统层,其运行权限大于电子设备中的其他进程的权限,因此, 可以有效避免其他进程访问虚拟机的指纹特征信息。In addition, the first intrusion detection module and the second intrusion detection module in ring 2 and ring 3 are virtual machines installed with real operating systems, so as to better collect information. In addition, in order to prevent the intruded electronic device from seeing through the honeypot mechanism, the fingerprint feature information of the virtual machine is managed by a preset program plug-in running at the system layer; wherein, the fingerprint feature information includes: network card information, registry information and/or key value information, etc. Among them, the fingerprint feature information belongs to a kind of environmental feature information. Moreover, the program plug-in runs at the system layer, and its running authority is greater than the authority of other processes in the electronic device, so it can effectively prevent other processes from accessing the fingerprint feature information of the virtual machine.
具体实施时,为了对第一入侵检测模块以及第二入侵检测模块内部的虚 拟化环境进行防护,以防止电子设备识破,第一入侵检测模块和/或第二入侵 检测模块还可以进一步执行以下操作:当监测到用于访问虚拟化环境的环境 特征信息的访问请求消息时,拦截该访问请求消息;确定与该访问请求消息 相对应的访问结果数据,并确定访问结果数据的数据类型;查询与访问结果 数据的数据类型相匹配的防护策略,根据查询到的防护策略对该访问请求消 息进行防护处理。During specific implementation, in order to protect the virtualized environment inside the first intrusion detection module and the second intrusion detection module to prevent the electronic device from seeing through, the first intrusion detection module and/or the second intrusion detection module may further perform the following operations : When monitoring the access request message for accessing the environment feature information of the virtualized environment, intercept the access request message; determine the access result data corresponding to the access request message, and determine the data type of the access result data; For the protection policy that matches the data type of the access result data, protection processing is performed on the access request message according to the queried protection policy.
具体地,需要预先确定用于访问虚拟化环境的环境特征信息的访问请求 消息所对应的应用程序接口(API),针对这些应用程序接口设置挂钩函数; 其中,挂钩函数用于监测通过应用程序接口触发的访问请求消息。其中,虚 拟化环境的环境特征信息包括与系统环境相关的所有特征,例如,包括上述 的虚拟机的指纹特征信息。在确定用于访问虚拟化环境的环境特征信息的访 问请求消息所对应的应用程序接口时,可以监测入侵虚拟化环境的电子设备 针对虚拟化环境发出的访问行为,根据访问行为确定用于访问所述虚拟化环 境的环境特征信息的访问请求消息。举例而言,由于入侵虚拟化环境的电子 设备往往会有意识地获取虚拟化环境的环境特征信息,以便确定当前的系统 环境是否为通过蜜罐技术实现的虚拟化环境,一旦电子设备发现当前的系统 环境是通过蜜罐技术实现的虚拟化环境,则会离开当前环境。因此,通过监 测电子设备的访问行为,能够确定电子设备常用于获取虚拟化环境的环境特 征信息的访问请求消息所对应的API,并针对这些API进行监控。例如,在 本实施例中,通过监测电子设备的访问行为发现,电子设备检测虚拟机时一般通过以下几种手段实现:检测执行环境中的特定CPU指令、检测执行环境 中的特定注册表信息及配置信息、检测执行环境中的特定进程和服务、检测 执行环境中的文件系统和特定硬件信息(MAC地址、硬盘)、检测执行环境 中的内存特征、检测执行环境的配置(硬盘大小、内存大小、CPU核数等)。 另外,由于本实施例中的入侵检测模块还可以通过沙盒实现,因此,通过监 测电子设备的访问行为发现,电子设备检测沙盒时一般通过以下几种手段实现:检测执行环境中是否有特定的用户活动(比如鼠标移动,访问某个网址 等)、Sleep一段时间再执行、循环延迟执行、检测挂钩Hook(包括:用户 Hook、内核Hook等)、检测网络连通性、检测用户名称、只在特定日期执 行、检测时间加速、结束分析工具执行、检测浏览器记录、运行程序、安装 的程序等。并且,电子设备通常会利用多种手段的组合来实现虚拟机和沙箱 的检测操作,为此,本实施例通过预先监测电子设备的上述操作,确定出上 述操作所对应的访问请求消息及其对应的API,相应地,在该API处设置挂 钩函数,以便截获并处理通过该API发送的访问请求消息。Specifically, the application program interface (API) corresponding to the access request message for accessing the environmental feature information of the virtualized environment needs to be predetermined, and hook functions are set for these application program interfaces; Triggered access request message. Wherein, the environment feature information of the virtualized environment includes all features related to the system environment, for example, including the above-mentioned fingerprint feature information of the virtual machine. When determining the application program interface corresponding to the access request message for accessing the environmental feature information of the virtualized environment, the access behavior sent by the electronic device intruding into the virtualized environment for the virtualized environment can be monitored, and the access behavior used to access the virtualized environment can be determined according to the access behavior. The access request message describing the environment characteristic information of the virtualized environment. For example, since electronic devices that invade the virtualized environment often consciously obtain the environmental characteristic information of the virtualized environment, so as to determine whether the current system environment is a virtualized environment realized by honeypot technology, once the electronic device discovers the current system environment The environment is a virtualized environment realized by honeypot technology, and it will leave the current environment. Therefore, by monitoring the access behavior of the electronic device, it is possible to determine the APIs corresponding to the access request messages commonly used by the electronic device to obtain the environmental feature information of the virtualized environment, and monitor these APIs. For example, in this embodiment, by monitoring the access behavior of the electronic device, it is found that when the electronic device detects the virtual machine, it is generally implemented by the following means: detecting specific CPU instructions in the execution environment, detecting specific registry information in the execution environment, and Configuration information, detection of specific processes and services in the execution environment, detection of file systems and specific hardware information (MAC address, hard disk) in the execution environment, detection of memory characteristics in the execution environment, detection of the configuration of the execution environment (hard disk size, memory size) , CPU cores, etc.). In addition, since the intrusion detection module in this embodiment can also be implemented through a sandbox, it is found by monitoring the access behavior of the electronic device that the electronic device generally implements the sandbox detection by the following means: Detecting whether there is a specific User activities (such as mouse movement, visiting a website, etc.), Sleep for a period of time and then execution, loop delay execution, detection hook hooks (including: user hooks, kernel hooks, etc.), detection of network connectivity, detection of user names, only in Execute on a specific date, detect time acceleration, end analysis tool execution, detect browser records, run programs, installed programs, etc. In addition, the electronic device usually uses a combination of various means to realize the detection operation of the virtual machine and the sandbox. Therefore, in this embodiment, the above-mentioned operation of the electronic device is monitored in advance to determine the access request message corresponding to the above-mentioned operation and its corresponding API, accordingly, set hook function at this API to intercept and process the access request message sent through this API.
