CN101742508A - System and method for transferring files between WAPI terminal and application server - Google Patents
System and method for transferring files between WAPI terminal and application serverDownload PDFInfo
- Publication number
- CN101742508A CN101742508ACN200910247064ACN200910247064ACN101742508ACN 101742508 ACN101742508 ACN 101742508ACN 200910247064 ACN200910247064 ACN 200910247064ACN 200910247064 ACN200910247064 ACN 200910247064ACN 101742508 ACN101742508 ACN 101742508A
- Authority
- CN
- China
- Prior art keywords
- terminal
- application server
- wapi
- content
- digital signature
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
- 238000000034methodMethods0.000titleclaimsabstractdescription43
- 230000005540biological transmissionEffects0.000claimsabstractdescription10
- 238000004364calculation methodMethods0.000claimsdescription48
- 238000012546transferMethods0.000claimsdescription5
- 238000005538encapsulationMethods0.000claims2
- 230000015572biosynthetic processEffects0.000claims1
- 238000012795verificationMethods0.000abstractdescription14
- 238000009434installationMethods0.000abstract1
- 230000006870functionEffects0.000description19
- 230000008569processEffects0.000description17
- 238000010586diagramMethods0.000description5
- 230000007246mechanismEffects0.000description2
- 238000012545processingMethods0.000description2
- 230000004044responseEffects0.000description2
- 230000008859changeEffects0.000description1
- 238000004891communicationMethods0.000description1
- 238000010276constructionMethods0.000description1
- 238000005516engineering processMethods0.000description1
- 230000003993interactionEffects0.000description1
- 230000005055memory storageEffects0.000description1
- 238000010561standard procedureMethods0.000description1
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/10—Integrity
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/12—Applying verification of the received information
- H04L63/123—Applying verification of the received information received data contents, e.g. message integrity
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/03—Protecting confidentiality, e.g. by encryption
- H04W12/033—Protecting confidentiality, e.g. by encryption of the user plane, e.g. user's traffic
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Storage Device Security (AREA)
- Computer And Data Communications (AREA)
- Information Transfer Between Computers (AREA)
- Mobile Radio Communication Systems (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本发明涉及WAPI技术领域,具体涉及一种WAPI终端与应用服务器传输文件的系统及方法。The invention relates to the technical field of WAPI, in particular to a system and method for transferring files between a WAPI terminal and an application server.
背景技术Background technique
为了解决无线局域网国际标准ISO/IEC 8802-11中定义的WEP(WiredEquivalent Privacy)安全机制存在的安全漏洞,我国颁布了无线局域网国家标准及其第一号修改单,采用无线局域网认证与保密基础结构WAPI(WLANAuthentication and Privacy Infrastructure)替代WEP,解决无线局域网的安全问题。WAPI由无线局域网鉴别基础结构(WAI WLAN AuthenticationInfrastructure)和无线局域网保密基础结构(WPI WLAN Privacy Infrastructure)组成。WAI采用了公开密钥加密技术,用于终端与接入点之间的互相身份鉴别;WPI采用国家密码管理委员会办公室批准的用于WLAN的对称密码算法实现数据保护,对MAC子层的MSDU进行加、解密处理。规范中介绍的基础结构包括了几个功能实体,接入点(AP access point)是指任何一个具备站点功能,通过无线媒体为关联的站点提供访问分布式服务的实体;鉴别请求者实体(ASUE authentication supplicant entity)是在接入服务之前请求进行鉴别操作的实体;鉴别器实体(AE authenticator entity)为鉴别请求者在接入服务之前提供鉴别操作的实体。该实体主流在接入点或终端内;鉴别服务单元(ASU authentication service unit)的基本功能是实现对用户证书的管理和用户身份的鉴别等,是基于公开密钥密码技术的WAI鉴别基础结构中重要的组成部分;鉴别服务实体(ASE authentication service entity)为鉴别器和鉴别请求者提供身份鉴别服务的实体。该实体驻留在鉴别服务单元中,鉴别服务单元对应网络中的节点为WAPI鉴别服务器。用户证书为公开密钥证书,它是WAI系统构造中重要的环节。公开密钥证书是网络用户的数字身份凭证,通过私有密钥验证可以唯一地确定网络用户的身份。In order to solve the security loopholes in the WEP (Wired Equivalent Privacy) security mechanism defined in the international wireless LAN standard ISO/IEC 8802-11, my country promulgated the wireless local area network national standard and its No. 1 amendment, using wireless LAN authentication and confidentiality infrastructure WAPI (WLAN Authentication and Privacy Infrastructure) replaces WEP to solve the security problem of wireless local area network. WAPI consists of WAI WLAN Authentication Infrastructure and WPI WLAN Privacy Infrastructure. WAI uses public key encryption technology for mutual identity authentication between terminals and access points; WPI adopts the symmetric encryption algorithm for WLAN approved by the Office of the State Cryptography Management Encryption and decryption processing. The infrastructure introduced in the specification includes several functional entities. An access point (AP access point) refers to any entity that has a station function and provides access to distributed services for associated stations through wireless media; authentication requester entity (ASUE authentication supplicant entity) is an entity that requests authentication operations before accessing services; authenticator entity (AE authenticator entity) is an entity that provides authentication operations for authentication requesters before accessing services. The mainstream of this entity is in the access point or terminal; the basic function of the authentication service unit (ASU authentication service unit) is to realize the management of user certificates and the identification of user identities, etc. An important component; the authentication service entity (ASE authentication service entity) is an entity that provides identity authentication services for the authenticator and the authentication requester. The entity resides in the authentication service unit, and the authentication service unit corresponds to a node in the network as a WAPI authentication server. The user certificate is a public key certificate, which is an important link in the construction of the WAI system. The public key certificate is the digital identity certificate of the network user, and the identity of the network user can be uniquely determined through the private key verification.
网络存储是一种常见的互联网业务,提供各类文件内容的上传、下载和检索功能。随着WAPI的部署和实施,越来越多的移动终端支持无线局域网接入,同时也将会支持越来越多的互联网业务功能。网络存储对于移动终端而言,具有相当大的使用价值。目前的移动终端已逐渐演变为以个人沟通交流为核心的多媒体信息平台,终端强大的多媒体信息采集功能势必需要一个可靠的内存存储平台,考虑到多设备间的内容共享,网络存储无疑是一个非常有潜力的移动互联网业务。基于Web的网络存储应用在互联网环境下,通常会有自己的登录机制,如需用户提供用户名密码以辨明身份。移动终端在接入网络时已经完成了身份鉴别过程,如果可以充分利用接入鉴别的能力,一方面简化了终端用户的操作,另一方面,应用提供商可复用WAPI所依赖的公开密钥基础设施PKI(Public Key Infrastructure),包括证书颁发系统和客户端上的证书等资源,还可以向客户提供存储内容的完整性、机密性保护功能。Network storage is a common Internet service that provides functions for uploading, downloading, and retrieving various file contents. With the deployment and implementation of WAPI, more and more mobile terminals support WLAN access, and will also support more and more Internet service functions. Network storage has considerable use value for mobile terminals. The current mobile terminal has gradually evolved into a multimedia information platform with personal communication as the core. The powerful multimedia information collection function of the terminal will inevitably require a reliable memory storage platform. Considering the content sharing among multiple devices, network storage is undoubtedly a very Potential mobile Internet business. Web-based network storage applications usually have their own login mechanism in the Internet environment. For example, users are required to provide usernames and passwords to identify their identities. The mobile terminal has completed the identity authentication process when accessing the network. If the ability of access authentication can be fully utilized, on the one hand, the operation of the end user is simplified. On the other hand, the application provider can reuse the public key that WAPI relies on. Infrastructure PKI (Public Key Infrastructure), including resources such as the certificate issuing system and certificates on the client, can also provide customers with the integrity and confidentiality protection functions of stored content.
发明内容Contents of the invention
本发明要解决的技术问题是提供一种WAPI终端与应用服务器传输文件的系统及方法,有效地保证了传输文件内容的安全性。The technical problem to be solved by the present invention is to provide a system and method for transferring files between a WAPI terminal and an application server, which effectively ensures the security of the contents of the transferred files.
为了解决上述问题,本发明提供了一种WAPI终端与应用服务器传输文件的方法,包括:In order to solve the above problems, the invention provides a method for transferring files between a WAPI terminal and an application server, including:
WAPI终端与应用服务器之间采用HTTP消息传输文件内容时,发送端使用WPI算法对传输的文件内容进行加密,并对传输的内容做数字签名后传输,接收端收到包含文件内容的HTTP消息后解析出所述文件内容并验证所述数字签名,若数字签名验证通过则传输的文件内容未被更改。When the WAPI terminal and the application server use HTTP messages to transmit file content, the sending end uses the WPI algorithm to encrypt the transmitted file content, and digitally signs the transmitted content before transmission, and the receiving end receives the HTTP message containing the file content. Parsing out the content of the file and verifying the digital signature, if the digital signature is verified, the content of the transmitted file has not been changed.
