CN105791221B - Method and device for issuing rules - Google Patents
Method and device for issuing rulesDownload PDFInfo
- Publication number
- CN105791221B CN105791221BCN201410806644.XACN201410806644ACN105791221BCN 105791221 BCN105791221 BCN 105791221BCN 201410806644 ACN201410806644 ACN 201410806644ACN 105791221 BCN105791221 BCN 105791221B
- Authority
- CN
- China
- Prior art keywords
- rule
- program
- rules
- server
- behavior
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Active
Links
Images
Landscapes
- Information Transfer Between Computers (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明涉及互联网技术领域,具体涉及一种规则下发方法及装置。The present invention relates to the field of Internet technologies, in particular to a method and device for issuing rules.
背景技术Background technique
主动防御是基于程序行为自主分析判断,以防御恶意程序的实时防护技术。恶意程序是一个概括性的术语,指任何故意创建用来执行未经授权并通常是有害行为的软件程序。计算机病毒、后门程序、键盘记录器、密码盗取者、Word和Excel宏病毒、引导区病毒、脚本病毒、木马、犯罪软件、间谍软件和广告软件等等,都可以称之为恶意程序。Active defense is a real-time protection technology based on autonomous analysis and judgment of program behavior to defend against malicious programs. Malicious program is an umbrella term that refers to any software program that is intentionally created to perform unauthorized and often harmful behavior. Computer viruses, backdoor programs, keyloggers, password stealers, Word and Excel macro viruses, boot sector viruses, script viruses, Trojans, crimeware, spyware and adware, etc., can all be called malicious programs.
主动防御在进行恶意程序防御时,不以文件特征值作为判断恶意程序的依据,而是从最原始的定义出发,直接将程序的行为作为判断恶意程序的依据。以基于主机的入侵防御系统(Host-based Intrusion Prevention System,简称HIPS)为例,HIPS是一种能监控计算机中文件的运行和文件运行了其他的文件以及文件对注册表的修改,并发出报告请求允许运行或修改的主动防御软件。Active defense does not use file feature values as the basis for judging malicious programs when defending against malicious programs, but starts from the most primitive definition and directly uses program behavior as the basis for judging malicious programs. Taking Host-based Intrusion Prevention System (HIPS) as an example, HIPS is a kind of system that can monitor the operation of files in the computer and the operation of other files and the modification of the registry by files, and issue reports. Active defense software that requests permission to run or modify.
然而当某个程序触发某个行为的时候,云端会下发许多关于执行该程序的防御规则,大量的规则占用了较多的系统内存,造成系统启动速度变慢,导致用户体验差。However, when a program triggers a certain behavior, the cloud will issue many defense rules for executing the program. A large number of rules occupy more system memory, resulting in slower system startup and poor user experience.
发明内容SUMMARY OF THE INVENTION
针对现有技术中的缺陷,本发明提供了一种规则下发方法及装置,解决了现有技术的设备中因下发大量的规则占用较多的系统内存,提升了用户体验。Aiming at the defects in the prior art, the present invention provides a method and device for issuing rules, which solves the problem that the device in the prior art occupies a lot of system memory due to issuing a large number of rules, and improves user experience.
第一方面,本发明提供了一种规则下发装置,包括:In a first aspect, the present invention provides a device for issuing rules, including:
监控模块,用于监控设备中每一程序对应的程序行为;The monitoring module is used to monitor the program behavior corresponding to each program in the device;
判断模块,用于采用预设的行为触发条件判断当前程序对应的程序行为是否符合规则触发标识;a judgment module, configured to use a preset behavior trigger condition to judge whether the program behavior corresponding to the current program conforms to the rule trigger identifier;
第一发送模块,用于在所述程序行为符合所述规则触发标识时,向服务器发送规则请求,以使服务器根据所述规则请求查找与该规则触发标识对应的规则;a first sending module, configured to send a rule request to the server when the program behavior conforms to the rule trigger identifier, so that the server searches for a rule corresponding to the rule trigger identifier according to the rule request;
第一接收模块,用于接收服务器发送的规则,采用所述服务器发送的规则对所述当前程序对应的程序行为进行监控。The first receiving module is configured to receive the rules sent by the server, and use the rules sent by the server to monitor the program behavior corresponding to the current program.
可选的,所述装置还包括第二发送模块,用于在所述服务器发送的部分/全部规则不匹配监控到的所述当前程序对应的程序行为时,向服务器发送与所述部分/全部规则对应的规则撤销请求,以使服务器根据所述规则撤销请求发送所述部分/全部规则的删除指令;Optionally, the device further includes a second sending module, configured to send the part/all rules to the server when part/all of the rules sent by the server do not match the monitored program behavior corresponding to the current program. a rule revocation request corresponding to the rule, so that the server sends a deletion instruction of the part/all of the rules according to the rule revocation request;
第二接收模块,用于接收服务器发送的删除指令,根据所述删除指令将所述部分/全部规则删除。The second receiving module is configured to receive a deletion instruction sent by the server, and delete some/all of the rules according to the deletion instruction.
可选的,所述预设的行为触发条件为服务器根据多个设备中的程序对应的程序行为统计的,并预先发送设备的行为触发条件;Optionally, the preset behavior triggering conditions are collected by the server according to program behaviors corresponding to programs in multiple devices, and the behavior triggering conditions of the devices are sent in advance;
所述行为触发条件中包括:每一程序对应的程序行为,和与该程序行为对应的规则触发标识。The behavior triggering conditions include: program behaviors corresponding to each program, and rule triggering identifiers corresponding to the program behaviors.
可选的,所述装置还包括:Optionally, the device further includes:
第三接收模块,用于接收所述服务器发送的用于删除所述设备中不使用规则的规则删除指令,所述规则删除指令包括:所述服务器发送到所述设备中的规则删除标识;A third receiving module, configured to receive a rule deletion instruction sent by the server for deleting an unused rule in the device, where the rule deletion instruction includes: a rule deletion identifier sent by the server to the device;
确定模块,用于查找所述设备中与所述规则删除标识匹配的规则,并确定该规则已经不再监控当前程序的程序行为,则根据所述规则删除指令将该规则删除。A determination module, configured to search for a rule in the device that matches the rule deletion identifier, and determine that the rule no longer monitors the program behavior of the current program, and delete the rule according to the rule deletion instruction.
可选的,接收服务器发送的规则为防御规则、文件防御规则、拦截规则、数据处理规则;Optionally, the rules sent by the receiving server are defense rules, file defense rules, interception rules, and data processing rules;
所述程序行为包括:进程创建、线程创建、文件读写操作、注册表读写操作、注册表改写操作、堆栈操作、网络通讯、和/或,线程注入的操作。The program behavior includes: process creation, thread creation, file read and write operations, registry read and write operations, registry rewrite operations, stack operations, network communication, and/or thread injection operations.