针对截获到的访问请求消息,确定与该访问请求消息相对应的访问结果 数据,并确定访问结果数据的数据类型;查询与访问结果数据的数据类型相 匹配的防护策略,根据查询到的防护策略对该访问请求消息进行防护处理。 在本实施例中,预先将访问请求消息相对应的访问结果数据划分为第一类数 据类型以及第二类数据类型。For the intercepted access request message, determine the access result data corresponding to the access request message, and determine the data type of the access result data; query the protection policy matching the data type of the access result data, according to the obtained protection policy Perform protection processing on the access request message. In this embodiment, the access result data corresponding to the access request message is divided into a first type of data type and a second type of data type in advance.
其中,第一类数据类型包括:在虚拟化环境中以及非虚拟化环境中同时 具备的数据所对应的类型。例如,无论是虚拟化环境还是非虚拟化环境,都 需要具备网卡信息和注册表信息,因此,将该类信息所对应的访问结果数据 作为第一类数据类型。由于该类型的数据是所有环境中都存在的,因此,必 须向电子设备返回访问结果,否则会引起电子设备使用者的怀疑。对此,本 实施例设置的与第一类数据类型相匹配的防护策略包括:预先针对第一类数 据类型的访问结果数据设置对应的伪结果数据,当拦截到针对第一类数据类型的访问结果数据发出的访问请求消息时,针对该访问请求消息返回与第一 类数据类型的访问结果数据相对应的伪结果数据。也就是说,针对第一类数 据类型的访问结果数据,预先确定该数据的数值是否会泄露虚拟化环境的特 征,若是,则针对该数据设置对应的伪结果数据,并向电子设备返回对应的 伪结果数据。例如,对于物理网卡而言,虽然虚拟化环境和非虚拟化环境都 具备物理网卡,但是,两种环境中的网卡特征可能不同,对此,针对网卡的 访问结果数据,为其设置相对应的伪结果数据(即与非虚拟化环境一致的数 据),一旦电子设备请求网卡数据,则会收到对应的伪结果数据,以使电子 设备无法识破虚拟化环境。Among them, the first type of data type includes: the type corresponding to the data both in the virtualized environment and in the non-virtualized environment. For example, whether it is a virtualized environment or a non-virtualized environment, both network card information and registry information are required. Therefore, the access result data corresponding to this type of information is used as the first type of data type. Since this type of data exists in all environments, access results must be returned to the electronic device, otherwise the user of the electronic device will be suspicious. In this regard, the protection strategy set in this embodiment that matches the first type of data includes: pre-setting corresponding pseudo-result data for the access result data of the first type of data, when intercepting the access to the first type of data When an access request message is sent from the result data, pseudo result data corresponding to the access result data of the first type of data type is returned for the access request message. That is to say, for the access result data of the first type of data, it is pre-determined whether the value of the data will leak the characteristics of the virtualized environment, and if so, the corresponding pseudo result data is set for the data, and the corresponding data is returned to the electronic device. Fake result data. For example, for physical network cards, although both virtualized environments and non-virtualized environments have physical network cards, the characteristics of network cards in the two environments may be different. For pseudo-result data (ie, data consistent with the non-virtualized environment), once the electronic device requests network card data, it will receive corresponding pseudo-result data, so that the electronic device cannot see through the virtualized environment.
第二类数据类型包括:在虚拟化环境中具备、且在非虚拟化环境中不具 备的数据所对应的类型。由于该类型的数据是仅存在于虚拟化环境中的,因 此,一旦向电子设备返回对应的数据则会使电子设备识破虚拟化环境。为此, 本实施例中设置的与第二类数据类型相匹配的防护策略包括:当拦截到针对 第二类数据类型的访问结果数据发出的访问请求消息时,针对该访问请求消 息返回空消息。也就是说,对于第二类数据类型所对应的访问请求消息不予 返回响应结果,以使电子设备无法获取到用于识别虚拟化环境特征的数据。 由此可见,本实施例中的虚拟化环境包括:由虚拟机构造的虚拟化环境、和/ 或由沙箱构造的虚拟化环境。无论是哪种类型的虚拟化环境,都能够通过上 述的两种策略实现防护。The second type of data type includes: the type corresponding to the data that is available in the virtualized environment and not available in the non-virtualized environment. Since this type of data exists only in the virtualized environment, once the corresponding data is returned to the electronic device, the electronic device will see through the virtualized environment. To this end, the protection policy set in this embodiment that matches the second type of data includes: when an access request message sent for the access result data of the second type of data is intercepted, returning an empty message for the access request message . That is to say, no response result is returned for the access request message corresponding to the second type of data, so that the electronic device cannot obtain the data for identifying the characteristics of the virtualization environment. It can be seen from this that the virtualized environment in this embodiment includes: a virtualized environment constructed by a virtual machine, and/or a virtualized environment constructed by a sandbox. Regardless of the type of virtualized environment, protection can be achieved through the two strategies described above.
除此之外,本实施例中还可以通过以下方式实现虚拟化环境的防护:(1) 利用开源硬件虚拟化软件,源码编译去掉或修改虚拟机特定指纹信息,令电 子设备中的恶意软件检测失效;(2)更改沙盒硬件配置使其更像一台真实的 机器(可选的还可以通过Hook方式返回虚假配置信息);(3)正常配置系 统,安装常用软件,以增加迷惑性;(4)模拟用户正常操作(鼠标点击,网 络访问),以防止被电子设备识破;(5)适当增加检测时间;(6)Hook掉一些非正常操作(重启、关机);(7)针对Hook检测做相应的对抗;(8) 通过其他能够规避检测的方式配置虚拟网络环境等。In addition, in this embodiment, the protection of the virtualized environment can also be achieved in the following ways: (1) Using open-source hardware virtualization software, source code compilation to remove or modify the specific fingerprint information of the virtual machine, so that malicious software in the electronic device can be detected. Invalid; (2) Change the hardware configuration of the sandbox to make it more like a real machine (optionally, it can also return false configuration information through Hook); (3) Configure the system normally and install common software to increase confusion; (4) Simulate the normal operation of the user (mouse click, network access) to prevent it from being seen by electronic devices; (5) Appropriately increase the detection time; (6) Hook some abnormal operations (restart, shutdown); (7) For Hook (8) Configure the virtual network environment through other methods that can avoid detection.
