CN101867530A - Internet of things gateway system and data interaction method based on virtual machine - Google Patents
Internet of things gateway system and data interaction method based on virtual machineDownload PDFInfo
- Publication number
- CN101867530A CN101867530ACN 201010188081CN201010188081ACN101867530ACN 101867530 ACN101867530 ACN 101867530ACN 201010188081CN201010188081CN 201010188081CN 201010188081 ACN201010188081 ACN 201010188081ACN 101867530 ACN101867530 ACN 101867530A
- Authority
- CN
- China
- Prior art keywords
- module
- virtual machine
- data
- user
- information
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
Images
Landscapes
- Data Exchanges In Wide-Area Networks (AREA)
- Computer And Data Communications (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明属于通信技术领域,涉及物联网中的网关结构设计与使用,具体是一种基于虚拟机技术的物联网融合网关系统和使用方法,应用于物联网中不同网络间融合的通信和安全领域。The invention belongs to the field of communication technology, and relates to the design and use of a gateway structure in the Internet of Things, specifically an Internet of Things fusion gateway system based on virtual machine technology and a method for using it, which is applied to the communication and security fields of fusion between different networks in the Internet of Things .
背景技术Background technique
“物联网”这一概念是在互联网概念的基础上,将其用户端延伸和扩展到任何物品与物品之间,进行信息交换和通信的一种网络概念。其中无线传感器网络、RFID网络等作为末端感应网络,与现有的Internet网络或无线通信网络互联,通过相应协议把实际的物品与互联网相连接,进行信息交换和通信的一种网络结构的概念。物联网最早源于对无线传感网络的研究。2005年,国际电信联盟(ITU)正式提出了“物联网”的概念。The concept of "Internet of Things" is a network concept that extends and expands its client terminal to any item and item for information exchange and communication on the basis of the concept of the Internet. Among them, the wireless sensor network, RFID network, etc. are used as the terminal sensing network, interconnected with the existing Internet network or wireless communication network, and connect the actual items with the Internet through corresponding protocols for information exchange and communication. A network structure concept. The Internet of Things originated from the research on wireless sensor networks. In 2005, the International Telecommunication Union (ITU) formally proposed the concept of "Internet of Things".
物联网被认为拥有“更透彻的感知,更广泛的互联互通,更深入的智能化”,物联网产业被认为是继计算机产业、通信产业后的又一次信息技术浪潮,据权威机构预测:未来物联网产业将是互联网产业的30倍。物联网可以应用于智能化识别、定位、跟踪、监控和管理等诸多行业和领域。在智能家庭、医疗保健、环境监测等方面都已经开始进行了逐步的应用。而随着“感知中国”、“智慧地球”等概念的提出,物联网进入了加速发展的阶段,逐渐开始进行较大范围的应用。The Internet of Things is considered to have "more thorough perception, wider interconnection, and deeper intelligence". The Internet of Things industry is considered to be another wave of information technology after the computer industry and the communication industry. The IoT industry will be 30 times larger than the Internet industry. The Internet of Things can be applied to many industries and fields such as intelligent identification, positioning, tracking, monitoring and management. It has been gradually applied in smart home, health care, environmental monitoring and other aspects. With the introduction of concepts such as "perceiving China" and "smart earth", the Internet of Things has entered a stage of accelerated development and gradually began to be applied in a wider range.
“虚拟机”最早可追溯到IBM的VM/370。使用虚拟机技术可以在在一台物理计算机上模拟出一台或多台虚拟的计算机,这些虚拟机完全就像真正的计算机那样进行工作。而由于虚拟机技术可以良好的隔离不同的应用,它可以用于隔离不同安全性的应用,进而防止较为危险的应用对安全性要求较高的应用产生不良的影响。因此在安全方面已经有一些基于虚拟机的安全方案的研究和探索。The "virtual machine" can be traced back to IBM's VM/370. Using virtual machine technology, one or more virtual computers can be simulated on a physical computer, and these virtual machines work exactly like real computers. And because the virtual machine technology can well isolate different applications, it can be used to isolate applications with different security, thereby preventing more dangerous applications from adversely affecting applications with higher security requirements. Therefore, in terms of security, there have been some researches and explorations on security schemes based on virtual machines.
现有的物联网网络研究对于网关结构的研究不多,对于网关安全结构的研究更少。由于物联网是一种多网融合的网络结构,一些重要的感知信息将在公共的传统网络,如Internet或移动通信网络中传输,因此安全性对于物联网的实现十分重要。网关由于是融合的关键位置,其安全性非常重要。如果不能有效的分离用户的服务使用和网关内的安全信息和安全过程,则很可能使网关遭受到针对于此的恶意攻击。而且由于物联网中不同网络间安全协议的不同,不同安全协议间的融合难度较大。同时如果不能在一个安全的网关结构上完成安全协议的转换过程,很可能会使这些安全协议的安全性都大为降低。Existing Internet of Things network research does not have much research on the gateway structure, and even less research on the gateway security structure. Since the Internet of Things is a multi-network integration network structure, some important perception information will be transmitted in public traditional networks, such as the Internet or mobile communication networks, so security is very important for the realization of the Internet of Things. Because the gateway is a key location for integration, its security is very important. If the user's service usage cannot be effectively separated from the security information and security process in the gateway, the gateway is likely to be subject to malicious attacks aimed at this. Moreover, due to the different security protocols between different networks in the Internet of Things, it is difficult to integrate different security protocols. At the same time, if the conversion process of security protocols cannot be completed on a secure gateway structure, the security of these security protocols may be greatly reduced.
发明内容Contents of the invention
本发明为了解决上述问题,提出了一种基于虚拟机的物联网网关系统及其数据交互方法,以有效的把安全信息和安全过程与用户和对外接口隔离,提高网关的安全性,同时简化了物联网中各不同网络安全融合难度,提高物联网等整体安全性。In order to solve the above problems, the present invention proposes a virtual machine-based Internet of Things gateway system and its data interaction method, which effectively isolates security information and security processes from users and external interfaces, improves the security of the gateway, and simultaneously simplifies It is difficult to integrate different networks in the Internet of Things to improve the overall security of the Internet of Things.
