CN101599963A - Network suspected threat information filter and screening processing method - Google Patents
Network suspected threat information filter and screening processing methodDownload PDFInfo
- Publication number
- CN101599963A CN101599963ACNA2009100595514ACN200910059551ACN101599963ACN 101599963 ACN101599963 ACN 101599963ACN A2009100595514 ACNA2009100595514 ACN A2009100595514ACN 200910059551 ACN200910059551 ACN 200910059551ACN 101599963 ACN101599963 ACN 101599963A
- Authority
- CN
- China
- Prior art keywords
- module
- screening
- unit
- network
- packet
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
Images
Landscapes
- Data Exchanges In Wide-Area Networks (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明属于网络安全技术领域,特别是与入侵检测系统(IDS:Intrusion DetectionSystem)配套、对网络中所存在的疑似威胁信息进行筛选的筛选器及筛选处理方法,本发明筛选器及其筛选处理方法,可对拟进入检测系统的信息流首先进行筛选,将正常信息流筛选出、而仅将含有疑似威胁信息的数据包传送给入侵检测系统(IDS)进一步处理。The invention belongs to the technical field of network security, especially a filter and a screening processing method for screening suspected threat information existing in the network, which is matched with an intrusion detection system (IDS: Intrusion Detection System). , the information flow intended to enter the detection system can be screened first, the normal information flow can be screened out, and only the data packets containing suspected threat information can be sent to the intrusion detection system (IDS) for further processing.
背景技术Background technique
随着互联网的发展,网络安全越来越受到人们的重视。入侵检测系统(IDS)这种新的网络安全技术,被认为是防火墙之后的第二道安全门。IDS通过从计算机网络中的关键点收集信息,并对这些信息进行检测(如:协议解析、特征检测、异常检测等),从而发现网络或者系统中是否存在危害网络或系统安全的行为、病毒等,以便进行针对性处理、确保网络安全运行。常规IDS工作流程为:With the development of the Internet, people pay more and more attention to network security. Intrusion Detection System (IDS), a new network security technology, is considered to be the second security door behind the firewall. IDS collects information from key points in the computer network and detects the information (such as: protocol analysis, feature detection, anomaly detection, etc.), so as to find out whether there are behaviors and viruses that endanger network or system security in the network or system. , in order to carry out targeted processing and ensure the safe operation of the network. The general IDS workflow is:
1.从网络的不同关键点收集信息;1. Gather information from different key points of the network;
2.将该信息与行为特征库进行比对,分析信息是否含有恶意攻击行为;2. Compare the information with the behavior signature database, and analyze whether the information contains malicious attacks;
3.对检测到的行为做出响应;3. Respond to detected behavior;
4.记录并报告检测结果。4. Record and report the test results.
目前,随着网络容量的急速提升,千兆级入侵检测系统(IDS)已经成为其主流。在众多千兆级IDS系统的技术方案中,比较流行的是基于高性能CPU、网络处理器(NetworkProcessor,NP)以及与硬件加速器协同处理的架构等。其中,高性能CPU主要完成整个系统的控制,网络处理器(NP)用于网络协议处理、防火墙、QoS等,而硬件加速器一般采用ASIC(专用集成电路)或者FPGA(现场可编程门阵列)器件。上述基于硬件设备的IDS系统,虽然能较好地执行复杂度较高的程序(处理方法),但是这些高性能的千兆级IDS装置往往结构复杂、价格昂贵,难以在广大的中小用户中得到推广和普及。此外,针对上述基于硬件的IDS系统存在的缺陷,目前,在个人电脑等平台上也有采用纯软件来实现入侵检测的方法,如:开源的SNORT IDS等;这些软件IDS系统虽然具有运行费用低、且有很强的入侵检测能力,但由于此类IDS系统中软件抓包器的速率一般为每秒数十兆比特,因而,若将其应用在千兆级网络中则存在:一是运行中会直接漏检很多数据包,二是软件方式实现的模式匹配、使协议分析等处理速度极慢,最终导致整个系统性能低下等致命的缺陷。At present, with the rapid increase of network capacity, gigabit intrusion detection system (IDS) has become its mainstream. Among the technical solutions of many gigabit IDS systems, the more popular ones are based on high-performance CPUs, network processors (NetworkProcessor, NP), and architectures for co-processing with hardware accelerators. Among them, the high-performance CPU mainly completes the control of the entire system, the network processor (NP) is used for network protocol processing, firewall, QoS, etc., and the hardware accelerator generally uses ASIC (application specific integrated circuit) or FPGA (field programmable gate array) devices . Although the above-mentioned IDS systems based on hardware equipment can execute relatively high-complexity programs (processing methods), these high-performance gigabit-level IDS devices are often complex in structure and expensive, and are difficult to obtain in the vast number of small and medium-sized users. promotion and popularization. In addition, in view of the defects of the above-mentioned hardware-based IDS systems, at present, there are methods of using pure software to realize intrusion detection on platforms such as personal computers, such as: open source SNORT IDS, etc.; although these software IDS systems have low operating costs, And it has a strong intrusion detection capability, but because the rate of software packet grabbers in this type of IDS system is generally tens of megabits per second, if it is applied to a gigabit network, there will be: one is running Many data packets will be directly missed. Second, the pattern matching implemented by software makes the processing speed of protocol analysis extremely slow, which eventually leads to fatal flaws such as low performance of the entire system.