由此可见,本系统中的第一入侵检测模块和第二入侵检测模块能够对虚 拟化环境进行隐藏,以防止被电子设备识别出蜜罐环境,从而提升系统的可 用性。It can be seen that the first intrusion detection module and the second intrusion detection module in this system can hide the virtualized environment to prevent the electronic device from identifying the honeypot environment, thereby improving the usability of the system.
另外,本系统还能够根据各个模块收集到的信息实现黑客画像功能,以 实现对攻击者的定位。相应地,该系统进一步执行以下操作:当检测到入侵 无线网络的电子设备时,记录该电子设备的设备接入信息(即上述无线接入 模块实现的功能);获取所述电子设备产生的网络流量信息,根据网络流量 信息确定电子设备的设备属性信息以及与电子设备相对应的用户属性信息; 将电子设备的设备接入信息、电子设备的设备属性信息以及与电子设备相对 应的用户属性信息进行关联分析,根据分析结果确定与电子设备相对应的攻击用户信息;其中,攻击用户信息用于定位攻击者和/或检测电子设备的位置。 其中,设备接入信息以及设备属性信息的具体内涵和获取方式均已在上文中 予以描述,此处不再赘述。与电子设备相对应的用户属性信息主要是指与攻 击者相关的个人行为信息,该部分信息既可以通过设备属性信息确定,也可 以根据上文中提到的行为特征信息确定。在本实施例中,用户属性信息可以 包括用户身份信息,例如包括:社交账号信息、攻击工具信息、远控木马的 上线地址信息、以及后门的登录密码信息。也就是说,在本实施例中,可以 将上文提到的设备属性信息中与用户行为相关的信息分离出来作为用户属性 信息。In addition, the system can also realize the hacker portrait function according to the information collected by each module, so as to realize the location of the attacker. Correspondingly, the system further performs the following operations: when detecting an electronic device that invades the wireless network, record the device access information of the electronic device (that is, the function implemented by the above-mentioned wireless access module); obtain the network generated by the electronic device Traffic information, determine the device attribute information of the electronic device and the user attribute information corresponding to the electronic device according to the network traffic information; Correlation analysis is performed, and attack user information corresponding to the electronic device is determined according to the analysis result; wherein the attack user information is used to locate the attacker and/or detect the position of the electronic device. The specific connotation and acquisition method of the device access information and the device attribute information have been described above, and will not be repeated here. The user attribute information corresponding to the electronic device mainly refers to the personal behavior information related to the attacker, and this part of the information can be determined either through the device attribute information or the behavior feature information mentioned above. In this embodiment, the user attribute information may include user identity information, for example, including: social account information, attack tool information, online address information of the remote control Trojan, and login password information of the backdoor. That is to say, in this embodiment, the information related to user behavior in the device attribute information mentioned above can be separated as user attribute information.
为了便于理解,下面以设备指纹类信息为例,列举几种常见的设备属性 信息,具体包括:IP地址、地理位置、网络身份、设备指纹、操作系统、浏 览器等。除此之外,设备属性信息还可以通过WebRTC(Web Real-Time Communication,网页实时通信)、UA(User Agent,用户代理)、绘图(Canvas)、 分辨率(包括:尺寸、颜色16/24)、插件、时区、语言(language)、GPU (Graphics Processing Unit,图形处理器)、AudioContext等辅助确定。具体 地,利用WebRTC协议能够获取内外网的IP地址,即使有VPN(Virtual Private Network,虚拟专用网络)也可以获取到。通过UA能够判断浏览器版本及操 作系统版本。另外,绘制Canvas图片时,同样的Canvas绘制代码,在不同机 器和浏览器中绘制的图片特征是相同并且独一无二的,基于这一特性,本发 明只需提取最简单的CRC(Cyclic Redundancy Code,循环冗余校验)值便可 以唯一标识和跟踪一个电子设备及其对应的用户。通过获取攻击者电子设备的分辨率作为辅助条件,能够更加准确地确定电子设备的唯一性。并且,通 过获取攻击者电子设备的插件来判断攻击者安装的软件及作为辅助条件,能 够更为准确地确定电子设备的唯一性。并且,通过获取攻击者电子设备的时 区,能够判断攻击者所属的国家或地区,并作为辅助条件来确定电子设备的 唯一性。通过获取攻击者电子设备的GPU型号,能够作为辅助条件来确定电 子设备的唯一性。另外,关于上述提到的语言(即language),并不限定于当 前浏览器所使用的语言,而是包括系统支持的所有语言,比如中文简体、中 文繁体、英语。发明人在实现本发明的过程中发现,现有技术中并没有现成 的调用接口来获取系统的语言信息,为了解决这一问题,本实施例中采取如 下方式:要求电子设备的使用者在页面中用所有的语言写两个字,如果系统 支持该语言,那么就能正常写出来;如果不支持,显示出来的就是方框,通 过这种方法即可获取系统支持的语言,进而通过系统支持的语言辅助确定电 子设备的唯一性以及电子设备使用者的身份信息。具体实施时,可以通过挂 钩函数拦截电子设备发出的预设指令,并通过挂钩函数中设置的分别通过各 种语言实现书写的操作逻辑确定系统支持的语言。由此可见,本实施例中的 设备属性信息可以包括多种内容,并且,其中的部分信息还可以用于辅助确 定用户属性信息。For ease of understanding, the following uses device fingerprint information as an example to list several common device attribute information, including: IP address, geographic location, network identity, device fingerprint, operating system, browser, etc. In addition, device attribute information can also be accessed through WebRTC (Web Real-Time Communication), UA (User Agent, User Agent), drawing (Canvas), resolution (including: size, color 16/24) , plug-in, time zone, language (language), GPU (Graphics Processing Unit, graphics processor), AudioContext and other auxiliary determination. Specifically, the IP address of the internal and external networks can be obtained by using the WebRTC protocol, even if there is a VPN (Virtual Private Network, virtual private network), it can also be obtained. UA can determine the browser version and operating system version. In addition, when drawing Canvas pictures, the same Canvas drawing code, the picture features drawn in different machines and browsers are the same and unique. Based on this feature, the present invention only needs to extract the simplest CRC (Cyclic Redundancy Code, cycle Redundancy Check) value can uniquely identify and track an electronic device and its corresponding user. By obtaining the resolution of the attacker's electronic device as an auxiliary condition, the uniqueness of the electronic device can be determined more accurately. In addition, by obtaining the plug-in of the attacker's electronic device to determine the software installed by the attacker and as an auxiliary condition, the uniqueness of the electronic device can be more accurately determined. In addition, by obtaining the time zone of the attacker's electronic device, the country or region to which the attacker belongs can be determined, and the uniqueness of the electronic device can be determined as an auxiliary condition. By obtaining the GPU model of the attacker's electronic device, the uniqueness of the electronic device can be determined as an auxiliary condition. In addition, the language (namely language) mentioned above is not limited to the language used by the current browser, but includes all languages supported by the system, such as simplified Chinese, traditional Chinese, and English. In the process of implementing the present invention, the inventor found that there is no ready-made calling interface to obtain the language information of the system in the prior art. In order to solve this problem, the following method is adopted in this embodiment: the user of the electronic device is required to Write two words in all languages. If the system supports the language, it can be written normally; if not, the box will be displayed. In this way, the language supported by the system can be obtained, and then the system supports The language aids in determining the uniqueness of an electronic device and the identity of the user of the electronic device. During specific implementation, the preset instruction sent by the electronic device can be intercepted through the hook function, and the language supported by the system can be determined through the operation logic set in the hook function to realize writing in various languages. It can be seen that the device attribute information in this embodiment may include various contents, and some of the information therein may also be used to assist in determining user attribute information.