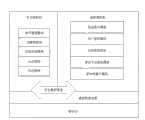
为实现上述目的,本发明的物联网网关系统,包括多网络接口模块、发布模块、用户管理模块、信息管理模块、感知节点管理模块、信息处理模块、密钥管理模块、认证模块和加解密模块,其中:网关的硬件层上搭建有虚拟机监视器,在虚拟机监视器上建立安全虚拟机和服务虚拟机;所述的密钥管理模块、认证模块加解密模块以及信息处理模块设置在安全虚拟机内,所述的多网络接口模块、用户管理模块、信息管理模块、感知节点管理模块和信息发布模块设置在服务虚拟机内,以实现对明文、密钥、加解密过程、认证过程和信息处理过程与用户和外部接口的隔离。To achieve the above object, the Internet of Things gateway system of the present invention includes a multi-network interface module, a publishing module, a user management module, an information management module, a sensing node management module, an information processing module, a key management module, an authentication module and an encryption and decryption module , wherein: a virtual machine monitor is set up on the hardware layer of the gateway, and a security virtual machine and a service virtual machine are established on the virtual machine monitor; In the virtual machine, the multi-network interface module, user management module, information management module, sensing node management module and information release module are set in the service virtual machine, so as to realize the process of plaintext, key, encryption and decryption process, authentication process and Isolation of information processing processes from users and external interfaces.
所述的安全虚拟机和服务虚拟机之间通过虚拟机监视器中的安全数据通道传输受限制的数据,该受限数据仅包括数据密文、用户数据要求、更新要求、用户身份信息、节点身份信息以及用户和节点的认证信息。The restricted data is transmitted between the secure virtual machine and the service virtual machine through the secure data channel in the virtual machine monitor, and the restricted data only includes data ciphertext, user data requirements, update requirements, user identity information, node Identity information and authentication information for users and nodes.
所述的服务虚拟机通过多网络接口模块对外通信,安全虚拟机没有对外通信接口,即用户只能访问服务虚拟机,无法访问安全虚拟机。The service virtual machine communicates externally through the multi-network interface module, and the security virtual machine has no external communication interface, that is, users can only access the service virtual machine, but cannot access the security virtual machine.
所述的安全虚拟机内设有判定模块,用于判定是否有用户的数据要求、感知节点的报警要求或更新要求,当有更新要求时,通知服务虚拟机内的感知节点管理模块向感知节点发送数据更新要求;当有用户数据要求或感知节点报警信息要求时发送用户身份IDU给加解密模块并要求它加密安全虚拟机内暂存的信息。The safety virtual machine is provided with a judging module for judging whether there is a data request from a user, an alarm request or an update request from a sensing node, and when there is an update request, the sensing node management module in the service virtual machine is notified to report to the sensing node Send a data update request; when there is a user data request or a sensor node alarm information request, send the user IDU to the encryption and decryption module and ask it to encrypt the information temporarily stored in the security virtual machine.
为实现上述目的,本发明基于虚拟机的物联网网关数据交互方法,包括如下步骤:In order to achieve the above object, the present invention is based on a virtual machine Internet of Things gateway data interaction method, comprising the following steps:
(1)用户通过多网络接口模块接入网关,用户管理模块通过多网络接口模块获得用户所在网络信息Field,将用户认证信息发送给安全虚拟机的认证模块,安全虚拟机的认证模块验证用户身份认证信息,并将验证结果发送给用户管理模块,如果用户认证信息验证正确,则成功认证用户,用户管理模块将用户指令、身份IDU和用户所在网络信息Field转发给信息管理模块,否则对用户拒绝服务;(1) The user accesses the gateway through the multi-network interface module, the user management module obtains the user's network information Field through the multi-network interface module, and sends the user authentication information to the authentication module of the security virtual machine, and the authentication module of the security virtual machine verifies the identity of the user Authentication information, and the verification result is sent to the user management module, if the user authentication information verification is correct, then successfully authenticate the user, the user management module forwards the user instruction, the identity IDU and the user's network information Field to the information management module, otherwise the user denial of service;
(2)信息管理模块根据用户指令中的控制信息作出配置,将指令中的数据要求和用户身份IDU通过安全数据通道发送给安全虚拟机的判定模块,并根据用户配置的时间向判定模块定时发送数据更新要求;(2) The information management module makes configuration according to the control information in the user instruction, sends the data requirements in the instruction and the user identity IDU to the judgment module of the security virtual machine through the secure data channel, and sends timing to the judgment module according to the time configured by the user Send data update request;
(3)判定模块根据是否有数据要求或警报要求产生要求加解密模块进行数据加密的通知,若没有要求,则不对安全虚拟机内暂存的数据进行加密操作,若有要求,则产生要求加解密模块对暂存在安全虚拟机的数据进行加密的通知,此时根据是否有更新要求进行暂存数据的更新,若没有更新要求,则发送产生的通知和要求所涉及的用户身份IDU到加解密模块,若有更新要求,则通过感知节点管理模块通知感知节点更新数据;(3) The judgment module generates a notification requesting the encryption and decryption module to encrypt data according to whether there is a data request or an alarm request. If there is no request, the data temporarily stored in the security virtual machine will not be encrypted. If there is a request, a request for encryption will be generated. The decryption module encrypts the data temporarily stored in the security virtual machine. At this time, the temporary data is updated according to whether there is an update request. If there is no update request, the generated notification and the user IDU involved in the request are sent to the adder. The decryption module, if there is an update requirement, notifies the sensing node to update data through the sensing node management module;
(4)加解密模块收到判定模块的通知后,根据收到的用户身份IDU在密钥管理模块中查询用户通信密钥KUT并使用KUT对虚拟机中暂存的数据信息加密,之后通过安全数据通道发送数据密文给信息管理模块;(4) After the encryption and decryption module receives the notification from the determination module, it queries the user communication key KUT in the key management module according to the received user identity IDU and uses KUT to encrypt the data information temporarily stored in the virtual machine, Then send the data ciphertext to the information management module through the secure data channel;
(5)信息管理模块将数据密文、用户所在网络信息Field和用户身份IDU发送给发布模块,发布模块根据用户的身份IDU和所在网络信息Field,通过多网络接口模块选择发送网络,将数据密文信息发送到用户;(5) The information management module sends the data ciphertext, the user's network information Field and the user identity IDU to the release module, and the release module selects the sending network through the multi-network interface module according to the user's identity IDU and the network information Field, and sends the The data ciphertext information is sent to the user;
(6)感知节点收到步骤(3)的更新数据要求或者感知到事件时,通过多网络接口模块接入感知节点管理模块,感知节点管理模块将感知节点认证信息发送给安全虚拟机的认证模块,安全虚拟机的认证模块验证节点身份认证信息,并将验证结果发送给感知节点管理模块,如果身份信息验证正确,则认为认证成功,将信息数据密文和感知节点身份IDN发送给安全虚拟机的加解密模块,否则拒绝接受感知节点的数据;(6) When the sensing node receives the update data request of step (3) or perceives an event, it accesses the sensing node management module through the multi-network interface module, and the sensing node management module sends the sensing node authentication information to the authentication module of the security virtual machine , the authentication moduleof the security virtual machine verifies the identity authentication information of the node, and sends the verification result to the perception node management module. The encryption and decryption module of the machine, otherwise it refuses to accept the data of the sensing node;
(7)加解密模块收到数据密文后根据感知节点身份IDN在密钥管理模块中查询感知节点通信密钥KNT,并使用KNT对密文解密,发送数据明文给数据处理模块;(7) After the encryption and decryption module receives the data ciphertext, query the communication key KNT of the sensing node in the key management module according to the identity IDN of the sensing node, and use KNT to decrypt the ciphertext, and send the data plaintext to the data processing module;
(9)数据处理模块对数据明文进行融合,并将融合后的数据处理为易于用户使用的标准化的数据格式后,根据是否是警报信息进行操作,若是警报信息,则暂存处理后的数据,并将警报要求发送给判定模块,返回步骤(3),若不是警报信息,则不发送警报要求,暂存处理后的数据,返回步骤(3)。(9) The data processing module fuses the data plaintext, and processes the fused data into a standardized data format that is easy for users to use, and then operates according to whether it is an alarm message. If it is an alarm message, the processed data is temporarily stored. And send the alarm request to the judgment module, return to step (3), if not alarm information, then do not send the alarm request, temporarily store the processed data, return to step (3).
