CN103716292A - Cross-domain single-point login method and device thereof - Google Patents
Cross-domain single-point login method and device thereofDownload PDFInfo
- Publication number
- CN103716292A CN103716292ACN201210379442.2ACN201210379442ACN103716292ACN 103716292 ACN103716292 ACN 103716292ACN 201210379442 ACN201210379442 ACN 201210379442ACN 103716292 ACN103716292 ACN 103716292A
- Authority
- CN
- China
- Prior art keywords
- domain
- sign
- authentication information
- sso
- user
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/0815—Network architectures or network communication protocols for network security for authentication of entities providing single-sign-on or federations
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/31—User authentication
- G06F21/41—User authentication where a single sign-on provides access to a plurality of computers
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F2221/00—Indexing scheme relating to security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F2221/21—Indexing scheme relating to G06F21/00 and subgroups addressing additional information or applications relating to security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F2221/2113—Multi-level security, e.g. mandatory access control
Landscapes
- Engineering & Computer Science (AREA)
- Computer Hardware Design (AREA)
- Computer Security & Cryptography (AREA)
- Theoretical Computer Science (AREA)
- General Engineering & Computer Science (AREA)
- Signal Processing (AREA)
- Computer Networks & Wireless Communication (AREA)
- Software Systems (AREA)
- Physics & Mathematics (AREA)
- General Physics & Mathematics (AREA)
- Computing Systems (AREA)
- Information Transfer Between Computers (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明涉及一种进行单点登录的方法和设备,特别涉及一种跨域的单点登录方法和设备。The present invention relates to a method and device for single sign-on, in particular to a cross-domain single sign-on method and device.
背景技术Background technique
目前,在大型企业中,随着应用系统与信息技术的发展,常常需要用户从一个应用系统切换到另一个应用系统中。在登录到每个应用系统时,需要用户输入用户名和密码进行登录。由于每个应用系统登录时都需要输入用户名和密码,使得工作效率很低,并且由于用户需要记忆多个密码,所以很多用户会使用相同的密码,从而降低了应用系统的安全性。At present, in large enterprises, with the development of application systems and information technology, users are often required to switch from one application system to another. When logging in to each application system, the user is required to enter a user name and password to log in. Because each application system needs to input a user name and password when logging in, the work efficiency is very low, and because users need to remember multiple passwords, many users will use the same password, thereby reducing the security of the application system.
单点登录(Single sign-on,SSO)机制的出现很好地解决了上述问题。SSO机制使得在多个应用系统中,用户只需要登录一次就可以访问所有相互信任的应用系统。它是目前比较流行的企业业务整合的解决方案之一。The emergence of the single sign-on (SSO) mechanism has solved the above problems well. The SSO mechanism makes it possible for users to log in once in multiple application systems to access all mutually trusted application systems. It is one of the more popular enterprise business integration solutions.
目前已经提出了多种实现SSO机制的解决方案。这些解决方案大体可分为两大类,即,密码同步方案和票据方案。Various solutions for implementing the SSO mechanism have been proposed so far. These solutions can be roughly divided into two categories, namely, password synchronization schemes and ticket schemes.
在密码同步方案中,SSO处理模块预先在一个数据库中存储用于用户的一个主密码和与之对应的用于多个应用系统的多个从密码。当用户输入主密码时,先由SSO处理模块将其翻译成针对特定应用系统的从密码,再利用从密码完成相应的认证过程。这样,用户通过输入一个主密码就可以访问多个应用系统。In the password synchronization scheme, the SSO processing module pre-stores a master password for a user and multiple slave passwords corresponding to it for multiple application systems in a database. When the user enters the master password, the SSO processing module first translates it into a slave password for a specific application system, and then uses the slave password to complete the corresponding authentication process. In this way, the user can access multiple application systems by entering a master password.
在票据方案中,当用户第一次登录,例如访问应用系统1的时候,根据用户提供的登录信息,SSO认证服务器对用户进行身份效验,如果用户的身份通过了效验,SSO认证服务器返回给用户一个票据(ticket)。当用户第二次登录,例如再访问应用系统2的时候,这个ticket会被携带在登录请求中,作为用户认证的凭据,应用系统2接收到该登录请求之后会把ticket送到SSO认证服务器进行效验,以检查ticket的合法性。如果通过效验,用户就可以在不用再次输入用户名和密码的情况下访问应用系统2了。In the ticket scheme, when a user logs in for the first time, for example, when accessing
但在大型企业和机构中,一般都包括多层次的组织机构,每个组织机构都有自己独立的应用系统和信任的认证中心。例如,一个大企业一般都有总部组织机构、省级组织机构,甚至还有市级组织机构,这些组织机构都不在同一个认证域中,也即这些组织机构都有各自信任的认证中心。如果一个已登录省级组织机构的用户想要获取总部组织机构的学习系统中的资料,该用户须输入针对总部组织机构的用户名和密码登录到总部组织机构后,才能获取该学习系统中的资料。However, in large enterprises and institutions, there are generally multi-level organizations, and each organization has its own independent application system and trusted certification center. For example, a large enterprise generally has headquarters organizations, provincial organizations, and even municipal organizations. These organizations are not in the same certification domain, that is, these organizations have their own trusted certification centers. If a user who has logged into the provincial organization wants to obtain the materials in the learning system of the headquarters organization, the user must enter the user name and password for the headquarters organization to log in to the headquarters organization to obtain the materials in the learning system .
因此,现有技术中还需要一种支持跨域的单点登录方案。Therefore, there is also a need for a cross-domain single sign-on solution in the prior art.
发明内容Contents of the invention
有鉴于此,本发明的一个目的在于提供一种用于单点登录的方案,用以实现跨域的单点登录。In view of this, an object of the present invention is to provide a solution for single sign-on, so as to realize cross-domain single sign-on.
本发明的另一个目的在于提供一种易于部署的跨域单点登录机制,而无需对现有系统进行过多改动。Another object of the present invention is to provide an easy-to-deploy cross-domain single sign-on mechanism without making too many changes to the existing system.
根据本发明实施例的一个方面,提供一种用于单点登录的方法,包括:According to an aspect of an embodiment of the present invention, a method for single sign-on is provided, including:
第一域的单点登录发起方将通过第一域认证的用户的单点登录认证信息发送给第二域的单点登录中心;The SSO initiator of the first domain sends the SSO authentication information of the user authenticated by the first domain to the SSO center of the second domain;
在所述单点登录认证信息认证通过后,所述单点登录发起方从所述第二域的单点登录中心接收所述用户的跨域单点登录认证信息,其中,所述跨域单点登录认证信息中包含有所述第二域的单点登录中心的签名信息;After the SSO authentication information is authenticated, the SSO initiator receives the cross-domain SSO authentication information of the user from the SSO center of the second domain, wherein the cross-domain SSO The SSO authentication information includes the signature information of the SSO center of the second domain;
所述单点登录发起方向第二域的单点登录接收方发送所述跨域单点登录认证信息。The SSO initiator sends the cross-domain SSO authentication information to the SSO recipient in the second domain.