下面介绍几种常见的用户属性信息:The following describes several common user attribute information:
首先,用户属性信息包括用户身份信息。例如,包括通过上文提到的方 式获取到的用户账号信息。其中,用户账号信息包括用户在各大网站注册的 账号及对应的密码信息。除用户账号信息外,还可以包括其他各类能够反映 用户身份的信息。First, the user attribute information includes user identity information. For example, including the user account information obtained by the above-mentioned methods. Among them, the user account information includes the account registered by the user on each major website and the corresponding password information. In addition to user account information, it can also include other types of information that can reflect the user's identity.
其次,用户属性信息还包括用户行为信息,该用户行为信息主要用于确 定攻击者的攻击工具及攻击手法。具体地,捕获攻击者使用的攻击工具及攻 击手法,提取工具中的特征,如:URL、IP、样本的MD5、远控木马的上线 地址、后门的登录密码等;通过上述特征来确定两个攻击者是否为同一个人, 并且,还能够确定攻击者的等级。例如,同一个攻击者,其每次登陆后下载 的样本是相同的,因此,样本的MD5必然也相同。并且,同一个攻击者,其远控木马的上线地址以及后门的登录密码必然也相同。相应地,通过上述信 息即可唯一地确定一个攻击者。Secondly, the user attribute information also includes user behavior information, which is mainly used to determine the attacker's attack tools and attack methods. Specifically, capture the attack tools and attack methods used by the attacker, and extract the characteristics of the tools, such as: URL, IP, MD5 of the sample, online address of the remote control Trojan, login password of the backdoor, etc.; Whether the attacker is the same person, and the level of the attacker can also be determined. For example, the same attacker downloads the same sample after each login, so the MD5 of the sample must also be the same. Moreover, for the same attacker, the online address of the remote control Trojan and the login password of the backdoor must be the same. Accordingly, an attacker can be uniquely determined through the above information.
在得到上述的设备接入信息、设备属性信息以及用户属性信息之后,将 上述信息进行关联分析,根据分析结果确定与该电子设备相对应的攻击用户 信息。所谓关联分析,是指根据设备标识将上述的各项信息关联到一起后进 行分析。由于同一个用户的设备接入信息、设备属性信息以及用户属性信息 所对应的设备标识均相同,因此,通过设备标识可以将同一个用户的各项信 息相互关联,并将关联后得到的结果作为攻击用户信息。After obtaining the above-mentioned device access information, device attribute information and user attribute information, the above-mentioned information is correlated and analyzed, and the attack user information corresponding to the electronic device is determined according to the analysis result. The so-called association analysis refers to the analysis after correlating the above items of information according to the device ID. Since the device access information, device attribute information, and device identification corresponding to the user attribute information of the same user are all the same, the device identification can be used to correlate the information of the same user with each other, and the result obtained after the association is used as Attack user information.
接下来,在根据分析结果确定与电子设备相对应的攻击用户信息之后, 进一步设置与攻击用户信息相对应的攻击用户标识,将攻击用户信息与攻击 用户标识作为一条数据记录关联存储到预设的攻击用户列表中。这里,攻击 用户标识与设备标识的区别在于:设备标识主要用于唯一地确定一个电子设 备,因此,设备标识与电子设备的硬件特征相互关联,例如,一个电子设备 的显卡、分辨率、网卡等硬件特征是不变的,因此,设备标识主要用于标识 一个电子设备本身。然而,攻击用户标识主要用于唯一地确定一个攻击者, 通常情况下,一个攻击者各次攻击时所使用的电子设备是相同的,因此,通 常情况下,设备标识与攻击用户标识的作用可相互替代。但是,不排除某些 特殊情况下,一个攻击者各次攻击时所使用的电子设备不同,此时,设备标 识与攻击用户标识的内涵和作用则截然不同。通俗的说,攻击用户标识与攻 击者的用户属性信息相互关联,例如,同一个攻击者的社交账号信息是不变 的,且同一个攻击者的攻击手法和攻击工具是固定不变的,因此,攻击用户标识主要用于标识一个攻击者本身。Next, after determining the attacking user information corresponding to the electronic device according to the analysis result, further setting the attacking user identification corresponding to the attacking user information, and storing the attacking user information and the attacking user identification as a data record in a preset association. Attacked users list. Here, the difference between the attacking user ID and the device ID is that the device ID is mainly used to uniquely identify an electronic device. Therefore, the device ID is associated with the hardware features of the electronic device, such as the graphics card, resolution, network card, etc. of an electronic device. Hardware characteristics are unchanged, therefore, device identification is mainly used to identify an electronic device itself. However, the attacking user ID is mainly used to uniquely identify an attacker. Usually, the electronic device used by an attacker for each attack is the same. Therefore, in general, the functions of the device ID and the attacking user ID can be replace each other. However, it cannot be ruled out that in some special cases, the electronic equipment used by an attacker for each attack is different. At this time, the connotation and function of the equipment identification and the attacking user identification are completely different. In layman's terms, the attacking user ID and the attacker's user attribute information are related to each other. For example, the social account information of the same attacker is unchanged, and the attacking methods and attacking tools of the same attacker are fixed. Therefore, , the attack user ID is mainly used to identify an attacker itself.
具体实施时,可以将设备接入信息以及设备属性信息作为与设备标识一 一对应的信息,将用户属性信息作为与攻击用户标识一一对应的信息。相应 地,通过本发明中的方式,不仅能够唯一地确定一个电子设备,还能够唯一 地确定一个攻击者,从而既可以实现对电子设备的定位,还可以实现对攻击 者的信息收集和查找。During specific implementation, the device access information and the device attribute information may be regarded as the information corresponding to the device identification one-to-one, and the user attribute information may be regarded as the information corresponding to the attacking user identification one-to-one. Correspondingly, through the method of the present invention, not only an electronic device but also an attacker can be uniquely determined, so that the location of the electronic device can be realized, and the information collection and search of the attacker can also be realized.