本发明具有如下优点:The present invention has the following advantages:
1)本发明由于提出了一种基于虚拟机的物联网网关系统结构,通过在虚拟机监视器上建立服务虚拟机和安全虚拟机的方式,将明文、密钥、数据处理过程、加解密过程和认证过程与用户和对外接口隔离,保证用户和外部程序无法对安全虚拟机部分直接访问,提高了安全性;1) Since the present invention proposes a virtual machine-based Internet of Things gateway system structure, by establishing a service virtual machine and a safe virtual machine on a virtual machine monitor, the plaintext, key, data processing process, encryption and decryption process The authentication process is isolated from the user and the external interface, ensuring that users and external programs cannot directly access the part of the secure virtual machine, improving security;
2)本发明由于使用了隔离的结构,不要求用户设备网络和感知节点网络使用相同的密码算法协议,使具体的安全协议的转化过程在本发明的网关中安全实现,简化了不同网络间安全协议间的融合,在多网融合为主的物联网内有较好的适用性;2) The present invention does not require the user equipment network and the sensing node network to use the same cryptographic algorithm protocol due to the use of an isolated structure, so that the conversion process of the specific security protocol can be safely implemented in the gateway of the present invention, which simplifies the security between different networks. The integration between protocols has better applicability in the Internet of Things, which is dominated by multi-network integration;
附图说明Description of drawings
图1是本发明的应用场景示意图;Fig. 1 is a schematic diagram of an application scenario of the present invention;
图2是本发明基于虚拟机的物联网网关系统结构示意图;Fig. 2 is a schematic structural diagram of the Internet of Things gateway system based on a virtual machine in the present invention;
图3是本发明中基于虚拟机的物联网网关数据交互方法流程图。Fig. 3 is a flow chart of the virtual machine-based IoT gateway data interaction method in the present invention.
具体实施方式Detailed ways
本发明所应用的场景如图1所示,基于虚拟机的物联网网关系统位于物联网中服务提供网络和Internet或移动通信网络等通信网络之间,服务提供网络,如无线传感器网络、RFID网络,包含大量的感知节点,而用户主要通过Internet或移动通信网络进行通信。物联网网关通过多网络接口模块和服务提供网络中的感知节点通信,并通过多网络接口模块接入Internet或移动通信网络,用户通过各自不同的网络接入方式接入Internet或移动通信网络,与物联网网关通信。The scenario where the present invention is applied is shown in Figure 1. The virtual machine-based Internet of Things gateway system is located between the service provision network in the Internet of Things and communication networks such as the Internet or mobile communication networks. The service provision network, such as wireless sensor networks, RFID networks , including a large number of sensing nodes, and users mainly communicate through the Internet or mobile communication network. The Internet of Things gateway provides communication between sensing nodes in the network through multiple network interface modules and services, and accesses the Internet or mobile communication network through multiple network interface modules. Users access the Internet or mobile communication network through different network access methods. IoT gateway communication.
服务提供网络中的大量感应节点分别对各自地理范围内的事件进行感知,并把感知数据发送给物联网网关,网关完成不同网络间数据帧格式的转换和安全协议的转换,以及对数据进行数据融合和标准化格式的处理。之后网关根据用户所在的网络,选择合适的网络接口,将加密后的数据发送给通过网关认证的用户。A large number of sensing nodes in the service provider network perceive events within their respective geographical ranges and send the sensing data to the IoT gateway. The gateway completes the conversion of data frame formats and security protocols between different networks, and performs data processing on the data. Processing of fusion and normalization formats. Then the gateway selects an appropriate network interface according to the network where the user is located, and sends the encrypted data to the user who has passed the gateway authentication.
本发明提出了基于虚拟机的物联网网关系统,以及基于虚拟机的物联网网关数据交互方法,The present invention proposes a virtual machine-based Internet of Things gateway system and a virtual machine-based Internet of Things gateway data interaction method,
参照图2,本发明基于虚拟机的物联网网关系统,是在物联网网关的硬件层上搭建有虚拟机监视器,在虚拟机监视器上搭建有两个虚拟机,包括安全虚拟机和服务虚拟机。两个虚拟机内部包括各自的功能模块。两个虚拟机的内部模块相互隔离,仅能通过虚拟机监视器内的安全数据通道交互受限的数据,这些数据仅包括数据密文、用户数据要求、更新要求、用户身份信息、节点身份信息以及用户和节点的认证信息。With reference to Fig. 2, the Internet of Things gateway system based on the virtual machine of the present invention is to set up a virtual machine monitor on the hardware layer of the Internet of Things gateway, and set up two virtual machines on the virtual machine monitor, including a safe virtual machine and a service virtual machine. The two virtual machines include their own functional modules. The internal modules of the two virtual machines are isolated from each other, and only restricted data can be exchanged through the secure data channel in the virtual machine monitor. These data only include data ciphertext, user data requirements, update requirements, user identity information, and node identity information And user and node authentication information.