在本发明实施方式中,由于能够由第二域的单点登录中心对用户的单点登录认证信息进行认证并签名,而第二域中单点登录中心被第二域中的单点登录接收方信任,因此可以实现第二域中的单点登录接收方对用户身份的认证,从而实现了跨域的单点登录,满足大型企业和具有多层次组织机构的要求,提高了工作效率,并且本发明实施方式易于部署,在提高用户的体验的同时,还可以促进大众化的商业系统发展。In the embodiment of the present invention, since the SSO authentication information of the user can be authenticated and signed by the SSO center in the second domain, the SSO center in the second domain is received by the SSO in the second domain Therefore, the single sign-on receiver in the second domain can authenticate the user's identity, thereby realizing cross-domain single sign-on, meeting the requirements of large enterprises and multi-level organizations, improving work efficiency, and The embodiment of the present invention is easy to deploy, and can promote the development of a popular commercial system while improving user experience.
优选地,所述单点登录发起方向第二域的单点登录接收方发送所述跨域单点登录认证信息之前,还包括:Preferably, before the SSO initiator sends the cross-domain SSO authentication information to the SSO receiver of the second domain, it further includes:
所述单点登录发起方对所述跨域单点登录认证信息进行加密处理.The SSO initiator encrypts the cross-domain SSO authentication information.
在本发明实施方式中,由于对传输的跨域单点登录认证信息进行加密处理,从而提高了传输跨域单点登录认证信息过程中的安全性,同时进一步提高了单点登录的安全性。In the embodiment of the present invention, since the transmitted cross-domain single sign-on authentication information is encrypted, the security in the process of transmitting the cross-domain single sign-on authentication information is improved, and the security of the single sign-on is further improved.
优选地,所述单点登录发起方将通过第一域认证的用户的单点登录认证信息发送给第二域的单点登录中心之前,还包括:Preferably, before the SSO initiator sends the SSO authentication information of the user authenticated by the first domain to the SSO center of the second domain, it further includes:
所述单点登录发起方向第一域中的单点登录中心申请所述单点登录认证信息,所述单点登录认证信息中包含有所述用户的认证级别。The SSO initiator applies for the SSO authentication information to the SSO center in the first domain, and the SSO authentication information includes the authentication level of the user.
在本发明实施方式中,由于增加了认证级别,在用户的认证级别高于应用系统的认证级别后,才允许用户访问应用系统,从而完善了整体系统的性能。比如对于一些特殊的系统(比如财务系统等),只有特定用户才能访问,所以针对这些系统可以设定较高的认证级别,从而保证认证级别较低的用户无法访问。In the embodiment of the present invention, since the authentication level is increased, the user is allowed to access the application system only after the authentication level of the user is higher than that of the application system, thereby improving the performance of the overall system. For example, for some special systems (such as financial systems, etc.), only specific users can access, so a higher authentication level can be set for these systems, so as to ensure that users with lower authentication levels cannot access.
优选地,在所述单点登录发起方从所述第二域的单点登录中心接收所述用户的跨域单点登录认证信息时,所述单点登录发起方还从所述第二域的单点登录中心接收所述用户的会话标识;Preferably, when the single sign-on initiator receives the cross-domain single sign-on authentication information of the user from the single sign-on center of the second domain, the single sign-on initiator also receives the cross-domain single sign-on authentication information from the second domain The SSO center receives the user's session ID;
在所述单点登录发起方向第二域的单点登录接收方发送所述跨域单点登录认证信息时,还向所述第二域的单点登录接收方发送所述会话标识。When the SSO initiator sends the cross-domain SSO authentication information to the SSO receiver of the second domain, the session identifier is also sent to the SSO receiver of the second domain.
在本发明实施方式中,由于加入了会话标识,在收到的会话标识通过认证后,才允许用户访问应用系统,可以防止重放攻击,从而提高了跨域单点登录的安全性,为用户提供了更安全的网络环境,提高了用户体验。In the embodiment of the present invention, since the session identifier is added, the user is allowed to access the application system only after the received session identifier passes the authentication, which can prevent replay attacks, thereby improving the security of cross-domain single sign-on, and providing users with Provides a more secure network environment and improves user experience.
优选地,所述单点登录发起方向第二域的单点登录接收方发送所述会话标识之前,还包括:Preferably, before the SSO initiator sends the session identifier to the SSO receiver of the second domain, it further includes:
所述单点登录发起方对所述会话标识进行加密处理。The SSO initiator encrypts the session ID.
在本发明实施方式中,由于对传输的会话标识进行加密处理,从而提高了传输会话标识过程中的安全性,同时进一步提高了单点登录的安全性。In the embodiment of the present invention, since the transmitted session identifier is encrypted, the security in the process of transmitting the session identifier is improved, and at the same time, the security of the single sign-on is further improved.
根据本发明实施例的另一个方面,提供了一种用于单点登录的设备,该设备包括:According to another aspect of the embodiments of the present invention, a device for single sign-on is provided, and the device includes:
发送模块,用于将通过第一域认证的用户的单点登录认证信息发送给第二域的单点登录中心;A sending module, configured to send the single sign-on authentication information of the user authenticated by the first domain to the single sign-on center of the second domain;
接收模块,用于在所述单点登录认证信息认证通过后,所述单点登录发起方从所述第二域的单点登录中心接收所述用户的跨域单点登录认证信息,其中,所述跨域单点登录认证信息中包含有所述第二域的单点登录中心的签名信息;A receiving module, configured to receive, by the SSO initiator, the cross-domain SSO authentication information of the user from the SSO center of the second domain after the SSO authentication information is authenticated, wherein, The cross-domain single sign-on authentication information includes the signature information of the single sign-on center of the second domain;
处理模块,用于向第二域的单点登录接收方发送所述跨域单点登录认证信息。A processing module, configured to send the cross-domain single sign-on authentication information to the single sign-on receiver of the second domain.
附图说明Description of drawings
下文将以明确易懂的方式通过对优选实施方式的说明并结合附图来对本发明上述特性、技术特征、优点及其实施方式予以进一步说明,其中:The above-mentioned characteristics, technical features, advantages and implementation methods of the present invention will be further described below in a clear and understandable manner through descriptions of preferred embodiments and in conjunction with the accompanying drawings, wherein:
图1A为本发明实施方式用于单点登录的方法流程图;FIG. 1A is a flowchart of a method for single sign-on according to an embodiment of the present invention;
图1B为本发明实施方式的第一种进行跨域单点登录的方法流程图;FIG. 1B is a flow chart of the first cross-domain single sign-on method according to the embodiment of the present invention;
图2为本发明实施方式的第二种进行跨域单点登录的方法流程图;FIG. 2 is a flowchart of a second cross-domain single sign-on method according to an embodiment of the present invention;
图3为本发明实施方式的第三种进行跨域单点登录的方法流程图;FIG. 3 is a flow chart of a third cross-domain single sign-on method according to an embodiment of the present invention;
图4为本发明实施方式的应用环境示意图;Fig. 4 is a schematic diagram of the application environment of the embodiment of the present invention;
图5A为本发明实施方式的第四种进行跨域单点登录的方法流程图;FIG. 5A is a flowchart of a fourth cross-domain single sign-on method according to an embodiment of the present invention;
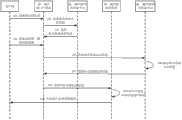
图5B为本发明实施方式单点登录认证信息的结构示意图;5B is a schematic structural diagram of single sign-on authentication information according to an embodiment of the present invention;
图5C为本发明实施方式的单点登录示意图;FIG. 5C is a schematic diagram of a single sign-on according to an embodiment of the present invention;
图6为本发明实施方式的用于单点登录的设备结构示意图。FIG. 6 is a schematic structural diagram of a device for single sign-on according to an embodiment of the present invention.