相应地,在根据分析结果确定与电子设备相对应的攻击用户信息时,进 一步查询该攻击用户列表中是否包含与分析结果相匹配的数据记录;若是, 根据分析结果更新该数据记录。具体地,分别针对攻击用户列表中的每条数 据记录,确定该数据记录中是否包含与分析结果中的信息项取值相同的信息 项;若是,判断该取值相同的信息项的名称和/或数量是否符合预设匹配规则, 若是,确定该数据记录与分析结果相匹配。通过该种方式即可通过攻击用户 列表存储各个攻击者的信息,并针对攻击者进行定位和查询,从而提升系统 的安全性。Correspondingly, when the attack user information corresponding to the electronic device is determined according to the analysis result, it is further inquired whether the attack user list contains a data record matching the analysis result; if so, the data record is updated according to the analysis result. Specifically, for each data record in the attacking user list, determine whether the data record contains an information item with the same value as the information item in the analysis result; if so, determine the name and/or name of the information item with the same value. or whether the quantity complies with the preset matching rule, and if so, determine that the data record matches the analysis result. In this way, the information of each attacker can be stored in the attack user list, and the attacker can be located and queried, thereby improving the security of the system.
综上可知,通过本发明提供的系统,能够诱使攻击者进入蜜罐,并暴露 相关信息。系统中的各个模块以逐层递进的方式收集多方面的信息,并且, 这些信息可以联动查询。该系统还支持通过短信或邮件等方式进行攻击告警。 而且,还可以通过定位攻击者位置以及制止攻击行为等方式实现应急处理。 除此之外,该系统还能够通过查看攻击日志实现溯源、取证分析等目的。To sum up, the system provided by the present invention can induce attackers to enter the honeypot and expose relevant information. Each module in the system collects various information in a layer-by-layer progressive manner, and these information can be queried in linkage. The system also supports attack alerts via SMS or email. Moreover, emergency treatment can also be achieved by locating the attacker's location and stopping the attack behavior. In addition, the system can also achieve source tracing, forensic analysis and other purposes by viewing attack logs.
另外,本实施例中的系统的第二入侵检测模块是以Windows型高交互性 蜜罐为例进行介绍的,实质上,该系统中的第二入侵检测模块还可以是Linux 型高交互性蜜罐。In addition, the second intrusion detection module of the system in this embodiment is introduced by taking a Windows type high-interaction honeypot as an example. In essence, the second intrusion detection module in the system may also be a Linux type high-interactivity honeypot. Can.
综上可知,本发明中的基于无线网络入侵的预警方法可由上述系统中的 网络传输模块实现,当然,上述系统中的其他模块(例如无线接入模块、第 一/第二入侵检测模块)中实现的功能也都可以应用于本发明中的基于无线网 络入侵的预警方法中。相应地,关于本发明中的基于无线网络入侵的预警方 法中的具体细节可参照上述系统中相应部分的描述。To sum up, it can be seen that the early warning method based on wireless network intrusion in the present invention can be realized by the network transmission module in the above-mentioned system. The realized functions can also be applied to the early warning method based on wireless network intrusion in the present invention. Correspondingly, for the specific details of the wireless network intrusion-based early warning method in the present invention, reference may be made to the description of the corresponding part in the above-mentioned system.
图4示出了本发明另一个实施例提供的一种基于无线网络入侵的预警装 置的结构示意图,如图4所示,该装置包括:Fig. 4 shows the structural representation of a kind of early warning device based on wireless network intrusion provided by another embodiment of the present invention, as shown in Fig. 4, this device comprises:
获取模块41,适于获取入侵无线网络的电子设备产生的网络流量信息;an
分析模块42,适于针对所述网络流量信息进行分析,根据分析结果确定 所述电子设备的网络访问行为;An
预警模块43,适于判断所述电子设备的网络访问行为是否符合预设的预 警规则,若是,则生成用于预警的入侵预警信号。The
可选的,所述预警规则包括多个网络安全等级的预警规则,则所述预警 模块进一步用于:Optionally, the pre-warning rules include pre-warning rules of multiple network security levels, then the pre-warning module is further used for:
确定当前的网络安全等级,选择与当前的网络安全等级相匹配的预警规 则。Determine the current network security level, and select an early warning rule that matches the current network security level.
可选的,所述预设的预警规则包括以下规则中的至少一个:Optionally, the preset early warning rules include at least one of the following rules:
当监测到通过预设扫描工具实施扫描行为时进行预警的规则;A rule for alerting when a scanning behavior is detected by a preset scanning tool;
当监测到针对无线网络内的预设设备实施试探性连接的行为时进行预警 的规则;A rule for alerting when a tentative connection to a preset device in a wireless network is detected;
当监测到针对无线网络内的预设设备连接成功的行为时进行预警的规 则。A rule for alerting when a successful connection to a preset device in the wireless network is detected.
可选的,所述获取模块具体适于:Optionally, the obtaining module is specifically adapted to:
分别获取所述电子设备入侵无线网络后针对所述无线网络中的各个预设 设备产生的点对点网络流量信息,并将所述点对点网络流量信息提供给对应 的预设设备;其中,各个预设设备以桥接方式接入所述无线网络。Respectively acquire peer-to-peer network traffic information generated for each preset device in the wireless network after the electronic device invades the wireless network, and provide the peer-to-peer network traffic information to the corresponding preset device; wherein, each preset device Access the wireless network in a bridging manner.
可选的,所述装置进一步包括:Optionally, the device further includes:
定位模块44,适于根据电子设备产生的网络流量信息,拦截所述电子设 备发送的网站访问请求,在拦截到的网站访问请求中插入用于访问预设网站 的预设访问脚本;接收与所述预设网站相对应的访问结果数据,根据所述访 问结果数据确定所述电子设备的设备属性信息;根据所述设备属性信息定位 所述电子设备。The
其中,该装置可由上述系统中的网络传输模块实现。Wherein, the device can be realized by the network transmission module in the above-mentioned system.
根据本发明一个实施例提供了一种非易失性计算机存储介质,所述计算 机存储介质存储有至少一可执行指令,该计算机可执行指令可执行上述任意 方法实施例中的基于无线网络入侵的预警方法。According to an embodiment of the present invention, a non-volatile computer storage medium is provided, and the computer storage medium stores at least one executable instruction, and the computer executable instruction can execute the wireless network intrusion-based method in any of the above method embodiments. method of early warning.