进一步地,在传输文件内容前,所述终端向应用服务器发送HTTP GET请求时将该请求的一头域值表示为一预设值表示该终端为WAPI终端,所述应用服务器收到所述HTTP GET请求后若所述头域值为预设值则判定所述终端为WAPI终端。Further, before the content of the file is transmitted, when the terminal sends an HTTP GET request to the application server, the header domain value of the request is represented as a preset value indicating that the terminal is a WAPI terminal, and the application server receives the HTTP GET After the request, if the header field value is a preset value, it is determined that the terminal is a WAPI terminal.
进一步地,应用服务器收到所述终端发来的HTTP GET请求后向所述终端返回200OK消息时增加一个数字签名,所述数字签名的方式为,使用WAI散列算法计算返回的页面,并使用应用服务器WAPI证书的私钥,利用WAI的椭圆曲线算法,对散列计算结果做加密计算生成签名;Further, after the application server receives the HTTP GET request sent by the terminal, a digital signature is added when returning a 200OK message to the terminal. The way of the digital signature is to use the WAI hash algorithm to calculate the returned page, and use The private key of the WAPI certificate of the application server uses the elliptic curve algorithm of WAI to encrypt the hash calculation result to generate a signature;
所述终端收到200OK消息后解析出所述数字签名,获取预存于终端上的应用服务器WAPI证书的公钥解密该数字签名,并利用WAI的散列函数对网页内容进行散列计算,之后比较散列计算的结果与解密的数字签名是否一致,若一致则通过对应用服务器的鉴别,否则鉴别未通过。After the terminal receives the 200OK message, it parses out the digital signature, obtains the public key of the WAPI certificate of the application server pre-stored on the terminal to decrypt the digital signature, and uses the hash function of WAI to perform hash calculation on the webpage content, and then compares Whether the result of the hash calculation is consistent with the decrypted digital signature, if they are consistent, the authentication of the application server is passed, otherwise the authentication is not passed.
进一步地,当所述终端向应用服务器上传内容时,先生成一个128位随机数作为临时会话密钥,使用WPI中的SMS4算法对上传文件内容做加密得到密文,接着使用应用服务器WAPI证书的公钥对临时会话密钥进行公开密钥算法加密得到加密后的密钥,还对上传的文件内容做数字签名;加密后的密文、数字签名和加密后的随机数和用户WAPI证书标识或WAPI证书一起封装,将封装的内容通过HTTP POST发送至应用服务器;Further, when the terminal uploads content to the application server, first generate a 128-bit random number as a temporary session key, use the SMS4 algorithm in WPI to encrypt the content of the uploaded file to obtain ciphertext, and then use the WAPI certificate of the application server to The public key encrypts the temporary session key with the public key algorithm to obtain the encrypted key, and also digitally signs the uploaded file content; the encrypted ciphertext, digital signature, encrypted random number and user WAPI certificate ID or Encapsulate the WAPI certificate together, and send the encapsulated content to the application server through HTTP POST;
所述应用服务器收到所述HTTP POST后,分离出用户的WAPI证书标识或WAPI证书,若分离出的是WAPI证书标识则获取WAPI证书,使用应用服务器的WAPI证书的私钥对加密后的密钥进行公开密钥算法解密得到临时会话密钥,对上传内容中的密文进行对称密钥算法解密得到正文,并对解密出的正文进行散列计算得到散列值,所述应用服务器还使用终端WAPI证书的公钥对签名进行公开密钥算法解密得到另一散列值,之后比较得到的上述2个散列值是否一致,若一致则对终端的验证通过,且接收的文件内容未被更改。After the application server receives the HTTP POST, it separates the user's WAPI certificate identifier or WAPI certificate, if the WAPI certificate identifier is separated, the WAPI certificate is obtained, and the encrypted password is encrypted using the private key of the WAPI certificate of the application server. public key algorithm to decrypt the key to obtain a temporary session key, decrypt the ciphertext in the uploaded content with a symmetric key algorithm to obtain the text, and perform hash calculation on the decrypted text to obtain a hash value. The application server also uses The public key of the terminal WAPI certificate decrypts the signature with the public key algorithm to obtain another hash value, and then compare whether the above two hash values are consistent. If they are consistent, the verification of the terminal is passed, and the received file content is not blocked. Change.
进一步地,当所述终端从应用服务器获取内容时,向应用服务器发送HTTP GET消息时携带要获取内容对应的统一资源定位符;Further, when the terminal obtains the content from the application server, when sending the HTTP GET message to the application server, it carries the uniform resource locator corresponding to the content to be obtained;
所述应用服务器收到HTTP GET消息后根据所述统一资源定位符获知终端请求的文档内容,之后生成128位随机数作为临时会话密钥,并使用此临时会话密钥对客户端请求的文档内容做SMS4加密,并对文档内容做数字签名,还使用终端WAPI证书的公钥对临时会话密钥进行公开密钥算法加密得到加密后的密钥,所有内容以固定格式封装或以表单形式作为200OK消息体返回给终端;After the application server receives the HTTP GET message, it obtains the document content requested by the terminal according to the uniform resource locator, and then generates a 128-bit random number as a temporary session key, and uses this temporary session key to verify the content of the document requested by the client. Do SMS4 encryption, and digitally sign the content of the document, and use the public key of the terminal WAPI certificate to encrypt the temporary session key with a public key algorithm to obtain the encrypted key. All content is encapsulated in a fixed format or in the form of a form as 200OK The message body is returned to the terminal;
所述终端收到所述200OK消息后,利用终端WAPI证书的私钥对加密的密钥进行公开密钥算法解密得出临时会话密钥,之后使用该临时会话密钥对密文进行对称密钥算法解密得到文档正文,并对解密出的正文进行散列计算得到散列值,还使用应用服务器WAPI证书的公钥对签名进行公开密钥算法解密得到另一散列值,比较得到的上述2个散列值是否一致,若一致则验证通过,且接收的文件内容未被更改。After the terminal receives the 200OK message, it uses the private key of the terminal WAPI certificate to decrypt the encrypted key with a public key algorithm to obtain a temporary session key, and then uses the temporary session key to perform symmetric key encryption on the ciphertext. The algorithm decrypts to get the text of the document, and hashes the decrypted text to get the hash value, and uses the public key of the application server WAPI certificate to decrypt the signature with the public key algorithm to get another hash value, and compares the above 2 Whether the hash values are consistent, if they are consistent, the verification is passed, and the content of the received file has not been changed.
进一步地,所述终端向应用服务器发送HTTP GET消息时对所述统一资源定位符进行数字签名,之后将所述数字签名及用户证书标识作为统一资源定位符参数通过HTTP GET消息发送至应用服务器,所述应用服务器收到HTTP GET消息后分离出用户证书标识,并获取用户证书,之后使用证书中的公开密钥解密该数字签名,并利用WAI的散列函数对网页内容进行散列计算,之后比较散列计算的结果与解密的数字签名是否一致,若一致则通过对终端的鉴别。Further, when the terminal sends an HTTP GET message to the application server, digitally signs the uniform resource locator, and then sends the digital signature and the user certificate identifier as parameters of the uniform resource locator to the application server through the HTTP GET message, After the application server receives the HTTP GET message, it separates the user certificate identifier and obtains the user certificate, then uses the public key in the certificate to decrypt the digital signature, and uses the hash function of WAI to perform hash calculation on the webpage content, and then Compare whether the result of the hash calculation is consistent with the decrypted digital signature, and if they are consistent, pass the authentication of the terminal.
进一步地,所述终端对上传的文件内容做数字签名是指,对所述文件内容做散列计算,之后使用终端WAPI证书的私钥对散列计算后的值进行公开密钥算法加密。Further, the digital signature of the uploaded file content by the terminal refers to performing hash calculation on the file content, and then using the private key of the terminal WAPI certificate to encrypt the hash calculated value with a public key algorithm.
进一步地,所述应用服务器对文档内容做签名计算是指,对所述文档内容做散列计算,之后使用应用服务器WAPI证书的私钥对散列计算后的值进行公开密钥算法加密。Further, the application server performing signature calculation on the document content refers to performing hash calculation on the document content, and then using the private key of the WAPI certificate of the application server to encrypt the hash calculated value with a public key algorithm.
本发明还提供一种WAPI终端与应用服务器传输文件的系统,包括发送端与接收端;The present invention also provides a system for transferring files between a WAPI terminal and an application server, including a sending end and a receiving end;
所述发送端,用于使用WPI算法对传输的文件内容进行加密,并对传输的内容做数字签名后通过HTTP消息发送至所述接收端;The sending end is used to use the WPI algorithm to encrypt the content of the transmitted file, and digitally sign the transmitted content and send it to the receiving end through an HTTP message;
所述接收端,用于收到所述HTTP消息后解析出所述文件内容并验证所述数字签名,若数字签名验证通过则传输的文件内容未被更改。The receiving end is configured to parse out the file content and verify the digital signature after receiving the HTTP message, and if the digital signature is verified, the transmitted file content has not been changed.