第二方面,本发明提供了一种规则下发方法,包括:In a second aspect, the present invention provides a method for issuing rules, including:
监控设备中每一程序对应的程序行为;Monitor the program behavior corresponding to each program in the device;
采用预设的行为触发条件判断当前程序对应的程序行为是否符合规则触发标识;Use preset behavior trigger conditions to determine whether the program behavior corresponding to the current program conforms to the rule trigger identifier;
如果所述程序行为符合所述规则触发标识,向服务器发送规则请求,以使服务器根据所述规则请求查找与该规则触发标识对应的规则;If the program behavior complies with the rule triggering identifier, send a rule request to the server, so that the server searches for a rule corresponding to the rule triggering identifier according to the rule request;
接收服务器发送的规则,采用所述服务器发送的规则对所述当前程序对应的程序行为进行监控。The rules sent by the server are received, and the program behavior corresponding to the current program is monitored by using the rules sent by the server.
可选的,所述方法还包括:Optionally, the method further includes:
若所述服务器发送的部分/全部规则不匹配监控到的所述当前程序对应的程序行为,则向服务器发送与所述部分/全部规则对应的规则撤销请求,以使服务器根据所述规则撤销请求发送所述部分/全部规则的删除指令;If some/all of the rules sent by the server do not match the monitored program behavior corresponding to the current program, send a rule revocation request corresponding to the part/all of the rules to the server, so that the server revokes the request according to the rule send a deletion instruction for some/all of the rules;
接收服务器发送的删除指令,根据所述删除指令将所述部分/全部规则删除。A deletion instruction sent by the server is received, and some/all of the rules are deleted according to the deletion instruction.
可选的,所述预设的行为触发条件为服务器根据多个设备中的程序对应的程序行为统计的,并预先发送设备的行为触发条件;Optionally, the preset behavior triggering conditions are collected by the server according to program behaviors corresponding to programs in multiple devices, and the behavior triggering conditions of the devices are sent in advance;
所述行为触发条件中包括:每一程序对应的程序行为,和与该程序行为对应的规则触发标识。The behavior triggering conditions include: program behaviors corresponding to each program, and rule triggering identifiers corresponding to the program behaviors.
可选的,所述方法还包括:Optionally, the method further includes:
接收所述服务器发送的用于删除所述设备中不使用规则的规则删除指令,所述规则删除指令包括:所述服务器发送到所述设备中的规则删除标识;Receive a rule deletion instruction sent by the server for deleting an unused rule in the device, where the rule deletion instruction includes: a rule deletion identifier sent by the server to the device;
查找所述设备中与所述规则删除标识匹配的规则,并确定该规则已经不再监控当前程序的程序行为,则根据所述规则删除指令将该规则删除。Find a rule in the device that matches the rule deletion identifier, and determine that the rule no longer monitors the program behavior of the current program, then delete the rule according to the rule deletion instruction.
可选的,接收服务器发送的规则为防御规则、文件防御规则、拦截规则、数据处理规则;Optionally, the rules sent by the receiving server are defense rules, file defense rules, interception rules, and data processing rules;
所述程序行为包括:进程创建、线程创建、文件读写操作、注册表读写操作、注册表改写操作、堆栈操作、网络通讯、和/或,线程注入的操作。The program behavior includes: process creation, thread creation, file read and write operations, registry read and write operations, registry rewrite operations, stack operations, network communication, and/or thread injection operations.
由上述技术方案可知,本发明提供的一种规则下发方法及装置,该装置通过监控设备中的每一程序对应的程序行为,当采用预设的行为触发条件判断当前程序对应的程序行为符合规则触发标识时,使云端服务器根据该规则触发标识下发与该规则触发标识对应的规则,在接收该规则后根据该规则监控当前程序对应的程序行为,由此,可不预先将设备使用的所有规则下发,进而可减少规则下发量,降低了设备中系统内存的占用,提升了用户体验。It can be seen from the above technical solutions that the present invention provides a method and device for issuing rules. The device monitors the program behavior corresponding to each program in the device, and judges that the program behavior corresponding to the current program conforms to the preset behavior trigger conditions. When the rule triggers the ID, make the cloud server issue the rule corresponding to the rule trigger ID according to the rule trigger ID, and monitor the program behavior corresponding to the current program according to the rule after receiving the rule. The rules are issued, which can reduce the amount of rules issued, reduce the system memory occupation in the device, and improve the user experience.
附图说明Description of drawings
图1为本发明一实施例提供的规则下发方法的流程示意图;1 is a schematic flowchart of a method for issuing rules according to an embodiment of the present invention;
图2A和图2B为本发明另一实施例提供的规则下发方法的流程示意图;2A and 2B are schematic flowcharts of a method for issuing a rule provided by another embodiment of the present invention;
图3A和图3B为本发明另一实施例提供的规则下发方法的流程示意图;3A and 3B are schematic flowcharts of a method for issuing rules provided by another embodiment of the present invention;
图4为本发明另一实施例提供的规则下发方法的流程示意图;4 is a schematic flowchart of a method for issuing rules provided by another embodiment of the present invention;
图5为本发明一实施例提供的规则下发装置的结构示意图;5 is a schematic structural diagram of an apparatus for issuing rules provided by an embodiment of the present invention;
图6为本发明另一实施例提供的规则下发装置的结构示意图;6 is a schematic structural diagram of an apparatus for issuing rules provided by another embodiment of the present invention;
图7为本发明另一实施例提供的规则下发装置的结构示意图。FIG. 7 is a schematic structural diagram of an apparatus for issuing rules according to another embodiment of the present invention.
具体实施方式Detailed ways
下面结合附图,对发明的具体实施方式作进一步描述。以下实施例仅用于更加清楚地说明本发明的技术方案,而不能以此来限制本发明的保护范围。The specific embodiments of the invention will be further described below with reference to the accompanying drawings. The following examples are only used to illustrate the technical solutions of the present invention more clearly, and cannot be used to limit the protection scope of the present invention.
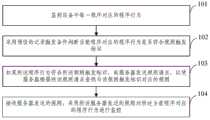
图1示出了本发明实施例提供的规则下发方法的流程示意图,如图1所示,该规则下发方法包括如下步骤:FIG. 1 shows a schematic flowchart of a method for issuing rules provided by an embodiment of the present invention. As shown in FIG. 1 , the method for issuing rules includes the following steps:
101、监控设备中每一程序对应的程序行为;101. Monitor the program behavior corresponding to each program in the device;
本实施例中的设备,如手机、个人计算机、平板电脑、台式机、任一具有操作系统的设备/管理设备等;The device in this embodiment, such as a mobile phone, a personal computer, a tablet computer, a desktop computer, any device with an operating system/management device, etc.;
上述程序可以包括:“即时聊天程序、视频通话程序、在线游戏程序、下载软件程序、安全检测程序、群发信息程序等。102、采用预设的行为触发条件判断当前程序对应的程序行为是否符合规则触发标识;The above program may include: "instant chat program, video call program, online game program, download software program, security detection program, mass message program, etc. 102. Use preset behavior trigger conditions to determine whether the program behavior corresponding to the current program complies with the rules. trigger mark;
举例来说,本实施例中的规则触发标识可以为启动程序时触发的规则下载的标识,例如,写某个程序注册表项的规则触发标识、或进行某个网络通讯的规则触发标识等。For example, the rule trigger identifier in this embodiment may be a rule download identifier triggered when a program is started, for example, a rule trigger identifier for writing a registry entry of a program, or a rule trigger identifier for performing a certain network communication.