图5示出了根据本发明一个实施例提供的电子设备的结构示意图,本发 明具体实施例并不对电子设备的具体实现做限定。Fig. 5 shows a schematic structural diagram of an electronic device provided according to an embodiment of the present invention, and the specific embodiment of the present invention does not limit the specific implementation of the electronic device.
如图5所示,该电子设备可以包括:处理器(processor)502、通信接口(Communications Interface)504、存储器(memory)506、以及通信总线508。As shown in FIG. 5 , the electronic device may include: a processor (processor) 502 , a communication interface (Communications Interface) 504 , a memory (memory) 506 , and a communication bus 508 .
其中:处理器502、通信接口504、以及存储器506通过通信总线508完 成相互间的通信。Among them: the processor 502, the
通信接口504,用于与其它设备比如客户端或其它服务器等的网元通信。The
处理器502,用于执行程序510,具体可以执行上述性能测试方法实施例 中的相关步骤。The processor 502 is configured to execute the program 510, and specifically may execute the relevant steps in the above-mentioned embodiments of the performance testing method.
具体地,程序510可以包括程序代码,该程序代码包括计算机操作指令。Specifically, the program 510 may include program code including computer operation instructions.
处理器502可能是中央处理器CPU,或者是特定集成电路ASIC (ApplicationSpecific Integrated Circuit),或者是被配置成实施本发明实施例 的一个或多个集成电路。电子设备包括的一个或多个处理器,可以是同一类 型的处理器,如一个或多个CPU;也可以是不同类型的处理器,如一个或多 个CPU以及一个或多个ASIC。The processor 502 may be a central processing unit (CPU), or an application specific integrated circuit (ASIC), or one or more integrated circuits configured to implement embodiments of the present invention. The one or more processors included in the electronic device may be the same type of processors, such as one or more CPUs; or may be different types of processors, such as one or more CPUs and one or more ASICs.
存储器506,用于存放程序510。存储器506可能包含高速RAM存储器, 也可能还包括非易失性存储器(non-volatile memory),例如至少一个磁盘存 储器。The memory 506 is used to store the program 510 . Memory 506 may include high-speed RAM memory, and may also include non-volatile memory, such as at least one disk memory.
程序510具体可以用于使得处理器502执行以下操作:The program 510 can specifically be used to cause the processor 502 to perform the following operations:
获取入侵无线网络的电子设备产生的网络流量信息;Obtain network traffic information generated by electronic devices that invade the wireless network;
针对所述网络流量信息进行分析,根据分析结果确定所述电子设备的网 络访问行为;Analyze the network traffic information, and determine the network access behavior of the electronic device according to the analysis result;
判断所述电子设备的网络访问行为是否符合预设的预警规则,若是,则 生成用于预警的入侵预警信号。It is judged whether the network access behavior of the electronic device complies with the preset early warning rules, and if so, an intrusion warning signal for early warning is generated.
其中,所述预警规则包括多个网络安全等级的预警规则,则程序510具 体可以用于使得处理器502执行以下操作:确定当前的网络安全等级,选择 与当前的网络安全等级相匹配的预警规则。Wherein, the pre-warning rules include pre-warning rules of multiple network security levels, and the program 510 may specifically be used to cause the processor 502 to perform the following operations: determine the current network security level, select the pre-warning rule matching the current network security level .
其中,所述预设的预警规则包括以下规则中的至少一个:Wherein, the preset early warning rules include at least one of the following rules:
当监测到通过预设扫描工具实施扫描行为时进行预警的规则;A rule for alerting when a scanning behavior is detected by a preset scanning tool;
当监测到针对无线网络内的预设设备实施试探性连接的行为时进行预警 的规则;A rule for alerting when a tentative connection to a preset device in a wireless network is detected;
当监测到针对无线网络内的预设设备连接成功的行为时进行预警的规 则。A rule for alerting when a successful connection to a preset device in the wireless network is detected.
程序510具体可以用于使得处理器502执行以下操作:分别获取所述电 子设备入侵无线网络后针对所述无线网络中的各个预设设备产生的点对点网 络流量信息,并将所述点对点网络流量信息提供给对应的预设设备;其中, 各个预设设备以桥接方式接入所述无线网络。The program 510 may be specifically configured to cause the processor 502 to perform the following operations: respectively acquire the peer-to-peer network traffic information generated for each preset device in the wireless network after the electronic device invades the wireless network, and store the peer-to-peer network traffic information. provided to the corresponding preset device; wherein, each preset device accesses the wireless network in a bridging manner.
程序510具体可以用于使得处理器502执行以下操作:根据电子设备产 生的网络流量信息,拦截所述电子设备发送的网站访问请求,在拦截到的网 站访问请求中插入用于访问预设网站的预设访问脚本;The program 510 can specifically be used to cause the processor 502 to perform the following operations: according to the network traffic information generated by the electronic device, intercept the website access request sent by the electronic device, and insert a website access request for accessing a preset website into the intercepted website access request. Preset access scripts;
接收与所述预设网站相对应的访问结果数据,根据所述访问结果数据确 定所述电子设备的设备属性信息;Receive access result data corresponding to the preset website, and determine the device attribute information of the electronic device according to the access result data;
则所述生成用于预警的入侵预警信号的步骤之后,进一步包括:根据所 述设备属性信息定位所述电子设备。Then, after the step of generating an intrusion warning signal for early warning, the step further includes: locating the electronic device according to the device attribute information.
在预设的无线接入设备中设置网络漏洞,以供外部的电子设备接入无线 网络;Set network loopholes in the preset wireless access device for external electronic devices to access the wireless network;
其中,所述网络漏洞通过以下方式实现:开启无线网络端口、和/或弱化 无线网络密码。Wherein, the network vulnerability is realized by the following methods: opening the wireless network port, and/or weakening the wireless network password.
程序510具体可以用于使得处理器502执行以下操作:The program 510 can specifically be used to cause the processor 502 to perform the following operations:
向所述电子设备推送预设网页,获取所述电子设备针对所述预设网页产 生的访问结果,根据所述访问结果确定所述电子设备的设备接入信息。Pushing a preset web page to the electronic device, acquiring an access result generated by the electronic device for the preset web page, and determining device access information of the electronic device according to the access result.
其中,所述预设网页包括:通过社交账号登录的社交网页,则所述电子 设备的设备接入信息包括:根据针对社交网页产生的访问结果确定的社交账 号信息。Wherein, the preset webpage includes: a social webpage logged in through a social account, and the device access information of the electronic device includes: social account information determined according to an access result generated for the social webpage.