进一步地,所述发送端为WAPI终端或应用服务器,接收端为应用服务器或WAPI终端;Further, the sending end is a WAPI terminal or an application server, and the receiving end is an application server or a WAPI terminal;
所述终端包括设置模块、发送模块;The terminal includes a setting module and a sending module;
所述终端的设置模块用于在传输文件内容前,向应用服务器发送HTTPGET请求时将该请求的一头域值表示为一预设值表示该终端为WAPI终端;The setting module of the terminal is used to represent a header domain value of the request as a preset value when sending an HTTPGET request to the application server before transmitting the file content, indicating that the terminal is a WAPI terminal;
所述应用服务器用于收到所述HTTP GET请求后若所述头域值为预设值则判定所述终端为WAPI终端。The application server is configured to determine that the terminal is a WAPI terminal if the header field value is a preset value after receiving the HTTP GET request.
进一步地,所述应用服务器包括加密模块及发送模块;Further, the application server includes an encryption module and a sending module;
所述应用服务器的加密模块用于使用WAI散列算法计算返回的页面,并使用应用服务器WAPI证书的私钥,利用WAI的椭圆曲线算法,对散列计算结果做加密计算生成数字签名;The encryption module of the application server is used to use the WAI hash algorithm to calculate the returned page, and use the private key of the application server WAPI certificate to utilize the elliptic curve algorithm of WAI to encrypt the hash calculation result to generate a digital signature;
所述应用服务器的发送模块用于向终端返回200OK消息时携带上述数字签名;The sending module of the application server is used to carry the above-mentioned digital signature when returning a 200OK message to the terminal;
所述终端的解密模块收到200OK消息后解析出所述数字签名,获取预存于终端上的应用服务器WAPI证书的公钥解密该数字签名,并利用WAI的散列函数对网页内容进行散列计算,之后比较散列计算的结果与解密的数字签名是否一致,若一致则通过对应用服务器的鉴别,否则鉴别未通过。The decryption module of the terminal parses out the digital signature after receiving the 200OK message, obtains the public key of the WAPI certificate of the application server pre-stored on the terminal to decrypt the digital signature, and uses the hash function of WAI to perform hash calculation on the web page content , and then compare whether the result of the hash calculation is consistent with the decrypted digital signature. If they are consistent, the authentication to the application server is passed; otherwise, the authentication fails.
进一步地,当所述终端向应用服务器上传内容时所述终端为发送端,所述应用服务器为接收端;Further, when the terminal uploads content to the application server, the terminal is the sending end, and the application server is the receiving end;
所述终端包括加密模块及发送模块;The terminal includes an encryption module and a sending module;
所述终端的加密模块,用于生成一个128位随机数作为临时会话密钥,以及使用WPI中的SMS4算法对上传的文件内容做加密得到密文,使用应用服务器WAPI证书的公钥对临时会话密钥进行公开密钥算法加密得到加密后的密钥,还用于对上传的文件内容做数字签名;The encryption module of the terminal is used to generate a 128-bit random number as a temporary session key, and use the SMS4 algorithm in WPI to encrypt the content of the uploaded file to obtain ciphertext, and use the public key of the application server WAPI certificate to pair the temporary session key. The key is encrypted with a public key algorithm to obtain the encrypted key, which is also used to digitally sign the content of the uploaded file;
所述终端的发送模块,用于将加密后的密文、数字签名、加密后的随机数和用户WAPI证书标识或WAPI证书一起封装,以及将封装的内容通过HTTP POST发送至应用服务器;The sending module of the terminal is used to encapsulate encrypted ciphertext, digital signature, encrypted random number and user WAPI certificate identification or WAPI certificate together, and send the encapsulated content to the application server through HTTP POST;
所述应用服务器包括接收模块及解密模块;The application server includes a receiving module and a decryption module;
所述应用服务器的接收模块,用于收到所述HTTP POST后,分离出用户的WAPI证书标识或WAPI证书,若分离出的是WAPI证书标识则获取WAPI证书;The receiving module of the application server is used to separate the user's WAPI certificate identification or WAPI certificate after receiving the HTTP POST, and obtain the WAPI certificate if the WAPI certificate identification is separated;
所述应用服务器的解密模块,用于使用应用服务器的WAPI证书的私钥对加密后的密钥进行公开密钥算法解密得到临时会话密钥,以及使用该临时会话密钥对上传内容中的密文进行对称密钥算法解密得到正文,并对解密出的正文进行散列计算得到散列值,还用于使用终端WAPI证书的公钥对签名进行公开密钥算法解密得到另一散列值,并比较得到的上述2个散列值是否一致,若一致则对终端的验证通过,且接收的文件内容未被更改。The decryption module of the application server is used to use the private key of the WAPI certificate of the application server to perform public key algorithm decryption on the encrypted key to obtain a temporary session key, and use the temporary session key to decrypt the encrypted key in the uploaded content. The text is decrypted by a symmetric key algorithm to obtain the text, and the decrypted text is hashed to obtain a hash value, which is also used to decrypt the signature with a public key algorithm using the public key of the terminal WAPI certificate to obtain another hash value. And compare whether the obtained above two hash values are consistent, if they are consistent, the verification of the terminal is passed, and the content of the received file has not been changed.
进一步地,当所述终端从应用服务器获取内容时所述应用服务器为发送端,所述终端为接收端;Further, when the terminal acquires content from the application server, the application server is the sending end, and the terminal is the receiving end;
所述终端包括发送模块、接收模块及解密模块;The terminal includes a sending module, a receiving module and a decryption module;
所述终端的发送模块用于向应用服务器发送HTTP GET消息时携带要获取内容对应的统一资源定位符;The sending module of the terminal is used to carry the uniform resource locator corresponding to the content to be obtained when sending the HTTP GET message to the application server;
所述应用服务器包括接收模块、加密模块及发送模块;The application server includes a receiving module, an encryption module and a sending module;
所述应用服务器的接收模块,用于收到HTTP GET消息后根据所述统一资源定位符获知终端请求的文档内容;The receiving module of the application server is used to obtain the document content requested by the terminal according to the uniform resource locator after receiving the HTTP GET message;
所述应用服务器的加密模块,用于生成128位随机数作为临时会话密钥,以及使用该临时会话密钥对终端请求的文档内容做SMS4加密形成密文,并对文档内容做数字签名,还用于使用终端WAPI证书的公钥对临时会话密钥进行公开密钥算法加密得到加密后的密钥;The encryption module of the application server is used to generate a 128-bit random number as a temporary session key, and use the temporary session key to perform SMS4 encryption on the content of the document requested by the terminal to form a ciphertext, and digitally sign the content of the document, and It is used to encrypt the temporary session key with the public key algorithm using the public key of the terminal WAPI certificate to obtain the encrypted key;
所述应用服务器的发送模块,用于将所述密文、签名以及加密后的临时会话密钥作为200OK消息体发送至终端;The sending module of the application server is used to send the ciphertext, the signature and the encrypted temporary session key to the terminal as a 200 OK message body;
所述终端的接收模块,用于将收到的所述200OK消息发送至解密模块;The receiving module of the terminal is configured to send the received 200OK message to a decryption module;
所述终端的解密模块,用于使用终端WAPI证书的私钥对加密的密钥进行公开密钥算法解密得出临时会话密钥,以及该临时会话密钥对密文进行对称密钥算法解密得到文档正文,并对解密出的正文进行散列计算得到散列值,还用于使用应用服务器WAPI证书的公钥对签名进行公开密钥算法解密得到另一散列值,以及比较得到的上述2个散列值是否一致,若一致则验证通过,且接收的文件内容未被更改。The decryption module of the terminal is used to use the private key of the terminal WAPI certificate to decrypt the encrypted key with a public key algorithm to obtain a temporary session key, and the temporary session key to decrypt the ciphertext with a symmetric key algorithm to obtain Document text, and hash the decrypted text to obtain a hash value, and use the public key of the application server WAPI certificate to decrypt the signature with a public key algorithm to obtain another hash value, and compare the above 2 Whether the hash values are consistent, if they are consistent, the verification is passed, and the content of the received file has not been changed.
进一步地,所述终端的加密模块还用于向应用服务器发送HTTP GET消息时对所述统一资源定位符进行数字签名;Further, the encryption module of the terminal is also used to digitally sign the uniform resource locator when sending an HTTP GET message to the application server;
所述终端的发送模块还用于向应用服务器发送HTTP GET消息时将所述数字签名及用户证书标识作为统一资源定位符参数发送至应用服务器;The sending module of the terminal is also used to send the digital signature and the user certificate identification to the application server as uniform resource locator parameters when sending the HTTP GET message to the application server;
所述应用服务器的解密模块还用于分离出HTTP GET消息中的用户证书标识,并获取用户证书,以及使用证书中的公开密钥解密该数字签名,并利用WAI的散列函数对统一资源定位符进行散列计算,之后比较散列计算的结果与解密的数字签名是否一致,若一致则通过对终端的鉴别。The decryption module of the application server is also used to separate the user certificate identification in the HTTP GET message, and obtain the user certificate, and use the public key in the certificate to decrypt the digital signature, and utilize the hash function of WAI to locate the unified resource Then, compare the result of the hash calculation with the decrypted digital signature, and if they are consistent, pass the authentication of the terminal.
进一步地,所述终端的加密模块对上传的文件内容做数字签名是指,对所述文件内容做散列计算,之后使用终端WAPI证书的私钥对散列计算后的值进行公开密钥算法加密。Further, digitally signing the uploaded file content by the encryption module of the terminal refers to performing a hash calculation on the file content, and then using the private key of the terminal WAPI certificate to perform a public key algorithm on the hashed value. encryption.
进一步地,所述应用服务器的加密模块对文档内容做签名计算是指,对所述文档内容做散列计算,之后使用应用服务器WAPI证书的私钥对散列计算后的值进行公开密钥算法加密。Further, the encryption module of the application server performing signature calculation on the document content refers to performing a hash calculation on the document content, and then using the private key of the application server WAPI certificate to perform a public key algorithm on the value after the hash calculation encryption.
采用本发明的技术方案,充分利用了WAPI基础设施提供的公开密钥证书颁发机构和客户端WAPI证书。WAPI终端用户在登录网络存储应用的过程中,依靠WAPI鉴别服务实现用户登录过程,登录过程无需用户输入用户名密码。客户端在保存内容时,通过证书鉴别过程中协商得到的临时会话密钥和对称加密算法,加密存储内容,确保内容机密性,客户端通过散列函数和公有证书的私有密钥,对存储内容做数字签名计算,并由服务器侧验证签名和解密内容,确保内容真实有效未被修改。客户端在获取内容时,通过证书鉴别过程中协商的临时会话密钥和对称加密算法,解密获取内容。本发明中介绍用户认证的方法亦可应用于其他基于Web访问的网络应用。By adopting the technical solution of the present invention, the public key certificate authority provided by the WAPI infrastructure and the WAPI certificate of the client are fully utilized. In the process of logging in to the network storage application, the WAPI terminal user relies on the WAPI authentication service to realize the user login process, and the login process does not require the user to enter the user name and password. When the client saves the content, it encrypts the stored content through the temporary session key negotiated during the certificate authentication process and the symmetric encryption algorithm to ensure the confidentiality of the content. The client uses the hash function and the private key of the public certificate to store the content. Do digital signature calculation, and verify the signature and decrypt the content by the server side to ensure that the content is true and valid and has not been modified. When the client obtains the content, it decrypts and obtains the content through the temporary session key negotiated during the certificate authentication process and the symmetric encryption algorithm. The user authentication method introduced in the present invention can also be applied to other network applications based on Web access.
附图说明Description of drawings
图1网络系统结构;Figure 1 network system structure;
图2是本发明系统结构示意图;Fig. 2 is a schematic structural diagram of the system of the present invention;
图3是本发明终端向应用服务器上传内容时的流程图;Fig. 3 is a flow chart when the terminal of the present invention uploads content to the application server;
图4是本发明终端从应用服务器获取内容时的流程图;Fig. 4 is a flow chart when the terminal of the present invention acquires content from the application server;
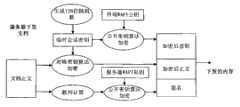
图5是本发明终端上传内容时的处理过程图;Fig. 5 is a process diagram when the terminal of the present invention uploads content;
图6是本发明应用服务器下发内容时的处理过程图;Fig. 6 is a process diagram when the application server of the present invention delivers content;
图7是本发明终端及应用服务器接收文件内容后的处理过程图;Fig. 7 is a process diagram of the terminal and the application server of the present invention after receiving the content of the file;
图8是本发明终端对应用服务器进行鉴别的处理过程图。Fig. 8 is a process diagram of the authentication process of the terminal to the application server in the present invention.
具体实施方式Detailed ways
本发明提供一种WAPI终端与应用服务器传输文件的系统,如图2所示,该系统包括发送端与接收端;The present invention provides a system for transferring files between a WAPI terminal and an application server, as shown in Figure 2, the system includes a sending end and a receiving end;
发送端为WAPI终端或应用服务器,接收端为应用服务器或WAPI终端;The sending end is a WAPI terminal or an application server, and the receiving end is an application server or a WAPI terminal;
发送端,用于使用WPI算法对传输的文件内容进行加密,并对传输的内容做数字签名后通过HTTP消息发送至所述接收端;The sending end is used to encrypt the content of the transmitted file using the WPI algorithm, and digitally sign the transmitted content and send it to the receiving end through an HTTP message;
接收端,用于收到HTTP消息后解析出文件内容并验证数字签名,若数字签名验证通过则传输的文件内容未被更改。The receiving end is used to parse out the file content and verify the digital signature after receiving the HTTP message. If the digital signature verification passes, the transmitted file content has not been changed.
终端包括设置模块、加密模块、解密模块、发送模块及接收模块;The terminal includes a setting module, an encryption module, a decryption module, a sending module and a receiving module;
应用服务器包括加密模块、解密模块、发送模块及接收模块;The application server includes an encryption module, a decryption module, a sending module and a receiving module;
终端的设置模块用于在传输文件内容前,向应用服务器发送HTTP GET请求时将该请求的一头域值表示为一预设值表示该终端为WAPI终端,应用服务器收到HTTP GET请求后若该头域值为预设值则判定终端为WAPI终端。The terminal setting module is used to represent the header domain value of the request as a preset value when sending an HTTP GET request to the application server before transmitting the file content, indicating that the terminal is a WAPI terminal. After the application server receives the HTTP GET request, if the If the header field value is a preset value, it is determined that the terminal is a WAPI terminal.
应用服务器的加密模块用于使用WAI散列算法计算返回的页面,并使用应用服务器WAPI证书的私钥,利用WAI的椭圆曲线算法,对散列计算结果做加密计算生成数字签名;The encryption module of the application server is used to use the WAI hash algorithm to calculate the returned page, and use the private key of the WAPI certificate of the application server to use the elliptic curve algorithm of WAI to perform encryption calculation on the hash calculation result to generate a digital signature;
应用服务器的发送模块用于向终端返回200OK消息时携带上述数字签名;The sending module of the application server is used to carry the above-mentioned digital signature when returning the 200OK message to the terminal;
终端的解密模块用于收到200OK消息后解析出数字签名,获取预存于终端上的应用服务器WAPI证书中的公钥解密该数字签名,并利用WAI的散列函数对网页内容进行散列计算,之后比较散列计算的结果与解密的数字签名是否一致,若一致则通过对应用服务器的鉴别,否则鉴别未通过。The decryption module of the terminal is used to parse out the digital signature after receiving the 200OK message, obtain the public key in the WAPI certificate of the application server pre-stored on the terminal to decrypt the digital signature, and use the hash function of WAI to perform hash calculation on the webpage content. Then compare whether the result of the hash calculation is consistent with the decrypted digital signature. If they are consistent, the authentication to the application server is passed; otherwise, the authentication fails.
(1)当终端向应用服务器上传内容时终端为发送端,应用服务器为接收端;(1) When the terminal uploads content to the application server, the terminal is the sending end, and the application server is the receiving end;
终端的加密模块,用于生成一个128位随机数作为临时会话密钥,以及使用WPI中的SMS4算法对上传的文件内容做加密得到密文,使用应用服务器WAPI证书的公钥对临时会话密钥进行公开密钥算法加密得到加密后的密钥,还用于对上传的文件内容做数字签名;The encryption module of the terminal is used to generate a 128-bit random number as a temporary session key, and use the SMS4 algorithm in WPI to encrypt the content of the uploaded file to obtain ciphertext, and use the public key of the WAPI certificate of the application server to pair the temporary session key Perform public key algorithm encryption to obtain the encrypted key, which is also used to digitally sign the uploaded file content;
终端的发送模块,用于将加密后的密文、数字签名、加密后的随机数和用户WAPI证书标识或WAPI证书一起封装,以及将封装的内容通过HTTPPOST发送至应用服务器;The sending module of the terminal is used to encapsulate encrypted ciphertext, digital signature, encrypted random number and user WAPI certificate identifier or WAPI certificate together, and send the encapsulated content to the application server through HTTPPOST;
应用服务器的接收模块,用于收到HTTP POST后,分离出用户的WAPI证书标识或WAPI证书,若分离出的是WAPI证书标识则获取WAPI证书;The receiving module of the application server is used to separate the user's WAPI certificate identifier or WAPI certificate after receiving the HTTP POST, and obtain the WAPI certificate if the separated WAPI certificate identifier is obtained;
应用服务器的解密模块,用于使用应用服务器的WAPI证书的私钥对加密后的密钥进行公开密钥算法解密得到临时会话密钥,以及使用该临时会话密钥对上传内容中的密文进行对称密钥算法解密得到正文,并对解密出的正文进行散列计算得到散列值,还用于使用终端WAPI证书的公钥对签名进行公开密钥算法解密得到另一散列值,并比较得到的上述2个散列值是否一致,若一致则对终端的验证通过,且接收的文件内容未被更改。The decryption module of the application server is used to use the private key of the WAPI certificate of the application server to decrypt the encrypted key with a public key algorithm to obtain a temporary session key, and use the temporary session key to decrypt the ciphertext in the uploaded content. The symmetric key algorithm is used to decrypt the text to obtain the text, and the decrypted text is hashed to obtain the hash value, which is also used to decrypt the signature with the public key algorithm using the public key of the terminal WAPI certificate to obtain another hash value, and compared Whether the obtained above two hash values are consistent, if they are consistent, the verification of the terminal is passed, and the content of the received file has not been changed.
终端的加密模块对上传的文件内容做数字签名是指,对文件内容做散列计算,之后使用终端WAPI证书的私钥对散列计算后的值进行公开密钥算法加密。The digital signature of the uploaded file content by the encryption module of the terminal refers to performing hash calculation on the file content, and then using the private key of the terminal WAPI certificate to encrypt the hashed value with a public key algorithm.
(2)当终端从应用服务器获取内容时应用服务器为发送端,终端为接收端;(2) When the terminal acquires content from the application server, the application server is the sending end, and the terminal is the receiving end;
终端的发送模块,用于向应用服务器发送HTTP GET消息时携带要获取内容对应的统一资源定位符;The sending module of the terminal is used to carry the uniform resource locator corresponding to the content to be obtained when sending the HTTP GET message to the application server;
应用服务器的接收模块,用于收到HTTP GET消息后根据统一资源定位符获知终端请求的文档内容;The receiving module of the application server is used to obtain the content of the document requested by the terminal according to the uniform resource locator after receiving the HTTP GET message;
应用服务器的加密模块,用于生成128位随机数作为临时会话密钥,以及使用该临时会话密钥对终端请求的文档内容做SMS4加密形成密文,并对文档内容做数字签名,还用于使用终端WAPI证书的公钥对临时会话密钥进行公开密钥算法加密得到加密后的密钥;The encryption module of the application server is used to generate a 128-bit random number as a temporary session key, and use the temporary session key to perform SMS4 encryption on the document content requested by the terminal to form ciphertext, and to digitally sign the document content. Use the public key of the terminal WAPI certificate to encrypt the temporary session key with a public key algorithm to obtain the encrypted key;
应用服务器的发送模块,用于将密文、签名以及加密后的临时会话密钥作为200OK消息体发送至终端;The sending module of the application server is used to send the ciphertext, signature and encrypted temporary session key to the terminal as a 200OK message body;
终端的接收模块,用于将收到的200OK消息发送至解密模块;The receiving module of the terminal is used to send the received 200OK message to the decryption module;
终端的解密模块,用于使用终端WAPI证书的私钥对加密的密钥进行公开密钥算法解密得出临时会话密钥,以及该临时会话密钥对密文进行对称密钥算法解密得到文档正文,并对解密出的正文进行散列计算得到散列值,还用于使用应用服务器WAPI证书的公钥对签名进行公开密钥算法解密得到另一散列值,以及比较得到的上述2个散列值是否一致,若一致则验证通过,且接收的文件内容未被更改。The decryption module of the terminal is used to use the private key of the terminal WAPI certificate to decrypt the encrypted key with a public key algorithm to obtain a temporary session key, and the temporary session key to decrypt the ciphertext with a symmetric key algorithm to obtain the text of the document , and hash the decrypted text to obtain a hash value, and use the public key of the application server WAPI certificate to decrypt the signature with a public key algorithm to obtain another hash value, and compare the above two hashes Whether the column values are consistent, if they are consistent, the verification is passed, and the content of the received file has not been changed.
终端的加密模块还用于向应用服务器发送HTTP GET消息时对统一资源定位符进行数字签名;The encryption module of the terminal is also used to digitally sign the Uniform Resource Locator when sending the HTTP GET message to the application server;
终端的发送模块还用于向应用服务器发送HTTP GET消息时将数字签名及用户证书标识作为统一资源定位符参数发送至应用服务器;The sending module of the terminal is also used to send the digital signature and the user certificate identification as uniform resource locator parameters to the application server when sending the HTTP GET message to the application server;
应用服务器的解密模块还用于分离出HTTP GET消息中的用户证书标识,并获取用户证书,以及使用证书中的公开密钥解密该数字签名,并利用WAI的散列函数对统一资源定位符进行散列计算,之后比较散列计算的结果与解密的数字签名是否一致,若一致则通过对终端的鉴别。The decryption module of the application server is also used to separate out the user certificate identifier in the HTTP GET message, obtain the user certificate, and use the public key in the certificate to decrypt the digital signature, and use the hash function of WAI to perform a process on the uniform resource locator. Hash calculation, and then compare whether the result of the hash calculation is consistent with the decrypted digital signature, and if they are consistent, pass the authentication of the terminal.
应用服务器的加密模块对文档内容做签名计算是指,对文档内容做散列计算,之后使用应用服务器WAPI证书的私钥对散列计算后的值进行公开密钥算法加密。The encryption module of the application server performs signature calculation on the document content, which refers to performing hash calculation on the document content, and then uses the private key of the WAPI certificate of the application server to encrypt the value after the hash calculation with a public key algorithm.
本发明还提供一种WAPI终端与应用服务器传输文件的方法,WAPI终端与应用服务器之间采用HTTP消息传输文件内容时,发送端使用WPI算法对传输的文件内容进行加密,并对传输的内容做数字签名后传输,接收端收到包含文件内容的HTTP消息后解析出文件内容并验证数字签名,若数字签名验证通过则传输的文件内容未被更改。The present invention also provides a method for transmitting files between a WAPI terminal and an application server. When HTTP messages are used to transmit file content between the WAPI terminal and the application server, the sending end uses the WPI algorithm to encrypt the transmitted file content, and encrypts the transmitted content. After the digital signature is transmitted, the receiving end parses the file content and verifies the digital signature after receiving the HTTP message containing the file content. If the digital signature verification passes, the transmitted file content has not been changed.
实施例一Embodiment one
本实施例为终端向应用服务器上传文件内容的方法,如图3所示,包括以下步骤:This embodiment is a method for a terminal to upload file content to an application server, as shown in Figure 3, including the following steps:
步骤301:终端浏览器向应用服务器发送HTTP GET请求,获取到网络存储应用的页面,终端通过将请求中的某头域值设置为预设值表示其为WAPI终端,如可以是将User-Agent(用户代理)设置为WAPI-Mobile-ClientV1.0;Step 301: The terminal browser sends an HTTP GET request to the application server to obtain the page of the network storage application, and the terminal indicates that it is a WAPI terminal by setting a header field value in the request to a preset value, such as User-Agent (User Agent) is set to WAPI-Mobile-ClientV1.0;
该头域的值可以是终端在组建请求时指定,也可以通过和无线局域网段相邻的WAP/HTTP应用网关修改。The value of the header field can be specified by the terminal when forming the request, or can be modified by the WAP/HTTP application gateway adjacent to the wireless local area network segment.
步骤302:应用服务器收到终端发来的HTTP GET请求,根据其中某头域中的值判断此请求是否来自于WAPI终端;如根据User-Agent的值为WAPI-Mobile-Client V1.0时判定该终端是WAPI终端;Step 302: The application server receives the HTTP GET request sent by the terminal, and judges whether the request comes from a WAPI terminal according to the value in one of the header fields; if the value of User-Agent is WAPI-Mobile-Client V1.0, it is judged The terminal is a WAPI terminal;
步骤303:应用服务器向终端返回200OK消息,在该消息中增加一个隐藏表单,内容至少包含一个采用WAI公开密钥算法加密的数字签名,签名方法如下:Step 303: The application server returns a 200OK message to the terminal, and a hidden form is added to the message, the content of which contains at least one digital signature encrypted with the WAI public key algorithm, and the signature method is as follows:
(a)使用WAI散列算法计算返回的页面、即超文本格式字符串。(a) Use the WAI hash algorithm to calculate the returned page, that is, the hypertext format string.
(b)使用应用服务器WAPI证书的私钥,利用WAI的椭圆曲线算法,对散列计算结果做加密计算,生成签名。(b) Use the private key of the WAPI certificate of the application server and use the elliptic curve algorithm of WAI to perform encryption calculation on the hash calculation result to generate a signature.
生成的签名存入页面响应中的隐藏表单里下发给终端浏览器。The generated signature is stored in the hidden form in the page response and sent to the terminal browser.
步骤304:如图8所示,终端在收到200OK消息后,从隐藏表单中解析出数字签名,获取预存于终端上的应用服务器WAPI证书中的公钥解密该数字签名,并利用WAI的散列函数对网页内容进行散列计算,之后比较散列计算的结果与解密的数字签名是否一致,若一致则鉴别通过,否则鉴别未通过。Step 304: As shown in Figure 8, after receiving the 200OK message, the terminal parses the digital signature from the hidden form, obtains the public key in the WAPI certificate of the application server pre-stored on the terminal to decrypt the digital signature, and uses the hash of the WAI to decrypt the digital signature. The column function performs hash calculation on the content of the web page, and then compares whether the result of the hash calculation is consistent with the decrypted digital signature. If they are consistent, the authentication passes, otherwise the authentication fails.
本发明中终端获得应用服务器WAPI证书的方法同现有技术。The method for the terminal to obtain the WAPI certificate of the application server in the present invention is the same as that of the prior art.
步骤305:WAPI终端浏览器在获取应用服务器网页数据并完成对服务器身份鉴别之后,呈现页面。终端通过浏览器提交需上传的文件内容。提交过程采用HTTP POST方法。Step 305: The WAPI terminal browser presents the page after obtaining the web page data of the application server and completing the identity authentication of the server. The terminal submits the content of the file to be uploaded through the browser. The submission process uses the HTTP POST method.
WAPI终端首先生成一个128位随机数作为临时会话密钥,使用WPI中SMS4算法(即图5中的对称密钥算法)对上传文件内容做加密得到密文,接着使用应用服务器WAPI证书的公钥对临时会话密钥进行公开密钥算法加密得到加密后的密钥,接着使用终端WAPI证书的私钥完成上传的内容的数字签名,数字签名的过程即先对文件内容做散列计算,然后使用终端WAPI证书的私钥加密散列计算后的值;加密后的正文、数字签名和加密后的随机数和用户WAPI证书标识或证书通过某一固定格式封装,例如:The WAPI terminal first generates a 128-bit random number as a temporary session key, uses the SMS4 algorithm in WPI (that is, the symmetric key algorithm in Figure 5) to encrypt the content of the uploaded file to obtain the ciphertext, and then uses the public key of the WAPI certificate of the application server Encrypt the temporary session key with the public key algorithm to obtain the encrypted key, and then use the private key of the terminal WAPI certificate to complete the digital signature of the uploaded content. The process of digital signature is to perform hash calculation on the file content first, and then use The encrypted hash value of the private key of the terminal WAPI certificate; the encrypted text, digital signature, encrypted random number, and user WAPI certificate ID or certificate are encapsulated in a fixed format, for example:
<upload-content><upload-content>
<body-sign>@e23233dsew.....</body-sign><body-sign>@e23233dsew.....</body-sign>
<encrypted-rand>we233dse..</encrypted-rand><encrypted-rand>we233dse..</encrypted-rand>
<encrypted-body>3EWRW@#4..</encrypted-body><encrypted-body>3EWRW@#4..</encrypted-body>
<cert-id>232341</cert-id><cert-id>232341</cert-id>
</upload-content></upload-content>
终端浏览器或通过表单的方式,组成了POST的内容并发送给应用服务器。The terminal browser or through the form forms the content of POST and sends it to the application server.
步骤306:应用服务器收到此HTTP POST消息后,首先根据表单或者某一固定格式,分离出用户的WAPI证书标识或WAPI证书,如果是证书标识,则通过与公共认证中心的交互,获取用户的公钥证书(获取过程为标准流程,本发明不再详述)。Step 306: After receiving the HTTP POST message, the application server first separates the user's WAPI certificate ID or WAPI certificate according to the form or a fixed format. If it is a certificate ID, it obtains the user's ID through interaction with the public authentication center Public key certificate (the acquisition process is a standard procedure, which will not be described in detail in the present invention).
应用服务器获取由终端生成的并由应用服务器公钥加密的后的随机数加密值,使用应用服务器的WAPI证书的私钥对加密后的密钥进行公开密钥算法解密得到128位临时会话密钥,之后使用此128位临时会话密钥对上传内容中的密文进行对称密钥算法解密得到正文,并对解密出的正文进行散列计算得到散列值,应用服务器还使用终端WAPI证书的公钥对签名进行公开密钥算法解密得到另一散列值,之后比较得到的上述2个散列值是否一致,若一致则验证通过,说明上传的文件内容未被更改,若不一致则验证未通过。The application server obtains the random number encryption value generated by the terminal and encrypted by the public key of the application server, and uses the private key of the WAPI certificate of the application server to decrypt the encrypted key with a public key algorithm to obtain a 128-bit temporary session key , and then use the 128-bit temporary session key to decrypt the ciphertext in the uploaded content using the symmetric key algorithm to obtain the text, and perform hash calculation on the decrypted text to obtain the hash value. The application server also uses the public key of the terminal WAPI certificate The public key algorithm decrypts the signature of the key pair to obtain another hash value, and then compares whether the above two hash values obtained are consistent. If they are consistent, the verification passes, indicating that the uploaded file content has not been changed. If they are inconsistent, the verification fails. .
实施例二Embodiment two
本实施例为终端从应用服务器获取内容的方法,如图4所示,包括以下步骤:This embodiment is a method for a terminal to obtain content from an application server, as shown in FIG. 4 , including the following steps:
步骤401:终端浏览器向应用服务器发送HTTP GET请求,获取到网络存储应用的页面,终端通过将请求的某头域值设置为一预设值表示其为WAPI终端,如可以是将User-Agent(用户代理)设置为WAPI-Mobile-ClientV1.0;Step 401: The terminal browser sends an HTTP GET request to the application server to obtain the page of the network storage application, and the terminal indicates that it is a WAPI terminal by setting a certain header field value of the request to a preset value, such as User-Agent (User Agent) is set to WAPI-Mobile-ClientV1.0;
该头域的值可以是终端在组建请求时指定,也可以通过和无线局域网段相邻的WAP/HTTP应用网关修改。The value of the header field can be specified by the terminal when forming the request, or can be modified by the WAP/HTTP application gateway adjacent to the wireless local area network segment.
步骤402:应用服务器收到终端发来的HTTP GET请求,根据其中某头域值判断此请求是否来自于WAPI终端;如根据User-Agent的值为WAPI-Mobile-Client V1.0时判定该终端是WAPI终端;Step 402: The application server receives the HTTP GET request sent by the terminal, and judges whether the request comes from a WAPI terminal according to one of the header field values; if the value of User-Agent is WAPI-Mobile-Client V1.0, the terminal is judged is a WAPI terminal;
步骤403:应用服务器向终端返回200OK消息,在该消息中增加一个隐藏表单,内容至少包含一个采用WAI公开密钥算法加密的数字签名,签名方法如下:Step 403: The application server returns a 200OK message to the terminal, and a hidden form is added to the message, the content of which contains at least one digital signature encrypted with the WAI public key algorithm, and the signature method is as follows:
(a)使用WAI散列算法计算返回的页面、即超文本格式字符串。(a) Use the WAI hash algorithm to calculate the returned page, that is, the hypertext format string.
(b)使用应用服务器WAPI证书的私钥,利用WAI的椭圆曲线算法,对散列计算结果做加密计算,生成签名。(b) Use the private key of the WAPI certificate of the application server and use the elliptic curve algorithm of WAI to perform encryption calculation on the hash calculation result to generate a signature.
生成的签名存入页面响应中的隐藏表单里下发给终端浏览器。The generated signature is stored in the hidden form in the page response and sent to the terminal browser.
步骤404:如图8所示,终端在收到200OK消息后,从隐藏表单中解析出数字签名,获取预存于终端上的应用服务器WAPI证书的公钥对签名进行公开密钥算法解密,并利用WAI的散列函数对网页内容进行散列计算,之后比较散列计算的结果与解密的数字签名是否一致,若一致则鉴别通过,否则鉴别未通过。Step 404: As shown in Figure 8, after receiving the 200OK message, the terminal parses the digital signature from the hidden form, obtains the public key of the WAPI certificate of the application server pre-stored on the terminal, decrypts the signature with a public key algorithm, and uses The hash function of WAI performs hash calculation on the content of the webpage, and then compares whether the hash calculation result is consistent with the decrypted digital signature. If they are consistent, the authentication passes, otherwise the authentication fails.
本发明中终端获得应用服务器WAPI证书的方法同现有技术。The method for the terminal to obtain the WAPI certificate of the application server in the present invention is the same as that of the prior art.
步骤405:WAPI终端浏览器在获取应用服务器网页数据并完成对服务器身份鉴别之后,呈现页面。Step 405: The WAPI terminal browser presents the page after obtaining the webpage data of the application server and completing the identity authentication of the server.
步骤406:终端通过界面指定要获取内容对应的URL(Uniform ResourceLocator,统一资源定位符),并使用GET方法获取内容。Step 406: The terminal specifies the URL (Uniform Resource Locator, Uniform Resource Locator) corresponding to the content to be obtained through the interface, and uses the GET method to obtain the content.
终端用户通过浏览器操作界面选择获取文件时,将通过GET方法完成,客户端插件调用WAI功能对统一资源定位符(URL,Uniform ResourceLocator)做签名计算,签名方法如下:When the end user chooses to obtain the file through the browser operation interface, it will be completed through the GET method. The client plug-in calls the WAI function to perform signature calculation on the Uniform Resource Locator (URL, Uniform ResourceLocator). The signature method is as follows:
(a)使用WAI散列算法计算URL;(a) calculate the URL using the WAI hashing algorithm;
(b)使用终端WAPI证书对应的私钥,利用WAI的椭圆曲线算法,对散列计算结果做加密计算,生成签名。(b) Use the private key corresponding to the terminal WAPI certificate, and use the elliptic curve algorithm of WAI to encrypt the hash calculation result to generate a signature.
URL签名和用户证书标识通过URL参数的方式提交给服务器,例如:The URL signature and user certificate identification are submitted to the server through URL parameters, for example:
http://upload-doc-server.com/document/20091117203?Url-sign=deFQWER3d&certid=2343....http://upload-doc-server.com/document/20091117203?Url-sign=deFQWER3d &certid=2343....
对统一资源定位符的数字签名不包括URL参数部分。A digital signature on a Uniform Resource Locator does not include the URL parameter portion.
步骤407:应用服务器收到HTTP GET消息,分离出URL参数中的用户证书标识,获取用户证书,之后使用终端WAPI证书中的公开密钥解密该数字签名,并利用WAI的散列函数对网页内容进行散列计算,之后比较散列计算的结果与解密的数字签名是否一致,若一致则通过对终端的鉴别,否则鉴别未通过。Step 407: The application server receives the HTTP GET message, separates the user certificate identifier in the URL parameter, obtains the user certificate, and then uses the public key in the terminal WAPI certificate to decrypt the digital signature, and uses the hash function of WAI to decrypt the webpage content Carry out the hash calculation, and then compare whether the result of the hash calculation is consistent with the decrypted digital signature. If they are consistent, the authentication of the terminal is passed; otherwise, the authentication fails.
如图6所示,应用服务器完成对终端的鉴别后,生成128位随机数作为临时会话密钥,并使用此临时会话密钥对客户端请求的文档内容做SMS4加密(即图6中所示的对文档进行对称密钥加密),并对文档正文做数字签名,数字签名的过程即先对文档正文作散列计算,之后使用应用服务器WAPI证书的私钥对散列计算后的值进行公开密钥算法加密;应用服务器还使用终端WAPI证书的公钥对临时会话密钥进行公开密钥算法加密得到加密后的密钥;最后,所有内容以固定格式封装或以表单形式,作为200OK消息体返回给终端。As shown in Figure 6, after the application server completes the authentication of the terminal, it generates a 128-bit random number as a temporary session key, and uses this temporary session key to encrypt the document content requested by the client with SMS4 (that is, as shown in Figure 6 Encrypt the document with a symmetric key), and digitally sign the text of the document. The process of digital signature is to hash the text of the document first, and then use the private key of the WAPI certificate of the application server to disclose the value after the hash calculation. Key algorithm encryption; the application server also uses the public key of the terminal WAPI certificate to perform public key algorithm encryption on the temporary session key to obtain the encrypted key; finally, all content is encapsulated in a fixed format or in a form, as a 200OK message body return to the terminal.
步骤408:如图7所示,终端收到200OK消息后,利用终端WAPI证书的私钥对加密的密钥进行公开密钥算法解密得出临时会话密钥,之后使用该临时会话密钥对密文进行对称密钥算法解密得到文档正文,并对解密出的正文进行散列计算得到散列值,还使用应用服务器WAPI证书的公钥对签名进行公开密钥算法解密得到另一散列值,比较得到的上述2个散列值是否一致,若一致则验证通过,且接收的文件内容未被更改,若不一致则验证未通过。Step 408: As shown in Figure 7, after receiving the 200OK message, the terminal uses the private key of the terminal WAPI certificate to decrypt the encrypted key with a public key algorithm to obtain a temporary session key, and then uses the temporary session key to encrypt The text is decrypted by the symmetric key algorithm to obtain the document text, and the decrypted text is hashed to obtain the hash value, and the signature is decrypted by the public key algorithm using the public key of the WAPI certificate of the application server to obtain another hash value. Compare whether the above two hash values obtained are consistent. If they are consistent, the verification is passed, and the content of the received file has not been changed. If they are inconsistent, the verification fails.
本发明中终端及应用服务器使用相同的公开密钥算法进行加密及解密。In the present invention, the terminal and the application server use the same public key algorithm for encryption and decryption.
本发明在不改动HTTP协议的基础上,通过HTTP消息体或者超文本中的表单,完成基于WAPI证书的鉴别过程,和传输数据的加密及完整性保护,对于应用服务器来说,不影响其WEB访问请求处理的正常流程,所提及功能可以通过新增功能模块完成,新增功能只涉及WAPI相关公钥及对称加密计算,未改动HTTP及超文本传输协议的内容。On the basis of not changing the HTTP protocol, the present invention completes the authentication process based on the WAPI certificate and the encryption and integrity protection of the transmitted data through the HTTP message body or the form in the hypertext, and does not affect its WEB for the application server. The normal flow of access request processing, the mentioned functions can be completed through the new function modules, the new functions only involve WAPI-related public keys and symmetric encryption calculations, and the content of HTTP and hypertext transfer protocol has not been changed.
Claims (16)
Priority Applications (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN200910247064ACN101742508A (en) | 2009-12-21 | 2009-12-21 | System and method for transferring files between WAPI terminal and application server |
| PCT/CN2010/075406WO2011076008A1 (en) | 2009-12-21 | 2010-07-22 | System and method for transmitting files between wapi teminal and application sever |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN200910247064ACN101742508A (en) | 2009-12-21 | 2009-12-21 | System and method for transferring files between WAPI terminal and application server |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN101742508Atrue CN101742508A (en) | 2010-06-16 |
Family
ID=42465224
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN200910247064APendingCN101742508A (en) | 2009-12-21 | 2009-12-21 | System and method for transferring files between WAPI terminal and application server |
Country Status (2)
| Country | Link |
|---|---|
| CN (1) | CN101742508A (en) |
| WO (1) | WO2011076008A1 (en) |
Cited By (22)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2011076008A1 (en)* | 2009-12-21 | 2011-06-30 | 中兴通讯股份有限公司 | System and method for transmitting files between wapi teminal and application sever |
| CN102868765A (en)* | 2012-10-09 | 2013-01-09 | 乐视网信息技术(北京)股份有限公司 | Method and system for uploading files |
| CN103220295A (en)* | 2013-04-26 | 2013-07-24 | 福建伊时代信息科技股份有限公司 | Document encryption and decryption method, device and system |
| CN103220159A (en)* | 2012-01-19 | 2013-07-24 | 北京千橡网景科技发展有限公司 | Method used for transferring information and device used for transferring information |
| CN103368901A (en)* | 2012-03-27 | 2013-10-23 | 复旦大学 | Cloud computing system based on large-scale discrete data |
| CN105227514A (en)* | 2014-05-27 | 2016-01-06 | 北大方正集团有限公司 | Based on document transmission processing method and the browser of browser |
| CN105825145A (en)* | 2016-03-16 | 2016-08-03 | 孙凤鸣 | Electronic evidence taking method, evidence taking server, evidence taking intelligent terminal and evidence taking system |
| CN105933124A (en)* | 2016-06-30 | 2016-09-07 | 武汉理工大学 | Digital signature and message hash value recovery method |
| CN106326394A (en)* | 2016-08-18 | 2017-01-11 | 乐视控股(北京)有限公司 | Method and device for obtaining file name |
| CN106790075A (en)* | 2016-12-21 | 2017-05-31 | 上海云熵网络科技有限公司 | For the Verification System and authentication method of UDP transmission |
| CN107920069A (en)* | 2017-11-15 | 2018-04-17 | 中国联合网络通信集团有限公司 | Application security processing method and processing device in ciphering terminal |
| CN108400979A (en)* | 2018-02-06 | 2018-08-14 | 武汉斗鱼网络科技有限公司 | Communication means and electronic equipment applied to client and server |
| CN108549701A (en)* | 2018-04-17 | 2018-09-18 | 上海海事大学 | Cloud environment encrypts outsourcing data semantic extended search method and system |
| CN109088889A (en)* | 2018-10-16 | 2018-12-25 | 深信服科技股份有限公司 | A kind of SSL encipher-decipher method, system and computer readable storage medium |
| CN109150516A (en)* | 2018-08-31 | 2019-01-04 | 密信技术(深圳)有限公司 | The signature and/or encryption method of browser file, device, browser and medium |
| CN109194631A (en)* | 2018-08-17 | 2019-01-11 | 郑州云海信息技术有限公司 | A kind of proof of identity method and relevant apparatus |
| CN109561124A (en)* | 2017-09-27 | 2019-04-02 | 深圳市创易联合科技有限公司 | A kind of method, system and the terminal device of file transmission |
| CN109672530A (en)* | 2019-01-08 | 2019-04-23 | 如般量子科技有限公司 | Anti- quantum calculation digital signature method and anti-quantum calculation digital signature system based on unsymmetrical key pond |
| CN109831311A (en)* | 2019-03-21 | 2019-05-31 | 深圳市网心科技有限公司 | A kind of server validation method, system, user terminal and readable storage medium storing program for executing |
| CN109889344A (en)* | 2019-01-31 | 2019-06-14 | 深圳中兴飞贷金融科技有限公司 | The transmission method and computer readable storage medium of terminal, data |
| CN110008727A (en)* | 2019-04-10 | 2019-07-12 | 鼎信信息科技有限责任公司 | Processing method, device, computer equipment and storage medium for encrypting sensitive parameters |
