CN103856332A - Implementation method of one-to-multiple account mapping binding of convenient and rapid multi-screen multi-factor WEB identity authentication - Google Patents
Implementation method of one-to-multiple account mapping binding of convenient and rapid multi-screen multi-factor WEB identity authenticationDownload PDFInfo
- Publication number
- CN103856332A CN103856332ACN201410109452.3ACN201410109452ACN103856332ACN 103856332 ACN103856332 ACN 103856332ACN 201410109452 ACN201410109452 ACN 201410109452ACN 103856332 ACN103856332 ACN 103856332A
- Authority
- CN
- China
- Prior art keywords
- account
- user
- binding
- information
- spid
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
- 238000000034methodMethods0.000titleclaimsabstractdescription59
- 238000013507mappingMethods0.000titleclaimsabstractdescription38
- 238000012795verificationMethods0.000claimsabstractdescription47
- 230000008569processEffects0.000claimsabstractdescription36
- 230000004913activationEffects0.000claimsdescription7
- 238000005516engineering processMethods0.000claimsdescription7
- YSCNMFDFYJUPEF-OWOJBTEDSA-N4,4'-diisothiocyano-trans-stilbene-2,2'-disulfonic acidChemical compoundOS(=O)(=O)C1=CC(N=C=S)=CC=C1\C=C\C1=CC=C(N=C=S)C=C1S(O)(=O)=OYSCNMFDFYJUPEF-OWOJBTEDSA-N0.000claimsdescription4
- 238000007726management methodMethods0.000abstractdescription9
- 230000006870functionEffects0.000description10
- 238000013475authorizationMethods0.000description9
- 230000008901benefitEffects0.000description7
- 238000010586diagramMethods0.000description3
- 230000005540biological transmissionEffects0.000description2
- 238000013461designMethods0.000description2
- 238000000060site-specific infrared dichroism spectroscopyMethods0.000description2
- 230000003068static effectEffects0.000description2
- 238000004364calculation methodMethods0.000description1
- 238000004891communicationMethods0.000description1
- 230000007812deficiencyEffects0.000description1
- 238000011161developmentMethods0.000description1
- 238000002955isolationMethods0.000description1
- 230000007246mechanismEffects0.000description1
- 238000003032molecular dockingMethods0.000description1
- 230000006855networkingEffects0.000description1
- 238000012545processingMethods0.000description1
- 238000012360testing methodMethods0.000description1
Images
Landscapes
- Information Transfer Between Computers (AREA)
- Mobile Radio Communication Systems (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明属于信息安全领域的身份认证领域,具体涉及到一种多屏多因子便捷WEB身份认证的一对多账号映射绑定的实现方法。The invention belongs to the field of identity authentication in the field of information security, and in particular relates to a method for realizing one-to-many account mapping and binding of multi-screen, multi-factor convenient WEB identity authentication.
背景技术Background technique
随着网络的发展和互联网的普及(桌面服务的网络化),用户在获得网络服务的同时将拥有大量的账号。调查表明:如果一个用户拥有30个账号,则该用户会使用5个或者6个密码,而且用户总是采用尝试的方法进行登陆,即尝试每一个密码登陆直到登陆成功,或者是使用重置密码功能登陆。这样用户将会耗费大量的时间在登录过程中,并且由于网站登录策略的限制会耗费更长的时间,即有些网站要求在输入几次错误密码后,需要填写验证码。随着越来越多的网络服务的涌现,如果用户在登陆每个网站都需使用不同的密码,这将是对用户记忆力的一大考验。With the development of the network and the popularization of the Internet (networking of desktop services), users will have a large number of accounts while obtaining network services. The survey shows that if a user has 30 accounts, the user will use 5 or 6 passwords, and the user always uses the method of trying to log in, that is, try every password to log in until the login is successful, or reset the password Function login. In this way, the user will spend a lot of time in the login process, and it will take a longer time due to the restrictions of the website login strategy, that is, some websites require to fill in the verification code after entering the wrong password several times. With the emergence of more and more network services, if users need to use different passwords to log in to each website, this will be a big test for users' memory.
单点登录(Single Sign-On,简称SSO)可大大简化用户登陆网站的过程:它允许用户使用同一个身份提供者(Identity Provider,简称IDP)的账户登录各服务提供商(Service Provider,简称SP)的网站,使用户从在多个网站注册账号和使用多个密码的记忆中解脱出来。因此,SSO具有使用户记忆较少的密码、一点登陆,全域漫游、用户体验性好等优点。但是,传统SSO登陆方式并没有从本质上解决用户高安全登陆的问题,只是将用户能否安全便捷登陆SP转化为能否安全登陆IDP,一旦IDP登陆账号被人窃取,该IDP绑定的其他SP网络服务就会被人盗用,使用户数据面临着严重的安全威胁。Single sign-on (Single Sign-On, referred to as SSO) can greatly simplify the process of users logging in to the website: it allows users to use the same identity provider (Identity Provider, referred to as IDP) account to log in to each service provider (Service Provider, referred to as SP ) website, freeing users from the memory of registering accounts on multiple websites and using multiple passwords. Therefore, SSO has the advantages of less passwords for users to remember, one-point login, global roaming, and good user experience. However, the traditional SSO login method does not essentially solve the problem of high-security login for users. It only converts whether the user can safely and conveniently log in to the SP into whether the user can log in to the IDP safely. Once the IDP login account is stolen, other users bound to the IDP SP network service will be stolen, so that user data is facing serious security threats.
传统增强的身份认证方式,一般采用两步身份认证,即在服务器端通过验证用户知道的信息(something know)、用户拥有的信息(something have)、用户自身信息(something are)中的两到三项完成多因子认证来提高认证的安全等级。若用户在连接服务器的过程中信道被劫持,再多的认证因子信息也会通过被劫持信道泄露,给用户带来潜在的安全隐患。The traditional enhanced identity authentication method generally adopts two-step identity authentication, that is, through verification on the server side, two to three of the information the user knows (something know), the information the user has (something have), and the user's own information (something are) Items complete multi-factor authentication to improve the security level of authentication. If the user's channel is hijacked during the process of connecting to the server, no amount of authentication factor information will be leaked through the hijacked channel, bringing potential security risks to the user.
发明内容Contents of the invention
本发明技术解决问题:克服现有技术的不足,提供一种多屏多因子便捷WEB身份认证的一对多账号映射绑定的实现方法,在保证用户身份认证操作便捷的情况下,大大的提高了认证过程中信息的安全性。The technical problem of the present invention is to overcome the deficiencies of the prior art, and provide a method for realizing the one-to-many account mapping and binding of multi-screen and multi-factor convenient WEB identity authentication, which greatly improves user identity authentication while ensuring convenient operation. The security of information during the authentication process is ensured.
本发明技术解决方案:在保证用户身份认证高安全与操作便捷的前提下,在多屏多因子身份认证(即用户首先移动智能终端设备完成本地敏感信息验证,验证通过后,在服务器端完成基于一次性密码OTP(One Time Password,简称OTP)验证)中通过身份提供者IDP账号与服务提供商SP服务账号的一对多双向关联和身份提供者IDP账号与设备账号(DeviceIdentity,简称DID)的一对多双向关联,完成一种新型的SSO账号映射管理方法,从而实现将多SP的登陆过程变为使用多DID中的任意一个完成单点登录过程。The technical solution of the present invention: on the premise of ensuring high security and convenient operation of user identity authentication, in multi-screen multi-factor identity authentication (that is, the user first moves the smart terminal device to complete local sensitive information verification, after the verification is passed, complete the authentication based on One-time password OTP (One Time Password, referred to as OTP) verification) through the one-to-many two-way association between the identity provider IDP account and the service provider SP service account and the identity provider IDP account and device account (DeviceIdentity, referred to as DID) One-to-many two-way association, completes a new type of SSO account mapping management method, so as to realize the login process of multiple SPs to use any one of multiple DIDs to complete the single sign-on process.
本发明具体实现步骤如下:The concrete realization steps of the present invention are as follows:
(1)首先建立三层账号体系(1) First establish a three-tier account system
借助三层账号体系,完成对设备、用户、服务三个层面的关联,所述三层账号体系分别是设备账号DID、用户账号UID和服务账号SPID,分别对应设备层(DID)、用户层(UID)和服务层(SPID);其中:With the help of a three-tier account system, the association of devices, users, and services is completed. The three-tier account system is the device account DID, user account UID, and service account SPID, which correspond to the device layer (DID), user layer ( UID) and Service Layer (SPID); where:
设备账号DID作为移动智能终端设备的识别信息,起到标识用户拥有该设备的作用,由移动智能终端设备在设备仓库服务器VS上通过证书激活技术获得;DID信息由两部分信息共同组成,一部分为移动智能终端设备拥有者信息,保存在移动智能终端本地安全存储区上;另一部分为移动智能终端设备本身信息,保存在设备仓库服务器VS上;用户信息利用本地设备映射关系,直接跟DID信息关联,设备仓库服务器VS上只存储设备信息;The device account DID, as the identification information of the mobile smart terminal device, plays the role of identifying the user owning the device, and is obtained by the mobile smart terminal device through the certificate activation technology on the device warehouse server VS; the DID information is composed of two parts of information, one part is The owner information of the mobile smart terminal device is stored in the local security storage area of the mobile smart terminal; the other part is the information of the mobile smart terminal device itself, which is stored on the device warehouse server VS; the user information is directly associated with the DID information using the local device mapping relationship , only device information is stored on the device warehouse server VS;
用户账号UID作为用户在WS的账号,是用户的身份,由用户在认证服务器WS上注册获得,UID信息保存在认证服务器WS,为DID与SPID关联的中间件,是三层账号体系的实施的基础;User account UID, as the user's account in WS, is the user's identity. It is obtained by the user's registration on the authentication server WS. The UID information is stored in the authentication server WS. It is the middleware associated with DID and SPID, and it is the implementation of the three-tier account system. Base;
服务账号SPID为用户的服务账号,由SP提供;SPID的注册在SP端进行,同时SPID的信息保存在SP服务器上,SPID的服务权限由SP提供管理;The service account SPID is the user's service account, provided by the SP; the registration of the SPID is carried out on the SP side, and the information of the SPID is saved on the SP server, and the service authority of the SPID is provided and managed by the SP;
(2)三层账号映射绑定及使用(2) Three-tier account mapping binding and use
三层账号映射绑定的方式为多个DID映射绑定到一个UID,一个UID映射绑定到多个SPID上,即通过设备证书激活技术获得设备层标识、在服务提供商SP处获得用户服务层标识、在认证服务器用户注册获得用户层标识,并在该层实现用户三层账号体系下的映射关联,用户在完成三层账号体系映射绑定后,要获得服务提供商SP提供的服务时,首先在通过本地设备层验证后,将移动智能终端的DID及包括OTP信息的其它信息发送给认证服务器WS,认证服务器WS从中找到DID对应的UID,再根据用户UID对应的要登录的服务提供商提供的服务选择对应的服务层账号SPID,认证服务器WS将相关信息发送给SP服务器,完成用户要享受服务的认证登录过程;The three-tier account mapping and binding method is that multiple DIDs are mapped to one UID, and one UID is mapped to multiple SPIDs, that is, the device layer identification is obtained through the device certificate activation technology, and user services are obtained from the service provider SP. Layer identification, user registration on the authentication server to obtain the user layer identification, and realize the mapping and association under the user's three-tier account system at this layer. After the user completes the mapping and binding of the three-tier account system, when the user wants to obtain the service provided by the service provider SP , first, after passing the local device layer verification, send the DID of the mobile smart terminal and other information including OTP information to the authentication server WS, from which the authentication server WS finds the UID corresponding to the DID, and then provides the service to be logged in according to the user UID. The service provided by the provider selects the corresponding service layer account SPID, and the authentication server WS sends the relevant information to the SP server to complete the authentication and login process for the user to enjoy the service;
(3)三层账号体系下账号映射绑定后的登陆过程(3) The login process after account mapping and binding under the three-tier account system
(31)移动智能终端注册(31) Mobile smart terminal registration
在移动智能终端设备上安装客户端,首次运行时在设备仓库服务器VS上注册设备账号DID;Install the client on the mobile smart terminal device, and register the device account DID on the device warehouse server VS when running for the first time;
(32)用户在移动智能终端上注册(32) The user registers on the mobile smart terminal
用户在使用移动智能终端设备时,在移动智能终端本地上注册用户信息,然后完成与设备账号DID的绑定;When using a mobile smart terminal device, the user registers user information locally on the mobile smart terminal, and then completes the binding with the device account DID;
(33)用户注册用户账号(33) User registration user account
用户在认证服务器WS上注册用户账号UID;The user registers the user account UID on the authentication server WS;
(34)设备账号DID绑定用户账号UID(34) Device account DID is bound to user account UID
用户完成步骤(33)时,需要绑定到DID上,这时需要用户继续完成绑定过程,然后选择绑定UID,浏览器安全插件会启动本地Wi-Fi,将Wi-Fi连接信息以QR码的形式展现给用户,用户通过移动智能终端的QR码扫描功能,读取传入信息建立与浏览器插件的无线互联,同时传送DID信息及OTP信息经浏览器插件转发给WS,验证通过后完成绑定;When the user completes step (33), he needs to bind to the DID. At this time, the user needs to continue to complete the binding process, and then choose to bind the UID. The browser security plug-in will start the local Wi-Fi, and the Wi-Fi connection information will be sent to QR The user reads the incoming information through the QR code scanning function of the mobile smart terminal to establish a wireless connection with the browser plug-in, and at the same time transmits the DID information and OTP information to the WS through the browser plug-in. After the verification is passed Complete the binding;
(35)设备账号DID绑定服务账号SPID(35) Device account DID binding service account SPID
用户完成步骤(34)时,即完成了账号的基本绑定过程;每当用户访问服务提供商SP时,通过本地验证和SP服务器验证后,会根据DID找对应SP绑定的SPID,如没有绑定,跳转到初始SPID绑定,绑定过程为先通过SPID的账号和密码完成登录,登陆后SPID将SPID和安全断言发送给认证服务器WS,认证服务器WS依据断言和SPID与UID的对应关系完成绑定;若已绑定,WS发送安全断言和SPID信息至SP服务器,完成认证登录过程。When the user completes step (34), the basic binding process of the account is completed; whenever the user accesses the service provider SP, after passing the local authentication and the SP server authentication, the SPID corresponding to the SP binding will be found according to the DID, if there is no Binding, jump to the initial SPID binding, the binding process is to complete the login through the SPID account and password first, after login, the SPID sends the SPID and security assertion to the authentication server WS, and the authentication server WS is based on the assertion and the correspondence between SPID and UID The relationship is bound; if it is bound, WS sends the security assertion and SPID information to the SP server to complete the authentication and login process.
所述步骤(31)中,首次运行客户端需要完成设备在设备仓库服务器VS上注册,若VS上已有注册,跳过在VS上注册过程,并通知用户设备已注册过,可继续使用。In the step (31), when running the client for the first time, the device needs to be registered on the device warehouse server VS. If the VS has already been registered, the registration process on the VS will be skipped, and the user will be notified that the device has been registered and can continue to be used.
所述步骤(32)中,绑定信息存于移动智能终端本地,目的是为用户将输入自己的本地账号信息留在移动智能终端以完成本地验证,验证通过完成第一层验证,设备启动OTP产生过程以完成后续验证;若本地验证不通过,则要求重新验证直至成功。In the step (32), the binding information is stored locally in the mobile smart terminal, the purpose is for the user to leave the inputted local account information in the mobile smart terminal to complete the local verification. After the verification is passed, the first layer of verification is completed, and the device starts the OTP A process is generated to complete the subsequent verification; if the local verification fails, re-authentication is required until it succeeds.
所述步骤(34)中,如果验证不通过则绑定失败,回滚到UID注册前,防止出现单独的UID无DID绑定的情况,带来潜在威胁。In the step (34), if the verification fails, the binding fails, and the UID is rolled back before the registration to prevent a single UID without DID binding and potential threats.
所述步骤(35)中,安全断言分别为SP服务器和认证服务器WS分别产生,所有的验证不通过都会导致步骤(35)失败,要求重新执行。In the step (35), the security assertion is generated by the SP server and the authentication server WS respectively, and all verification failures will result in the failure of the step (35), requiring re-execution.
下面简要介绍本方案的基本原理。The basic principle of this scheme is briefly introduced below.
方面一,设备账号DID。DID作为用户的移动智能终端设备识别标志,起到标识用户拥有该设备的作用,由移动终端设备在设备仓库服务器VS上注册,通过设备证书激活技术获得设备账号信息(如设备证书等)。DID账号信息由两部分组成,一部分为用户静态敏感信息保存在移动终端;另一部分为移动终端设备信息保存在设备仓库服务器VS。这两部分信息存在一种映射关联关系。其优点在于:(1)服务器并不知道具体使用者的身份,只能识别可信设备,即通过可信设备的身份起到标识用户账号身份的作用,从而保护了用户身份的隐私安全;(2)设备账号对移动终端有识别功能,为后期增强的身份认证信息比对,起到用户信息与移动终端映射关联作用。On the one hand, the device account DID. DID, as the identification mark of the user's mobile smart terminal device, plays the role of identifying the user owning the device. The mobile terminal device is registered on the device warehouse server VS, and the device account information (such as device certificate, etc.) is obtained through the device certificate activation technology. The DID account information consists of two parts, one part is the user static sensitive information stored in the mobile terminal; the other part is the mobile terminal device information stored in the device warehouse server VS. There is a mapping relationship between these two parts of information. Its advantages are: (1) The server does not know the identity of the specific user, but can only identify the trusted device, that is, the identity of the trusted device can identify the identity of the user account, thereby protecting the privacy and security of the user's identity; ( 2) The device account has the function of identifying the mobile terminal, which is used for the comparison of identity authentication information enhanced in the later stage, and plays the role of mapping the user information and the mobile terminal.
方面二,用户账号UID。用户账号UID作为三层账号体系的中间件,起到了三层账号间连接桥梁的作用,由用户在认证服务器WS上注册获得用户账号信息。这层账号存在的好处在于:将映射绑定控制权交予认证服务器WS的账号管理模块处理,实现用户账号UID与设备账号DID一对多的映射绑定及关联解锁、用户账户UID与服务账号SPID一对多的映射绑定及关联解锁,提供更好的使用体验和对高兼容性的支持。The second aspect is the user account UID. As the middleware of the three-tier account system, the user account UID acts as a bridge between the three-tier accounts, and the user registers on the authentication server WS to obtain user account information. The advantage of the existence of this layer of accounts is that the mapping and binding control rights are handed over to the account management module of the authentication server WS to realize the one-to-many mapping binding and associated unlocking of user account UID and device account DID, and the user account UID and service account SPID one-to-many mapping binding and associated unlocking provide better user experience and support for high compatibility.
方面三,服务账号SPID。SPID为用户的服务账号,由服务提供商SP提供。SPID的注册在服务提供商SP的服务器端完成,同时SPID的信息保存在SP服务器上,SPID的服务权限由SP进行管理。三层账号体系下UID账号关联服务账号SPID,SPID作为用户网络服务可识别的信息,既保证服务控制权保留在SP,使SP可通过黑名单来拒绝用户的服务请求,又确保SP不进行改动,降低了与SP对接的代价和安全风险,增加了系统部署的便捷性。Aspect three, the service account SPID. The SPID is the user's service account and is provided by the service provider SP. The registration of the SPID is completed on the server side of the service provider SP, and the information of the SPID is saved on the SP server at the same time, and the service authority of the SPID is managed by the SP. Under the three-tier account system, the UID account is associated with the service account SPID, and the SPID is used as the identifiable information of the user's network service, which not only ensures that the service control right is reserved in the SP, but also enables the SP to reject the user's service request through the blacklist, and ensures that the SP does not make changes , which reduces the cost and security risk of connecting with the SP, and increases the convenience of system deployment.
本发明提出的一种多屏多因子便捷WEB身份认证的一对多账号映射绑定的实现方法,需要用户在FIDO(Fast Identity Online,简称FIDO,快速身份认证联盟)基础框架之上利用多屏多因子认证机制内提供的FIDO-IDP(FIDO身份提供者)网站内注册一个属于自己的FIDO用户账号UID,然后将所使用的网络服务账号与该账号绑定。用户在需要使用网络服务时,需要通过一次两层的安全认证登陆FIDO-IDP,得到FIDO-IDP对SP账号的授权后即可使用网络服务。A method for realizing one-to-many account mapping and binding of multi-screen and multi-factor convenient WEB identity authentication proposed by the present invention requires users to use multi-screen on the basic framework of FIDO (Fast Identity Online, referred to as FIDO, Fast Identity Authentication Alliance) Register a FIDO user account UID on the FIDO-IDP (FIDO Identity Provider) website provided in the multi-factor authentication mechanism, and then bind the network service account used with this account. When users need to use network services, they need to log in to FIDO-IDP through a two-layer security authentication, and can use network services after being authorized by FIDO-IDP to the SP account.
本发明与现有技术相比有优点在于:本发明通过多屏多因子的安全认证方式提高用户登录安全性的同时提出一种便捷账号映射管理方法。首先在移动智能终端设备验证用户本地静态敏感信息,验证通过后,将移动智能终端设备生成的一次性密钥(OTP)加密处理后提交至服务端FIDO-IDP进行验证,最大限度的保证用户认证的安全,同时借助移动智能终端设备账号,FIDO-IDP用户账号和服务提供商SP服务账号SPID的三层的关联体系,简化了单点登录的过程和身份的识别过程。Compared with the prior art, the present invention has the advantages that: the present invention improves user login security through a multi-screen multi-factor security authentication method, and at the same time proposes a convenient account mapping management method. Firstly, the user's local static sensitive information is verified on the mobile smart terminal device. After the verification is passed, the one-time key (OTP) generated by the mobile smart terminal device is encrypted and submitted to the server FIDO-IDP for verification, ensuring user authentication to the greatest extent. At the same time, with the help of the three-tier association system of mobile smart terminal device account, FIDO-IDP user account and service provider SP service account SPID, the single sign-on process and identity identification process are simplified.
附图说明Description of drawings
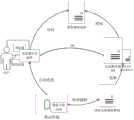
图1本发明的整体实施示意图;The overall implementation schematic diagram of Fig. 1 the present invention;
图2本发明多屏多因子身份认证中三层账号体系示意图;Fig. 2 is a schematic diagram of the three-tier account system in the multi-screen multi-factor identity authentication of the present invention;
图3本发明多屏多因子身份认证中三层账号体系下用户便捷登陆示意图;Fig. 3 is a schematic diagram of user convenient login under the three-tier account system in the multi-screen multi-factor identity authentication of the present invention;
图4本发明多屏多因子身份认证中三层账号体系下账号绑定登录流程图。Fig. 4 is a flow chart of account binding and login under the three-tier account system in the multi-screen multi-factor identity authentication of the present invention.
具体实施方式Detailed ways
为使本发明的目的、优点以及技术方案更加清楚明白,以下通过具体实施,并结合附图,对本发明进一步详细说明。In order to make the objectives, advantages and technical solutions of the present invention more clear, the present invention will be further described in detail below through specific implementation and in conjunction with the accompanying drawings.
三层账号体系本发明在多屏多因子认证方法(即在本地设备层和服务端服务器层分别对不同认证数据进行验证。避免了传统认证中仅在服务器层对数据进行验证,通过多屏下多层级的验证提高了身份认证过程中的安全性。即用户通过移动智能终端设备的本地身份验证,再借助移动智能终端设备登陆FIDO-IDP,最终获得网络服务授权的过程)基础上,借助三层账号关联体系,完成对设备、用户、服务三个层面的关联。以用户账号为关键的中间连接层,保持设备、用户、服务关联的同时,使它们各自保持一定的独立性。通过分层的实现方法既保证了安全认证过程的完整性,同时也保护了各层数据的隐私安全。Three-layer account system The present invention verifies different authentication data in the multi-screen multi-factor authentication method (that is, at the local device layer and the server layer at the server end respectively. It avoids only verifying the data at the server layer in traditional authentication, and through multi-screen Multi-level verification improves the security of the identity authentication process. That is, the user passes the local identity verification of the mobile smart terminal device, and then logs in to FIDO-IDP with the help of the mobile smart terminal device, and finally obtains the network service authorization process). The layered account association system completes the association of equipment, users, and services at three levels. The intermediate connection layer with the user account as the key maintains the association of devices, users, and services while maintaining their independence to a certain extent. The layered implementation not only ensures the integrity of the security authentication process, but also protects the privacy and security of the data at each layer.
本发明针对用户登录的时提供多屏多因子的认证方法,即用户在移动智能终端设备进行本地的验证后,再利用移动智能终端设备生成的OTP提交到认证服务器FIDO-IDP进行验证。完成两层认证功能需要的部件有:浏览器插件、移动智能终端设备、设备仓库服务器(VS)、设备仓库验证缓存(VC)、认证服务器(WS)、服务提供商(SP)。The present invention provides a multi-screen multi-factor authentication method for user login, that is, after the user performs local verification on the mobile smart terminal device, the OTP generated by the mobile smart terminal device is then used to submit to the authentication server FIDO-IDP for verification. The components required to complete the two-tier authentication function are: browser plug-in, mobile smart terminal device, device warehouse server (VS), device warehouse verification cache (VC), authentication server (WS), and service provider (SP).
浏览器插件是安装在用户智能终端,为了保证整个系统的各部分顺利工作所定制的一个重要功能部件,它主要提供生成QR码,与移动智能终端设备的安全连接,消息内容的转发等功能。用户在绑定用户账号或者登陆用户账号时,需要调用该插件生成包含智能终端连接信息的QR码,移动智能终端设备扫描QR码后,利用QR码中的信息与插件进行安全连接,该插件还会在建立安全连接后完成一些消息内容(如OTP)的转发操作。The browser plug-in is installed on the user's smart terminal and is an important functional component customized to ensure the smooth operation of all parts of the entire system. It mainly provides functions such as generating QR codes, securely connecting with mobile smart terminal devices, and forwarding message content. When the user binds the user account or logs in the user account, he needs to call the plug-in to generate a QR code containing the connection information of the smart terminal. After scanning the QR code, the mobile smart terminal device uses the information in the QR code to connect securely with the plug-in. The forwarding operation of some message content (such as OTP) will be completed after the secure connection is established.
移动智能终端提供了一个密码的物理隔离设备。移动智能终端设备在使用前需要在VC上进行注册,并协商产生OTP的共享秘钥;它还能够提供第一因素的本地的验证功能,并在验证通过之后,才会生成OTP以提供第二因素的验证。同时,移动智能终端设备通过扫描QR码获得智能终端的连接信息,与智能终端完成自动无线连接。The smart mobile terminal provides a cryptographic physical isolation device. Mobile smart terminal devices need to register on VC before use, and negotiate to generate OTP shared secret key; it can also provide the local authentication function of the first factor, and after the authentication is passed, OTP will be generated to provide the second factor verification. At the same time, the mobile smart terminal device obtains the connection information of the smart terminal by scanning the QR code, and completes the automatic wireless connection with the smart terminal.
设备仓库验证缓存(VC)是设备仓库服务器存储数据的一个缓存,它和认证服务器WS是物理相连的。认证服务器WS每次提交移动智能终端设备识别信息DID后,它能够快速高效的返回对应的OTP。The device warehouse verification cache (VC) is a cache for storing data in the device warehouse server, and it is physically connected to the authentication server WS. After the authentication server WS submits the mobile smart terminal device identification information DID each time, it can quickly and efficiently return the corresponding OTP.
认证服务器(WS)是本系统的核心部分,是FIDO-IDP的最要的组成部分,负责核心的用户账号管理和账号绑定管理。用户在登录SP时需要在该服务器登录用户账号,得到该服务器返回的对服务提供商账号的授权。用户在登录账号时,它会向VC提交DID对应OTP请求。The authentication server (WS) is the core part of the system and the most important part of FIDO-IDP, responsible for the core user account management and account binding management. When logging in to the SP, the user needs to log in the user account on the server, and obtain the authorization of the service provider account returned by the server. When the user logs in to the account, it will submit an OTP request corresponding to the DID to the VC.
设备仓库服务器(VS)提供移动智能终端设备的注册功能,所有的移动智能终端设备在使用该系统前都需要注册。它与移动智能终端设备共同协商秘钥和移动智能终端设备识别信息(DID)等内容。它会存储这些内容并将其更新到VC中,以便WS在对用户的第二因素验证过程中能够得到用户对应移动智能终端设备的信息。The device warehouse server (VS) provides the registration function of mobile smart terminal devices, and all mobile smart terminal devices need to be registered before using the system. It negotiates with the mobile smart terminal device on the secret key and mobile smart terminal device identification information (DID) and other content. It will store these contents and update them to VC, so that WS can obtain the information of the user's corresponding mobile smart terminal device during the second factor verification process of the user.
服务提供商(SP)则是提供网络服务的实体,用户可以通过将用户账号绑定多个服务提供商账号,这样通过登陆一个用户账号则可以登陆多个服务提供商账号。服务提供商需要和WS建立一定的信任关系并且有安全的通信方式。A service provider (SP) is an entity that provides network services. Users can bind multiple service provider accounts with their user accounts, so that they can log in to multiple service provider accounts by logging in to one user account. The service provider needs to establish a certain trust relationship with WS and have a secure communication method.
上述完成多屏多因子认证方法中的功能部件,设备仓库服务器VS负责提供三层账号体系下的设备账号,服务提供商SP负责提供三层账号体系下的用户服务账号,认证服务器WS负责提供三层账号体系下用户账号,是三层账号连接的桥梁。The functional components in the multi-screen multi-factor authentication method are completed above, the device warehouse server VS is responsible for providing the device account under the three-tier account system, the service provider SP is responsible for providing the user service account under the three-tier account system, and the authentication server WS is responsible for providing the three-tier account system. The user account under the layered account system is the bridge connecting the three layers of accounts.
对于图1从整体上描述了多屏多因子身份认证中账号管理实施的总体架构,主要包括下面两部分的内容。Figure 1 describes the overall architecture of account management implementation in multi-screen multi-factor authentication as a whole, mainly including the following two parts.
一、多屏多因子身份认证中三层账号体系的实现方法1. Implementation method of three-tier account system in multi-screen multi-factor authentication
如图2,三层账号体系设计分别对应设备层(DID)、用户层(UID)和服务层(SPID),这种三层账号设计主要是为了解决身份认证过程中,信息的保密与多身份间的便捷管理。As shown in Figure 2, the design of the three-tier account system corresponds to the device layer (DID), user layer (UID) and service layer (SPID). This three-tier account design is mainly to solve the problem of information confidentiality and multiple identities Convenient management between.
设备账号DID作为移动智能终端设备的识别信息,由移动智能终端设备在VS上通过证书激活技术获得。DID信息由两部分信息共同组成,一部分为移动智能终端设备拥有者信息,保存在移动智能终端本地安全存储区上;另一部分为移动智能终端设备本身信息,保存在设备仓库服务器VS上。用户信息利用本地设备映射关系,直接跟DID信息关联,服务器VS上只存储设备信息,这样的好处是,服务器并不知道具体使用者的身份,只能识别为使用者拥有设备为信任设备,同时设备所有者可授权其拥有设备给其他可信使用者使用。DID起到了对移动智能终端设备的识别功能,同时为用户身份认证信息提供在认证服务器WS端的比对功能,作为用户身份认证信息与移动智能终端设备关联的桥梁。The device account DID, as the identification information of the mobile smart terminal device, is obtained by the mobile smart terminal device through the certificate activation technology on the VS. DID information is composed of two parts of information, one part is the information of the owner of the mobile smart terminal device, which is stored in the local safe storage area of the mobile smart terminal; the other part is the information of the mobile smart terminal device itself, which is stored on the device warehouse server VS. The user information uses the local device mapping relationship and is directly associated with the DID information. Only the device information is stored on the server VS. The advantage of this is that the server does not know the identity of the specific user and can only recognize the device as the trusted device. Device owners can authorize their devices to be used by other trusted users. DID plays the role of identifying mobile smart terminal equipment, and at the same time provides a comparison function for user identity authentication information on the authentication server WS, serving as a bridge between user identity authentication information and mobile smart terminal equipment.
用户账号UID作为用户在WS的账号,是用户的身份,由用户在WS服务器上注册获得,UID信息保存在WS服务器,为DID与SPID关联的中间件,是三层账号体系的实施的基础。存在该层账号的好处在于将映射控制权交予WS处理,通过WS上账号管理模块,对DID实现一对多的映射绑定和对SPID实现一对多的映射绑定以及与DID和SPID的关联解锁,提供更好的使用体验和高兼容性的支持。User account UID, as the user's account in WS, is the user's identity. It is obtained by the user's registration on the WS server. The UID information is stored in the WS server. It is the middleware associated with DID and SPID, and is the basis for the implementation of the three-tier account system. The advantage of having accounts at this layer is that the mapping control right is handed over to WS. Through the account management module on WS, one-to-many mapping binding for DID and one-to-many mapping binding for SPID are realized, as well as the connection between DID and SPID. Associated unlocking provides better user experience and high compatibility support.
服务账号SPID为用户的服务账号,由SP提供。SPID的注册在SP端进行,同时SPID的信息保存在SP服务器上,SPID的服务权限由SP提供管理。UID账号系统关联SPID,SPID为服务提供商SP可识别的信息,既可以使服务控制方保留在SP,使SP可以通过黑名单来拒绝用户的服务请求,又保证了对SP服务系统无需改动,降低了与SP服务系统对接的代价,增加了系统部署的便捷性,同时将服务控制方分散于各SP,在一定程度上保护了用户的隐私信息。The service account SPID is the user's service account and is provided by the SP. The registration of SPID is carried out on the SP side, and the information of SPID is saved on the SP server at the same time, and the service authority of SPID is provided and managed by SP. The UID account system is associated with SPID, and SPID is information that can be identified by the service provider SP. It can not only keep the service controller in the SP, but also enable the SP to reject the user's service request through the blacklist, and ensure that the SP service system does not need to be changed. It reduces the cost of docking with the SP service system, increases the convenience of system deployment, and at the same time disperses the service controllers in each SP, protecting the user's privacy information to a certain extent.
三层账号映射绑定及使用绑定的方式为多个DID映射绑定到一个UID,一个UID映射绑定到多个SPID上,即通过设备证书激活技术获得设备层标识、在服务提供商SP处获得用户服务层标识、在认证服务器用户注册获得用户层标识,并在该层实现用户三层账号体系下的映射关联。用户在完成三层账号体系映射绑定后,用户要获得服务提供商提供的服务时用户首先在通过本地设备层验证后,将移动智能终端的DID及其它信息(如OTP信息)发送给认证服务器,认证服务器WS从中找到DID对应的UID,再根据用户UID对应的要登录的服务提供商提供的服务选择对应的服务层账号SPID,认证服务器将相关信息发送给SP服务器,完成用户要享受服务的认证登录过程。The three-tier account mapping binding and binding method is that multiple DIDs are mapped to one UID, and one UID is mapped to multiple SPIDs, that is, the device layer identity is obtained through the device certificate activation technology, and the service provider SP Obtain the user service layer identifier at the user service layer, obtain the user layer identifier at the authentication server user registration, and realize the mapping association under the user's three-tier account system at this layer. After the user completes the mapping and binding of the three-tier account system, when the user wants to obtain the service provided by the service provider, the user first passes the verification of the local device layer, and then sends the DID of the mobile smart terminal and other information (such as OTP information) to the authentication server , the authentication server WS finds the UID corresponding to the DID, and then selects the corresponding service layer account SPID according to the service provided by the service provider corresponding to the user UID to log in, and the authentication server sends the relevant information to the SP server to complete the user to enjoy the service. Authentication login process.
二、三层账号体系下账号映射绑定后的登陆过程2. The login process after account mapping and binding under the three-tier account system
初始化用户在使用该方案映射绑定之前,需要对移动智能终端设备(如智能手机、Pad等)和智能终端(如电脑、智能云电视等)等进行初始化操作,以便获得三层账号提下各层对应的账号信息。Initialization Users need to initialize mobile smart terminal devices (such as smartphones, Pads, etc.) and smart terminals (such as computers, smart cloud TVs, etc.) Layer corresponding account information.
移动智能终端设备的初始化:用户在移动智能终端设备安装多屏多因子认证应用后,需对其应用进行初始化,即连接设备验证服务器VS完成注册,协商得到用户的移动智能终端设备证书,该证书用于标识用户和建立安全信道SSL连接等功能。同时协商得到标识证书的DID,以及生成OTP的共享秘钥K,这些数据都被存储在移动智能终端设备的安全存储区,该存储区只能被多屏多因子认证应用访问。注册成功后,VS会将移动智能终端设备对应的信息更新至各分布式设备仓库验证缓存VC。该过程实现主要建立起设备层账号,为多屏多因子认证奠定设备层条件。Initialization of the mobile smart terminal device: After the user installs the multi-screen multi-factor authentication application on the mobile smart terminal device, the application needs to be initialized, that is, the device verification server VS is connected to complete the registration, and the user's mobile smart terminal device certificate is obtained through negotiation. Used to identify users and establish secure channel SSL connections and other functions. At the same time, the DID of the identification certificate and the shared secret key K for generating the OTP are negotiated. These data are stored in the secure storage area of the mobile smart terminal device, which can only be accessed by multi-screen multi-factor authentication applications. After the registration is successful, VS will update the information corresponding to the mobile smart terminal device to the verification cache VC of each distributed device warehouse. The realization of this process mainly establishes the device layer account, and establishes the device layer conditions for multi-screen multi-factor authentication.
智能终端的初始化:用户需要在智能终端(如PC、智能云电视)浏览器上安装认证安全插件,完成基于无线安全传递认证信息的登陆功能。同时,用户需安装在智能终端浏览器上安装证书以保证认证安全插件和移动智能终端设备、认证安全插件和认证服务器WS之间的建立安全信道SSL。Initialization of smart terminals: Users need to install authentication security plug-ins on the browsers of smart terminals (such as PCs and smart cloud TVs) to complete the login function based on wireless security transmission of authentication information. At the same time, the user needs to install a certificate on the smart terminal browser to ensure the establishment of a secure channel SSL between the authentication security plug-in and the mobile smart terminal device, the authentication security plug-in and the authentication server WS.
如图3所示,一次完整的登陆需要这些步骤。假设用户已经拥有用户账号UID和服务提供商账号SPID,并且它们已经在认证服务器WS端完成绑定。设备账号DID和用户账号UID已完成映射绑定。由于在本方案内移动智能终端设备并不限定为某一类设备,本文以智能手机为例,结合附图4,说明具体的实施过程,其中a)-h)步为用户账号登陆过程,i)-l)步得到为服务提供商SP账号授权的过程:As shown in Figure 3, a complete login requires these steps. It is assumed that the user already has a user account UID and a service provider account SPID, and they have been bound at the authentication server WS. The device account DID and user account UID have been mapped and bound. Since mobile intelligent terminal equipment is not limited to a certain type of equipment in this solution, this paper takes a smart phone as an example, and in conjunction with accompanying drawing 4, illustrates the specific implementation process, wherein steps a)-h) are the user account login process, i )-l) Steps to obtain the authorization process for the SP account of the service provider:
a)用户在智能终端PC中的浏览器B访问SP网站,并选择单点登陆,服务提供商SP网站将跳转至认证服务器WS登陆页面;a) The user visits the SP website with browser B in the smart terminal PC, and selects single sign-on, and the service provider SP website will jump to the authentication server WS login page;
b)浏览器借助认证安全插件与WS服务器建立SSL安全连接,令SSL共享秘钥为KBW。WS页面调用已经安装在浏览器的安全插件,建立WI-FI接入点,并将PC的Wi-Fi连接信息生成二维码显示于页面中。二维码包含的信息为:[SSID,Password,Address,Port],其中SSID为Wi-Fi接入点的标记ID,Password为Wi-Fi接入点密码,Address为Wi-Fi接入点的IP地址信息,Port为Wi-Fi接入点的空闲端口号;b) The browser establishes an SSL secure connection with the WS server through the authentication security plug-in, and sets the SSL shared key to KBW. The WS page invokes the security plug-in already installed in the browser, establishes a WI-FI access point, and generates a QR code from the PC’s Wi-Fi connection information to display on the page. The information contained in the QR code is: [SSID, Password, Address, Port], where SSID is the tag ID of the Wi-Fi access point, Password is the password of the Wi-Fi access point, and Address is the ID of the Wi-Fi access point. IP address information, Port is the free port number of the Wi-Fi access point;
c)用户首先在移动智能终端设备利用本地密码解锁对应本地账号,打开移动智能终端设备的应用,扫描b)步骤生成二维码,解析二维码内容并与智能终端PC浏览器建立安全信道SSL连接,令SSL共享秘钥为KBM;c) The user first uses the local password on the mobile smart terminal device to unlock the corresponding local account, opens the application of the mobile smart terminal device, scans step b) to generate a QR code, parses the content of the QR code and establishes a secure channel SSL with the PC browser of the smart terminal Connect, let the SSL shared key be KBM;
d)移动智能终端设备利用预先协商的共享秘钥K生成OTP,利用c)建立的安全连接将信息{DID,Time,Sig}KBM发送至智能终端:d) The mobile smart terminal device uses the pre-negotiated shared secret key K to generate OTP, and uses the secure connection established in c) to send the information {DID, Time, Sig} KBM to the smart terminal:
e)智能终端PC的安全插件接收到移动智能终端设备无线安全传递的消息后,再通过浏览器与WS服务器之间建立地安全信道将(e)转发至WS服务器;e) After the security plug-in of the smart terminal PC receives the wireless security transmission message of the mobile smart terminal device, it forwards (e) to the WS server through the secure channel established between the browser and the WS server;
f)WS服务器接收到智能终端PC发送的消息,在安全信道SSL利用KBW解密后获得DID、Time和Sig,验证Time的有效性,并且将DID、Time和Sig提交至设备仓库验证缓存VC验证其有效性;若Time无效,验证不通过,该提示用户失败;f) The WS server receives the message sent by the smart terminal PC, obtains the DID, Time and Sig after decrypting with KBW in the secure channel SSL, verifies the validity of Time, and submits the DID, Time and Sig to the device warehouse verification cache VC for verification Validity; if the Time is invalid and the verification fails, the user will be prompted to fail;
g)VC在接收到DID、Sig和Time后,通过DID找到对应的共享秘钥K,再使用该秘钥和系统当前时间作为计算参数生成OTP,利用OTP采用与一种智能终端相同的HMAC算法对DID,Time签名,并与接受到Sig值比对,将验证结果返回给WS;g) After receiving DID, Sig and Time, VC finds the corresponding shared secret key K through DID, and then uses the secret key and the current system time as calculation parameters to generate OTP, and uses OTP to adopt the same HMAC algorithm as an intelligent terminal Sign the DID and Time, compare it with the received Sig value, and return the verification result to WS;
h)若Sig验证通过,即VC返回验证成功的结果,至此DID绑定的用户账号登陆成功;若Sig不通过,验证失败。此时WS页面会显示用户已经绑定的SP账号,用户选择其中一个SP账号进行登陆。WS会随机生成一个验证码Authorization Code并将其与用户选定的SP账号关联。并返回一个带参数的跳转至SP的链接,其中参数为Authorization Code;h) If the Sig verification is passed, that is, the VC returns a successful verification result, and the user account bound to the DID has successfully logged in; if the Sig does not pass, the verification fails. At this time, the WS page will display the SP accounts that the user has bound, and the user can select one of the SP accounts to log in. WS will randomly generate a verification code Authorization Code and associate it with the SP account selected by the user. And return a link with parameters to jump to SP, where the parameter is Authorization Code;
i)浏览器将根据WS返回的链接跳转至SP的处理页面;i) The browser will jump to the processing page of SP according to the link returned by WS;
j)SP验证此次跳转链接请求的有效性,即此跳转链接的请求和开始登陆的请求来自同一个浏览器。验证有效,则将Authorization Code发送至WS,请求SP账号的授权;若无效,返回登录错误;j) The SP verifies the validity of the jump link request, that is, the jump link request and the login start request come from the same browser. If the verification is valid, the Authorization Code will be sent to WS to request the authorization of the SP account; if it is invalid, a login error will be returned;
k)WS在收到SP账号授权请求后,将Authorization Code对应的SP账号返回至服务提供商SP;k) WS returns the SP account corresponding to the Authorization Code to the service provider SP after receiving the SP account authorization request;
l)SP向智能终端PC的浏览器返回SP账号登陆成功或失败的结果。l) The SP returns the result of successful or failed login of the SP account to the browser of the smart terminal PC.
Claims (5)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201410109452.3ACN103856332B (en) | 2014-03-22 | 2014-03-22 | Implementation method of one-to-multiple account mapping binding of convenient and rapid multi-screen multi-factor WEB identity authentication |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201410109452.3ACN103856332B (en) | 2014-03-22 | 2014-03-22 | Implementation method of one-to-multiple account mapping binding of convenient and rapid multi-screen multi-factor WEB identity authentication |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN103856332Atrue CN103856332A (en) | 2014-06-11 |
| CN103856332B CN103856332B (en) | 2017-02-08 |
Family
ID=50863577
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN201410109452.3AExpired - Fee RelatedCN103856332B (en) | 2014-03-22 | 2014-03-22 | Implementation method of one-to-multiple account mapping binding of convenient and rapid multi-screen multi-factor WEB identity authentication |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN103856332B (en) |
Cited By (19)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN104144163A (en)* | 2014-07-24 | 2014-11-12 | 腾讯科技(深圳)有限公司 | Identity verification method, device and system |
| CN104283885A (en)* | 2014-10-14 | 2015-01-14 | 中国科学院信息工程研究所 | An implementation method of multi-SP security binding based on local authentication of intelligent terminals |
| CN105553992A (en)* | 2015-12-22 | 2016-05-04 | 北京奇虎科技有限公司 | A method and system for logging in by borrowing another person's account |
| CN105656890A (en)* | 2015-12-30 | 2016-06-08 | 深圳数字电视国家工程实验室股份有限公司 | FIDO (Fast Identity Online) authenticator, system and method based on TEE (Trusted Execution Environment) and wireless confirmation |
| CN105721480A (en)* | 2016-03-02 | 2016-06-29 | 北京九州云腾科技有限公司 | FIDO hardware-based user operating method and system |
| CN106230845A (en)* | 2016-08-04 | 2016-12-14 | 杭州帕拉迪网络科技有限公司 | A kind of multifactor user authen method of flexibly configurable |
| CN108259458A (en)* | 2017-09-30 | 2018-07-06 | 中国平安人寿保险股份有限公司 | Application software account relating method, apparatus and storage medium |
| CN109361535A (en)* | 2018-09-27 | 2019-02-19 | 北京小米移动软件有限公司 | Smart device binding method, device and storage medium |
| CN104901796B (en)* | 2015-06-02 | 2019-04-05 | 新华三技术有限公司 | A kind of authentication method and equipment |
| CN110867189A (en)* | 2018-08-28 | 2020-03-06 | 北京京东尚科信息技术有限公司 | Login method and device |
| CN111031540A (en)* | 2019-11-22 | 2020-04-17 | 儒庭信息技术(上海)有限公司 | Wireless network connection method and computer storage medium |
| CN111164594A (en)* | 2019-07-02 | 2020-05-15 | 阿里巴巴集团控股有限公司 | System and method for mapping decentralized identities to real entities |
| CN111695108A (en)* | 2020-06-04 | 2020-09-22 | 中国科学院计算机网络信息中心 | Unified account identification system for multi-source accounts in heterogeneous computing environment |
| CN112199652A (en)* | 2020-10-23 | 2021-01-08 | 网易(杭州)网络有限公司 | Login method, terminal, server, system, medium and equipment of application program |
| CN113079085A (en)* | 2021-03-30 | 2021-07-06 | 北京有竹居网络技术有限公司 | Business service interaction method, business service interaction device, business service interaction equipment and storage medium |
| WO2021155490A1 (en)* | 2020-02-03 | 2021-08-12 | Nokia Solutions And Networks Oy | Providing mutl-device serivce using network application programming interface |
| CN113452584A (en)* | 2021-04-28 | 2021-09-28 | 珠海格力电器股份有限公司 | Binding control method and device of electric appliance, storage medium, mobile terminal and electric appliance |
| CN115277624A (en)* | 2022-03-07 | 2022-11-01 | 上海诺行信息技术有限公司 | A multi-card aggregation real-name authentication method |
| CN115459994A (en)* | 2022-09-06 | 2022-12-09 | 亚数信息科技(上海)有限公司 | A FIDO2 authentication system and method based on Internet |
Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN102420800A (en)* | 2010-09-28 | 2012-04-18 | 俞浩波 | Method, system and authentication terminal for accomplishing service by multi-factor identity authentication |
| US20120240204A1 (en)* | 2011-03-11 | 2012-09-20 | Piyush Bhatnagar | System, design and process for strong authentication using bidirectional OTP and out-of-band multichannel authentication |
| CN103428001A (en)* | 2013-09-05 | 2013-12-04 | 中国科学院信息工程研究所 | Implicit type enhanced convenient WEB identity authentication method |
- 2014
- 2014-03-22CNCN201410109452.3Apatent/CN103856332B/ennot_activeExpired - Fee Related
Patent Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN102420800A (en)* | 2010-09-28 | 2012-04-18 | 俞浩波 | Method, system and authentication terminal for accomplishing service by multi-factor identity authentication |
| US20120240204A1 (en)* | 2011-03-11 | 2012-09-20 | Piyush Bhatnagar | System, design and process for strong authentication using bidirectional OTP and out-of-band multichannel authentication |
| CN103428001A (en)* | 2013-09-05 | 2013-12-04 | 中国科学院信息工程研究所 | Implicit type enhanced convenient WEB identity authentication method |
Cited By (28)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN104144163A (en)* | 2014-07-24 | 2014-11-12 | 腾讯科技(深圳)有限公司 | Identity verification method, device and system |
| CN104283885B (en)* | 2014-10-14 | 2017-07-28 | 中国科学院信息工程研究所 | A kind of implementation method of many SP secure bindings based on intelligent terminal local authentication |
| CN104283885A (en)* | 2014-10-14 | 2015-01-14 | 中国科学院信息工程研究所 | An implementation method of multi-SP security binding based on local authentication of intelligent terminals |
| CN104901796B (en)* | 2015-06-02 | 2019-04-05 | 新华三技术有限公司 | A kind of authentication method and equipment |
| CN105553992B (en)* | 2015-12-22 | 2019-02-12 | 北京奇虎科技有限公司 | A method and system for logging in by borrowing another person's account |
| CN105553992A (en)* | 2015-12-22 | 2016-05-04 | 北京奇虎科技有限公司 | A method and system for logging in by borrowing another person's account |
| CN105656890B (en)* | 2015-12-30 | 2018-11-06 | 深圳数字电视国家工程实验室股份有限公司 | A kind of FIDO authenticators and system and method based on TEE and without line justification |
| CN105656890A (en)* | 2015-12-30 | 2016-06-08 | 深圳数字电视国家工程实验室股份有限公司 | FIDO (Fast Identity Online) authenticator, system and method based on TEE (Trusted Execution Environment) and wireless confirmation |
| CN105721480A (en)* | 2016-03-02 | 2016-06-29 | 北京九州云腾科技有限公司 | FIDO hardware-based user operating method and system |
| CN106230845A (en)* | 2016-08-04 | 2016-12-14 | 杭州帕拉迪网络科技有限公司 | A kind of multifactor user authen method of flexibly configurable |
| CN108259458A (en)* | 2017-09-30 | 2018-07-06 | 中国平安人寿保险股份有限公司 | Application software account relating method, apparatus and storage medium |
| CN108259458B (en)* | 2017-09-30 | 2021-12-28 | 中国平安人寿保险股份有限公司 | Application software account correlation method and device and storage medium |
| CN110867189A (en)* | 2018-08-28 | 2020-03-06 | 北京京东尚科信息技术有限公司 | Login method and device |
| CN109361535A (en)* | 2018-09-27 | 2019-02-19 | 北京小米移动软件有限公司 | Smart device binding method, device and storage medium |
| CN111164594A (en)* | 2019-07-02 | 2020-05-15 | 阿里巴巴集团控股有限公司 | System and method for mapping decentralized identities to real entities |
| CN111164594B (en)* | 2019-07-02 | 2023-08-25 | 创新先进技术有限公司 | System and method for mapping a de-centralized identity to a real entity |
| CN111031540A (en)* | 2019-11-22 | 2020-04-17 | 儒庭信息技术(上海)有限公司 | Wireless network connection method and computer storage medium |
| WO2021155490A1 (en)* | 2020-02-03 | 2021-08-12 | Nokia Solutions And Networks Oy | Providing mutl-device serivce using network application programming interface |
| CN111695108A (en)* | 2020-06-04 | 2020-09-22 | 中国科学院计算机网络信息中心 | Unified account identification system for multi-source accounts in heterogeneous computing environment |
| CN112199652A (en)* | 2020-10-23 | 2021-01-08 | 网易(杭州)网络有限公司 | Login method, terminal, server, system, medium and equipment of application program |
| CN112199652B (en)* | 2020-10-23 | 2023-08-25 | 网易(杭州)网络有限公司 | Login method, terminal, server, system, medium and equipment of application program |
| CN113079085B (en)* | 2021-03-30 | 2023-01-10 | 北京有竹居网络技术有限公司 | Business service interaction method, device, equipment and storage medium |
| CN113079085A (en)* | 2021-03-30 | 2021-07-06 | 北京有竹居网络技术有限公司 | Business service interaction method, business service interaction device, business service interaction equipment and storage medium |
| CN113452584B (en)* | 2021-04-28 | 2023-01-31 | 珠海格力电器股份有限公司 | Binding control method and device of electric appliance, storage medium, mobile terminal and electric appliance |
| CN113452584A (en)* | 2021-04-28 | 2021-09-28 | 珠海格力电器股份有限公司 | Binding control method and device of electric appliance, storage medium, mobile terminal and electric appliance |
| CN115277624A (en)* | 2022-03-07 | 2022-11-01 | 上海诺行信息技术有限公司 | A multi-card aggregation real-name authentication method |
| CN115459994A (en)* | 2022-09-06 | 2022-12-09 | 亚数信息科技(上海)有限公司 | A FIDO2 authentication system and method based on Internet |
| CN115459994B (en)* | 2022-09-06 | 2025-04-25 | 亚数信息科技(上海)有限公司 | A FIDO2 authentication system and method based on Internet network |
Also Published As
| Publication number | Publication date |
|---|---|
| CN103856332B (en) | 2017-02-08 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN103856332B (en) | Implementation method of one-to-multiple account mapping binding of convenient and rapid multi-screen multi-factor WEB identity authentication | |
| US11323441B2 (en) | System and method for proxying federated authentication protocols | |
| CN103780397B (en) | A kind of multi-screen multiple-factor convenient WEB identity authentication method | |
| CN102624720B (en) | Method, device and system for identity authentication | |
| CN104917727B (en) | A kind of method, system and device of account's authentication | |
| CN104283886B (en) | A kind of implementation method of the web secure access based on intelligent terminal local authentication | |
| US8707409B2 (en) | Method and apparatus for providing trusted single sign-on access to applications and internet-based services | |
| CN101515932B (en) | Method and system for accessing Web service safely | |
| CN104065616B (en) | Single-point logging method and system | |
| CN104283885B (en) | A kind of implementation method of many SP secure bindings based on intelligent terminal local authentication | |
| CN101902327B (en) | Method and device for realizing single-point log-in and system thereof | |
| US9419974B2 (en) | Apparatus and method for performing user authentication by proxy in wireless communication system | |
| US20080092215A1 (en) | System and method for transparent single sign-on | |
| CN102882835B (en) | A kind of method and system realizing single-sign-on | |
| US11823007B2 (en) | Obtaining device posture of a third party managed device | |
| CN101159557A (en) | Single point logging method, device and system | |
| WO2014183526A1 (en) | Identity recognition method, device and system | |
| CN103067338A (en) | Third party application centralized safety management method and system and corresponding communication system | |
| CN102112991B (en) | Means for managing user authentication | |
| CN105554004A (en) | An authentication system and method for container services in a hybrid cloud computing environment | |
| CN101986598B (en) | Authentication method, server and system | |
| US20110289567A1 (en) | Service access control | |
| KR101690989B1 (en) | Method of electric signature using fido authentication module | |
| US8627423B2 (en) | Authorizing remote access points | |
| CN107770192A (en) | Identity authentication method and computer-readable recording medium in multisystem |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| C06 | Publication | ||
| PB01 | Publication | ||
| C10 | Entry into substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| C14 | Grant of patent or utility model | ||
| GR01 | Patent grant | ||
| CF01 | Termination of patent right due to non-payment of annual fee | Granted publication date:20170208 Termination date:20180322 | |
| CF01 | Termination of patent right due to non-payment of annual fee |