其中,所述设备接入信息包括以下中的至少一个:设备名称、IP地址、 MAC地址、浏览器版本、操作系统版本、设备屏幕分辨率、以及浏览器插件 信息。Wherein, the device access information includes at least one of the following: device name, IP address, MAC address, browser version, operating system version, device screen resolution, and browser plug-in information.
在此提供的算法和显示不与任何特定计算机、虚拟系统或者其它设备固 有相关。各种通用系统也可以与基于在此的示教一起使用。根据上面的描述, 构造这类系统所要求的结构是显而易见的。此外,本发明也不针对任何特定 编程语言。应当明白,可以利用各种编程语言实现在此描述的本发明的内容, 并且上面对特定语言所做的描述是为了披露本发明的最佳实施方式。The algorithms and displays provided herein are not inherently related to any particular computer, virtual system, or other device. Various general-purpose systems can also be used with teaching based on this. The structure required to construct such a system is apparent from the above description. Furthermore, the present invention is not directed to any particular programming language. It should be understood that various programming languages can be used to implement the inventions described herein, and that the descriptions of specific languages above are intended to disclose the best mode for carrying out the invention.
在此处所提供的说明书中,说明了大量具体细节。然而,能够理解,本 发明的实施例可以在没有这些具体细节的情况下实践。在一些实例中,并未 详细示出公知的方法、结构和技术,以便不模糊对本说明书的理解。In the description provided herein, numerous specific details are set forth. It will be understood, however, that embodiments of the invention may be practiced without these specific details. In some instances, well-known methods, structures and techniques have not been shown in detail in order not to obscure an understanding of this description.
类似地,应当理解,为了精简本公开并帮助理解各个发明方面中的一个 或多个,在上面对本发明的示例性实施例的描述中,本发明的各个特征有时 被一起分组到单个实施例、图、或者对其的描述中。然而,并不应将该公开 的方法解释成反映如下意图:即所要求保护的本发明要求比在每个权利要求 中所明确记载的特征更多的特征。更确切地说,如下面的权利要求书所反映 的那样,发明方面在于少于前面公开的单个实施例的所有特征。因此,遵循 具体实施方式的权利要求书由此明确地并入该具体实施方式,其中每个权利要求本身都作为本发明的单独实施例。Similarly, it is to be understood that in the above description of exemplary embodiments of the invention, various features of the invention are sometimes grouped together into a single embodiment, figure, or its description. However, this method of disclosure should not be construed to reflect an intention that the claimed invention requires more features than are expressly recited in each claim. Rather, as the following claims reflect, inventive aspects lie in less than all features of a single foregoing disclosed embodiment. Thus, the claims following the Detailed Description are hereby expressly incorporated into this Detailed Description, with each claim standing on its own as a separate embodiment of this invention.
本领域那些技术人员可以理解,可以对实施例中的设备中的模块进行自 适应性地改变并且把它们设置在与该实施例不同的一个或多个设备中。可以 把实施例中的模块或单元或组件组合成一个模块或单元或组件,以及此外可 以把它们分成多个子模块或子单元或子组件。除了这样的特征和/或过程或者 单元中的至少一些是相互排斥之外,可以采用任何组合对本说明书(包括伴 随的权利要求、摘要和附图)中公开的所有特征以及如此公开的任何方法或 者设备的所有过程或单元进行组合。除非另外明确陈述,本说明书(包括伴 随的权利要求、摘要和附图)中公开的每个特征可以由提供相同、等同或相 似目的的替代特征来代替。Those skilled in the art will appreciate that the modules in the device in an embodiment can be adaptively changed and placed in one or more devices different from the embodiment. The modules or units or components in the embodiments may be combined into one module or unit or component, and further they may be divided into multiple sub-modules or sub-units or sub-assemblies. All features disclosed in this specification (including accompanying claims, abstract and drawings) and any method so disclosed may be employed in any combination, unless at least some of such features and/or procedures or elements are mutually exclusive. All processes or units of equipment are combined. Each feature disclosed in this specification (including the accompanying claims, abstract and drawings) may be replaced by alternative features serving the same, equivalent or similar purpose, unless expressly stated otherwise.
此外,本领域的技术人员能够理解,尽管在此的一些实施例包括其它实 施例中所包括的某些特征而不是其它特征,但是不同实施例的特征的组合意 味着处于本发明的范围之内并且形成不同的实施例。例如,在下面的权利要 求书中,所要求保护的实施例的任意之一都可以以任意的组合方式来使用。Furthermore, it will be understood by those skilled in the art that although some of the embodiments herein include certain features, but not others, included in other embodiments, that combinations of features of the different embodiments are intended to be within the scope of the present invention And form different embodiments. For example, in the following claims, any of the claimed embodiments may be used in any combination.
本发明的各个部件实施例可以以硬件实现,或者以在一个或者多个处理 器上运行的软件模块实现,或者以它们的组合实现。本领域的技术人员应当理解,可以在实践中使用微处理器或者数字信号处理器(DSP)来实现根据本发明实施例的装置中的一些或者全部部件的一些或者全部功能。本发明还可以实现为用于执行这里所描述的方法的一部分或者全部的设备或者装置程序 (例如,计算机程序和计算机程序产品)。这样的实现本发明的程序可以存储在计算机可读介质上,或者可以具有一个或者多个信号的形式。这样的信号可以从因特网网站上下载得到,或者在载体信号上提供,或者以任何其他形式提供。Various component embodiments of the present invention may be implemented in hardware, or in software modules running on one or more processors, or in a combination thereof. Those skilled in the art should understand that a microprocessor or a digital signal processor (DSP) may be used in practice to implement some or all of the functions of some or all of the components in the apparatus according to the embodiments of the present invention. The present invention can also be implemented as apparatus or apparatus programs (eg, computer programs and computer program products) for performing part or all of the methods described herein. Such a program implementing the present invention may be stored on a computer-readable medium, or may be in the form of one or more signals. Such signals may be downloaded from Internet sites, or provided on carrier signals, or in any other form.