所述的服务虚拟机,主要负责多网络的管理、用户和感知节点的管理以及信息的发布,它是用户直接访问的虚拟机,拥有对外的接口。该服务虚拟机中包括的模块有:多网络接口模块、用户管理模块、感知节点管理模块、信息管理模块和发布模块。该多网络接口模块,负责多网络的的协议实现和连通;该用户管理模块,负责网关对用户的管理,在安全虚拟机认证模块的帮助下对用户进行认证和对接收到的用户指令的转发;该感知节点管理模块负责感知节点的管理,在安全虚拟机认证模块的帮助下对感知节点认证并将节点发送来的数据密文发送给安全虚拟机;该信息管理模块,负责信息的管理,根据用户的指令向安全虚拟机内的判定模块发送用户数据要求和更新要求,并且接受安全虚拟机发送来的密文;该发布模块负责将数据密文根据用户网络信息选择合适的网络发布给用户。The service virtual machine is mainly responsible for the management of multiple networks, the management of users and sensing nodes, and the release of information. It is a virtual machine directly accessed by users and has an external interface. The modules included in the service virtual machine are: a multi-network interface module, a user management module, a perception node management module, an information management module and a release module. The multi-network interface module is responsible for the implementation and connection of multi-network protocols; the user management module is responsible for the management of users by the gateway, and authenticates users and forwards received user instructions with the help of the security virtual machine authentication module ; The perception node management module is responsible for the management of the perception nodes, authenticates the perception nodes with the help of the security virtual machine authentication module and sends the data ciphertext sent by the nodes to the security virtual machine; the information management module is responsible for information management, Send user data requirements and update requirements to the judgment module in the security virtual machine according to the user's instructions, and accept the ciphertext sent by the security virtual machine; the publishing module is responsible for publishing the data ciphertext to the user by selecting an appropriate network based on the user's network information .
所述的安全虚拟机,主要负责密钥和数据明文的管理和储存,它是禁止用户访问的虚拟机,没有对外的接口。该安全虚拟机中包括的模块有:密钥管理模块、加解密模块、认证模块、信息处理模块和判定模块。该密钥管理模块,负责密钥的管理,用于存储和查询用户和感知节点的通信密钥和认证密钥;该加解密模块,负责依据用户通信密钥或感知节点通信密钥完成加解密过程;该认证模块,负责依据用户和感知节点的认证密钥,对接入的感知节点和用户的身份认证信息进行验证;该信息处理模块,负责对信息的融合、标准化处理和产生警报要求;该判定模块,负责根据用户数据要求和警报要求通知加解密模块进行加密工作,根据更新要求通知感知节点管理模块要求感知节点更新数据。The security virtual machine is mainly responsible for the management and storage of keys and plaintext data. It is a virtual machine that is prohibited from being accessed by users and has no external interface. The modules included in the safe virtual machine are: a key management module, an encryption and decryption module, an authentication module, an information processing module and a judgment module. The key management module is responsible for key management, and is used to store and query the communication key and authentication key of the user and the sensing node; the encryption and decryption module is responsible for completing encryption and decryption based on the user communication key or the sensing node communication key process; the authentication module is responsible for verifying the identity authentication information of the connected sensing node and user according to the authentication key of the user and the sensing node; the information processing module is responsible for information fusion, standardized processing and generating alarm requirements; The determination module is responsible for notifying the encryption and decryption module to perform encryption work according to user data requirements and alarm requirements, and notifying the sensing node management module to request the sensing node to update data according to the update requirement.
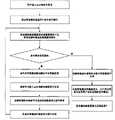
参照图3,本发明基于虚拟机技术的物联网网关系统的数据交互方法包括以下步骤:Referring to Fig. 3, the data interaction method of the Internet of Things gateway system based on virtual machine technology of the present invention comprises the following steps:
步骤1,用户接入认证和指令发送。Step 1, user access authentication and command sending.
(1a)用户通过多网络接口模块接入,发送用户指令和身份认证信息给用户管理模块;(1a) The user accesses through the multi-network interface module, and sends user instructions and identity authentication information to the user management module;
(1b)用户管理模块将用户认证信息通过安全数据通道发送给认证模块;(1b) The user management module sends the user authentication information to the authentication module through a secure data channel;
(1c)认证模块通过认证信息声称的身份IDU在密钥管理模块中查找对应的KUI,验证身份认证信息,并将验证结果发送给用户管理模块;(1c) The authentication module searches the corresponding KUI in the key management module through the identity IDU claimed by the authentication information, verifies the identity authentication information, and sends the verification result to the user management module;
(1d)用户管理模块根据认证信息验证结果进行操作,如果认证信息验证正确,则认为用户认证成功,将用户身份IDU、用户所在网络信息Field和用户的指令发送给信息管理模块,如果身份信息验证错误,则认为用户认证失败,用户管理模块拒绝对用户服务。(1d) The user management module operates according to the authentication information verification result. If the authentication information verification is correct, the user authentication is considered successful, and the user identity IDU , the user's network information Field and the user's instruction are sent to the information management module. If the identity information If the authentication is wrong, it is considered that the user authentication has failed, and the user management module refuses to serve the user.
步骤2,信息管理模块根据用户指令进行操作。In step 2, the information management module operates according to user instructions.
(2a)信息管理模块根据用户指令中的控制信息配置用户数据要求的更新时间,并根据配置的更新时间向判断模块发送更新要求;(2a) The information management module configures the update time required by the user data according to the control information in the user instruction, and sends an update request to the judgment module according to the configured update time;
(2b)信息管理模块存储用户身份IDU和用户所在网络信息Field;(2b) The information management module stores the user identity IDU and the network information Field where the user is located;
(2c)信息管理模块将指令中的数据要求和用户身份IDU通过安全数据通道发送给安全虚拟机的判定模块。(2c) The information management module sends the data requirements in the instruction and the user IDU to the judgment module of the security virtual machine through the security data channel.
步骤3,判定模块根据数据要求或警报要求产生要求加解密模块加密数据的通知。Step 3, the judging module generates a notification requesting the encryption and decryption module to encrypt data according to the data requirement or the alarm requirement.
判定模块跟据当前时刻是否有来自信息管理模块的用户数据要求或者来自数据处理模块的警报要求产生要求加解密模块进行数据加密的通知,如果用户数据要求和警报要求两者都不存在,则不对暂存在虚拟机内的数据进行处理,继续进行步骤4;如果用户数据要求或报警要求两者任一存在,则获得相应的用户数据要求或报警要求中涉及的用户身份IDU并产生要求加解密模块进行加密的通知,继续进行步骤4。The judgment module generates a notification requiring the encryption and decryption module to perform data encryption according to whether there is a user data request from the information management module or an alarm request from the data processing module at the current moment. If both the user data request and the alarm request do not exist, then no Process the data temporarily stored in the virtual machine, and proceed to step 4; if either the user data request or the alarm request exists, obtain the user IDU involved in the corresponding user data request or alarm request and generate a request for encryption and decryption If the module is notified of encryption, proceed to step 4.
步骤4,判定模块根据更新要求更新数据。Step 4, the judging module updates the data according to the update requirement.
安全虚拟机内的判定模块根据当前时刻是否有来自信息管理模块的更新要求更新安全虚拟机内暂存的数据,如果有更新要求,则向感知节点管理模块发送更新要求,进入步骤8;如果没有更新要求,则将步骤3中的要求加解密模块工作的通知和涉及的用户身份IDU发送给加解密模块,进入步骤5,如果此时没有暂存的要求加解密模块工作的通知,则返回步骤3。The judging module in the security virtual machine updates the temporarily stored data in the security virtual machine according to whether there is an update request from the information management module at the current moment, and if there is an update request, then sends an update request to the perception node management module and enters step 8; if not Update the request, then send the notice requiring the encryption and decryption module to work and the user IDU involved in step 3 to the encryption and decryption module, and enter step 5, if there is no temporarily stored notice requiring the encryption and decryption module to work, then return Step 3.
步骤5,加解密模块对虚拟机内暂存的数据进行加密。Step 5, the encryption and decryption module encrypts the data temporarily stored in the virtual machine.
安全虚拟机内的加解密模块收到来自判定模块的通知后,根据涉及的用户身份IDU在密钥管理模块中查找到相应的用户通信密钥KUT,并对用户要求的安全虚拟机内暂存的数据进行加密,将加密后的数据和用户身份IDU通过安全数据通道发送给信息管理模块。After the encryption and decryption module in the security virtual machine receives the notification from the decision module, it finds the corresponding user communication key KUT in the key management module according to the user identity IDU involved, and sends the required key to the security virtual machine. The temporarily stored data is encrypted, and the encrypted data and user IDU are sent to the information management module through a secure data channel.
步骤6,信息管理模块转发数据密文和用户信息给发布模块。Step 6, the information management module forwards the data ciphertext and user information to the issuing module.
(6a)信息管理模块在收到来自安全虚拟机的数据密文和对应的用户身份IDU后,根据IDU查询用户所在网络信息Field;(6a) After receiving the data ciphertext from the security virtual machine and the corresponding user identity IDU , the information management module queries the user's network information Field according to the IDU ;
(6b)信息管理模块将用户身份IDU、用户所在网络信息Field和数据密文发送给发布模块。(6b) The information management module sends the user identity IDU , the user's network information Field and data ciphertext to the publishing module.
步骤7,发布模块根据用户身份IDU和用户所在网络信息Field在多网络接口模块中选择合适的网络接口,将数据密文发送给用户。Step 7: The publishing module selects an appropriate network interface in the multi-network interface module according to the user IDU and the network information Field where the user is located, and sends the data ciphertext to the user.
步骤8,感知节点管理模块收到步骤4中判定模块发送的更新要求后,向感知节点发送指令,要求感知节点更新数据。Step 8: After receiving the update request sent by the judgment module in step 4, the sensing node management module sends an instruction to the sensing node to request the sensing node to update data.
步骤9,感知节点接入认证和感知数据密文发送。Step 9, the sensing node access authentication and sensing data cipher text transmission.
(9a)感知节点在收到步骤8的数据更新要求或者感知到事件发生时,将感知数据的密文和感知节点身份认证信息发送给节点管理模块;(9a) The sensing node sends the ciphertext of the sensing data and the identity authentication information of the sensing node to the node management module when receiving the data update request in step 8 or sensing the occurrence of the event;
(9b)节点管理模块通将感知节点的身份认证信息通过安全数据通道发送给安全虚拟机内的认证模块;(9b) The node management module sends the identity authentication information of the sensing node to the authentication module in the security virtual machine through the security data channel;
(9c)认证模块通过感知节点认证信息声称的IDN在密钥管理模块中查找认证密钥KNI,验证身份认证信息并将结果发送给感知节点管理模块;(9c) The authentication module looks up the authentication key KNI in the key management module through the IDN claimed by the sensing node authentication information, verifies the identity authentication information and sends the result to the sensing node management module;
(9d)感知节点管理模块根据认证信息验证结果进行操作,如果身份认证信息验证错误,则认为感知节点认证失败,用户管理模块拒绝接受感知节点的数据;如果身份认证证信息验证正确,则认为节点认证成功,将感知节点身份IDN和数据密文通过安全数据通道发送给安全虚拟机。(9d) The perception node management module operates according to the authentication information verification result. If the identity authentication information verification is wrong, the perception node authentication fails, and the user management module refuses to accept the data of the perception node; if the identity authentication certificate information verification is correct, then the node is considered If the authentication is successful, the sensing node identity IDN and data ciphertext are sent to the secure virtual machine through the secure data channel.
步骤10,加解密模块对感知节点发送的的数据密文进行解密。Step 10, the encryption and decryption module decrypts the data ciphertext sent by the sensing node.
安全虚拟机内的加解密模块在收到来自感知节点管理模块的数据密文后,根据感知节点身份IDN在密钥管理模块中查找到相应的感知节点通信密钥KNT,使用KNT对数据密文进行解密,并将解密后得到的数据明文发送给信息处理模块。After receiving the data ciphertext from the sensory node management module, the encryption and decryption module in the security virtual machine finds the corresponding sensory node communication key KNT in the key management module according to the sensory node identity IDN , and uses KNT to The data ciphertext is decrypted, and the data plaintext obtained after decryption is sent to the information processing module.
步骤11,信息处理模块对数据明文进行处理。Step 11, the information processing module processes the data plaintext.
(11a)信息处理模块将步骤10产生的数据明文进行融合,并将融合后的数据处理为便于用户使用的标准化的数据格式;(11a) The information processing module fuses the data plaintext generated in step 10, and processes the fused data into a standardized data format that is convenient for users to use;
(11b)信息处理模块根据处理后的数据中是否有警报信息发送警报要求给判定模块。如果有警报信息,则发送警报要求给判定模块,将处理后的数据暂存在安全虚拟机中,进入步骤3判断后进行发布;如果没有警报信息,则不发送警报要求给判定模块,将处理后的数据暂存在安全虚拟机中,进入步骤3。(11b) The information processing module sends an alarm request to the judging module according to whether there is alarm information in the processed data. If there is an alarm message, send an alarm request to the judgment module, temporarily store the processed data in the security virtual machine, and publish it after entering step 3 for judgment; if there is no alarm message, then do not send an alarm request to the judgment module, and will process The data is temporarily stored in the security virtual machine, go to step 3.
符号说明Symbol Description
IDU:用户身份信息IDU : user identity information
IDN:感知节点身份信息IDN : perception node identity information
Field:用户所在网络信息Field: User's network information
KUI:用户认证密钥KUI : User Authentication Key
KNI:感知节点认证密钥KNI : Sensing node authentication key
KUT:用户通信密钥KUT : user communication key
KNT:感知节点通信密钥。KNT : Perceptual node communication key.
Claims (5)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201010188081ACN101867530B (en) | 2010-05-31 | 2010-05-31 | Things-internet gateway system based on virtual machine and data interactive method |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201010188081ACN101867530B (en) | 2010-05-31 | 2010-05-31 | Things-internet gateway system based on virtual machine and data interactive method |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN101867530Atrue CN101867530A (en) | 2010-10-20 |
| CN101867530B CN101867530B (en) | 2012-10-24 |
Family
ID=42959099
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN201010188081AExpired - Fee RelatedCN101867530B (en) | 2010-05-31 | 2010-05-31 | Things-internet gateway system based on virtual machine and data interactive method |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN101867530B (en) |
Cited By (29)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN101984706A (en)* | 2010-11-04 | 2011-03-09 | 中国电信股份有限公司 | Gateway of Internet of things and automatic adaptation method of communication protocol |
| CN102025577A (en)* | 2011-01-06 | 2011-04-20 | 西安电子科技大学 | Network system of Internet of things and data processing method thereof |
| CN102045896A (en)* | 2010-11-22 | 2011-05-04 | 中山爱科数字科技有限公司 | Virtual Internet-of-things gateway system capable of realizing multiprotocol and network self-adapting |
| CN102215180A (en)* | 2011-05-26 | 2011-10-12 | 苏州震旦科技有限公司 | Access gateway of internet of things |
| CN102571338A (en)* | 2010-12-23 | 2012-07-11 | 北京时代凌宇科技有限公司 | PKI (Public Key Infrastructure)-based method and system for certifying internet of things |
| CN102663278A (en)* | 2012-03-09 | 2012-09-12 | 浪潮通信信息系统有限公司 | Cloud computing mode Internet of Things platform data processing safety protection method |
| CN102801658A (en)* | 2011-05-23 | 2012-11-28 | 镇江金钛软件有限公司 | Configurable access gateway for Internet of things |
| CN102882676A (en)* | 2011-07-15 | 2013-01-16 | 深圳市汇川控制技术有限公司 | Method and system for equipment to safely access Internet of things |
| CN102932459A (en)* | 2012-11-05 | 2013-02-13 | 广州杰赛科技股份有限公司 | Security control method of virtual machine |
| CN102984258A (en)* | 2012-11-30 | 2013-03-20 | 易程科技股份有限公司 | Internet of things data transmission method and adapter |
| CN103107994A (en)* | 2013-02-06 | 2013-05-15 | 中电长城网际系统应用有限公司 | Vitualization environment data security partition method and system |
| CN103312682A (en)* | 2012-03-16 | 2013-09-18 | 中兴通讯股份有限公司 | Method and system for accessing gateway safely |
| CN103428627A (en)* | 2012-05-22 | 2013-12-04 | 中国移动通信集团江苏有限公司 | Method for transferring data in internet of things, internet of things system and corresponding device |
| CN103544089A (en)* | 2013-10-13 | 2014-01-29 | 西安电子科技大学 | Xen-based operating system identification method |
| CN103917982A (en)* | 2011-03-16 | 2014-07-09 | 赛门铁克公司 | Techniques for securing checked-out virtual machine in virtual desktop infrastructure |
| CN103957242A (en)* | 2014-04-16 | 2014-07-30 | 北京大学工学院南京研究院 | Internet-of-things gateway achieving IP virtualization conversion |
| CN106487578A (en)* | 2015-08-26 | 2017-03-08 | 大同股份有限公司 | Error recovery method, and Internet of things system and charging system applying same |
| CN107026870A (en)* | 2017-05-03 | 2017-08-08 | 桂斌 | It is a kind of to encrypt the outdoor public Internet of Things access stack of dynamic group net safely |
| CN107908940A (en)* | 2017-11-06 | 2018-04-13 | 深圳市文鼎创数据科技有限公司 | The method and terminal device of a kind of fingerprint recognition |
| CN108123917A (en)* | 2016-11-29 | 2018-06-05 | 中国移动通信有限公司研究院 | A kind of newer method and apparatus of the Service Ticket of internet-of-things terminal |
| CN108696388A (en)* | 2018-04-19 | 2018-10-23 | 郑州科技学院 | A kind of hardware debugging management method based on Intelligent internet of things gateway |
| US10140147B2 (en) | 2017-02-16 | 2018-11-27 | Sanctum Solutions Inc. | Intelligently assisted IoT endpoint device |
| CN109845226A (en)* | 2016-08-22 | 2019-06-04 | Fybr有限责任公司 | System for distributed intelligent remote sensing system |
| US10382450B2 (en) | 2017-02-21 | 2019-08-13 | Sanctum Solutions Inc. | Network data obfuscation |
| CN110766886A (en)* | 2018-07-25 | 2020-02-07 | 新智数字科技有限公司 | Driving device, method for driving card reader to realize card service and self-service payment system |
| CN113709139A (en)* | 2021-08-26 | 2021-11-26 | 江苏省未来网络创新研究院 | Openstack east-west forwarding performance optimization method and system based on NUMA architecture |
| CN114244515A (en)* | 2022-02-25 | 2022-03-25 | 中瓴智行(成都)科技有限公司 | Hypervisor-based virtual machine communication method and device, readable storage medium and electronic equipment |
| CN116488924A (en)* | 2023-05-12 | 2023-07-25 | 山东中创软件商用中间件股份有限公司 | Data transmission method, device, electronic equipment and medium based on Internet of Things gateway |
| CN116545641A (en)* | 2022-12-22 | 2023-08-04 | 中国电建集团华东勘测设计研究院有限公司 | Virtual gateway data transmission system and data transmission method |
Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN1805441A (en)* | 2005-11-23 | 2006-07-19 | 西安电子科技大学 | Integrated WLAN authentication architecture and method of implementing structural layers |
| WO2008012567A1 (en)* | 2006-07-28 | 2008-01-31 | Hewlett-Packard Development Company, L.P. | Secure use of user secrets on a computing platform |
| CN101600198A (en)* | 2009-07-08 | 2009-12-09 | 西安电子科技大学 | Identity-based wireless sensor network security trust method |
| EP2172862A1 (en)* | 2008-10-02 | 2010-04-07 | Broadcom Corporation | Secure virtual machine manager |
- 2010
- 2010-05-31CNCN201010188081Apatent/CN101867530B/ennot_activeExpired - Fee Related
Patent Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN1805441A (en)* | 2005-11-23 | 2006-07-19 | 西安电子科技大学 | Integrated WLAN authentication architecture and method of implementing structural layers |
| WO2008012567A1 (en)* | 2006-07-28 | 2008-01-31 | Hewlett-Packard Development Company, L.P. | Secure use of user secrets on a computing platform |
| EP2172862A1 (en)* | 2008-10-02 | 2010-04-07 | Broadcom Corporation | Secure virtual machine manager |
| CN101600198A (en)* | 2009-07-08 | 2009-12-09 | 西安电子科技大学 | Identity-based wireless sensor network security trust method |
Non-Patent Citations (4)
| Title |
|---|
| 《西安电子科技大学学报(自然科学版)》 20090228 张志勇等 支持验证代理方的远程证明模型及其安全协议 第58-63页 1-5 第36卷, 第1期* |
| 《西安电子科技大学学报(自然科学版)》 20090228 张志勇等 支持验证代理方的远程证明模型及其安全协议 第58-63页 1-5 第36卷, 第1期 2* |
| 《计算机工程》 20080229 王结太等 无线传感器网络移动Agent的应用 第133-135页 1-5 第34卷, 第3期* |
| 《计算机工程》 20080229 王结太等 无线传感器网络移动Agent的应用 第133-135页 1-5 第34卷, 第3期 2* |
Cited By (43)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN101984706A (en)* | 2010-11-04 | 2011-03-09 | 中国电信股份有限公司 | Gateway of Internet of things and automatic adaptation method of communication protocol |
| CN102045896A (en)* | 2010-11-22 | 2011-05-04 | 中山爱科数字科技有限公司 | Virtual Internet-of-things gateway system capable of realizing multiprotocol and network self-adapting |
| CN102571338A (en)* | 2010-12-23 | 2012-07-11 | 北京时代凌宇科技有限公司 | PKI (Public Key Infrastructure)-based method and system for certifying internet of things |
| CN102571338B (en)* | 2010-12-23 | 2015-09-23 | 北京时代凌宇科技有限公司 | A kind of Internet of Things authentication method based on PKI technology and system |
| CN102025577A (en)* | 2011-01-06 | 2011-04-20 | 西安电子科技大学 | Network system of Internet of things and data processing method thereof |
| CN102025577B (en)* | 2011-01-06 | 2012-07-04 | 西安电子科技大学 | Network system of Internet of things and data processing method thereof |
| CN103917982B (en)* | 2011-03-16 | 2016-09-28 | 赛门铁克公司 | The technology publishing virtual machine in protection virtual desktop infrastructure |
| CN103917982A (en)* | 2011-03-16 | 2014-07-09 | 赛门铁克公司 | Techniques for securing checked-out virtual machine in virtual desktop infrastructure |
| CN102801658A (en)* | 2011-05-23 | 2012-11-28 | 镇江金钛软件有限公司 | Configurable access gateway for Internet of things |
| CN102215180A (en)* | 2011-05-26 | 2011-10-12 | 苏州震旦科技有限公司 | Access gateway of internet of things |
| CN102882676A (en)* | 2011-07-15 | 2013-01-16 | 深圳市汇川控制技术有限公司 | Method and system for equipment to safely access Internet of things |
| CN102663278B (en)* | 2012-03-09 | 2016-09-28 | 浪潮通信信息系统有限公司 | Cloud computing mode platform of internet of things data process method for security protection |
| CN102663278A (en)* | 2012-03-09 | 2012-09-12 | 浪潮通信信息系统有限公司 | Cloud computing mode Internet of Things platform data processing safety protection method |
| CN103312682A (en)* | 2012-03-16 | 2013-09-18 | 中兴通讯股份有限公司 | Method and system for accessing gateway safely |
| CN103312682B (en)* | 2012-03-16 | 2016-12-14 | 中兴通讯股份有限公司 | The method and system that gateway security accesses |
| CN103428627B (en)* | 2012-05-22 | 2016-12-14 | 中国移动通信集团江苏有限公司 | The transfer approach of data, Internet of things system and related device in Internet of things system |
| CN103428627A (en)* | 2012-05-22 | 2013-12-04 | 中国移动通信集团江苏有限公司 | Method for transferring data in internet of things, internet of things system and corresponding device |
| CN102932459A (en)* | 2012-11-05 | 2013-02-13 | 广州杰赛科技股份有限公司 | Security control method of virtual machine |
| CN102932459B (en)* | 2012-11-05 | 2016-02-10 | 广州杰赛科技股份有限公司 | A kind of method of controlling security of virtual machine |
| CN102984258A (en)* | 2012-11-30 | 2013-03-20 | 易程科技股份有限公司 | Internet of things data transmission method and adapter |
| CN103107994A (en)* | 2013-02-06 | 2013-05-15 | 中电长城网际系统应用有限公司 | Vitualization environment data security partition method and system |
| CN103107994B (en)* | 2013-02-06 | 2017-02-08 | 中电长城网际系统应用有限公司 | Vitualization environment data security partition method and system |
| CN103544089A (en)* | 2013-10-13 | 2014-01-29 | 西安电子科技大学 | Xen-based operating system identification method |
| CN103544089B (en)* | 2013-10-13 | 2016-05-25 | 西安电子科技大学 | Operating system recognition methods based on Xen |
| CN103957242B (en)* | 2014-04-16 | 2017-06-20 | 北京大学工学院南京研究院 | A kind of things-internet gateway of IP virtualizations conversion |