该触发标识如为启动程序的规则触发标识时,也可以这样定义:When the trigger ID is the rule trigger ID of the startup program, it can also be defined as follows:
例如:即时聊天程序中,在启动该即时聊天程序建立进程时,该建立进程的程序行为对应有第一规则触发标识;由此,可确定当前程序对应的程序行为符合第一规则触发标识,进而可执行下述的步骤103。For example: in the instant chat program, when the instant chat program establishment process is started, the program behavior of the establishment process corresponds to the first rule trigger mark; thus, it can be determined that the program behavior corresponding to the current program conforms to the first rule trigger mark, and then The following
或者,在即时聊天程序中需要发送照片时,该发送照片的程序行为对应有第二规则触发标识等。Or, when a photo needs to be sent in the instant chat program, the program behavior of sending the photo corresponds to a second rule triggering identifier and the like.
上述触发标识以及触发标识的定义,仅用作举例说明,本实施例并不对其进行具体的限定。The above trigger identifier and the definition of the trigger identifier are only used for illustration, and are not specifically limited in this embodiment.
103、如果所述程序行为符合所述规则触发标识,向服务器发送规则请求,以使服务器根据所述规则请求查找与该规则触发标识对应的规则;103. If the program behavior complies with the rule trigger identifier, send a rule request to the server, so that the server searches for a rule corresponding to the rule trigger identifier according to the rule request;
在本实施例中,上述服务器可为云端服务器,云端服务器根据规则请求查找与该规则触发标识对应的规则,云端服务器查找的规则为设备中当前程序对应的程序行为的下一步最有可能执行的行为规则。In this embodiment, the above-mentioned server may be a cloud server, the cloud server searches for the rule corresponding to the triggering identifier of the rule according to the rule request, and the rule searched by the cloud server is the next step of the program behavior corresponding to the current program in the device that is most likely to be executed Rules of Conduct.
具体的,在监控设备的程序对应的程序行为,通过预设的行为触发条件发现该设备当前程序对应的程序行为符合启动程序的规则触发标识,则直接向云端服务器发送获取启动某个程序的规则请求。比如启动一个程序安装包,则在此程序安装包安装程序启动之后,下一步最有可能执行的行为包括注册进程、加载其他应用安装程序等操作,此时云端服务器会将注册进程、加载其他应用安装程序等的对应的安全规则下发。Specifically, when monitoring the program behavior corresponding to the program of the device, it is found through the preset behavior trigger conditions that the program behavior corresponding to the current program of the device conforms to the rule trigger identifier of the startup program, and then directly sends the cloud server to obtain the rules for starting a certain program. ask. For example, to start a program installation package, after the program installation package installation program is started, the next most likely actions include the registration process, loading other application installation programs, etc. At this time, the cloud server will register the process, load other applications, etc. The corresponding security rules of the installation program, etc. are issued.
104、接收服务器发送的规则,采用所述服务器发送的规则对所述当前程序对应的程序行为进行监控。104. Receive the rules sent by the server, and use the rules sent by the server to monitor the program behavior corresponding to the current program.
在具体应用中,上述接收云服务器发送的规则可以为防御规则、文件防御规则、拦截规则、数据处理规则。In a specific application, the above-mentioned rules sent by the receiving cloud server may be defense rules, file defense rules, interception rules, and data processing rules.
上述防御规则例如应用程序防御体系(Application Defend,简称AD)、注册表防御体系(Registry Defend,简称RD),其中,AD用于对一些应用程序的启动或者运行过程等进行监视,RD用于对常见的系统敏感注册表项进行监视。The above defense rules are, for example, Application Defend (AD) and Registry Defend (RD), where AD is used to monitor the startup or running process of some applications, and RD is used to monitor the startup or running process of some applications. Common system sensitive registry keys are monitored.
文件防御规则例如:文件防御体系(File Defend,简称FD),通过可制定的规则对本地的运行程序、注册表的读写操作、以及文件读写操作进行判断并确定允许或禁止。FD用于监视系统敏感目录的文件(如HOSTS)操作,如修改删除系统目录里的任何文件或创建新文件等,也可以用来发现被驱动木马隐藏的文件本体。File defense rules, such as: File Defend (FD for short), judge and allow or prohibit local running programs, registry read and write operations, and file read and write operations through rules that can be formulated. FD is used to monitor file (such as HOSTS) operations in sensitive system directories, such as modifying and deleting any file in the system directory or creating new files, etc. It can also be used to discover the file body hidden by the driver Trojan.
拦截规则可以包括基于某个程序启动的拦截、启动某个程序后附带广告的拦截,某个程序操作权限的拦截等。The interception rules may include interception based on the start of a program, interception of an ad attached to a program after the start of a program, and interception of the operation authority of a program.
以权限拦截规则为例,权限拦截规则为Appstore(应用商店)的安全管理员根据开发人员上传的应用程序审核的结果,比如一个记事本程序在启动时却要求自己拥有读取通讯录的权限,那么安全管理员在将这个应用程序添加到Appstore的同时,会将这个应用程序的权限拦截规则添加至云端服务器,这时接收SecurityGuard上传的信息。网络管理员的设置的权限拦截规则不能代表用户的意志,SecurityGuard会将用户自行设定的权限拦截规则上传至云端服务器,云端服务器自动分析这些消息,然后计算每个权限的用户拦截率,用于提示新安装应用程序的用户。Taking the permission interception rule as an example, the security administrator of the permission interception rule is the Appstore (app store) based on the results of the application review uploaded by the developer. For example, a notepad program requires itself to have the permission to read the address book when it is started. Then, when the security administrator adds the application to the Appstore, he will add the application's permission interception rules to the cloud server, and then receive the information uploaded by SecurityGuard. The permission blocking rules set by the network administrator cannot represent the user's will. SecurityGuard will upload the permission blocking rules set by the user to the cloud server. The cloud server automatically analyzes these messages, and then calculates the user interception rate of each permission for use. Prompt users of newly installed applications.
如果每个权限的用户拦截率超过预设值的话,则在该记事本程序启动想要读取通讯录的权限时,对其进行拦截;另一种可能的情况下,如果每个权限的用户拦截率未超过预设值的话,则采用该规则在该记事本程序启动想要读取通讯录的权限时,不对其进行拦截,但是会给用户设备发送一个提示消息,以帮助用户了解此应用程序启动的程序行为时,该应用程序启动所对应的哪些程序行为是存在潜在危害的。If the user interception rate of each permission exceeds the preset value, the Notepad program will block it when it starts the permission to read the address book; in another possible case, if the user of each permission If the interception rate does not exceed the preset value, this rule will not be intercepted when the Notepad program activates the permission to read the address book, but a prompt message will be sent to the user's device to help the user understand this application. When the program behavior is started by the program, which program behaviors corresponding to the application start are potentially harmful.
上述数据处理规则与上述防御规则、文件防御规则、拦截规则类似,本实施例不再进行举例说明。The foregoing data processing rules are similar to the foregoing defense rules, file defense rules, and interception rules, and will not be described in this embodiment.
本实施例中的上述方法通过监控设备中的每一程序对应的程序行为,当采用预设的行为触发条件判断当前程序对应的程序行为符合规则触发标识时,使云端服务器根据该规则触发标识下发与该规则触发标识对应的规则,在接收该规则后根据该规则监控当前程序对应的程序行为,该装置针对规则触发标识下发程序行为的规则比现有不针对规则触发标识下发程序行为的规则,在减少规则下发量的同时,降低了系统内存的占用,提升了用户体验。The above-mentioned method in this embodiment monitors the program behavior corresponding to each program in the device, and when the preset behavior trigger condition is used to determine that the program behavior corresponding to the current program conforms to the rule trigger mark, the cloud server is made to download the trigger mark according to the rule trigger mark. Issue a rule corresponding to the triggering mark of the rule, and monitor the program behavior corresponding to the current program according to the rule after receiving the rule. The rules, while reducing the amount of rules issued, reduce the occupation of system memory and improve the user experience.
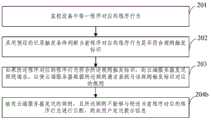
图2A示出了本发明另一实施例提供的规则下发方法的流程示意图,如图2A所示,该规则下发方法包括如下步骤:FIG. 2A shows a schematic flowchart of a method for issuing rules provided by another embodiment of the present invention. As shown in FIG. 2A , the method for issuing rules includes the following steps:
201、监控设备中每一程序对应的程序行为;201. Monitor the program behavior corresponding to each program in the device;
具体的,该程序行为包括:进程创建、线程创建、文件读写操作、注册表读写操作、注册表改写操作、堆栈操作、网络通讯、和/或,线程注入的操作。Specifically, the program behavior includes: process creation, thread creation, file read and write operations, registry read and write operations, registry rewrite operations, stack operations, network communication, and/or thread injection operations.
例如上述程序行为为进程创建,可以为监控程序的启动目录startup目录,例如,体验(experience,简称XP)系统所有程序的startup目录:“C:\Documents and Settings\All Users\[开始]菜单\程序\启动”;For example, the above program behavior is created by a process, which can be the startup directory of the monitoring program's startup directory, for example, the startup directory of all programs in the experience (experience, referred to as XP) system: "C:\Documents and Settings\All Users\[Start] menu\ program\start";
注册表项的改写程序,如Registry key rewrite procedures, such as
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Current Version\Run,其中Run是注册表中的键;HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Current Version\Run, where Run is the key in the registry;
HKEY_LOCAL_MACHINE\Systm\CurrentcontrolSet\Services\*\[I magePath],其中ImagePath是一个值,对应服务/驱动的路径。HKEY_LOCAL_MACHINE\Systm\CurrentcontrolSet\Services\*\[ImagePath], where ImagePath is a value corresponding to the service/driver path.
202、采用预设的行为触发条件判断当前程序对应的程序行为是否符合规则触发标识;202. Use a preset behavior trigger condition to determine whether the program behavior corresponding to the current program conforms to the rule trigger identifier;
本实施例中的预设的行为触发条件为云端服务器根据多个设备中的程序对应的程序行为统计的,并预先发送设备的行为触发条件;The preset behavior triggering conditions in this embodiment are statistics by the cloud server according to program behaviors corresponding to programs in multiple devices, and the behavior triggering conditions of the devices are sent in advance;
在具体应用中,云端服务器会对多个设备中的程序对应的程序行为统计后,实时或定时的发送到所述设备,其中该预设的行为触发条件包括该设备中所有程序对应的程序行为的触发条件。In a specific application, the cloud server will collect statistics on the program behaviors corresponding to programs in multiple devices, and then send them to the devices in real time or regularly, where the preset behavior triggering conditions include program behaviors corresponding to all programs in the device. trigger condition.
所述行为触发条件中包括:每一程序对应的程序行为,和与该程序行为对应的规则触发标识。The behavior triggering conditions include: program behaviors corresponding to each program, and rule triggering identifiers corresponding to the program behaviors.
具体的,与该程序行为对应的规则触发标识包括以下中的一种或多种:文件名、文件路径、文件大小、文件内部名、文件信息摘要算法、文件签名公司信息、文件修改时间、文件创建时间、文件属性、服务名称、注册表位置。Specifically, the rule triggering identifier corresponding to the program behavior includes one or more of the following: file name, file path, file size, file internal name, file information digest algorithm, file signature company information, file modification time, file Creation time, file attributes, service name, registry location.
当上述触发标识包括多个时,多个触发标识按照预设的组合规则组合得到的字符串。When there are multiple trigger identifiers, the multiple trigger identifiers are combined according to a preset combination rule to obtain a character string.
举例来说,触发标识为文件大小、文件信息摘要算法和文件属性,其中文件大小为1M、文件信息摘要算法MD5=d41d8cd98f00b204e9800998ecf8427、文件属性为只读,则组合得到的字符串可以为“1M d41d8cd98f00b204e9800998ecf8427只读”或者可以为“d41d8cd98f00b204e9800998ecf84271M只读”,或者还可以为“d41d8cd98f00b204e9800998ecf8427只读1M”当然还可以采用其他组合规则组合得到字符串。For example, if the trigger identifier is file size, file information digest algorithm and file attribute, where the file size is 1M, the file information digest algorithm MD5=d41d8cd98f00b204e9800998ecf8427, and the file attribute is read-only, the combined string can be "1M d41d8cd98f00b204e9800998ecf8427 only "Read" can either be "d41d8cd98f00b204e9800998ecf84271M read only", or it can also be "d41d8cd98f00b204e9800998ecf8427 read only 1M" Of course, other combination rules can be used to obtain strings.
上述行为触发条件可以以表格的形式存储在该设备中,如表1所示。The above behavior trigger conditions can be stored in the device in the form of a table, as shown in Table 1.
表1Table 1
203、如果所述程序对应的程序行为符合所述规则触发标识,向云端服务器发送规则请求,以使云端服务器根据所述规则请求查找与该规则触发标识对应的规则;203. If the program behavior corresponding to the program conforms to the rule trigger identifier, send a rule request to the cloud server, so that the cloud server searches for the rule corresponding to the rule trigger identifier according to the rule request;
204a、接收云端服务器发送的规则,且所述规则能够与所述当前程序对应的程序行为进行匹配,则通过规则对所述当前程序对应的程序行为进行监控。204a. Receive the rule sent by the cloud server, and the rule can match the program behavior corresponding to the current program, and monitor the program behavior corresponding to the current program through the rule.
举例来说,若当前程序的程序行为为某个程序安装包安装启动,此时接收云端服务器发送的运行该安装程序、加载其他应用安装程序等规则,在监控当前程序对应的程序行为时,发现当前程序对应的程序行为为加载了某个杀毒或某个浏览器等其他应用安装程序行为,此时查看云端服务器发送的加载其他应用安装程序的规则中是否允许将该杀毒或浏览器等其他应用安装程序进行安装,即通过规则判断程序对应的程序行为是否为恶意的,若该规则中允许安装该杀毒或浏览器等其他应用安装程序,即当前程序对应的程序行为为规则中的白名单中的运行程序,则保持当前程序对应的程序行为;若该规则中不允许安装该杀毒或浏览器等其他应用安装程序,即当前程序行为为规则中的黑名单中的运行程序,则将当前程序对应的程序行为进行拦截或者报警等处理。For example, if the program behavior of the current program is the installation and startup of a program installation package, at this time, the rules such as running the installation program and loading other application installation programs sent by the cloud server are received. When monitoring the program behavior corresponding to the current program, it is found that The program behavior corresponding to the current program is the behavior of loading an antivirus or a browser and other application installers. At this time, check whether the antivirus or browser and other applications are allowed in the rules sent by the cloud server for loading other application installers. Install the program to install, that is, determine whether the program behavior corresponding to the program is malicious through the rule. If the rule allows the installation of other application installation programs such as the antivirus or browser, that is, the program behavior corresponding to the current program is in the whitelist in the rule. If the running program of the current program is not allowed to install the antivirus or other application installation programs such as browsers, that is, the current program behavior is the running program in the blacklist in the rule, the current program will be The corresponding program behavior is intercepted or alarmed.
在另一个可实现的方式中,如图2B所示,上述方法在步骤203之后还包括步骤:In another achievable manner, as shown in FIG. 2B , after
204b、接收云端服务器发送的规则,且所述规则不能够与所述当前程序对应的程序行为进行匹配,则向用户发送提示信息。204b. Receive the rule sent by the cloud server, and if the rule cannot match the program behavior corresponding to the current program, send a prompt message to the user.
若当前程序对应的程序行为未与某个规则匹配,则该程序对应的程序行为为不能确定的程序行为,则提示用户,由用户进行相应的处理,如决定放行或拦截等操作,从而实现了对当前程序对应的程序行为的监控。If the program behavior corresponding to the current program does not match a certain rule, the program behavior corresponding to the program is an undetermined program behavior, and the user is prompted, and the user performs corresponding processing, such as deciding to release or intercept, thereby realizing Monitor the program behavior corresponding to the current program.
为了避免设备中的内存空间的大量占用,故需要将未与当前程序对应的程序行为匹配的规则进行删除操作,如图3A所示,上述方法在步骤204a之后还包括如下步骤:In order to avoid a large amount of memory space occupation in the device, it is necessary to delete the rules that do not match the program behavior corresponding to the current program. As shown in FIG. 3A, the above method further includes the following steps after
301a、若所述云端服务器发送的部分规则不匹配监控到的所述当前程序对应的程序行为,则向云端服务器发送与所述部分规则对应的规则撤销请求,以使云端服务器根据所述规则撤销请求发送所述部分规则的删除指令;301a. If the part of the rules sent by the cloud server does not match the monitored program behavior corresponding to the current program, send a rule revocation request corresponding to the part of the rules to the cloud server, so that the cloud server can revoke the rules according to the rules request to send a deletion instruction for the part of the rule;
302a、接收云端服务器发送的删除指令,根据所述删除指令将所述全部规则删除。302a. Receive a deletion instruction sent by the cloud server, and delete all the rules according to the deletion instruction.
举例来说,当云端服务器根据启动某个安装包这一启动程序的下一步执行行为下发运行该安装程序、加载其他应用安装程序等规则时,此时当前程序对应的程序行为为加载了某杀毒或浏览器等其他应用安装程序,此时当前程序的与进行状态已与加载其他应用安装程序的规则匹配了,而运行该安装程序等规则未匹配,为了避免大量规则在设备中占用内存,故向云端服务器发送运行该安装程序等规则的撤销请求。For example, when the cloud server issues rules such as running the installer and loading other application installers according to the next execution behavior of the startup program that starts an installation package, the program behavior corresponding to the current program at this time is to load a certain installation package. Antivirus or other application installation programs such as browsers. At this time, the current status of the program has matched the rules for loading other application installation programs, but the rules such as running the installation program do not match. In order to avoid a large number of rules occupying memory in the device, Therefore, a revocation request for running the installation program and other rules is sent to the cloud server.
在另一个可实现的方式中,上述步骤301a中若所述云端服务器发送的部分规则不匹配监控到的所述当前程序对应的程序行为,在该设备中存储有大量不匹配的规则时,则该设备也可以自行对不匹配的部分规则进行删除,不向云端服务器发送撤销请求。In another achievable manner, in the
如图3B所示,上述方法在步骤204b之后还包括如下步骤:As shown in FIG. 3B, the above method further includes the following steps after
301b、若所述云端服务器发送的全部规则不匹配监控到的所述当前程序对应的程序行为,则向云端服务器发送与所述全部规则对应的规则撤销请求,以使云端服务器根据所述规则撤销请求发送所述全部规则的删除指令;301b. If all the rules sent by the cloud server do not match the monitored program behavior corresponding to the current program, send a rule revocation request corresponding to all the rules to the cloud server, so that the cloud server can revoke the rules according to the rules Request to send a deletion instruction of all the rules;
302b、接收云端服务器发送的删除指令,根据所述删除指令将所述全部规则删除。302b. Receive a deletion instruction sent by the cloud server, and delete all the rules according to the deletion instruction.
举例来说,若当前程序对应的程序行为为加载该安装程序的安装地址的行为,则云端服务器下发的运行该安装程序、加载其他应用安装程序等规则均未匹配,则需向云端服务器发送运行该安装程序、加载其他应用安装程序等全部规则撤销的请求。则此时当前的程序对应的程序行为还可以根据触发标识通过其他防御规则进行监控,也可以向用户发送提示危险的信息,由用户来判断是否进行下一步的操作。For example, if the program behavior corresponding to the current program is the behavior of loading the installation address of the installation program, and the rules issued by the cloud server for running the installation program, loading other application installation programs, etc. do not match, then the cloud server needs to send a message to the cloud server. Running the installer, loading other app installers, etc. All rule revocation requests. At this time, the program behavior corresponding to the current program can also be monitored through other defense rules according to the trigger identifier, and information indicating danger can also be sent to the user, and the user can determine whether to perform the next operation.
在另一个可实现的方式中,上述步骤301b中若所述云端服务器发送的全部规则不匹配监控到的所述当前程序对应的程序行为,在该设备中存储有大量不匹配的规则时,则该设备也可以自行对不匹配的全部规则进行删除,不向云端服务器发送撤销请求。In another achievable manner, in the
如图4所示,在上述204a中在云端服务器发送的规则对所述当前程序对应的程序行为进行监控之后,在所使用的规则使用完成后,即当前程序对应的程序行为已进入下一工作状态时,为了减少规则过多占用设备的内存,影响设备的运行,故还需要将与当前程序对应的程序行为匹配的规则且当前程序已进入下一个工作状态,在不需要使用该规则时,则还需要对已经使用且暂时不再使用的规则进行删除操作。As shown in FIG. 4 , after the rules sent by the cloud server in the above 204a monitor the program behavior corresponding to the current program, after the used rules are used, that is, the program behavior corresponding to the current program has entered the next job In order to reduce the excessive occupation of the device's memory by the rules and affect the operation of the device, it is also necessary to match the rules with the program behavior corresponding to the current program and the current program has entered the next working state. It is also necessary to delete the rules that have been used and are no longer used temporarily.
具体的,包括如下步骤:Specifically, it includes the following steps:
401、接收所述云端服务器发送的用于删除所述设备中不使用规则的规则删除指令,所述规则删除指令包括:所述云端服务器发送到所述设备中的规则删除标识;401. Receive a rule deletion instruction sent by the cloud server for deleting an unused rule in the device, where the rule deletion instruction includes: a rule deletion identifier sent by the cloud server to the device;
具体的,当当前程序已进入下一工作状态时,也可以理解为当前程序的下一个程序对应的程序行为在满足预设的行为触发条件时,即云端服务器接收到满足预设的行为触发条件的规则请求时,此时云端服务器会发送用于删除所述设备中不使用规则的规则删除指令。Specifically, when the current program has entered the next working state, it can also be understood that when the program behavior corresponding to the next program of the current program satisfies the preset behavior trigger condition, that is, the cloud server receives the preset behavior trigger condition. When the rule request is made, the cloud server will send a rule deletion instruction for deleting the unused rules in the device.
402、查找所述设备中与所述规则删除标识匹配的规则,并确定该规则已经不再监控当前程序的程序行为,则根据所述规则删除指令将该规则删除。402. Find a rule in the device that matches the rule deletion identifier, and determine that the rule no longer monitors the program behavior of the current program, and delete the rule according to the rule deletion instruction.
上述步骤将云端服务器下发到设备中的规则进行清理,提高了设备的运行速度。The above steps clean up the rules delivered by the cloud server to the device, thereby improving the running speed of the device.
图5示出了本发明实施例提供的一种规则下发装置,如图5所示,该规则下发装置具体包括:监控模块51、判断模块52、第一发送模块53、第一接收模块54。FIG. 5 shows an apparatus for issuing rules provided by an embodiment of the present invention. As shown in FIG. 5 , the apparatus for issuing rules specifically includes: a
监控模块51,用于监控设备中每一程序对应的程序行为;The
举例来说,所述程序行为包括:进程创建、线程创建、文件读写操作、注册表读写操作、注册表该写操作、堆栈操作、网络通讯、和/或,线程注入的操作。For example, the program behavior includes: process creation, thread creation, file read and write operations, registry read and write operations, registry write operations, stack operations, network communication, and/or thread injection operations.
判断模块52,用于采用预设的行为触发条件判断当前程序对应的程序行为是否符合规则触发标识;The
具体的,所述预设的行为触发条件为云端服务器根据多个设备中的程序对应的程序行为统计的;所述预设的行为触发条件为所述云端服务器根据多个设备中的程序对应的程序行为统计后预先向所述设备发送的;所述预设的行为触发条件包括该设备中所有程序对应的程序行为的条件;Specifically, the preset behavior triggering conditions are calculated by the cloud server according to program behaviors corresponding to programs in multiple devices; the preset behavior triggering conditions are statistics corresponding to programs in multiple devices by the cloud server Sent to the device in advance after the program behavior is counted; the preset behavior triggering conditions include the program behavior conditions corresponding to all programs in the device;
所述行为触发条件中包括:每一程序对应的程序行为,和与该程序行为对应的规则触发标识。The behavior triggering conditions include: program behaviors corresponding to each program, and rule triggering identifiers corresponding to the program behaviors.
第一发送模块53,用于在所述程序对应的程序行为符合所述规则触发标识时,向服务器发送规则请求,以使服务器根据所述规则请求查找与该规则触发标识对应的规则;The
上述服务器可以为云端服务器。The above server may be a cloud server.
第一接收模块54,用于接收云端服务器发送的规则,采用所述云端服务器发送的规则对所述当前程序对应的程序行为进行监控。The
举例来说,接收云服务器发送的规则为防御规则、文件防御规则、拦截规则、数据处理规则。For example, the rules sent by the receiving cloud server are defense rules, file defense rules, interception rules, and data processing rules.
在另一个可能实现的方式中,图6示出了本发明实施例提供的一种规则下发装置,如图6所示,该规则下发装置具体包括:监控模块61、判断模块62、第一发送模块63、第一接收模块64、第二发送模块65、第二接收模块66。In another possible implementation manner, FIG. 6 shows a rule issuing apparatus provided by an embodiment of the present invention. As shown in FIG. 6 , the rule issuing apparatus specifically includes: a
监控模块61,用于监控设备中每一程序对应的程序行为;The
判断模块62,用于采用预设的行为触发条件判断当前程序对应的程序行为是否符合规则触发标识;The
第一发送模块63,用于在所述程序对应的程序行为符合所述规则触发标识时,向云端服务器发送规则请求,以使云端服务器根据所述规则请求查找与该规则触发标识对应的规则;The
第一接收模块64,用于接收云端服务器发送的规则,且所述规则能够与所述当前程序对应的程序行为进行匹配,则采用所述云端服务器发送的规则对所述当前程序对应的程序行为进行监控。The
所述第二发送模块65,用于在所述云端服务器发送的部分规则不匹配监控到的所述当前程序对应的程序行为时,向云端服务器发送与所述部分规则对应的规则撤销请求,以使云端服务器根据所述规则撤销请求发送所述部分规则的删除指令;The
所述第二接收模块66,用于接收云端服务器发送的删除指令,根据所述删除指令将所述部分规则删除。The
在另一种可实现的方式中,上述装置中的第一接收模块64、第二发送模块65和第二接收模块66还具体需要用于以下功能。In another achievable manner, the
第一接收模块64,用于接收云端服务器发送的规则,且所述规则不能够与所述当前程序对应的程序行为进行匹配,则向用户发送提示信息。The
具体的,若当前程序对应的程序行为未与某个规则匹配,则该程序对应的程序行为为不能确定的程序行为,则提示用户,由用户进行相应的处理,如决定放行或拦截等操作,从而实现了对当前程序对应的程序行为的监控。Specifically, if the program behavior corresponding to the current program does not match a certain rule, the program behavior corresponding to the program is an indeterminate program behavior, and the user is prompted, and the user performs corresponding processing, such as deciding to release or intercept operations, etc. Thus, the monitoring of the program behavior corresponding to the current program is realized.
所述第二发送模块65,用于在所述云端服务器发送的全部规则不匹配监控到的所述当前程序对应的程序行为时,向云端服务器发送与所述全部规则对应的规则撤销请求,以使云端服务器根据所述规则撤销请求发送所述全部规则的删除指令;The
所述第二接收模块66,用于接收云端服务器发送的删除指令,根据所述删除指令将所述全部规则删除。The
图7示出了本发明实施例提供的一种规则下发装置,如图7所示,该规则下发装置具体包括:监控模块71、判断模块72、第一发送模块73、第一接收模块74、第三接收模块75、确定模块76。FIG. 7 shows an apparatus for issuing rules provided by an embodiment of the present invention. As shown in FIG. 7 , the apparatus for issuing rules specifically includes: a
监控模块71,用于监控设备中每一程序对应的程序行为;The
判断模块72,用于采用预设的行为触发条件判断当前程序对应的程序行为是否符合规则触发标识;The
第一发送模块73,用于在所述程序行为符合所述规则触发标识时,向云端服务器发送规则请求,以使云端服务器根据所述规则请求查找与该规则触发标识对应的规则;The
第一接收模块74,用于接收云端服务器发送的规则,且所述规则能够与所述当前程序对应的程序行为进行匹配,则采用所述云端服务器发送的规则对所述当前程序对应的程序行为进行监控。The
第三接收模块75,用于接收所述云端服务器发送的用于删除所述设备中不使用规则的规则删除指令,所述规则删除指令包括:所述云端服务器发送到所述设备中的规则删除标识;The
确定模块76,用于查找所述设备中与所述规则删除标识匹配的规则,并确定该规则已经不再监控当前程序的程序行为,则根据所述规则删除指令将该规则删除。The determining
上述装置与上述方法是一一对应的,本发明对上述方法实施例的详细说明也同样适用于对装置的详细说明,本发明不对上述装置进行详细说明。The above-mentioned apparatus and the above-mentioned method are in one-to-one correspondence, and the detailed description of the above-mentioned method embodiments in the present invention is also applicable to the detailed description of the apparatus, and the present invention does not provide a detailed description of the above-mentioned apparatus.
本发明的说明书中,说明了大量具体细节。然而,能够理解,本发明的实施例可以在没有这些具体细节的情况下实践。在一些实例中,并未详细示出公知的方法、结构和技术,以便不模糊对本说明书的理解。In the description of the present invention, numerous specific details are set forth. It will be understood, however, that embodiments of the invention may be practiced without these specific details. In some instances, well-known methods, structures and techniques have not been shown in detail in order not to obscure an understanding of this description.
类似地,应当理解,为了精简本发明公开并帮助理解各个发明方面中的一个或多个,在上面对本发明的示例性实施例的描述中,本发明的各个特征有时被一起分组到单个实施例、图、或者对其的描述中。然而,并不应将该公开的方法解释呈反映如下意图:即所要求保护的本发明要求比在每个权利要求中所明确记载的特征更多的特征。更确切地说,如下面的权利要求书所反映的那样,发明方面在于少于前面公开的单个实施例的所有特征。因此,遵循具体实施方式的权利要求书由此明确地并入该具体实施方式,其中每个权利要求本身都作为本发明的单独实施例。Similarly, it is to be understood that in the above description of exemplary embodiments of the invention, various features of the invention are sometimes grouped together into a single embodiment in order to simplify the present disclosure and to aid in the understanding of one or more of the various aspects of the invention. , figures, or descriptions thereof. However, this method of disclosure should not be construed to reflect the intention that the invention as claimed requires more features than are expressly recited in each claim. Rather, as the following claims reflect, inventive aspects lie in less than all features of a single foregoing disclosed embodiment. Thus, the claims following the Detailed Description are hereby expressly incorporated into this Detailed Description, with each claim standing on its own as a separate embodiment of this invention.
本领域技术人员可以理解,可以对实施例中的设备中的模块进行自适应性地改变并且把它们设置在于该实施例不同的一个或多个设备中。可以把实施例中的模块或单元或组件组合成一个模块或单元或组件,以及此外可以把它们分成多个子模块或子单元或子组件。除了这样的特征和/或过程或者单元中的至少一些是互相排斥之处,可以采用任何组合对本说明书(包括伴随的权利要求、摘要和附图)中公开的所有特征以及如此公开的任何方法或者设备的所有过程或单元进行组合。除非另外明确陈述,本说明书(包括伴随的权利要求、摘要和附图)中公开的每个特征可以由提供相同、等同或相似目的的替代特征来代替。Those skilled in the art can understand that the modules in the device in the embodiment can be adaptively changed and arranged in one or more devices different in the embodiment. The modules or units or components in the embodiments may be combined into one module or unit or component, and further they may be divided into multiple sub-modules or sub-units or sub-assemblies. All features disclosed in this specification (including accompanying claims, abstract and drawings) and any method so disclosed may be employed in any combination, except to the extent that at least some of such features and/or procedures or elements are mutually exclusive. All processes or units of equipment are combined. Each feature disclosed in this specification (including accompanying claims, abstract and drawings) may be replaced by alternative features serving the same, equivalent or similar purpose, unless expressly stated otherwise.
此外,本领域的技术人员能够理解,尽管在此所述的一些实施例包括其它实施例中所包括的某些特征而不是其它特征,但是不同实施例的特征的组合意味着处于本发明的范围之内并且形成不同的实施例。例如,在下面的权利要求书中,所要求保护的实施例的任意之一都可以以任意的组合方式来使用。Furthermore, those skilled in the art will appreciate that although some of the embodiments described herein include certain features, but not others, included in other embodiments, that combinations of features of different embodiments are intended to be within the scope of the invention within and form different embodiments. For example, in the following claims, any of the claimed embodiments may be used in any combination.
本发明的各个部件实施例可以以硬件实现,或者以在一个或者多个处理器上运行的软件模块实现,或者以它们的组合实现。本领域的技术人员应当理解,可以在实践中使用微处理器或者数字信号处理器(DSP)来实现根据本发明实施例的一种浏览器终端的设备中的一些或者全部部件的一些或者全部功能。本发明还可以实现为用于执行这里所描述的方法的一部分或者全部的设备或者装置程序(例如,计算机程序和计算机程序产品)。这样的实现本发明的程序可以存储在计算机可读介质上,或者可以具有一个或者多个信号的形式。这样的信号可以从因特网网站上下载得到,或者在载体信号上提供,或者以任何其他形式提供。Various component embodiments of the present invention may be implemented in hardware, or in software modules running on one or more processors, or in a combination thereof. Those skilled in the art should understand that, in practice, a microprocessor or a digital signal processor (DSP) may be used to implement some or all functions of some or all components in a device for a browser terminal according to an embodiment of the present invention . The present invention can also be implemented as apparatus or apparatus programs (eg, computer programs and computer program products) for performing part or all of the methods described herein. Such a program implementing the present invention may be stored on a computer-readable medium, or may be in the form of one or more signals. Such signals may be downloaded from Internet sites, or provided on carrier signals, or in any other form.
应该注意的是上述实施例对本发明进行说明而不是对本发明进行限制,并且本领域技术人员在不脱离所附权利要求的范围的情况下可设计出替换实施例。在权利要求中,不应将位于括号之间的任何参考符号构造成对权利要求的限制。单词“包含”不排除存在未列在权利要求中的元件或步骤。位于元件之前的单词“一”或“一个”不排除存在多个这样的元件。本发明可以借助于包括有若干不同元件的硬件以及借助于适当编程的计算机来实现。在列举了若干装置的单元权利要求中,这些装置中的若干个可以是通过同一个硬件项来具体体现。单词第一、第二、以及第三等的使用不表示任何顺序。可将这些单词解释为名称。It should be noted that the above-described embodiments illustrate rather than limit the invention, and that alternative embodiments may be devised by those skilled in the art without departing from the scope of the appended claims. In the claims, any reference signs placed between parentheses shall not be construed as limiting the claim. The word "comprising" does not exclude the presence of elements or steps not listed in a claim. The word "a" or "an" preceding an element does not exclude the presence of a plurality of such elements. The invention can be implemented by means of hardware comprising several different elements and by means of a suitably programmed computer. In a unit claim enumerating several means, several of these means may be embodied by one and the same item of hardware. The use of the words first, second, and third, etc. do not denote any order. These words can be interpreted as names.
最后应说明的是:以上各实施例仅用以说明本发明的技术方案,而非对其限制;尽管参照前述各实施例对本发明进行了详细的说明,本领域的普通技术人员应当理解:其依然可以对前述各实施例所记载的技术方案进行修改,或者对其中部分或者全部技术特征进行等同替换;而这些修改或者替换,并不使相应技术方案的本质脱离本发明各实施例技术方案的范围,其均应涵盖在本发明的权利要求和说明书的范围当中。Finally, it should be noted that the above embodiments are only used to illustrate the technical solutions of the present invention, but not to limit them; although the present invention has been described in detail with reference to the foregoing embodiments, those of ordinary skill in the art should understand that: The technical solutions described in the foregoing embodiments can still be modified, or some or all of the technical features thereof can be equivalently replaced; and these modifications or replacements do not make the essence of the corresponding technical solutions deviate from the technical solutions of the embodiments of the present invention. The scope of the invention should be included in the scope of the claims and description of the present invention.
Claims (6)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201410806644.XACN105791221B (en) | 2014-12-22 | 2014-12-22 | Method and device for issuing rules |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201410806644.XACN105791221B (en) | 2014-12-22 | 2014-12-22 | Method and device for issuing rules |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN105791221A CN105791221A (en) | 2016-07-20 |
| CN105791221Btrue CN105791221B (en) | 2020-06-05 |
Family
ID=56385306
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN201410806644.XAActiveCN105791221B (en) | 2014-12-22 | 2014-12-22 | Method and device for issuing rules |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN105791221B (en) |
Families Citing this family (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| TWI608377B (en)* | 2017-04-13 | 2017-12-11 | 廣達電腦股份有限公司 | Monitoring management system and method |
| CN109376193B (en)* | 2018-09-29 | 2023-04-28 | 北京友友天宇系统技术有限公司 | Data exchange system based on self-adaptive rule |
| CN111913847B (en)* | 2020-07-21 | 2021-04-27 | 上海冰鉴信息科技有限公司 | Method and system for acquiring remote task execution progress |
Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN103401845A (en)* | 2013-07-15 | 2013-11-20 | Tcl集团股份有限公司 | Detection method and device for website safety |
| CN103617395A (en)* | 2013-12-06 | 2014-03-05 | 北京奇虎科技有限公司 | Method, device and system for intercepting advertisement programs based on cloud security |
| CN104135479A (en)* | 2014-07-29 | 2014-11-05 | 腾讯科技(深圳)有限公司 | Cloud real-time defense method and system |
- 2014
- 2014-12-22CNCN201410806644.XApatent/CN105791221B/enactiveActive
Patent Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN103401845A (en)* | 2013-07-15 | 2013-11-20 | Tcl集团股份有限公司 | Detection method and device for website safety |
| CN103617395A (en)* | 2013-12-06 | 2014-03-05 | 北京奇虎科技有限公司 | Method, device and system for intercepting advertisement programs based on cloud security |
| CN104135479A (en)* | 2014-07-29 | 2014-11-05 | 腾讯科技(深圳)有限公司 | Cloud real-time defense method and system |
Also Published As
| Publication number | Publication date |
|---|---|
| CN105791221A (en) | 2016-07-20 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US11657152B2 (en) | Methods for behavioral detection and prevention of cyberattacks, and related apparatus and techniques | |
| CN109684832B (en) | System and method for detecting malicious files | |
| CN109583193B (en) | System and method for cloud detection, investigation and elimination of target attacks | |
| US10282548B1 (en) | Method for detecting malware within network content | |
| EP2839406B1 (en) | Detection and prevention of installation of malicious mobile applications | |
| CN103180863B (en) | Computer system analysis method and apparatus | |
| CN103559446B (en) | Dynamic virus detection method and device for equipment based on Android system | |
| CN102902919B (en) | A kind of identifying processing methods, devices and systems of suspicious operation | |
| US8739284B1 (en) | Systems and methods for blocking and removing internet-traversing malware | |
| KR101607951B1 (en) | Dynamic cleaning for malware using cloud technology | |
| Zheng et al. | Droidray: a security evaluation system for customized android firmwares | |
| CN102882875B (en) | Active defense method and device | |
| US20140096246A1 (en) | Protecting users from undesirable content | |
| CN112106047A (en) | Anti-lux software system and method using countersinks at electronic devices | |
| WO2014121713A1 (en) | Url interception processing method, device and system | |
| CN106716432A (en) | Pre-launch Process Vulnerability Assessment | |
| CN103714292B (en) | A kind of detection method of vulnerability exploit code | |
| JP6030566B2 (en) | Unauthorized application detection system and method | |
| CN103617395A (en) | Method, device and system for intercepting advertisement programs based on cloud security | |
| WO2015007224A1 (en) | Malicious program finding and killing method, device and server based on cloud security | |
| CN112910895B (en) | Network attack behavior detection method and device, computer equipment and system | |
| CN113824678B (en) | System, method, and non-transitory computer readable medium for processing information security events | |
| WO2023124041A1 (en) | Ransomware detection method and related system | |
| CN105095758A (en) | Processing method and device for lock-screen application program and mobile terminal | |
| US8640242B2 (en) | Preventing and detecting print-provider startup malware |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| C06 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant | ||
| CP01 | Change in the name or title of a patent holder | ||
| CP01 | Change in the name or title of a patent holder | Address after:100088 room 112, block D, 28 new street, new street, Xicheng District, Beijing (Desheng Park) Patentee after:BEIJING QIHOO TECHNOLOGY Co.,Ltd. Patentee after:Beijing Qizhi Business Consulting Co.,Ltd. Address before:100088 room 112, block D, 28 new street, new street, Xicheng District, Beijing (Desheng Park) Patentee before:BEIJING QIHOO TECHNOLOGY Co.,Ltd. Patentee before:Qizhi software (Beijing) Co.,Ltd. | |
| TR01 | Transfer of patent right | ||
| TR01 | Transfer of patent right | Effective date of registration:20220324 Address after:1773, floor 17, floor 15, building 3, No. 10, Jiuxianqiao Road, Chaoyang District, Beijing 100015 Patentee after:Sanliu0 Digital Security Technology Group Co.,Ltd. Address before:100088 room 112, block D, 28 new street, new street, Xicheng District, Beijing (Desheng Park) Patentee before:BEIJING QIHOO TECHNOLOGY Co.,Ltd. Patentee before:Beijing Qizhi Business Consulting Co.,Ltd. |