发明内容Contents of the invention
本发明的目的是针对背景技术存在的缺陷,研究设计一种可与入侵检测系统(IDS)配套使用的网络疑似威胁信息筛选器及筛选处理方法,以达到有效降低入侵检测系统的负担、提高其检测效率及检测系统的资源利用率,扩大对网络系统检测的覆盖面和检测范围,降低运行费用,确保网络安全运行等目的。The purpose of the present invention is to aim at the defects that the background technology exists, research and design a kind of network suspected threat information filter and screening processing method that can be used in conjunction with an intrusion detection system (IDS), to achieve effectively reducing the burden of the intrusion detection system and improving its performance. Detection efficiency and resource utilization of the detection system, expanding the coverage and scope of network system detection, reducing operating costs, and ensuring network security.
本发明的解决方案是通过对FPGA(现场可编程门阵列)内部逻辑资源的调配(置),制得由各功能模块架构组成的筛选器并采用相应的筛选方法(流程)、对网络内各交换设备输出的拟进入检测系统的信息流首先进行筛选,将大量的正常信息数据包筛选出、仅将含有疑似威胁信息的数据包传送给入侵检测系统(IDS)进一步进行针对性处理。筛选器采用数据聚合功能模块,包头及净荷分离功能模块,输出处理功能模块,预处理功能模块,以及网络层、传输层和应用层三级疑似威胁数据包筛选功能模块架构装置及所带或自设软硬件接口组成;其筛选方法在网络层、传输层及应用层功能模块通过对数据包的协议特征、内容逐一识别筛选,然后将筛选出的含有疑似威胁信息的数据包传送给入侵检测系统,从而实现其目的。因而,本发明筛选器包括带软硬件接口的现场可编程门阵列(FPGA)器件,关键在于在现场可编程门阵列器件内设有接收网络交换设备输出信息的数据聚合模块,包头及净荷分离模块,网络层疑似威胁数据包筛选模块,传输层疑似威胁数据包筛选模块,输出处理模块,含IP重组单元(模块)、TCP(传输控制协议)会话重组单元(模块)、应用层协议规范化单元(模块)的预处理模块,以及含规则头匹配单元、内容匹配单元、疑似威胁数据包输出单元的应用层疑似威胁数据包筛选模块;上述各(功能)模块中:数据聚合模块与包头及净荷分离模块,输出处理模块与预处理模块、预处理模块与应用层疑似威胁数据包筛选模块之间通过对应的输出、输入端依次连接,网络层疑似威胁数据包筛选模块与传输层疑似威胁数据包筛选模块则并联于包头及净荷分离模块与输出处理模块之间;输出处理模块、预处理模块通过TCP会话重组单元、应用层疑似威胁数据包筛选模块通过疑似威胁数据包输出单元分别与软硬件接口连接。The solution of the present invention is to make a filter made up of each functional module framework and adopt a corresponding screening method (flow process) by deploying (configuring) internal logic resources of FPGA (Field Programmable Gate Array). The information flow output by the switching device to enter the detection system is first screened out, and a large number of normal information packets are screened out, and only the data packets containing suspected threat information are sent to the intrusion detection system (IDS) for further targeted processing. The filter adopts a data aggregation function module, a packet header and payload separation function module, an output processing function module, a preprocessing function module, and three-level suspected threat data packet screening function modules of the network layer, the transport layer and the application layer. Self-configured software and hardware interfaces; the screening method identifies and screens the protocol characteristics and content of the data packets one by one in the network layer, transport layer and application layer functional modules, and then transmits the screened data packets containing suspected threat information to intrusion detection system to achieve its purpose. Thereby, filter of the present invention comprises the Field Programmable Gate Array (FPGA) device of band hardware and software interface, and key is to be provided with the data aggregation module that receives the output information of network switching equipment in Field Programmable Gate Array device, and packet header and payload separation Module, network layer suspected threat data packet screening module, transport layer suspected threat data packet screening module, output processing module, including IP reassembly unit (module), TCP (transmission control protocol) session reassembly unit (module), application layer protocol standardization unit (module) preprocessing module, and an application layer suspected threat data packet screening module including a rule header matching unit, a content matching unit, and a suspected threat data packet output unit; among the above-mentioned (function) modules: the data aggregation module and the header and net The load separation module, the output processing module and the preprocessing module, the preprocessing module and the application layer suspected threat data packet screening module are connected sequentially through the corresponding output and input terminals, the network layer suspected threat data packet screening module and the transport layer suspected threat data packet The packet screening module is connected in parallel between the packet header and payload separation module and the output processing module; the output processing module and the preprocessing module communicate with the software respectively through the TCP session reorganization unit, and the application layer suspected threat data packet screening module through the suspected threat data packet output unit. Hardware interface connection.
上述网络层疑似威胁数据包筛选模块包括IP疑似威胁信息筛选单元、ICMP疑似威胁信息筛选单元、输出单元。所述传输层疑似威胁数据包筛选模块包括TCP疑似威胁信息筛选单元及输出单元。The network layer suspected threat data packet screening module includes an IP suspected threat information screening unit, an ICMP suspected threat information screening unit, and an output unit. The transmission layer suspected threat data packet screening module includes a TCP suspected threat information screening unit and an output unit.
本发明网络疑似威胁信息筛选处理方法包括:The method for screening and processing suspected network threat information of the present invention includes:
步骤1.聚合处理:将网络中各交换设备输入数据聚合模块(1)的数据(信息)进行聚合处理;
步骤2.分离处理:将经步骤1聚合处理后输入包头及净荷分离模块(2)的数据进行IP包头、IP净荷及传输协议包头分离处理,并将IP包头和IP净荷与传输协议包头分别输入网络层疑似威胁数据包筛选模块(3)及传输层疑似威胁数据包筛选模块(4)、以便在网络层与传输层并行完成非规则攻击筛选;
步骤3.网络层疑似威胁数据包筛选:将经步骤2分离处理后进入网络层疑似威胁数据包筛选模块(3)的IP包头及IP净荷,按照网络层协议的规定对含疑似威胁信息的数据包进行筛选,并将筛选结果连同IP包头、IP净荷输入到输出处理模块(5);
步骤4.传输层疑似威胁数据包筛选:而经步骤2分离处理后进入传输层疑似威胁数据包筛选模块(4)的传输协议包头,则按传输层协议的规定对含非规则攻击的疑似威胁信息的包头进行筛选,并将筛选结果连同传输层协议包头亦输入到输出处理模块(5);
步骤5.输出处理:经步骤3、步骤4筛选后输入的筛选结果及其包头、净荷,若其中只要有一结果的结论为含疑似威胁信息,则将该数据包作为含非规则疑似威胁信息的数据包,经软硬件接口(8)送入侵检测系统(A);若所有结论均为正常(不含疑似威胁信息),则将该数据包作为正常数据包输入预处理模块(6);
步骤6.数据包预处理:将由步骤5输入的正常数据包通过IP重组单元(6.1)重组IP分片数据、通过TCP会话重组单元(6.2)经软硬件接口(8)从入侵检测系统索取TCP连接信息表后进行TCP会话重组,再经应用层数据规范化单元(6.3)对数据进行规范化处理,然后将处理后的IP包头和传输协议包头与应用层数据分别输入应用层疑似威胁数据包筛选模块中的规则头匹配单元以及内容匹配单元;
步骤7.应用层疑似威胁数据包筛选:将由步骤6输入的IP包头和传输协议包头经规则头匹配单元(7.1)进行规则头匹配处理,而输入的应用层数据经内容匹配单元(7.2)对常字符串及正则表达式进行匹配处理;然后将匹配处理后含疑似威胁信息的数据包由疑似威胁数据包输出单元(7.3)经软硬件接口(8)送入侵检测系统;否则,作丢弃处理。Step 7. Application layer suspected threat data packet screening: carry out the rule header matching process through the rule header matching unit (7.1) by the IP packet header and the transport protocol header imported in
上述,在步骤3中所述按照网络层协议的规定对含疑似威胁信息的数据包进行筛选,其网络层协议包括ICMP(控制报文协议)及IP协议。而在步骤4中所述按传输层协议的规定对含非规则攻击的疑似威胁信息的包头进行筛选,其传输层协议包括TCP(传输控制协议)。在步骤6中所述对应用层数据进行规范化处理,包括完成HTTP(超文本传输协议)协议的URL(统一资源定位符)规范化表达及统一编码方式,删除Telnet(TerminaLNETwork)协议中的协商数据。As mentioned above, in
本发明由于采用FPGA(现场可编程门阵列)器件,通过对其内部逻辑资源的配置,制得由各功能模块架构等组成的筛选器,并采用本发明筛选方法,对各网络交换设备输出的拟进入检测系统的信息首先进行筛选,将大量不含疑似威胁信息的正常信息数据包筛选出、仅将含有疑似威胁信息的数据包传送给入侵检测系统(IDS)进一步进行针对性处理,从而大幅度减少了进入检测系统的待检测信息的流量,有效降低了入侵检测系统的负担;在筛选处理过程中TCP会话重组单元直接通过软硬件接口从入侵检测系统索取TCP连接信息表,不但降低了硬件处理的难度、而且节约了硬件资源;此外,由于本发明方法是针对数据包为单位进行筛选,对以流量攻击为特征的信息流,由于攻击流中的各数据包均不含疑似威胁信息,在筛选过程中均作为不含疑似威胁信息的数据包被筛选出、而不会进入入侵检测系统。因而本发明具有筛选器设计紧凑、处理功能强,与入侵检测系统配套可大幅度降低入侵检测系统的负担,提高其检测效率及检测系统的资源利用率,扩大对网络系统检测的覆盖面和检测范围,降低运行费用,确保网络安全运行等特点。