应该注意的是上述实施例对本发明进行说明而不是对本发明进行限制,并 且本领域技术人员在不脱离所附权利要求的范围的情况下可设计出替换实施 例。在权利要求中,不应将位于括号之间的任何参考符号构造成对权利要求 的限制。单词“包含”不排除存在未列在权利要求中的元件或步骤。位于元件之 前的单词“一”或“一个”不排除存在多个这样的元件。本发明可以借助于包括有 若干不同元件的硬件以及借助于适当编程的计算机来实现。在列举了若干装 置的单元权利要求中,这些装置中的若干个可以是通过同一个硬件项来具体 体现。单词第一、第二、以及第三等的使用不表示任何顺序。可将这些单词解释为名称。It should be noted that the above-described embodiments illustrate rather than limit the invention, and that alternative embodiments may be devised by those skilled in the art without departing from the scope of the appended claims. In the claims, any reference signs placed between parentheses shall not be construed as limiting the claim. The word "comprising" does not exclude the presence of elements or steps not listed in a claim. The word "a" or "an" preceding an element does not exclude the presence of a plurality of such elements. The invention can be implemented by means of hardware comprising several different elements and by means of a suitably programmed computer. In a unit claim enumerating several means, several of these means can be embodied by one and the same item of hardware. The use of the words first, second, and third, etc. do not denote any order. These words can be interpreted as names.
Claims (10)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201710944307.0ACN107465702B (en) | 2017-09-30 | 2017-09-30 | Method and device for early warning based on wireless network intrusion |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201710944307.0ACN107465702B (en) | 2017-09-30 | 2017-09-30 | Method and device for early warning based on wireless network intrusion |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN107465702A CN107465702A (en) | 2017-12-12 |
| CN107465702Btrue CN107465702B (en) | 2020-11-13 |
Family
ID=60553298
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN201710944307.0AActiveCN107465702B (en) | 2017-09-30 | 2017-09-30 | Method and device for early warning based on wireless network intrusion |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN107465702B (en) |
Families Citing this family (8)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN108259472A (en)* | 2017-12-28 | 2018-07-06 | 广州锦行网络科技有限公司 | Dynamic joint defence mechanism based on attack analysis realizes system and method |
| CN110351237B (en)* | 2019-05-23 | 2020-07-10 | 中国科学院信息工程研究所 | Honeypot method and device for numerical control machine tool |
| CN111818070B (en)* | 2020-07-14 | 2021-03-02 | 广州锦行网络科技有限公司 | Screen recording method under windows system |
| CN114465789A (en)* | 2022-01-21 | 2022-05-10 | 成都全景智能科技有限公司 | Analysis method, device and equipment for network rubbing equipment and storage medium |
| CN114844683A (en)* | 2022-04-09 | 2022-08-02 | 国网山东省电力公司信息通信公司 | Internet of things scanning control method and device based on authorization mechanism |
| US20230421562A1 (en)* | 2022-05-19 | 2023-12-28 | Capital One Services, Llc | Method and system for protection of cloud-based infrastructure |
| CN115277256B (en)* | 2022-09-27 | 2022-12-16 | 中国民用航空局空中交通管理局航空气象中心 | Early warning method and system for data intranet and extranet gateway transmission |
| CN119011160A (en)* | 2023-05-16 | 2024-11-22 | 华为技术有限公司 | Threat event tracing method and related equipment |
Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN104065539A (en)* | 2014-07-09 | 2014-09-24 | 武汉安问科技发展有限责任公司 | Method for monitoring unauthorized network equipment based on application behaviors |
| CN104468631A (en)* | 2014-12-31 | 2015-03-25 | 国家电网公司 | Network intrusion identification method based on anomaly flow and black-white list library of IP terminal |
| CN104486765A (en)* | 2014-12-22 | 2015-04-01 | 上海斐讯数据通信技术有限公司 | Wireless intrusion detecting system and detecting method |
| EP3110104A1 (en)* | 2015-06-26 | 2016-12-28 | Palantir Technologies, Inc. | Improved network anomaly detection |
Family Cites Families (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US9673920B2 (en)* | 2012-12-18 | 2017-06-06 | Department 13, LLC | Intrusion detection and radio fingerprint tracking |
- 2017
- 2017-09-30CNCN201710944307.0Apatent/CN107465702B/enactiveActive
Patent Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN104065539A (en)* | 2014-07-09 | 2014-09-24 | 武汉安问科技发展有限责任公司 | Method for monitoring unauthorized network equipment based on application behaviors |
| CN104486765A (en)* | 2014-12-22 | 2015-04-01 | 上海斐讯数据通信技术有限公司 | Wireless intrusion detecting system and detecting method |
| CN104468631A (en)* | 2014-12-31 | 2015-03-25 | 国家电网公司 | Network intrusion identification method based on anomaly flow and black-white list library of IP terminal |
| EP3110104A1 (en)* | 2015-06-26 | 2016-12-28 | Palantir Technologies, Inc. | Improved network anomaly detection |
Also Published As
| Publication number | Publication date |
|---|---|
| CN107465702A (en) | 2017-12-12 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN107465702B (en) | Method and device for early warning based on wireless network intrusion | |
| CN107612924B (en) | Attacker positioning method and device based on wireless network intrusion | |
| US11562068B2 (en) | Performing threat detection by synergistically combining results of static file analysis and behavior analysis | |
| US10587647B1 (en) | Technique for malware detection capability comparison of network security devices | |
| US10454950B1 (en) | Centralized aggregation technique for detecting lateral movement of stealthy cyber-attacks | |
| JP6441957B2 (en) | Systems, devices, and methods that automatically validate exploits on suspicious objects and highlight display information associated with the proven exploits | |
| US9973531B1 (en) | Shellcode detection | |
| CN107579997A (en) | Wireless Network Intrusion Detection System | |
| CN106557701B (en) | Virtual machine-based kernel vulnerability detection method and device | |
| US11861008B2 (en) | Using browser context in evasive web-based malware detection | |
| JP2020095753A (en) | Automated runtime detection of malware | |
| CN105512559B (en) | It is a kind of for providing the method and apparatus of accession page | |
| CN107566401B (en) | Protection method and device for virtualized environment | |
| CN106778243B (en) | Kernel vulnerability detection file protection method and device based on virtual machine | |
| CN105592017B (en) | The defence method and system of cross-site scripting attack | |
| CN103701816B (en) | Perform the scan method and scanning means of the server of Denial of Service attack | |
| CN104468632A (en) | Loophole attack prevention method, device and system | |
| US11909761B2 (en) | Mitigating malware impact by utilizing sandbox insights | |
| CN106778244B (en) | Virtual machine-based kernel vulnerability detection process protection method and device | |
| CN107566420B (en) | Method and equipment for positioning host infected by malicious code | |
| WO2018099206A1 (en) | Apt detection method, system, and device | |
| CN106778242B (en) | Kernel vulnerability detection method and device based on virtual machine | |
| CN114531258A (en) | Network attack behavior processing method and device, storage medium and electronic equipment | |
| CN110348210B (en) | Safety protection method and device | |
| CN107509200A (en) | Equipment localization method and device based on wireless network invasion |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |