CN107040517B - Cognitive intrusion detection method oriented to cloud computing environment - Google Patents
Cognitive intrusion detection method oriented to cloud computing environmentDownload PDFInfo
- Publication number
- CN107040517B CN107040517BCN201710096368.6ACN201710096368ACN107040517BCN 107040517 BCN107040517 BCN 107040517BCN 201710096368 ACN201710096368 ACN 201710096368ACN 107040517 BCN107040517 BCN 107040517B
- Authority
- CN
- China
- Prior art keywords
- cloud
- intrusion
- cognitive
- unit
- data
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Active
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H04L63/1416—Event detection, e.g. attack signature detection
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H04L63/1425—Traffic logging, e.g. anomaly detection
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1441—Countermeasures against malicious traffic
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/20—Network architectures or network communication protocols for network security for managing network security; network security policies in general
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本发明属于云计算领域,具体的是一种面向云计算环境的认知入侵检测方法。The invention belongs to the field of cloud computing, in particular to a cognitive intrusion detection method oriented to a cloud computing environment.
背景技术Background technique
云计算已经成为当前IT界关注的热点话题,但云计算的发展也面临许多关键性问题,而安全问题首当其冲,并且随着云计算的不断普及,其重要性呈现逐步上升趋势,已成为制约云计算发展的核心因素。云安全的挑战体现在3个方面:(1)数据安全,包含数据加密解密、访问控制、传输安全等;(2)服务安全,包含服务器安全、安全单点登录、身份认证、信任模型等;(3)安全监控体系,用来防御和阻止恶意入侵行为,保障所有用户的数据与隐私安全,是云安全至关重要的一环。Cloud computing has become a hot topic in the current IT industry, but the development of cloud computing also faces many key issues, and security issues bear the brunt. A central factor in the development of computing. The challenges of cloud security are reflected in three aspects: (1) data security, including data encryption and decryption, access control, transmission security, etc.; (2) service security, including server security, secure single sign-on, identity authentication, trust model, etc.; (3) The security monitoring system is used to prevent and prevent malicious intrusions and ensure the data and privacy security of all users. It is a crucial part of cloud security.
传统的被动式防御方法不能及时判断并阻止网络攻击,缺乏识别已知或未知的安全攻击的认知能力,不具备实时性、智能性已经不能满足云计算的环境。因此,云计算环境下需要更加主动的,先验的认知入侵检测方法,以达到快速识别、预警与防护云计算环境下的安全攻击。Traditional passive defense methods cannot judge and prevent network attacks in a timely manner, lack the cognitive ability to identify known or unknown security attacks, and lack real-time and intelligence, which can no longer meet the cloud computing environment. Therefore, more active and a priori cognitive intrusion detection methods are needed in the cloud computing environment to achieve rapid identification, early warning and protection of security attacks in the cloud computing environment.
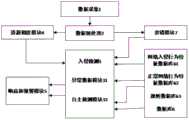
现有技术中文献一(申请号:201510870283.X)提供了一种基于云计算的入侵检测方法,将入侵检测功能从传统的主机端转移到云端,在云端以服务形式提供。其核心入侵检测分析服务置于云端,通过云服务商专业的网络安全团队对其进行更新维护。简化了主机端的复杂性,降低了维护成本。其主要过程如图1所示。该文献是针对互联网入侵检测的一个基础性专利,对于入侵检测系统而言,基于云计算环境的入侵检测系统使系统拥有了云数据库的数据集中和共享的优点。该技术的不足是:(1)未对入侵检测引擎,入侵检测比对规则库,智能异常检测作出具体阐述;(2)对于比较得到的可能的未知类入侵行为没有识别能力,没有给出相应的解决方案,简单作为新的入侵行为,不具备对未知攻击的认知能力。Document 1 (application number: 201510870283.X) in the prior art provides an intrusion detection method based on cloud computing, which transfers the intrusion detection function from the traditional host to the cloud, and provides it as a service in the cloud. Its core intrusion detection and analysis services are placed in the cloud, and are updated and maintained by the cloud service provider's professional network security team. The complexity of the host side is simplified and maintenance costs are reduced. Its main process is shown in Figure 1. This document is a basic patent for Internet intrusion detection. For the intrusion detection system, the intrusion detection system based on the cloud computing environment enables the system to have the advantages of data centralization and sharing of the cloud database. The shortcomings of this technology are: (1) The intrusion detection engine, the intrusion detection comparison rule base, and the intelligent anomaly detection are not elaborated; (2) There is no ability to identify the possible unknown intrusion behaviors obtained by comparison, and no corresponding intrusion behaviors are given. The solution, simply as a new intrusion behavior, does not have the cognitive ability to the unknown attack.
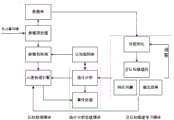
文献二(申请号:201610049716.X)提供了一种云计算环境中的自主分析入侵检测方法,利用改进的BP神经网络训练入侵检测器实时对经过预处理的网络流量异常的数据包进行检测,随后对异常数据进行识别,将得到的未知入侵行为进行特征提取以下次识别出新类型的入侵行为,提出了自主分析与检测的思路,扩展率高。其主要过程如图2所示。该文献是针对互联网入侵检测的一个较为前沿的专利,对于入侵检测系统而言,基于云计算环境且能检测已知和未知类型入侵行为并及时反馈,补充云数据库,使系统检测和防御功能得到改善。该技术的不足是:未知入侵行为的特征值提取方法还有很大改进空间,来提高系统的速度和安全性。Document 2 (application number: 201610049716.X) provides an autonomous analysis intrusion detection method in a cloud computing environment, using an improved BP neural network to train an intrusion detector to detect in real time the abnormal data packets of the preprocessed network traffic, Then, the abnormal data is identified, and the unknown intrusion behaviors obtained are extracted by feature extraction to identify new types of intrusion behaviors. The idea of autonomous analysis and detection is proposed, and the expansion rate is high. Its main process is shown in Figure 2. This document is a relatively cutting-edge patent for Internet intrusion detection. For the intrusion detection system, it is based on the cloud computing environment and can detect known and unknown types of intrusion behaviors and provide timely feedback to supplement the cloud database, so that the system detection and defense functions can be obtained. improve. The disadvantage of this technology is that there is still a lot of room for improvement in the feature value extraction method of unknown intrusion behavior to improve the speed and security of the system.
发明内容SUMMARY OF THE INVENTION
针对传统入侵检测系统(Intrusion Detection System)模型的被动式防御策略不能及时判断并阻止已知或未知的安全攻击,系统的危险系数较大等问题,提出了一种面向云计算的具有认知能力的入侵检测系统,具体方案如下:一种面向云计算环境的认知入侵检测方法,包括如下步骤:Aiming at the problems that the passive defense strategy of the traditional Intrusion Detection System (Intrusion Detection System) model cannot judge and prevent known or unknown security attacks in time, and the risk factor of the system is relatively large, a cloud computing-oriented cognitive system is proposed. An intrusion detection system, the specific scheme is as follows: A cognitive intrusion detection method oriented to a cloud computing environment, comprising the following steps:
步骤1,云计算环境中数据预处理单元接收到流量异常的数据包,对数据包中的数据进行规则化预处理,从而获取包含有特征向量的数据包文件,并把预处理后的数据包分别发到数据库和数据包检测单元中;Step 1: The data preprocessing unit in the cloud computing environment receives the data packets with abnormal traffic, and preprocesses the data in the data packets in a regularized manner, thereby obtaining the data packet files containing the feature vectors, and processing the preprocessed data packets. They are sent to the database and the packet detection unit respectively;
步骤2,所述数据库接收并存储带有特征向量数据的数据包文件,并根据存入的数据包建立日志记录;Step 2, the database receives and stores the packet file with feature vector data, and establishes a log record according to the stored packet;
步骤3,建立认知规则库,认知规则库中包含有已知入侵行为特征数据;Step 3, establish a cognitive rule base, and the cognitive rule base contains known intrusion behavior characteristic data;
步骤3,数据包检测单元根据已经建立起来的认知规则库中的信息进行规则匹配,若发现符合的匹配规则,则向入侵检测引擎单元报警,入侵检测引擎单元根据收到的报警信息向事件处理单元发送指令,事件处理单元收到指令后进行发出警报以及切断网络;Step 3, the data packet detection unit performs rule matching according to the information in the established cognitive rule base, and if a matching rule is found, it will alarm the intrusion detection engine unit, and the intrusion detection engine unit will report to the event according to the received alarm information. The processing unit sends an instruction, and the event processing unit issues an alarm and cuts off the network after receiving the instruction;
步骤4,如果数据包检测单元没有发现符合的匹配规则,则表示无法识别该数据包中的攻击种类,则由数据库将该数据包的信息传给云推理学习模块做入侵可能性进行评估;Step 4, if the data packet detection unit does not find a matching matching rule, it means that the attack type in the data packet cannot be identified, and the database transmits the information of the data packet to the cloud reasoning learning module for evaluation of the possibility of intrusion;
步骤5,建立云规则,在无网络连接时,云认知推理机以数据库中存储的特征向量数据为训练样本建立起云规则数据库;Step 5, establishing cloud rules, when there is no network connection, the cloud cognitive reasoning engine uses the feature vector data stored in the database as training samples to establish a cloud rules database;
步骤6,判断无法识别的攻击种类,网络连接时,云认知推理机接收无法识别攻击种类的数据包的特征向量数据,云认知推理机采用基于遗传算法的特征向量提取算法对征向量数据进行优化选择获得最优选的入侵特征向量,该入侵特征向量和建立的运管站数据库比对,激活多条定性云规则,通过云认知推理机进行不确定性推理,确定入侵种类,并把结果发送至入侵检测引擎单元;Step 6: Determine the unidentifiable attack type. When the network is connected, the cloud cognitive inference engine receives the feature vector data of the data packets that cannot identify the attack type. The cloud cognitive inference engine uses the genetic algorithm-based feature vector extraction algorithm to analyze the feature vector data Perform optimization selection to obtain the most optimal intrusion feature vector, compare the intrusion feature vector with the established operation and management station database, activate multiple qualitative cloud rules, conduct uncertainty inference through the cloud cognitive inference engine, determine the intrusion type, and determine the type of intrusion. The result is sent to the intrusion detection engine unit;
步骤7,所述入侵特征向量发送至原云规则化数据库中修正、更新成为型的云规则化数据库。Step 7, the intrusion feature vector is sent to the modified and updated cloud regularization database in the original cloud regularization database.
步骤8,所述入侵特征向量发送至统计分析单元中,统计分析单元根据入侵特征向量的日志记录判断是否构成网络入侵,把判断的结果发至入侵检测引擎单元和事件处理单元,同时把该入侵特征向量的数据信息发送至认知规则库中进行更新;Step 8, the intrusion feature vector is sent to the statistical analysis unit, the statistical analysis unit judges whether it constitutes a network intrusion according to the log record of the intrusion feature vector, and sends the judgment result to the intrusion detection engine unit and the event processing unit, and at the same time, the intrusion is sent to the intrusion detection engine unit and the event processing unit. The data information of the feature vector is sent to the cognitive rule base for updating;
步骤9,所述入侵检测引擎单元接收来自云认知推理机的推理结果和来自统计分析单元的判断结果,向事件处理单元发送指令;Step 9, the intrusion detection engine unit receives the inference result from the cloud cognitive inference engine and the judgment result from the statistical analysis unit, and sends an instruction to the event processing unit;
步骤10,所述事件处理单元收到来自入侵检测引擎单元和统计分析单元的指令后进行发出警报以及切断网络。Step 10, the event processing unit issues an alarm and disconnects the network after receiving the instructions from the intrusion detection engine unit and the statistical analysis unit.
进一步所述步骤6中的基于遗传算法的特征向量提取算法的具体步骤如下:The specific steps of the genetic algorithm-based feature vector extraction algorithm in step 6 are as follows:
1)设定进化代数g=0,生成包含n个个体的初始化群体P(g);1) Set the evolutionary algebra g=0, and generate an initialization population P(g) containing n individuals;
2)在该群体中对每个个体估值,计算各自适应度f(x);2) Evaluate each individual in the group, and calculate each adaptive degree f(x);
3)根据个体适应度f(x),从P(g)中选择两个个体作为父代(适应度值越大,选中的机会越大),根据交叉概率,让选出的两个个体进行交叉产生新的后代(如果交叉概率为0,即不进行交叉,则后代就是父代的完全复制),再根据变异概率,新生后代在各自基因座产生变异;重复上述步骤,产生新个体,将最后生成的个体形成新的群体P(g+1);3) According to the individual fitness f(x), select two individuals from P(g) as the parent (the greater the fitness value, the greater the chance of selection), and according to the crossover probability, let the two selected individuals carry out Crossover produces new offspring (if the crossover probability is 0, that is, no crossover is performed, the offspring is a complete copy of the parent), and then according to the mutation probability, the new offspring mutate at their respective loci; repeat the above steps to generate new individuals, The last generated individuals form a new group P(g+1);
4)将新产生的群体P(g+1)作为后续进化操作所需的群体,令进化代数g=g+1;4) Take the newly generated population P(g+1) as the population required for subsequent evolution operations, and let the evolutionary algebra g=g+1;
5)若终止条件满足,则算法结束,返回在当前群体中最好的个体,即最优解5) If the termination condition is satisfied, the algorithm ends and returns the best individual in the current group, that is, the optimal solution
6)若终止条件不满足,则跳至步骤2)继续该遗传算法。6) If the termination condition is not satisfied, skip to step 2) to continue the genetic algorithm.
进一步所述步骤6中所述的不确定性推理具体步骤如下:The specific steps of the uncertainty reasoning described in step 6 are as follows:
Step1,经过数据预处理后的一组未知入侵特征向量(X1,X2…Xn),每个Xi根据3En原则:|Ex-Xi|<3En激活规则;Step1, a set of unknown intrusion feature vectors (X1 , X2 ... Xn ) after data preprocessing, each Xi according to the 3En principle: |Ex-Xi |<3En activation rule;
Step2,每条被激活规则对应正向云发生器推理输出云滴(drop xi,yi);Step2, each activated rule corresponds to the forward cloud generator inference output cloud drop (drop xi , yi );
Step3,逆向云发生器在云滴drop(x1,y1),…(xn,yn)的基础上得到虚拟云的数值特征:Exij,Enij,Heij;Step3, the reverse cloud generator obtains the numerical features of the virtual cloud on the basis of cloud drop drop(x1 , y1 ),...(xn , yn ): Exij , Enij ,He ij ;
Step4,再将xi代入虚拟云中得到它的确定度;Step4, then substitutexi into the virtual cloud to get its certainty;
Step5,对每个xi重复Step2-5过程,分别得到对应的确定度;Step5, repeat the Step2-5 process for eachxi to obtain the corresponding degree of certainty;
Step6,依据最大确定度原则确定入侵类型。Step 6: Determine the intrusion type according to the principle of maximum certainty.
更进一步所述步骤8中统计分析处理单元通过在任意给定的时刻,对n个变量值进行测量,推理判断系统是否有入侵发生,每个Ni(i=1,2,···,n)变量表示系统不同方面的特征,包含SYN数据包数目、用户登录失败次数、CPU使用率及网络流量等,Mi(i=1,2,···,n)是正常情况下该数据的期望值预测,在t时刻定义的检测函数为:Furthermore, in step 8, the statistical analysis and processing unit measures the n variable values at any given moment, and inferentially judges whether there is an intrusion in the system, each Ni(i=1,2,...,n ) variables represent the characteristics of different aspects of the system, including the number of SYN packets, the number of user login failures, CPU usage and network traffic, etc. Mi (i=1,2,...,n) is the expected value of the data under normal circumstances Prediction, the detection function defined at time t is:
其中,λi>0体现了重要程度的权值,即敏感程度,F(t)越小,通信过程越接近正常情况,当F(t)超过预先设定的阀值后,就认为网络入侵发生了。Among them, λi > 0 reflects the weight of the importance degree, that is, the degree of sensitivity. The smaller F(t) is, the closer the communication process is to the normal situation. When F(t) exceeds the preset threshold, it is considered that network intrusion happened.
和现有技术相比较本发明中云认知推理学习模块采用遗传算法对特征向量进行优化,使所需的训练时间和监测时间比其他方法短,其次,实时在线的检测能力较强,最后,在云计算的环境中充分利用云计算进行大规模并行计算和大数据量处理的能力,使运算能力大大加强,使系统更加安全高效。Compared with the prior art, the cloud cognitive reasoning learning module of the present invention uses genetic algorithm to optimize the feature vector, so that the required training time and monitoring time are shorter than other methods, secondly, the real-time online detection ability is stronger, and finally, In the cloud computing environment, the ability of cloud computing to perform large-scale parallel computing and large-scale data processing is fully utilized, which greatly enhances the computing power and makes the system more secure and efficient.
附图说明Description of drawings
图1为文献一的基于云计算的入侵检测方法流程图;Fig. 1 is the flow chart of the intrusion detection method based on cloud computing in Document 1;
图2为文献二云计算环境中的自主分析入侵检测方法流程图;Fig. 2 is the flow chart of the intrusion detection method of autonomous analysis in the cloud computing environment of document 2;
图3为面向云计算的认知入侵检测方法流程图;Figure 3 is a flowchart of a cloud computing-oriented cognitive intrusion detection method;
图4为基于遗传算法获取特征向量提取的算法流程框图;Fig. 4 is the algorithm flow diagram that obtains feature vector extraction based on genetic algorithm;
图5云认知推理机的具体推理算法流程框图。Figure 5 is a block diagram of the specific reasoning algorithm flow chart of the cloud cognitive reasoning engine.
具体实施方式Detailed ways
实施例1Example 1
如图1所示,所述一种面向云计算的具有认知能力的入侵检测系统,包括认知检测模块:数据预处理负责收集网络中的数据流,生成一定格式的数据流文件。数据包检测对经过预处理的数据流进行数据包检测,根据已经建立起来的认知规则库,判断该数据流是否为已知的攻击形式,对已知的攻击建立符合一定规则的攻击签名,包含处理方式、传输层协议类型、应用层协议类型、端口号、IP地址范围、备注信息等。As shown in Figure 1, the cloud computing-oriented intrusion detection system with cognitive capability includes a cognitive detection module: data preprocessing is responsible for collecting data streams in the network and generating data stream files in a certain format. Packet inspection is to perform packet inspection on the preprocessed data stream, and according to the established cognitive rule base, determine whether the data stream is a known attack form, and establish an attack signature that conforms to certain rules for the known attack. Including processing method, transport layer protocol type, application layer protocol type, port number, IP address range, remarks, etc.
云认知推理学习模块:云推理学习模块是对入侵可能性进行评估。推理机的输入分为两部分:一部分入侵检测时(在线判决),采集器将采集到的网络特征向量提供给云认知推理机进行分析和推理。而网络连接时采集器采集的特征向量很多,为了快速云计算环境下海量的连接数据,采用遗传算法对特征向量进行优化选择,根据高检出率低误报率的适应度值,选出最优的特征个体;另一个是样本训练时(离线学习),采集器将预处理后的信息存储到数据库中为云认知推理机提供信息,进而采用云计算对入侵可能性进行评估。Cloud cognitive reasoning learning module: The cloud reasoning learning module is to evaluate the possibility of intrusion. The input of the inference engine is divided into two parts: one part of intrusion detection (online judgment), the collector provides the collected network feature vector to the cloud cognitive inference engine for analysis and reasoning. However, there are many eigenvectors collected by the collector when the network is connected. In order to quickly generate massive connection data in the cloud computing environment, the genetic algorithm is used to optimize the selection of eigenvectors. According to the fitness value of high detection rate and low false alarm rate, the most The other is during sample training (offline learning), the collector stores the preprocessed information in the database to provide information for the cloud cognitive inference engine, and then uses cloud computing to evaluate the possibility of intrusion.
统计分析处理模块:针对虚拟组织的日志记录,用于实时分析,发现异常事件。入侵检测引擎综合各个系统的报警信息,分析后向事件处理模块下达指令,完成报警、切断连接等工作。Statistical analysis and processing module: log records for virtual organizations for real-time analysis and detection of abnormal events. The intrusion detection engine integrates the alarm information of each system, and after analysis, issues instructions to the event processing module to complete the alarm, disconnection and other work.
所述认知检测模块中包括数据预处理单元、数据包检测单元、入侵检测引擎单元、数据库;云认知推理学习模块中包含有云认知推理机和云规则化单元;统计分析处理模块中包括统计分析单元和事件处理单元。The cognitive detection module includes a data preprocessing unit, a data packet detection unit, an intrusion detection engine unit, and a database; the cloud cognitive reasoning learning module includes a cloud cognitive reasoning machine and a cloud regularization unit; the statistical analysis processing module Including statistical analysis unit and event processing unit.
所述设计预处理单元分别与数据包检测单元和数据库连接,数据包检测单元与入侵检测引擎单元连接,入侵检测引擎单元与事件处理单元连接;所述数据库与云规则化单元连接,云规则化单元与云认知推理机相互连接,云认知推理机分别与云规则化单元、入侵检测引擎单元和统计分析单元连接,所述统计分析单元分别与认知规则库、事件处理单元和入侵检测引擎单元连接,所述认知认知规则库与数据包检测单元连接。The design preprocessing unit is respectively connected with the data packet detection unit and the database, the data packet detection unit is connected with the intrusion detection engine unit, and the intrusion detection engine unit is connected with the event processing unit; the database is connected with the cloud regularization unit, and the cloud regularization The unit and the cloud cognitive reasoning machine are connected to each other, and the cloud cognitive reasoning machine is respectively connected with the cloud regularization unit, the intrusion detection engine unit and the statistical analysis unit, and the statistical analysis unit is respectively connected with the cognitive rule base, the event processing unit and the intrusion detection unit. The engine unit is connected, and the cognitive cognitive rule base is connected with the data packet detection unit.
如图1、图2和图3所示,基于上述系统的一种面向云计算环境的认知入侵检测方法,包括以下步骤:As shown in Figure 1, Figure 2 and Figure 3, a cloud computing environment-oriented cognitive intrusion detection method based on the above system includes the following steps:
步骤1,云计算环境中数据预处理单元接收到流量异常的数据包,对数据包中的数据进行规则化预处理,从而获取包含有特征向量的数据包文件,并把预处理后的数据包分别发到数据库和数据包检测单元中;Step 1: The data preprocessing unit in the cloud computing environment receives the data packets with abnormal traffic, and preprocesses the data in the data packets in a regularized manner, thereby obtaining the data packet files containing the feature vectors, and processing the preprocessed data packets. They are sent to the database and the packet detection unit respectively;
步骤2,所述数据库接收并存储带有特征向量数据的数据包文件,并根据存入的数据包建立日志记录;Step 2, the database receives and stores the packet file with feature vector data, and establishes a log record according to the stored packet;
步骤3,建立认知规则库,认知规则库中包含有已知入侵行为特征数据;Step 3, establish a cognitive rule base, and the cognitive rule base contains known intrusion behavior characteristic data;
步骤3,数据包检测单元根据已经建立起来的认知规则库中的信息进行规则匹配,若发现符合的匹配规则,则向入侵检测引擎单元报警,入侵检测引擎单元根据收到的报警信息向事件处理单元发送指令,事件处理单元收到指令后进行发出警报以及切断网络;Step 3, the data packet detection unit performs rule matching according to the information in the established cognitive rule base, and if a matching rule is found, it will alarm the intrusion detection engine unit, and the intrusion detection engine unit will report to the event according to the received alarm information. The processing unit sends an instruction, and the event processing unit issues an alarm and cuts off the network after receiving the instruction;
步骤4,如果数据包检测单元没有发现符合的匹配规则,则表示无法识别该数据包中的攻击种类,则由数据库将该数据包的信息传给云推理学习模块做入侵可能性进行评估;Step 4, if the data packet detection unit does not find a matching matching rule, it means that the attack type in the data packet cannot be identified, and the database transmits the information of the data packet to the cloud reasoning learning module for evaluation of the possibility of intrusion;
步骤5,建立云规则,在无网络连接时,云认知推理机以数据库中存储的特征向量数据为训练样本建立起云规则数据库;Step 5, establishing cloud rules, when there is no network connection, the cloud cognitive reasoning engine uses the feature vector data stored in the database as training samples to establish a cloud rules database;
步骤6,判断无法识别的攻击种类,网络连接时,云认知推理机接收无法识别攻击种类的数据包的特征向量数据,云认知推理机采用基于遗传算法的特征向量提取算法对征向量数据进行优化选择获得最优选的入侵特征向量,该入侵特征向量和建立的运管站数据库比对,激活多条定性云规则,通过云认知推理机进行不确定性推理,确定入侵种类,并把结果发送至入侵检测引擎单元;Step 6: Determine the unidentifiable attack type. When the network is connected, the cloud cognitive inference engine receives the feature vector data of the data packets that cannot identify the attack type. The cloud cognitive inference engine uses the genetic algorithm-based feature vector extraction algorithm to analyze the feature vector data Perform optimization selection to obtain the most optimal intrusion feature vector, compare the intrusion feature vector with the established operation and management station database, activate multiple qualitative cloud rules, conduct uncertainty inference through the cloud cognitive inference engine, determine the intrusion type, and determine the type of intrusion. The result is sent to the intrusion detection engine unit;
所述步骤6中的基于遗传算法的特征向量提取算法的具体步骤如下:The specific steps of the genetic algorithm-based feature vector extraction algorithm in the step 6 are as follows:
1)设定进化代数g=0,生成包含n个个体的初始化群体P(g);1) Set the evolutionary algebra g=0, and generate an initialization population P(g) containing n individuals;
2)在该群体中对每个个体估值,计算各自适应度f(x);2) Evaluate each individual in the group, and calculate each adaptive degree f(x);
3)根据个体适应度f(x),从P(g)中选择两个个体作为父代(适应度值越大,选中的机会越大),根据交叉概率,让选出的两个个体进行交叉产生新的后代(如果交叉概率为0,即不进行交叉,则后代就是父代的完全复制),再根据变异概率,新生后代在各自基因座产生变异;重复上述步骤,产生新个体,将最后生成的个体形成新的群体P(g+1);3) According to the individual fitness f(x), select two individuals from P(g) as the parent (the greater the fitness value, the greater the chance of selection), and according to the crossover probability, let the two selected individuals carry out Crossover produces new offspring (if the crossover probability is 0, that is, no crossover is performed, the offspring is a complete copy of the parent), and then according to the mutation probability, the new offspring mutate at their respective loci; repeat the above steps to generate new individuals, The last generated individuals form a new group P(g+1);
4)将新产生的群体P(g+1)作为后续进化操作所需的群体,令进化代数g=g+1;4) Take the newly generated population P(g+1) as the population required for subsequent evolution operations, and let the evolutionary algebra g=g+1;
5)若终止条件满足,则算法结束,返回在当前群体中最好的个体,即最优解5) If the termination condition is satisfied, the algorithm ends and returns the best individual in the current group, that is, the optimal solution
6)若终止条件不满足,则跳至步骤2)继续该遗传算法。6) If the termination condition is not satisfied, skip to step 2) to continue the genetic algorithm.
根据上述步骤的计算结果可以修正并更新原来的云规则,以提高对当前网络环境的入侵检测的适应性。According to the calculation results of the above steps, the original cloud rules can be revised and updated, so as to improve the adaptability of intrusion detection to the current network environment.
所述步骤6中所述的不确定性推理具体步骤如下:The specific steps of the uncertainty reasoning described in the step 6 are as follows:
Step1,经过数据预处理后的一组未知入侵特征向量(X1,X2…Xn),每个Xi根据3En原则:|Ex-Xi|<3En激活规则;Step1, a set of unknown intrusion feature vectors (X1 , X2 ... Xn ) after data preprocessing, each Xi according to the 3En principle: |Ex-Xi |<3En activation rule;
Step2,每条被激活规则对应正向云发生器推理输出云滴(drop xi,yi);Step2, each activated rule corresponds to the forward cloud generator inference output cloud drop (drop xi , yi );
Step3,逆向云发生器在云滴drop(x1,y1),…(xn,yn)的基础上得到虚拟云的数值特征:Exij,Enij,Heij;Step3, the reverse cloud generator obtains the numerical features of the virtual cloud on the basis of cloud drop drop(x1 , y1 ),...(xn , yn ): Exij , Enij ,He ij ;
Step4,再将xi代入虚拟云中得到它的确定度;Step4, then substitutexi into the virtual cloud to get its certainty;
Step5,对每个xi重复Step2-5过程,分别得到对应的确定度;Step5, repeat the Step2-5 process for eachxi to obtain the corresponding degree of certainty;
Step6,依据最大确定度原则确定入侵类型。Step 6: Determine the intrusion type according to the principle of maximum certainty.
步骤7,所述入侵特征向量发送至原云规则化数据库中修正、更新成为型的云规则化数据库。Step 7, the intrusion feature vector is sent to the modified and updated cloud regularization database in the original cloud regularization database.
步骤8,所述入侵特征向量发送至统计分析单元中,统计分析单元根据入侵特征向量的日志记录判断是否构成网络入侵,把判断的结果发至入侵检测引擎单元和事件处理单元,同时把该入侵特征向量的数据信息发送至认知规则库中进行更新;Step 8, the intrusion feature vector is sent to the statistical analysis unit, the statistical analysis unit judges whether it constitutes a network intrusion according to the log record of the intrusion feature vector, and sends the judgment result to the intrusion detection engine unit and the event processing unit, and at the same time, the intrusion is sent to the intrusion detection engine unit and the event processing unit. The data information of the feature vector is sent to the cognitive rule base for updating;
所述步骤8中统计分析处理单元通过在任意给定的时刻,对n个变量值进行测量,推理判断系统是否有入侵发生,每个Ni(i=1,2,···,n)变量表示系统不同方面的特征,包含SYN数据包数目、用户登录失败次数、CPU使用率及网络流量等,Mi(i=1,2,···,n)是正常情况下该数据的期望值预测,在t时刻定义的检测函数为:In the step 8, the statistical analysis and processing unit measures the values of n variables at any given moment, and inferentially judges whether there is an intrusion in the system. Each Ni(i=1,2,...,n) variable Represents the characteristics of different aspects of the system, including the number of SYN packets, the number of user login failures, CPU usage and network traffic, etc. Mi (i=1,2,...,n) is the expected value prediction of the data under normal circumstances, The detection function defined at time t is:
其中,λi>0体现了重要程度的权值,即敏感程度,F(t)越小,通信过程越接近正常情况,当F(t)超过预先设定的阀值后,就认为网络入侵发生了。Among them, λi > 0 reflects the weight of the importance degree, that is, the degree of sensitivity. The smaller F(t) is, the closer the communication process is to the normal situation. When F(t) exceeds the preset threshold, it is considered that network intrusion happened.
步骤9,所述入侵检测引擎单元接收来自云认知推理机的推理结果和来自统计分析单元的判断结果,向事件处理单元发送指令;Step 9, the intrusion detection engine unit receives the inference result from the cloud cognitive inference engine and the judgment result from the statistical analysis unit, and sends an instruction to the event processing unit;
步骤10,所述事件处理单元收到来自入侵检测引擎单元和统计分析单元的指令后进行发出警报以及切断网络。Step 10, the event processing unit issues an alarm and disconnects the network after receiving the instructions from the intrusion detection engine unit and the statistical analysis unit.
与传统的入侵检测系统不同,面向云计算的具有认知能力的入侵检测系统(简称CIDCC)不再采用一对一的匹配,即单一特征匹配激活一条规则,而是当输入采集到的入侵特征向量,将激活多条定性云入侵规则,再通过云认知推理机来实现带有不确定性的关联推理,并只能判别结果输出给入侵检测引擎进行决策相应。Different from traditional intrusion detection systems, cloud computing-oriented intrusion detection systems with cognitive capabilities (CIDCC for short) no longer use one-to-one matching, that is, single feature matching activates a rule, but when the collected intrusion features are input. The vector will activate multiple qualitative cloud intrusion rules, and then use the cloud cognitive inference engine to realize the associated inference with uncertainty, and only the judgment result can be output to the intrusion detection engine for decision-making.
网络连接开始后,该网络防火墙的入侵检测系统内部会截获网络中的数据流,对数据预处理,即收集网络中的数据流,生成一定格式的数据包文件。然后,在数据包检测模块经过预处理的数据流会进行数据包检测。After the network connection is started, the intrusion detection system of the network firewall will intercept the data flow in the network, and preprocess the data, that is, collect the data flow in the network, and generate a data packet file in a certain format. Then, packet inspection is performed on the preprocessed data stream in the packet inspection module.
认知规则库中所提供的数据集,所有的攻击主要分为4大类:DOS类、PROBE类、R2L类和U2R类。其中,DOS类中包含的入侵类型有land、Nepture、pod、teardrop等;PROBE类包含的入侵类型有nmap、portsweep、satan、mscan、ipsweep。根据该认知规则库,判断数据流是否是已知攻击形式。对于已知的攻击,建立符合一定规则的攻击签名,攻击签名有以下几个部分组成:处理方式(Assert警告,Disconnect切断连接,Track跟踪记录)、传输层协议类型(TCP、UDP)、应用层协议类型(FTP、HTTP、SSH、Telnet)、端口号、IP地址范围、备注信息(Message)等。实验采用了整个数据集的1%(共为50000条连接记录),同时为了保证执行的效率,试验中分别随机选取10万条记录作为训练数据集和测试集。在训练样本中只包含DOS类、PROBE类、R2L类三类,余下的数据集另选2万条记录数据供测试用,其中包含训练集出现的各种攻击类型,也包含有在训练集中未出现的攻击类型。According to the data set provided in the cognitive rule base, all attacks are mainly divided into four categories: DOS, PROBE, R2L and U2R. Among them, the invasion types included in the DOS class include land, Nepture, pod, teardrop, etc.; the invasion types included in the PROBE class include nmap, portsweep, satan, mscan, and ipsweep. According to the cognitive rule base, it is judged whether the data stream is a known attack form. For known attacks, establish attack signatures that conform to certain rules. The attack signature consists of the following parts: processing method (Assert warning, Disconnect disconnection, Track trace record), transport layer protocol type (TCP, UDP), application layer Protocol type (FTP, HTTP, SSH, Telnet), port number, IP address range, message, etc. The experiment uses 1% of the entire data set (50,000 connection records in total). At the same time, in order to ensure the efficiency of execution, 100,000 records are randomly selected as the training data set and the test set in the experiment. Only DOS, PROBE, and R2L are included in the training samples, and 20,000 records are selected for the rest of the data set for testing, which include various attack types in the training set, as well as those not found in the training set. The type of attack that occurs.
检测结果验证,该系统对未知攻击和已知攻击有较好的检测能力,无论是对已知攻击还是未知攻击,利用了本文提出的新模型比利用传统入侵检测模型具有更高的ROC分值。而且基于云计算的认知入侵监测模型具有以下优点:首先,采用了该方法遗传算法对特征向量进行优化,使所需的训练时间和监测时间比其他方法短,其次,实时在线的检测能力较强,最后,在云计算的环境中充分利用云计算进行大规模并行计算和大数据量处理的能力,使运算能力大大加强,使系统更加安全高效。The detection results verify that the system has better detection ability for unknown attacks and known attacks. Whether it is known attacks or unknown attacks, the new model proposed in this paper has a higher ROC score than the traditional intrusion detection model. . Moreover, the cognitive intrusion monitoring model based on cloud computing has the following advantages: first, the genetic algorithm is used to optimize the feature vector, so that the required training time and monitoring time are shorter than other methods; secondly, the real-time online detection ability is relatively Finally, in the cloud computing environment, the ability of cloud computing to perform large-scale parallel computing and large-scale data processing can be fully utilized, which greatly enhances the computing power and makes the system more secure and efficient.
Claims (3)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201710096368.6ACN107040517B (en) | 2017-02-22 | 2017-02-22 | Cognitive intrusion detection method oriented to cloud computing environment |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201710096368.6ACN107040517B (en) | 2017-02-22 | 2017-02-22 | Cognitive intrusion detection method oriented to cloud computing environment |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN107040517A CN107040517A (en) | 2017-08-11 |
| CN107040517Btrue CN107040517B (en) | 2020-01-10 |
Family
ID=59533553
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN201710096368.6AActiveCN107040517B (en) | 2017-02-22 | 2017-02-22 | Cognitive intrusion detection method oriented to cloud computing environment |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN107040517B (en) |
Families Citing this family (18)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN107623691A (en)* | 2017-09-29 | 2018-01-23 | 长沙市智为信息技术有限公司 | A kind of ddos attack detecting system and method based on reverse transmittance nerve network algorithm |
| CN107612948A (en)* | 2017-11-08 | 2018-01-19 | 国网四川省电力公司信息通信公司 | A kind of intrusion prevention system and method |
| CN107992746B (en)* | 2017-12-14 | 2021-06-25 | 华中师范大学 | Malicious behavior mining method and device |
| CN107835201A (en)* | 2017-12-14 | 2018-03-23 | 华中师范大学 | Network attack detecting method and device |
| CN108183902B (en)* | 2017-12-28 | 2021-10-22 | 北京奇虎科技有限公司 | Method and device for identifying malicious website |
| CN109756478A (en)* | 2018-11-28 | 2019-05-14 | 国网江苏省电力有限公司南京供电分公司 | A multi-level backup blocking method for abnormal industrial control system attacks considering priority |
| CN109547455A (en)* | 2018-12-06 | 2019-03-29 | 南京邮电大学 | Industrial Internet of Things anomaly detection method, readable storage medium storing program for executing and terminal |
| CN110324348A (en)* | 2019-07-08 | 2019-10-11 | 陈浩 | A kind of information security of computer network monitoring system |
| CN110417823B (en)* | 2019-09-25 | 2020-04-14 | 广东电网有限责任公司佛山供电局 | Communication network intrusion detection method based on embedded feature selection architecture |
| CN112653651A (en)* | 2019-10-11 | 2021-04-13 | 四川无国界信息技术有限公司 | Vulnerability mining method based on cloud computing |
| CN112866175B (en)* | 2019-11-12 | 2022-08-19 | 华为技术有限公司 | Method, device, equipment and storage medium for reserving abnormal traffic types |
| CN112699219B (en)* | 2020-12-30 | 2025-07-22 | 平安证券股份有限公司 | Log searching method and device |
| CN113065127B (en)* | 2021-02-24 | 2022-09-20 | 山东英信计算机技术有限公司 | A database protection method, system and medium |
| CN114154160B (en)* | 2022-02-08 | 2022-09-16 | 中国电子信息产业集团有限公司第六研究所 | Container cluster monitoring method and device, electronic equipment and storage medium |
| CN115118500B (en)* | 2022-06-28 | 2023-11-07 | 深信服科技股份有限公司 | Attack behavior rule acquisition method and device and electronic equipment |
| CN116015760A (en)* | 2022-12-08 | 2023-04-25 | 范晓明 | Cloud computing protection early warning system based on big data |
| CN116168805B (en)* | 2023-01-20 | 2023-08-01 | 北京瑞帆科技有限公司 | Thinking training device and cognitive training system for cognitive training |
| CN117273571B (en)* | 2023-10-12 | 2024-04-02 | 江苏泓鑫科技有限公司 | Intelligent port operation data management system and method based on blockchain |
Citations (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN101924762A (en)* | 2010-08-18 | 2010-12-22 | 奇智软件(北京)有限公司 | Active defense method based on cloud security |
| CN102111420A (en)* | 2011-03-16 | 2011-06-29 | 上海电机学院 | Intelligent NIPS framework based on dynamic cloud/fire wall linkage |
| CN102123396A (en)* | 2011-02-14 | 2011-07-13 | 恒安嘉新(北京)科技有限公司 | Cloud detection method of virus and malware of mobile phone based on communication network |
| CN102663284A (en)* | 2012-03-21 | 2012-09-12 | 南京邮电大学 | Malicious code identification method based on cloud computing |
| CN102724176A (en)* | 2012-02-23 | 2012-10-10 | 北京市计算中心 | Intrusion detection system facing cloud calculating environment |
| CN104753920A (en)* | 2015-03-01 | 2015-07-01 | 江西科技学院 | Quantum genetic algorithm based intrusion detection method |
Family Cites Families (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20030113727A1 (en)* | 2000-12-06 | 2003-06-19 | Girn Kanwaljit Singh | Family history based genetic screening method and apparatus |
- 2017
- 2017-02-22CNCN201710096368.6Apatent/CN107040517B/enactiveActive
Patent Citations (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN101924762A (en)* | 2010-08-18 | 2010-12-22 | 奇智软件(北京)有限公司 | Active defense method based on cloud security |
| CN102123396A (en)* | 2011-02-14 | 2011-07-13 | 恒安嘉新(北京)科技有限公司 | Cloud detection method of virus and malware of mobile phone based on communication network |
| CN102111420A (en)* | 2011-03-16 | 2011-06-29 | 上海电机学院 | Intelligent NIPS framework based on dynamic cloud/fire wall linkage |
| CN102724176A (en)* | 2012-02-23 | 2012-10-10 | 北京市计算中心 | Intrusion detection system facing cloud calculating environment |
| CN102663284A (en)* | 2012-03-21 | 2012-09-12 | 南京邮电大学 | Malicious code identification method based on cloud computing |
| CN104753920A (en)* | 2015-03-01 | 2015-07-01 | 江西科技学院 | Quantum genetic algorithm based intrusion detection method |
Also Published As
| Publication number | Publication date |
|---|---|
| CN107040517A (en) | 2017-08-11 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN107040517B (en) | Cognitive intrusion detection method oriented to cloud computing environment | |
| Bendiab et al. | IoT malware network traffic classification using visual representation and deep learning | |
| Sriram et al. | Network flow based IoT botnet attack detection using deep learning | |
| Sherazi et al. | DDoS attack detection: A key enabler for sustainable communication in internet of vehicles | |
| Soe et al. | Rule generation for signature based detection systems of cyber attacks in iot environments | |
| Haddadi et al. | Benchmarking the effect of flow exporters and protocol filters on botnet traffic classification | |
| Barati et al. | Distributed Denial of Service detection using hybrid machine learning technique | |
| Le et al. | Data analytics on network traffic flows for botnet behaviour detection | |
| Haddadi et al. | Botnet behaviour analysis using ip flows: with http filters using classifiers | |
| Kato et al. | An intelligent ddos attack detection system using packet analysis and support vector machine | |
| CN113206860B (en) | A DRDoS attack detection method based on machine learning and feature selection | |
| Zang et al. | Machine learning-based intrusion detection system for big data analytics in VANET | |
| Al-Obeidat et al. | Hybrid multicriteria fuzzy classification of network traffic patterns, anomalies, and protocols | |
| Pan et al. | Anomaly based intrusion detection for building automation and control networks | |
| Ma et al. | DDoS detection for 6G Internet of Things: Spatial-temporal trust model and new architecture | |
| Rahman | Detection of distributed denial of service attacks based on machine learning algorithms | |
| Salih et al. | Implementation of hybrid artificial intelligence technique to detect covert channels attack in new generation internet protocol IPv6 | |
| Umamaheswari et al. | Honeypot TB-IDS: trace back model based intrusion detection system using knowledge based honeypot construction model | |
| Sharma et al. | Bot-iot: Detection of ddos attacks in internet of things for smart cities | |
| Palekar et al. | IoT authentication model with optimized deep Q network for attack detection and mitigation | |
| Thamaraimanalan et al. | ANFIS-based multilayered algorithm for botnet detection | |
| Lu et al. | Botnets detection based on irc-community | |
| Umamaheswaran et al. | RETRACTED: Smart intrusion detection system with balanced data in IoMT infra | |
| Qian et al. | Improved K-means-based solution for detecting DDoS attacks in SDN | |
| Lavi et al. | Fine-Tuning Large Language Models For Network Traffic Analysis in Cyber Security |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| CB02 | Change of applicant information | ||
| CB02 | Change of applicant information | Address after:Yuen Road Qixia District of Nanjing City, Jiangsu Province, No. 9 210023 Applicant after:Nanjing Post & Telecommunication Univ. Address before:210003 Gulou District, Jiangsu, Nanjing new model road, No. 66 Applicant before:Nanjing Post & Telecommunication Univ. | |
| GR01 | Patent grant | ||
| GR01 | Patent grant |