具体实施方式Detailed ways
如图1A所示,本发明实施方式用于单点登录的方法包括下列步骤:As shown in Figure 1A, the method for single sign-on in the embodiment of the present invention includes the following steps:
第一域的单点登录发起方将通过第一域认证的用户的单点登录认证信息发送给第二域的单点登录中心;The SSO initiator of the first domain sends the SSO authentication information of the user authenticated by the first domain to the SSO center of the second domain;
在所述单点登录认证信息认证通过后,所述单点登录发起方从所述第二域的单点登录中心接收所述用户的跨域单点登录认证信息,其中,所述跨域单点登录认证信息中包含有所述第二域的单点登录中心的签名信息;After the SSO authentication information is authenticated, the SSO initiator receives the cross-domain SSO authentication information of the user from the SSO center of the second domain, wherein the cross-domain SSO The SSO authentication information includes the signature information of the SSO center of the second domain;
所述单点登录发起方向第二域的单点登录接收方发送所述跨域单点登录认证信息。The SSO initiator sends the cross-domain SSO authentication information to the SSO recipient in the second domain.
在本发明的实施例中,单点登录发起方向第二域的单点登录接收方发送所述跨域单点登录认证信息,以用于使第二域的单点登录接收方在跨域单点登录认证信息认证通过后允许用户访问。In an embodiment of the present invention, the SSO initiator sends the cross-domain SSO authentication information to the SSO receiver of the second domain, so that the SSO receiver of the second domain can Click Login Authentication Information to allow users to access after passing the authentication.
这里可以由第二域的单点登录接收方对跨域单点登录认证信息中包含的所述第二域的单点登录中心的签名信息进行认证,也可以由第二域的单点登录中心对跨域单点登录认证信息中包含的所述第二域的单点登录中心的签名信息进行认证并将结果告知第二域的单点登录接收方。Here, the SSO recipient of the second domain may authenticate the signature information of the SSO center of the second domain included in the cross-domain SSO authentication information, or the SSO center of the second domain may Authenticating the signature information of the SSO center of the second domain included in the cross-domain SSO authentication information and notifying the SSO receiver of the second domain of the result.
为了提高传输的安全性,第一域的单点登录发起方可以对所述跨域单点登录认证信息进行加密处理,然后将加密处理后的跨域单点登录认证信息向第二域的单点登录接收方发送。则第二域的单点登录接收方对加密处理后的跨域单点登录认证信息进行解密处理,得到跨域单点登录认证信息。In order to improve transmission security, the SSO initiator in the first domain may encrypt the cross-domain SSO authentication information, and then send the encrypted cross-domain SSO authentication information to the SSO in the second domain. Click to register the receiver to send. Then the SSO receiver in the second domain decrypts the encrypted cross-domain SSO authentication information to obtain the cross-domain SSO authentication information.
通过第一域认证的用户的单点登录认证信息中可以包含有所述用户的认证级别。相应的,单点登录发起方可向第二域的单点登录接收方发送包含用户认证级别的跨域单点登录认证信息,用于通知所述第二域的单点登录接收方对用户的认证级别进行认证,并在认证通过后允许用户访问。The single sign-on authentication information of the user authenticated by the first domain may include the authentication level of the user. Correspondingly, the SSO initiator may send cross-domain SSO authentication information including the user authentication level to the SSO receiver of the second domain, to notify the SSO receiver of the second domain of the user's The authentication level is authenticated, and the user is allowed to access after the authentication is passed.
优选地,在单点登录发起方从第二域的单点登录中心接收用户的跨域单点登录认证信息时,单点登录发起方还从第二域的单点登录中心接收用户的会话标识;在单点登录发起方向第二域的单点登录接收方发送跨域单点登录认证信息时,还向第二域的单点登录接收方发送所述会话标识。第二域的单点登录接收方在会话标识认证通过后才允许用户访问。由于攻击者不能获知会话标识,即使其窃取了单点登录认证信息,也无法访问单点登录接收方,从而能够防止攻击者实施重放攻击,提高了网络的安全性。Preferably, when the SSO initiator receives the user's cross-domain SSO authentication information from the SSO center of the second domain, the SSO initiator also receives the user's session ID from the SSO center of the second domain ; When the SSO initiator sends cross-domain SSO authentication information to the SSO receiver of the second domain, the session identifier is also sent to the SSO receiver of the second domain. The single sign-on receiver of the second domain allows the user to access only after the session ID authentication is passed. Since the attacker cannot obtain the session identifier, even if he steals the SSO authentication information, he cannot access the SSO receiver, thereby preventing the attacker from implementing a replay attack and improving network security.
同样地,单点登录发起方还可对所述会话标识进行加密处理;而第二域的单点登录接收方对加密处理的会话标识相应进行解密处理。Similarly, the SSO initiator can also encrypt the session ID; and the SSO receiver of the second domain correspondingly decrypts the encrypted session ID.
本发明实施方式中的第一域的单点登录发起方可以是用户终端,比如浏览器或其它具有单点登录功能的客户端;也可以是具有单点登录功能的应用系统,如门户设备。用户可以通过多种方式实现单点登录。例如,用户可以通过输入用户名和密码而成功登录到应用系统A上,即完成一次登录。然后,用户再点击应用系统A页面上提供的超级链接而请求访问应用系统B。这时,发出访问请求的应用系统A称作单点登录发起方,而接收访问请求的应用系统B则称为单点登录接收方。可选地,用户还可以直接通过其具有SSO功能的用户终端向单点登录中心进行认证(即完成一次登录),且在认证成功后由其终端直接请求访问各个应用系统。在这种情况下,发出访问请求的用户终端称作单点登录发起方,而接收该访问请求的各个应用系统称作单点登录接收方。进一步,任何一个已经成功认证了用户身份的应用系统都可以作为单点登录发起方,来请求访问另一个应用系统,即单点登录接收方。The single sign-on initiator of the first domain in the embodiment of the present invention may be a user terminal, such as a browser or other client with a single sign-on function; it may also be an application system with a single sign-on function, such as a portal device. Users can implement single sign-on in several ways. For example, a user can successfully log in to the application system A by inputting a user name and a password, that is, a login is completed. Then, the user clicks on the hyperlink provided on the page of application system A to request access to application system B. At this time, the application system A that sends the access request is called the SSO initiator, and the application system B that receives the access request is called the SSO receiver. Optionally, users can also directly authenticate to the single sign-on center through their user terminals with SSO functions (that is, complete one login), and their terminals directly request access to various application systems after successful authentication. In this case, the user terminal that sends out the access request is called the single sign-on initiator, and each application system that receives the access request is called the single sign-on receiver. Furthermore, any application system that has successfully authenticated the user's identity can act as the SSO initiator to request access to another application system, that is, the SSO receiver.
下面以第一域的单点登录发起方为门户设备为例对本发明的实施方式进行说明,在该实施例中,客户端可以为用户的浏览器。第一域的单点登录发起方是用户终端的实施方式与下述实施例的技术原理相同,本领域的技术人员可以参照下述实施例进行适应性的改动。The following describes the implementation of the present invention by taking the SSO initiator of the first domain as a portal device as an example. In this embodiment, the client may be a user's browser. The implementation mode in which the SSO initiator of the first domain is the user terminal is the same as the technical principles of the following embodiments, and those skilled in the art can make adaptive changes with reference to the following embodiments.
如图1B所示,本发明实施方式的第一种进行跨域单点登录的方法包括下列步骤:As shown in Figure 1B, the first cross-domain single sign-on method in the embodiment of the present invention includes the following steps:
步骤101、用户通过其客户端向处于第一域的门户设备发送请求登录的信息;Step 101, the user sends information requesting login to the portal device in the first domain through its client;
步骤102、处于第一域的门户设备收到客户端的请求登录的信息后,在用户的身份验证通过后,向处于第一域的单点登录中心请求获取用户的单点登录认证信息(SSO ticket);Step 102: After the portal device in the first domain receives the login request information from the client, after the user's identity verification is passed, it requests the SSO ticket authentication information (SSO ticket) of the user from the SSO center in the first domain. );
步骤103、第一域中的单点登录中心将用户的单点登录认证信息返回给第一域的门户设备;Step 103, the single sign-on center in the first domain returns the user's single sign-on authentication information to the portal device in the first domain;
步骤104、用户通过其客户端向处于第一域中的门户设备发送请求访问第二域的应用系统;Step 104, the user sends a request to access the application system in the second domain to the portal device in the first domain through its client;
步骤105、第一域中的门户设备将用户的单点登录认证信息发送给第二域中的单点登录中心;Step 105, the portal device in the first domain sends the user's SSO authentication information to the SSO center in the second domain;
步骤106、第二域中的单点登录中心对收到的单点登录认证信息进行认证,在认证通过后,将第二域的签名信息(signature)置于单点登录认证信息中;Step 106, the SSO center in the second domain authenticates the received SSO authentication information, and puts the signature information (signature) of the second domain into the SSO authentication information after the authentication is passed;
步骤107、第二域中的单点登录中心将含有第二域的签名信息的单点登录认证信息返回给第一域中的门户设备;Step 107, the single sign-on center in the second domain returns the single sign-on authentication information containing the signature information of the second domain to the portal device in the first domain;
步骤108、第一域中的门户设备将含有第二域的签名信息的单点登录认证信息发送给第二域中的应用系统;Step 108, the portal device in the first domain sends the single sign-on authentication information containing the signature information of the second domain to the application system in the second domain;
步骤109、第二域中的应用系统对收到的单点登录认证信息中的第二域的签名信息进行认证;Step 109, the application system in the second domain authenticates the signature information of the second domain in the received SSO authentication information;
步骤110、第二域中的应用系统在单点登录认证信息中的第二域的签名信息认证通过后,允许用户访问应用系统。Step 110, the application system in the second domain allows the user to access the application system after the signature information of the second domain in the single sign-on authentication information is authenticated.
在步骤102中,第一域中的门户设备向处于第一域的单点登录中心请求用户的单点登录认证信息时,可以将用户标识发送给第一域的单点登录中心;相应的,步骤103中,第一域的单点登录中心可以将该用户标识对应的用户的认证级别置于用户的单点登录认证信息中。In step 102, when the portal device in the first domain requests the user's SSO authentication information from the SSO center in the first domain, it may send the user ID to the SSO center in the first domain; correspondingly, In step 103, the single sign-on center of the first domain may set the authentication level of the user corresponding to the user identifier into the user's single sign-on authentication information.
从而在步骤108中,第一域的门户设备可以将包含有用户认证级别的单点登录认证信息发送给第二域中的应用系统。Therefore, in step 108, the portal device in the first domain may send the single sign-on authentication information including the user authentication level to the application system in the second domain.
第一域中的门户设备可以根据步骤104中客户端发送的访问请求确定单点登录的接收方处在第一域还是第二域。客户端发送的访问请求中可以包含请求访问的URL地址,也可以包含待访问应用系统的标识,还可以包含其它能够确定单点登录接收方的信息。如果客户端请求访问一个URL地址,则第一域中的门户设备可以根据该URL地址判断该URL地址是否与其处在同一认证域;如果客户端发送请求中包含被访问应用系统的标识,则第一域中的门户设备可以根据应用系统标识和认证域的对应关系,确定需要访问的应用系统属于哪个认证域。The portal device in the first domain may determine whether the recipient of the single sign-on is in the first domain or the second domain according to the access request sent by the client in step 104 . The access request sent by the client may include the URL address requested for access, may also include the identifier of the application system to be accessed, and may also include other information capable of determining the recipient of the single sign-on. If the client requests to access a URL address, the portal device in the first domain can judge whether the URL address is in the same authentication domain as the URL address; if the request sent by the client includes the identifier of the accessed application system, the second The portal device in a domain can determine which authentication domain the application system to be accessed belongs to according to the corresponding relationship between the application system identifier and the authentication domain.
在步骤105中,第一域中的门户设备还可以将用户需要访问的应用系统的标识(APP ID)发送给第二域中的单点登录中心,供第二域中的单点登录中心确定被访问的应用系统。In step 105, the portal device in the first domain can also send the identification (APP ID) of the application system that the user needs to access to the SSO center in the second domain for the SSO center in the second domain to determine The application system being accessed.
在步骤106中,第二域中的单点登录中心对收到的单点登录认证信息进行认证时,可对单点登录认证信息中第一域的签名信息进行认证,在认证通过后,如果单点登录认证信息中有单点登录认证信息创建时间和单点登录认证信息到期时间,则第二域中的单点登录中心还可对单点登录认证信息创建时间和单点登录认证信息到期时间进行认证,查看该单点登录认证信息是否还有效。In step 106, when the SSO center in the second domain authenticates the received SSO authentication information, it may authenticate the signature information of the first domain in the SSO authentication information. After the authentication is passed, if The SSO authentication information includes the SSO authentication information creation time and the SSO authentication information expiration time, then the SSO center in the second domain can also set the SSO authentication information creation time and SSO authentication information Authenticate at the expiration time, and check whether the SSO authentication information is still valid.
单点登录认证信息中除了签名信息,根据需要还可以包括其他能够对用户单点登录认证信息的合法性进行验证的信息,则第二域中的单点登录中心还可以根据该信息对单点登录认证信息进行验证。In addition to the signature information, the single sign-on authentication information may also include other information that can verify the legitimacy of the user's single sign-on authentication information, and the single sign-on center in the second domain can also verify the single sign-on Login authentication information for verification.