| CN103957242A (en)* | 2014-04-16 | 2014-07-30 | 北京大学工学院南京研究院 | Internet-of-things gateway achieving IP virtualization conversion |
| US10805147B2 (en) | 2015-08-26 | 2020-10-13 | Tatung Company | Fail recovery method and internet of things system and charging system using the same |
| CN106487578A (en)* | 2015-08-26 | 2017-03-08 | 大同股份有限公司 | Error recovery method, and Internet of things system and charging system applying same |
| CN109845226A (en)* | 2016-08-22 | 2019-06-04 | Fybr有限责任公司 | System for distributed intelligent remote sensing system |
| CN108123917B (en)* | 2016-11-29 | 2021-07-23 | 中国移动通信有限公司研究院 | Method and device for updating authentication credential of IoT terminal |
| CN108123917A (en)* | 2016-11-29 | 2018-06-05 | 中国移动通信有限公司研究院 | A kind of newer method and apparatus of the Service Ticket of internet-of-things terminal |
| US10140147B2 (en) | 2017-02-16 | 2018-11-27 | Sanctum Solutions Inc. | Intelligently assisted IoT endpoint device |
| US10382450B2 (en) | 2017-02-21 | 2019-08-13 | Sanctum Solutions Inc. | Network data obfuscation |
| CN107026870A (en)* | 2017-05-03 | 2017-08-08 | 桂斌 | It is a kind of to encrypt the outdoor public Internet of Things access stack of dynamic group net safely |
| CN107908940A (en)* | 2017-11-06 | 2018-04-13 | 深圳市文鼎创数据科技有限公司 | The method and terminal device of a kind of fingerprint recognition |
| CN108696388A (en)* | 2018-04-19 | 2018-10-23 | 郑州科技学院 | A kind of hardware debugging management method based on Intelligent internet of things gateway |
| CN110766886A (en)* | 2018-07-25 | 2020-02-07 | 新智数字科技有限公司 | Driving device, method for driving card reader to realize card service and self-service payment system |
| CN110766886B (en)* | 2018-07-25 | 2023-01-10 | 新智数字科技有限公司 | Driving device, method for driving card reader to realize card service and self-service payment system |
| CN113709139A (en)* | 2021-08-26 | 2021-11-26 | 江苏省未来网络创新研究院 | Openstack east-west forwarding performance optimization method and system based on NUMA architecture |
| CN113709139B (en)* | 2021-08-26 | 2023-03-24 | 江苏省未来网络创新研究院 | Openstack east-west forwarding performance optimization method and system based on NUMA architecture |
| CN114244515A (en)* | 2022-02-25 | 2022-03-25 | 中瓴智行(成都)科技有限公司 | Hypervisor-based virtual machine communication method and device, readable storage medium and electronic equipment |
| CN116545641A (en)* | 2022-12-22 | 2023-08-04 | 中国电建集团华东勘测设计研究院有限公司 | Virtual gateway data transmission system and data transmission method |
| CN116488924A (en)* | 2023-05-12 | 2023-07-25 | 山东中创软件商用中间件股份有限公司 | Data transmission method, device, electronic equipment and medium based on Internet of Things gateway |
Also Published As
| Publication number | Publication date |
|---|---|
| CN101867530B (en) | 2012-10-24 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN101867530A (en) | Internet of things gateway system and data interaction method based on virtual machine | |
| CN111314056B (en) | Heaven and earth integrated network anonymous access authentication method based on identity encryption system | |
| Xi et al. | ZAMA: A ZKP-based anonymous mutual authentication scheme for the IoV | |
| CN102142961B (en) | Method, device and system for authenticating gateway, node and server | |
| CN104145465B (en) | The method and apparatus of bootstrapping based on group in machine type communication | |
| CN102685749B (en) | Wireless safety authentication method orienting to mobile terminal | |
| CN105530253B (en) | Wireless sensor network access authentication method under Restful framework based on CA certificate | |
| EP2767029B1 (en) | Secure communication | |
| KR20080089500A (en) | Methods, systems, and authentication centers for authentication in end-to-end communications based on mobile networks | |
| CN108667601A (en) | A method, device and equipment for transmitting data | |
| CN104468618B (en) | XMPP safety access method based on sensor network | |
| CN109347626B (en) | A secure identity authentication method with anti-tracking feature | |
| CN103118363A (en) | Method, system, terminal device and platform device of secret information transmission | |
| CN112804356B (en) | Block chain-based networking equipment supervision authentication method and system | |
| CN109639731A (en) | The certification of multiple-factor Universal-Composability and service authorizing method, communications service system | |
| WO2023236925A1 (en) | Authentication method and communication device | |
| CN111698263A (en) | Beidou satellite navigation data transmission method and system | |
| Zhang et al. | Is today's end-to-end communication security enough for 5g and its beyond? | |
| CN117715026A (en) | UAV safety authentication method and system based on embedded message authentication code | |
| CN107135228B (en) | Authentication system and authentication method based on central node | |
| CN103781026B (en) | The authentication method of common authentication mechanism | |
| CN103490887B (en) | A kind of network equipment and its certification and key management method | |
| CN107104888B (en) | A Secure Instant Messaging Method | |
| CN106209384B (en) | Use the client terminal of security mechanism and the communication authentication method of charging unit | |
| CN102694779B (en) | Combination attestation system and authentication method |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| C06 | Publication | ||
| PB01 | Publication | ||
| C10 | Entry into substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| C14 | Grant of patent or utility model | ||
| GR01 | Patent grant | ||
| CF01 | Termination of patent right due to non-payment of annual fee | Granted publication date:20121024 Termination date:20160531 |