| CN114499871A (en)* | 2021-12-23 | 2022-05-13 | 成都卫士通信息产业股份有限公司 | Signature encryption method, device and system and computer readable storage medium |
Families Citing this family (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN102542405A (en)* | 2011-12-14 | 2012-07-04 | 金峰顺泰知识产权有限公司 | Digital archive storage and identification method and system |
| CN114760129B (en)* | 2022-04-11 | 2024-07-09 | 平安国际智慧城市科技股份有限公司 | Data access method, device, equipment and storage medium |
| CN118174966B (en)* | 2024-05-14 | 2024-08-13 | 北京格尔国信科技有限公司 | Ship key rotation method, device, equipment and storage medium |
Family Cites Families (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN100428753C (en)* | 2002-11-29 | 2008-10-22 | 英华达(上海)电子有限公司 | Method and system for implementing program update by using hypertext transfer protocol service |
| CN100369434C (en)* | 2006-07-31 | 2008-02-13 | 西安西电捷通无线网络通信有限公司 | Method of Realizing Virtual Local Area Network Based on WAPI System in Wireless Local Area Network |
| CN101466079A (en)* | 2009-01-12 | 2009-06-24 | 中兴通讯股份有限公司 | Method, system and WAPI terminal for transmitting e-mail |
| CN101742508A (en)* | 2009-12-21 | 2010-06-16 | 中兴通讯股份有限公司 | System and method for transferring files between WAPI terminal and application server |
- 2009
- 2009-12-21CNCN200910247064Apatent/CN101742508A/enactivePending
- 2010
- 2010-07-22WOPCT/CN2010/075406patent/WO2011076008A1/enactiveApplication Filing
Cited By (27)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2011076008A1 (en)* | 2009-12-21 | 2011-06-30 | 中兴通讯股份有限公司 | System and method for transmitting files between wapi teminal and application sever |
| CN103220159A (en)* | 2012-01-19 | 2013-07-24 | 北京千橡网景科技发展有限公司 | Method used for transferring information and device used for transferring information |
| CN103368901A (en)* | 2012-03-27 | 2013-10-23 | 复旦大学 | Cloud computing system based on large-scale discrete data |
| CN102868765A (en)* | 2012-10-09 | 2013-01-09 | 乐视网信息技术(北京)股份有限公司 | Method and system for uploading files |
| CN102868765B (en)* | 2012-10-09 | 2015-06-03 | 乐视网信息技术(北京)股份有限公司 | Method and system for uploading files |
| CN103220295A (en)* | 2013-04-26 | 2013-07-24 | 福建伊时代信息科技股份有限公司 | Document encryption and decryption method, device and system |
| CN105227514A (en)* | 2014-05-27 | 2016-01-06 | 北大方正集团有限公司 | Based on document transmission processing method and the browser of browser |
| CN105825145B (en)* | 2016-03-16 | 2018-08-31 | 孙凤鸣 | Electronic evidence-collecting method, evidence obtaining server, evidence obtaining intelligent terminal and evidence-obtaining system |
| CN105825145A (en)* | 2016-03-16 | 2016-08-03 | 孙凤鸣 | Electronic evidence taking method, evidence taking server, evidence taking intelligent terminal and evidence taking system |
| CN105933124A (en)* | 2016-06-30 | 2016-09-07 | 武汉理工大学 | Digital signature and message hash value recovery method |
| CN106326394A (en)* | 2016-08-18 | 2017-01-11 | 乐视控股(北京)有限公司 | Method and device for obtaining file name |
| CN106790075A (en)* | 2016-12-21 | 2017-05-31 | 上海云熵网络科技有限公司 | For the Verification System and authentication method of UDP transmission |
| CN109561124A (en)* | 2017-09-27 | 2019-04-02 | 深圳市创易联合科技有限公司 | A kind of method, system and the terminal device of file transmission |
| CN107920069A (en)* | 2017-11-15 | 2018-04-17 | 中国联合网络通信集团有限公司 | Application security processing method and processing device in ciphering terminal |
| CN108400979B (en)* | 2018-02-06 | 2021-07-30 | 武汉斗鱼网络科技有限公司 | Communication method applied to client and server and electronic equipment |
| CN108400979A (en)* | 2018-02-06 | 2018-08-14 | 武汉斗鱼网络科技有限公司 | Communication means and electronic equipment applied to client and server |
| CN108549701A (en)* | 2018-04-17 | 2018-09-18 | 上海海事大学 | Cloud environment encrypts outsourcing data semantic extended search method and system |
| CN109194631A (en)* | 2018-08-17 | 2019-01-11 | 郑州云海信息技术有限公司 | A kind of proof of identity method and relevant apparatus |
| CN109150516A (en)* | 2018-08-31 | 2019-01-04 | 密信技术(深圳)有限公司 | The signature and/or encryption method of browser file, device, browser and medium |
| CN109088889A (en)* | 2018-10-16 | 2018-12-25 | 深信服科技股份有限公司 | A kind of SSL encipher-decipher method, system and computer readable storage medium |
| CN109672530A (en)* | 2019-01-08 | 2019-04-23 | 如般量子科技有限公司 | Anti- quantum calculation digital signature method and anti-quantum calculation digital signature system based on unsymmetrical key pond |
| CN109889344A (en)* | 2019-01-31 | 2019-06-14 | 深圳中兴飞贷金融科技有限公司 | The transmission method and computer readable storage medium of terminal, data |
| CN109831311A (en)* | 2019-03-21 | 2019-05-31 | 深圳市网心科技有限公司 | A kind of server validation method, system, user terminal and readable storage medium storing program for executing |
| CN109831311B (en)* | 2019-03-21 | 2022-04-01 | 深圳市网心科技有限公司 | Server verification method, system, user terminal and readable storage medium |
| CN110008727A (en)* | 2019-04-10 | 2019-07-12 | 鼎信信息科技有限责任公司 | Processing method, device, computer equipment and storage medium for encrypting sensitive parameters |
| CN114499871A (en)* | 2021-12-23 | 2022-05-13 | 成都卫士通信息产业股份有限公司 | Signature encryption method, device and system and computer readable storage medium |
| CN114499871B (en)* | 2021-12-23 | 2024-01-09 | 成都卫士通信息产业股份有限公司 | Signature encryption method, device and system and computer readable storage medium |
Also Published As
| Publication number | Publication date |
|---|---|
| WO2011076008A1 (en) | 2011-06-30 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN101742508A (en) | System and method for transferring files between WAPI terminal and application server | |
| CN107317789B (en) | Key distribution, authentication method, device and system | |
| US10284555B2 (en) | User equipment credential system | |
| KR102134302B1 (en) | Wireless network access method and apparatus, and storage medium | |
| CN101183938B (en) | A wireless network security transmission method, system and device | |
| KR100832893B1 (en) | A method for the access of the mobile terminal to the WLAN and for the data communication via the wireless link securely | |
| KR102124413B1 (en) | System and method for identity based key management | |
| CN101459506B (en) | Cipher key negotiation method, system, customer terminal and server for cipher key negotiation | |
| US9668230B2 (en) | Security integration between a wireless and a wired network using a wireless gateway proxy | |
| US8769284B2 (en) | Securing communication | |
| CN102082796B (en) | Method for encrypting channels and simplified method and system for encrypting channels based on HTTP (hyper text transport protocol) | |
| CN101466079A (en) | Method, system and WAPI terminal for transmitting e-mail | |
| WO2017185999A1 (en) | Method, apparatus and system for encryption key distribution and authentication | |
| CN100579010C (en) | Key generation and transmission method and system | |
| WO2018045817A1 (en) | Mobile network authentication method, terminal device, server and network authentication entity | |
| CN112165386B (en) | Data encryption method and system based on ECDSA | |
| JP2001524777A (en) | Data connection security | |
| KR101706117B1 (en) | Apparatus and method for other portable terminal authentication in portable terminal | |
| US20080137859A1 (en) | Public key passing | |
| CN113382002B (en) | Data request method, request response method, data communication system, and storage medium | |
| CN113918971A (en) | Block chain based message transmission method, device, equipment and readable storage medium | |
| Leu et al. | Improving security level of LTE authentication and key agreement procedure | |
| WO2015104567A1 (en) | Secure communication between a server and a client web browser | |
| CN101483867A (en) | User identity verification method, related device and system in WAP service | |
| CN119449310B (en) | Equipment authentication method based on block chain access control |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| C06 | Publication | ||
| PB01 | Publication | ||
| C10 | Entry into substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| C02 | Deemed withdrawal of patent application after publication (patent law 2001) | ||
| WD01 | Invention patent application deemed withdrawn after publication | Application publication date:20100616 |