为了进一步提高跨域单点登录的安全性,在单点登录中增加了会话标识(Session ID)。图2为本发明实施方式的第二种进行跨域单点登录的方法,其中步骤201~步骤205与图1中的步骤101~步骤105相同,在此不再赘述,这里只介绍不同之处:In order to further improve the security of cross-domain single sign-on, a session ID (Session ID) is added to single sign-on. Fig. 2 is the second cross-domain single sign-on method according to the embodiment of the present invention, in which steps 201 to 205 are the same as steps 101 to 105 in Fig. 1, and will not be repeated here, only the differences are introduced here :
步骤206、第二域中的单点登录中心对收到的单点登录认证信息进行认证,在认证通过后,将第二域的签名信息置于单点登录认证信息中,并为用户分配一个会话标识;Step 206, the single sign-on center in the second domain authenticates the received single sign-on authentication information, and after passing the authentication, puts the signature information of the second domain in the single sign-on authentication information, and assigns a user session ID;
步骤207、第二域中的单点登录中心将含有第二域的签名信息的单点登录认证信息和会话标识返回给第一域中的门户设备;Step 207, the single sign-on center in the second domain returns the single sign-on authentication information and session ID containing the signature information of the second domain to the portal device in the first domain;
步骤208、第一域中的门户设备将含有第二域的签名信息的单点登录认证信息和会话标识返回给客户端;Step 208, the portal device in the first domain returns the single sign-on authentication information and session ID containing the signature information of the second domain to the client;
步骤209、客户端将收到的跨域单点登录认证信息和会话标识发送给第二域中的应用系统;Step 209, the client sends the received cross-domain single sign-on authentication information and session identifier to the application system in the second domain;
步骤210、第二域中的应用系统将跨域单点登录认证信息和会话标识发送给第二域中的单点登录中心;Step 210, the application system in the second domain sends the cross-domain SSO authentication information and session ID to the SSO center in the second domain;
步骤211、第二域中的单点登录中心对跨域的单点登录认证信息和会话标识进行认证,并在步骤212中返回认证结果;Step 211, the single sign-on center in the second domain authenticates the cross-domain single sign-on authentication information and session identification, and returns the authentication result in step 212;
步骤213、第二域中的应用系统在认证通过后允许用户访问应用系统。Step 213, the application system in the second domain allows the user to access the application system after passing the authentication.
在本实施例中,根据实际的需求,在步骤208和209中,第一域的门户设备可以使用URL重定向和HTTP POST的方式通过客户端将用户的跨域单点登录信息发送给第二域中的应用系统。In this embodiment, according to actual needs, in steps 208 and 209, the portal device of the first domain can use URL redirection and HTTP POST to send the user's cross-domain single sign-on information to the second domain through the client. application systems in the domain.
会话标识可以是一个随机生成的数字或时间戳,也可以是其他能够唯一标识一个会话的信息。由于攻击者不能获知会话标识,也就无法访问应用系统,从而提高了网络的安全环境。A session ID can be a randomly generated number or timestamp, or other information that can uniquely identify a session. Since the attacker cannot obtain the session ID, he cannot access the application system, thereby improving the security environment of the network.
其中,会话标识也可以不随单点登录认证信息传输,只要保证在步骤210之前第二域中的应用系统能够收到会话标识即可。Wherein, the session identifier may not be transmitted along with the SSO authentication information, as long as it is ensured that the application system in the second domain can receive the session identifier before step 210 .
为了提高会话标识在传输中的安全性,优选地,步骤208中,第一域中的门户设备对会话标识进行加密处理,并将加密处理后的会话标识返回给客户端;相应的,步骤209中,客户端将加密处理后的会话标识发送给第二域中的应用系统;步骤210中,第二域中的应用系统对收到的加密处理后的会话标识进行解密处理。In order to improve the security of the session ID during transmission, preferably, in step 208, the portal device in the first domain encrypts the session ID, and returns the encrypted session ID to the client; correspondingly, step 209 , the client sends the encrypted session ID to the application system in the second domain; in step 210, the application system in the second domain decrypts the received encrypted session ID.
图3为本发明实施方式的第三种进行跨域单点登录的方法,其中除步骤303及步骤309不同以外,其余与图1中的相应步骤相同,在此不再赘述,这里只介绍不同之处:Fig. 3 is the third cross-domain single sign-on method according to the embodiment of the present invention, except for step 303 and step 309, the rest are the same as the corresponding steps in Fig. 1, and will not be repeated here, only the differences are introduced here Where:
步骤303、第一域中的单点登录中心请求将包含用户认证级别的单点登录认证信息返回给第一域中的门户设备;Step 303, the SSO center in the first domain requests to return the SSO authentication information including the user authentication level to the portal device in the first domain;
步骤309、第二域中的应用系统在单点登录认证信息中的第二域的签名信息认证通过,且用户的认证级别满足应用系统的认证级别后,允许用户访问应用系统。Step 309: After the application system in the second domain passes the authentication of the signature information of the second domain in the single sign-on authentication information, and the authentication level of the user meets the authentication level of the application system, the user is allowed to access the application system.
认证级别根据需要可以划分多个级别,比如认证级别是“0”表示:静态口令认证;认证级别是“1”表示:一次性口令认证;认证级别是“2”表示:证书认证。当然,还可以根据具体需要划分更多的认证级别。步骤303中,第一域中的单点登录中心根据用户的认证方式确定对应的认证级别。比如用户采用一次性口令登录成功,则确定用户认证级别是“1”。The authentication level can be divided into multiple levels according to the needs. For example, the authentication level is "0" means: static password authentication; the authentication level is "1" means: one-time password authentication; the authentication level is "2" means: certificate authentication. Of course, more certification levels can be divided according to specific needs. In step 303, the single sign-on center in the first domain determines the corresponding authentication level according to the authentication mode of the user. For example, if the user successfully logs in using the one-time password, it is determined that the user authentication level is "1".
不同的应用系统可能有不同的认证级别。如果应用系统需要的认证级别是“一次性口令认证”,对于通过“静态口令认证”的用户不能访问应用系统,对于通过“一次性口令认证”或“证书认证”的用户能访问应用系统。Different application systems may have different certification levels. If the authentication level required by the application system is "one-time password authentication", users who pass "static password authentication" cannot access the application system, and users who pass "one-time password authentication" or "certificate authentication" can access the application system.
下面以图4的应用环境为例,对本发明实施方式进行说明。The following describes the implementation of the present invention by taking the application environment in FIG. 4 as an example.
如图5A所示,本发明实施方式的第四种进行跨域单点登录的方法中,单点登录认证信息的结构可以参见图5B,具体步骤包括:As shown in FIG. 5A, in the fourth cross-domain single sign-on method of the embodiment of the present invention, the structure of the single sign-on authentication information can be referred to in FIG. 5B, and the specific steps include:
步骤501、客户端向省级门户设备(Provincial Portal)发送请求登录的信息;Step 501, the client sends information requesting login to the provincial portal device (Provincial Portal);
步骤502、省级门户设备向省级单点登录中心(Provincial SSO)请求获取用户的单点登录认证信息;Step 502, the provincial portal device requests the provincial single sign-on center (Provincial SSO) to obtain the user's single sign-on authentication information;
步骤503、省级单点登录中心将包含用户认证级别的单点登录认证信息返回给省级门户设备;Step 503, the provincial SSO center returns the SSO authentication information including the user authentication level to the provincial portal device;
步骤504、客户端向省级门户设备发送请求访问总部应用系统的信息;Step 504, the client sends information requesting access to the headquarters application system to the provincial portal device;
步骤505、省级门户设备将用户的单点登录认证信息发送给总部的单点登录中心,并申请会话标识;Step 505, the provincial portal device sends the user's single sign-on authentication information to the headquarters' single sign-on center, and applies for a session ID;
步骤506、总部的单点登录中心对收到的单点登录认证信息进行认证,在认证通过后,将总部的签名信息置于单点登录认证信息中;Step 506, the SSO center of the headquarter authenticates the received SSO authentication information, and puts the signature information of the headquarters into the SSO authentication information after the authentication is passed;
步骤507、总部的单点登录中心为用户分配一个会话标识;Step 507, the single sign-on center of the headquarters assigns a session ID to the user;
步骤508、总部的单点登录中心将含有总部签名信息的单点登录认证信息和会话标识返回给省级门户设备;Step 508, the single sign-on center of the headquarters returns the single sign-on authentication information and the session ID containing the signature information of the headquarters to the provincial portal device;
步骤509、省级门户设备对单点登录认证信息进行升级,将用户的单点登录认证信息更新为含有总部签名的单点登录认证信息;Step 509, the provincial portal device upgrades the single sign-on authentication information, and updates the user's single sign-on authentication information to the single sign-on authentication information containing the signature of the headquarters;
步骤510、省级门户设备对会话标识进行加密处理;Step 510, the provincial portal device encrypts the session identifier;
步骤511、省级门户设备将加密处理后的会话标识和单点登录认证信息返回给客户端;Step 511, the provincial portal device returns the encrypted session identifier and single sign-on authentication information to the client;
步骤512、客户端将加密处理后的会话标识和单点登录认证信息发送给总部的应用系统;Step 512, the client sends the encrypted session identifier and single sign-on authentication information to the application system of the headquarters;
步骤513、总部的应用系统对收到的会话标识进行解密处理;Step 513, the application system of the headquarters decrypts the received session identifier;
步骤514、总部的应用系统对收到的单点登录认证信息中的总部的签名信息进行认证;Step 514, the application system of the headquarters authenticates the signature information of the headquarters in the received SSO authentication information;
步骤515、总部的应用系统在总部的签名信息认证通过后,将会话标识发送给总部的单点登录中心;Step 515, the application system of the headquarters sends the session identifier to the single sign-on center of the headquarters after the signature information authentication of the headquarters is passed;
步骤516、总部的单点登录中心对会话标识进行认证;Step 516, the single sign-on center of the headquarters authenticates the session ID;
步骤517、总部的单点登录中心返回认证结果;Step 517, the single sign-on center of the headquarters returns the authentication result;
步骤518、总部的应用系统根据认证结果在确定会话标识认证通过后,对用户的认证级别和应用系统的认证级别进行比较;Step 518: The application system at the headquarters compares the authentication level of the user with the authentication level of the application system after determining that the session ID authentication has passed according to the authentication result;
步骤519、总部的应用系统在用户的认证级别满足应用系统的认证级别后,允许用户访问应用系统。Step 519: After the user's authentication level meets the authentication level of the application system, the application system at the headquarters allows the user to access the application system.
下面以图5C的应用环境为例,对本发明实施方式进行说明。The following describes the implementation of the present invention by taking the application environment of FIG. 5C as an example.
1、一个用户访问省级门户网站,并通过认证;1. A user visits the provincial portal website and passes the authentication;
2、省级门户网站通过省级单点登录中心,实现用户的单点登录;2. The provincial portal website realizes the single sign-on of users through the provincial single sign-on center;
3、用户单点登录到ERP(企业资源规划系统)系统;3. User single sign-on to the ERP (Enterprise Resource Planning System) system;
4、用户希望单点登录到位于总部的一个学习系统中,省级门户网站通过总部的单点登录中心申请到含有总部的签名信息的单点登录认证信息和会话标识;4. The user wants to single-sign on to a learning system located at the headquarters, and the provincial portal website applies for the single-sign-on authentication information and session ID containing the signature information of the headquarters through the single-sign-on center of the headquarters;
5、用户根据含有总部的签名信息的单点登录认证信息和会话标识就可以单点登录到总部的学习系统中。5. The user can single-sign on to the learning system of the headquarters according to the single-sign-on authentication information and the session ID containing the signature information of the headquarters.
基于同一发明构思,本发明实施例中还提供了一种与用于单点登录的方法对应的用于单点登录的设备,由于该设备解决问题的原理与用于单点登录的方法相似,因此该设备的实施方式可以参见根据本发明方法的实施例,重复之处不再赘述。Based on the same inventive concept, the embodiment of the present invention also provides a device for single sign-on corresponding to the method for single sign-on, since the principle of solving the problem of this device is similar to the method for single sign-on, Therefore, for the implementation of the device, reference may be made to the embodiment of the method according to the present invention, and repeated descriptions will not be repeated.
如图6所示,发明实施方式的用于单点登录的设备包括:发送模块61、接收模块62和处理模块63。As shown in FIG. 6 , the device for single sign-on in the embodiment of the invention includes: a sending
发送模块61,用于将通过第一域认证的用户的单点登录认证信息发送给第二域的单点登录中心;The sending
接收模块62,用于在所述单点登录认证信息认证通过后,所述单点登录发起方从所述第二域的单点登录中心接收所述用户的跨域单点登录认证信息,其中,所述跨域单点登录认证信息中包含有所述第二域的单点登录中心的签名信息;The receiving
处理模块63,用于向第二域的单点登录接收方发送所述跨域单点登录认证信息。The
优选地,所述设备还包括:第一加密模块64:用于在所述处理模块63向第二域的单点登录接收方发送所述跨域单点登录认证信息之前,对所述跨域单点登录认证信息进行加密处理。Preferably, the device further includes: a first encryption module 64: configured to encrypt the cross-domain SSO authentication information before the
优选地,发送模块61还用于:将通过第一域认证的用户的单点登录认证信息发送给第二域的单点登录中心之前,向第一域中的单点登录中心申请所述单点登录认证信息,所述单点登录认证信息中包含有所述用户的认证级别。Preferably, the sending
优选地,接收模块62还用于:在从所述第二域的单点登录中心接收所述用户的跨域单点登录认证信息时,还从所述第二域的单点登录中心接收所述用户的会话标识;处理模块63还用于在向第二域的单点登录接收方发送所述跨域单点登录认证信息时,还向所述第二域的单点登录接收方发送所述会话标识。Preferably, the receiving
优选地,所述设备还包括:第二加密模块65:用于在所述处理模块63向第二域的单点登录接收方发送所述会话标识之前,对所述会话标识进行加密处理。Preferably, the device further includes: a
需要说明的是,上述各流程和各系统结构图中不是所有的步骤和模块都是必须的,可以根据实际的需要忽略某些步骤或模块。各步骤的执行顺序不是固定的,可以根据需要进行调整。上述各实施例中描述的系统结构可以是物理结构,也可以是逻辑结构,即,有些模块可能由同一物理实体实现,或者,有些模块可能分由多个物理实体实现,或者,可以由多个独立设备中的某些部件共同实现。It should be noted that not all the steps and modules in the above processes and system structure diagrams are necessary, and some steps or modules can be ignored according to actual needs. The execution order of each step is not fixed and can be adjusted as required. The system structures described in the above embodiments may be physical structures or logical structures, that is, some modules may be realized by the same physical entity, or some modules may be realized by multiple physical entities, or may be realized by multiple Certain components in individual devices are implemented together.
以上各实施例中,硬件单元可以通过机械方式或电气方式实现。例如,一个硬件单元可以包括永久性专用的电路或逻辑(如专门的处理器,FPGA或ASIC)来完成相应操作。硬件单元还可以包括可编程逻辑或电路(如通用处理器或其它可编程处理器),可以由软件进行临时的设置以完成相应操作。具体的实现方式(机械方式、或专用的永久性电路、或者临时设置的电路)可以基于成本和时间上的考虑来确定。In the above embodiments, the hardware unit may be implemented mechanically or electrically. For example, a hardware unit may include permanently dedicated circuitry or logic (such as a dedicated processor, FPGA, or ASIC) to perform the corresponding operations. The hardware unit may also include programmable logic or circuits (such as general-purpose processors or other programmable processors), which can be temporarily set by software to complete corresponding operations. The specific implementation (mechanical way, or dedicated permanent circuit, or temporarily set circuit) can be determined based on cost and time considerations.
本发明还提供了一种机器可读介质,存储用于使一机器执行如本文所述的用于单点登录的方法的指令。具体地,可以提供配有存储介质的系统或者装置,在该存储介质上存储着实现上述实施例中任一实施例的功能的软件程序代码,且使该系统或者装置的计算机(或CPU或MPU)读出并执行存储在存储介质中的程序代码。The present invention also provides a machine-readable medium storing instructions for causing a machine to execute the method for single sign-on as described herein. Specifically, a system or device equipped with a storage medium may be provided, on which the software program code for realizing the functions of any of the above embodiments is stored, and the computer (or CPU or MPU of the system or device) ) to read and execute the program code stored in the storage medium.
在这种情况下,从存储介质读取的程序代码本身可实现上述实施例中任何一项实施例的功能,因此程序代码和存储程序代码的存储介质构成了本发明的一部分。In this case, the program code itself read from the storage medium can realize the function of any one of the above-mentioned embodiments, so the program code and the storage medium storing the program code constitute a part of the present invention.
用于提供程序代码的存储介质实施例包括软盘、硬盘、磁光盘、光盘(如CD-ROM、CD-R、CD-RW、DVD-ROM、DVD-RAM、DVD-RW、DVD+RW)、磁带、非易失性存储卡和ROM。可选择地,可以由通信网络从服务器计算机上下载程序代码。Examples of storage media for providing program code include floppy disks, hard disks, magneto-optical disks, optical disks (such as CD-ROM, CD-R, CD-RW, DVD-ROM, DVD-RAM, DVD-RW, DVD+RW), Tape, non-volatile memory card, and ROM. Alternatively, the program code can be downloaded from a server computer via a communication network.
此外,应该清楚的是,不仅可以通过执行计算机所读出的程序代码,而且可以通过基于程序代码的指令使计算机上操作的操作系统等来完成部分或者全部的实际操作,从而实现上述实施例中任意一项实施例的功能。In addition, it should be clear that not only by executing the program code read by the computer, but also by making the operating system on the computer complete part or all of the actual operations through instructions based on the program code, so as to realize the function of any one of the embodiments.
此外,可以理解的是,将由存储介质读出的程序代码写到插入计算机内的扩展板中所设置的存储器中或者写到与计算机相连接的扩展单元中设置的存储器中,随后基于程序代码的指令使安装在扩展板或者扩展单元上的CPU等来执行部分和全部实际操作,从而实现上述实施例中任一实施例的功能。In addition, it can be understood that the program code read from the storage medium is written into the memory provided in the expansion board inserted into the computer or written into the memory provided in the expansion unit connected to the computer, and then based on the program code The instruction causes the CPU installed on the expansion board or the expansion unit to perform some or all of the actual operations, so as to realize the functions of any one of the above-mentioned embodiments.
上文通过附图和优选实施方式对本发明进行了详细展示和说明,然而本发明不限于这些已揭示的实施方式,本领域技术人员从中推导出来的其它方案也在本发明的保护范围之内。The present invention has been shown and described in detail through the drawings and preferred embodiments above, but the present invention is not limited to these disclosed embodiments, and other schemes deduced therefrom by those skilled in the art are also within the protection scope of the present invention.
Claims (11)
Priority Applications (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201210379442.2ACN103716292A (en) | 2012-09-29 | 2012-09-29 | Cross-domain single-point login method and device thereof |
| PCT/EP2013/068819WO2014048749A1 (en) | 2012-09-29 | 2013-09-11 | Inter-domain single sign-on |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201210379442.2ACN103716292A (en) | 2012-09-29 | 2012-09-29 | Cross-domain single-point login method and device thereof |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN103716292Atrue CN103716292A (en) | 2014-04-09 |
Family
ID=49182239
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN201210379442.2APendingCN103716292A (en) | 2012-09-29 | 2012-09-29 | Cross-domain single-point login method and device thereof |
Country Status (2)
| Country | Link |
|---|---|
| CN (1) | CN103716292A (en) |
| WO (1) | WO2014048749A1 (en) |
Cited By (13)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2015176500A1 (en)* | 2014-05-21 | 2015-11-26 | 西安中兴新软件有限责任公司 | Single sign-on authentication method, device and system, and computer storage medium |
| CN105721412A (en)* | 2015-06-24 | 2016-06-29 | 乐视云计算有限公司 | Method and device for authenticating identity between multiple systems |
| CN105812350A (en)* | 2016-02-03 | 2016-07-27 | 北京中搜云商网络技术有限公司 | Cross-platform single-point registration system |
| CN105991602A (en)* | 2015-02-26 | 2016-10-05 | 北京神州泰岳信息安全技术有限公司 | Data access method and data access system |
| CN107835099A (en)* | 2017-11-29 | 2018-03-23 | 新华三信息安全技术有限公司 | A kind of information synchronization method and device |
| CN107835165A (en)* | 2017-10-27 | 2018-03-23 | 北京慧点科技有限公司 | The system and method for single sign-on |
| CN108718301A (en)* | 2018-05-09 | 2018-10-30 | 广州市冰海网络技术有限公司 | A kind of method of remote system single-sign-on |
| CN109246146A (en)* | 2018-11-01 | 2019-01-18 | 北京京航计算通讯研究所 | SAP ERP single-point logging method based on JAVA middleware intergration model |
| CN109492375A (en)* | 2018-11-01 | 2019-03-19 | 北京京航计算通讯研究所 | SAP ERP single-node login system based on JAVA middleware intergration model |
| CN111651747A (en)* | 2020-05-11 | 2020-09-11 | 腾讯科技(深圳)有限公司 | Login bill synchronization system and method and related equipment |
| US20210037005A1 (en)* | 2019-07-30 | 2021-02-04 | Dell Products L.P. | System And Method Of Single Sign On To Master Website And Silent Authentication For Subservient Websites |
| CN116471073A (en)* | 2023-04-13 | 2023-07-21 | 南京坚卓软件科技有限公司 | A cross-border multi-store operation management platform account single sign-on processing system and method |
| CN119520175A (en)* | 2025-01-22 | 2025-02-25 | 麒麟软件有限公司 | Terminal cross-domain management method, device, equipment and product |
Families Citing this family (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US10021084B2 (en)* | 2014-10-28 | 2018-07-10 | Open Text Sa Ulc | Systems and methods for credentialing of non-local requestors in decoupled systems utilizing a domain local authenticator |
| CN104378376B (en)* | 2014-11-18 | 2019-02-26 | 深圳中兴网信科技有限公司 | SOA-based single sign-on method, authentication server and browser |
| CN104468589A (en)* | 2014-12-12 | 2015-03-25 | 上海斐讯数据通信技术有限公司 | Method and system for achieving lightweight-level conversation |
| CN104506555A (en)* | 2015-01-06 | 2015-04-08 | 北京艾力泰尔信息技术有限公司 | Client zero-storage single sign-on method |
| CN106850517A (en)* | 2015-12-04 | 2017-06-13 | 北京京东尚科信息技术有限公司 | A kind of method, apparatus and system for solving intranet and extranet repeat logon |
| CN108200107B (en)* | 2018-03-30 | 2020-08-14 | 浙江网新恒天软件有限公司 | Method for realizing single sign-on in multi-domain environment |
Citations (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20040128542A1 (en)* | 2002-12-31 | 2004-07-01 | International Business Machines Corporation | Method and system for native authentication protocols in a heterogeneous federated environment |
| CN1745356A (en)* | 2002-03-18 | 2006-03-08 | 特伦诺有限公司 | Single sign-on secure service access |
| CN101133421A (en)* | 2005-04-01 | 2008-02-27 | 国际商业机器公司 | Method for runtime user account creation operations |
| CN102045329A (en)* | 2009-10-22 | 2011-05-04 | 中国移动通信集团公司 | Single point login method, login initiating terminal, target terminal and verification center |
| US20110119747A1 (en)* | 2009-11-17 | 2011-05-19 | Mark Lambiase | Single sign on with multiple authentication factors |
| US20120222104A1 (en)* | 2011-02-28 | 2012-08-30 | Nokia Corporation | Method and apparatus for providing single sign-on for computation closures |
- 2012
- 2012-09-29CNCN201210379442.2Apatent/CN103716292A/enactivePending
- 2013
- 2013-09-11WOPCT/EP2013/068819patent/WO2014048749A1/enactiveApplication Filing
Patent Citations (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN1745356A (en)* | 2002-03-18 | 2006-03-08 | 特伦诺有限公司 | Single sign-on secure service access |
| US20040128542A1 (en)* | 2002-12-31 | 2004-07-01 | International Business Machines Corporation | Method and system for native authentication protocols in a heterogeneous federated environment |
| CN101133421A (en)* | 2005-04-01 | 2008-02-27 | 国际商业机器公司 | Method for runtime user account creation operations |
| CN102045329A (en)* | 2009-10-22 | 2011-05-04 | 中国移动通信集团公司 | Single point login method, login initiating terminal, target terminal and verification center |
| US20110119747A1 (en)* | 2009-11-17 | 2011-05-19 | Mark Lambiase | Single sign on with multiple authentication factors |
| US20120222104A1 (en)* | 2011-02-28 | 2012-08-30 | Nokia Corporation | Method and apparatus for providing single sign-on for computation closures |
Cited By (19)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2015176500A1 (en)* | 2014-05-21 | 2015-11-26 | 西安中兴新软件有限责任公司 | Single sign-on authentication method, device and system, and computer storage medium |
| CN105991602A (en)* | 2015-02-26 | 2016-10-05 | 北京神州泰岳信息安全技术有限公司 | Data access method and data access system |
| CN105721412A (en)* | 2015-06-24 | 2016-06-29 | 乐视云计算有限公司 | Method and device for authenticating identity between multiple systems |
| CN105812350A (en)* | 2016-02-03 | 2016-07-27 | 北京中搜云商网络技术有限公司 | Cross-platform single-point registration system |
| CN107835165B (en)* | 2017-10-27 | 2021-05-28 | 北京慧点科技有限公司 | Single sign-on system and method |
| CN107835165A (en)* | 2017-10-27 | 2018-03-23 | 北京慧点科技有限公司 | The system and method for single sign-on |
| CN107835099A (en)* | 2017-11-29 | 2018-03-23 | 新华三信息安全技术有限公司 | A kind of information synchronization method and device |
| CN107835099B (en)* | 2017-11-29 | 2021-09-03 | 新华三信息安全技术有限公司 | Information synchronization method and device |
| CN108718301A (en)* | 2018-05-09 | 2018-10-30 | 广州市冰海网络技术有限公司 | A kind of method of remote system single-sign-on |
| CN109246146A (en)* | 2018-11-01 | 2019-01-18 | 北京京航计算通讯研究所 | SAP ERP single-point logging method based on JAVA middleware intergration model |
| CN109492375A (en)* | 2018-11-01 | 2019-03-19 | 北京京航计算通讯研究所 | SAP ERP single-node login system based on JAVA middleware intergration model |
| CN109246146B (en)* | 2018-11-01 | 2020-10-13 | 北京京航计算通讯研究所 | SAP ERP single sign-on method based on JAVA middleware integration mode |
| CN109492375B (en)* | 2018-11-01 | 2021-07-16 | 北京京航计算通讯研究所 | SAP ERP single sign-on system based on JAVA middleware integration mode |
| US20210037005A1 (en)* | 2019-07-30 | 2021-02-04 | Dell Products L.P. | System And Method Of Single Sign On To Master Website And Silent Authentication For Subservient Websites |
| US11570164B2 (en)* | 2019-07-30 | 2023-01-31 | Dell Products L.P. | System and method of single sign on to master website and silent authentication for subservient websites |
| CN111651747A (en)* | 2020-05-11 | 2020-09-11 | 腾讯科技(深圳)有限公司 | Login bill synchronization system and method and related equipment |
| CN111651747B (en)* | 2020-05-11 | 2024-05-24 | 腾讯科技(深圳)有限公司 | Login bill synchronization system and method and related equipment |
| CN116471073A (en)* | 2023-04-13 | 2023-07-21 | 南京坚卓软件科技有限公司 | A cross-border multi-store operation management platform account single sign-on processing system and method |
| CN119520175A (en)* | 2025-01-22 | 2025-02-25 | 麒麟软件有限公司 | Terminal cross-domain management method, device, equipment and product |
Also Published As
| Publication number | Publication date |
|---|---|
| WO2014048749A1 (en) | 2014-04-03 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN103716292A (en) | Cross-domain single-point login method and device thereof | |
| TWI706263B (en) | Trust registration method, server and system | |
| US11095635B2 (en) | Server authentication using multiple authentication chains | |
| US12250209B2 (en) | Network identity protection method and device, and electronic equipment and storage medium | |
| US9871791B2 (en) | Multi factor user authentication on multiple devices | |
| CN102201915B (en) | A terminal authentication method and device based on single sign-on | |
| TWI725958B (en) | Cloud host service authority control method, device and system | |
| US9838205B2 (en) | Network authentication method for secure electronic transactions | |
| CN101227468B (en) | Method, device and system for authenticating user to network | |
| CN101997685B (en) | Single sign-on method, single sign-on system, and related equipment | |
| US8532620B2 (en) | Trusted mobile device based security | |
| US20170244676A1 (en) | Method and system for authentication | |
| CN104065616B (en) | Single-point logging method and system | |
| CN110677376B (en) | Authentication method, related device and system and computer readable storage medium | |
| KR20120055728A (en) | Method and apparatus for trusted authentication and logon | |
| WO2014182865A1 (en) | Authentication and authorization with a bundled token | |
| CN105429991A (en) | Efficient data transmission method for mobile terminal | |
| US11924211B2 (en) | Computerized device and method for authenticating a user | |
| CN105024813A (en) | A server, a user equipment, and an interaction method between the user equipment and the server | |
| KR102062851B1 (en) | Single sign on service authentication method and system using token management demon | |
| CN105577606B (en) | A kind of method and apparatus for realizing authenticator registration | |
| US20220321345A1 (en) | Secure exchange of session tokens for claims-based tokens in an extensible system | |
| TWI698113B (en) | Identification method and systerm of electronic device | |
| CN114003892B (en) | Trusted authentication method, secure authentication device, and user terminal | |
| CN108965270A (en) | The method and apparatus for realizing access verifying |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| C06 | Publication | ||
| PB01 | Publication | ||
| C10 | Entry into substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| WD01 | Invention patent application deemed withdrawn after publication | ||
| WD01 | Invention patent application deemed withdrawn after publication | Application publication date:20140409 |