The present invention is owing to adopt FPGA (field programmable gate array) device, by the configuration of its internal logic resource, makes the screener that is made up of each functional module structure etc., and adopts screening method of the present invention, to each network switching equipment output The information to be entered into the detection system is screened first, and a large number of normal information packets without suspected threat information are screened out, and only the data packets containing suspected threat information are sent to the intrusion detection system (IDS) for further targeted processing, thereby greatly Significantly reduces the flow of information to be detected entering the detection system, effectively reducing the burden on the intrusion detection system; during the screening process, the TCP session reorganization unit directly obtains the TCP connection information table from the intrusion detection system through the software and hardware interface, which not only reduces the hardware The difficulty of processing, and saved hardware resources; In addition, because the inventive method is to screen for the unit of data packet, to the information flow that is characterized by traffic attack, since each data packet in the attack flow does not contain suspected threat information, During the screening process, all data packets that do not contain suspected threat information are screened out, and will not enter the intrusion detection system. Therefore, the present invention has a filter with compact design and strong processing functions, which can greatly reduce the burden of the intrusion detection system when matched with the intrusion detection system, improve its detection efficiency and the resource utilization rate of the detection system, and expand the coverage and detection range of network system detection , reduce operating costs, and ensure safe operation of the network.
附图说明Description of drawings
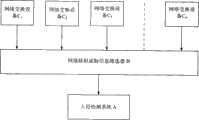
图1为本发明筛选器功能模块架构装置结构示意图(方框图);Fig. 1 is the structural schematic diagram (block diagram) of filter functional module architecture device of the present invention;
图2为本发明筛选处理方法流程示意图(方框图);Fig. 2 is a schematic flow chart (block diagram) of the screening treatment method of the present invention;
图3为本发明筛选器与网络设备及入侵检测系统(IDS)配套使用连接关系示意图。Fig. 3 is a schematic diagram of the connection relationship between the filter of the present invention, the network equipment and the intrusion detection system (IDS).
图中:1.数据聚合(功能)模块,2.IP包头及净荷分离模块,3.网络层疑似威胁数据包筛选模块,4.传输层疑似威胁数据包筛选模块,5.输出处理模块,6.预处理模块、6.1.IP重组单元(模块)、6.2.TCP会话重组单元(模块)、6.3.应用层协议规范化单元(模块),7.应用层疑似威胁数据包筛选模块、7.1.规则头匹配单元、7.2.内容匹配单元、7.3.疑似威胁数据包输出单元,8.软硬件接口;A.入侵检测系统,B.筛选器,C1~Cn:网络交换设备。In the figure: 1. data aggregation (function) module, 2. IP packet header and payload separation module, 3. network layer suspected threat data packet screening module, 4. transmission layer suspected threat data packet screening module, 5. output processing module, 6. Preprocessing module, 6.1. IP reassembly unit (module), 6.2. TCP session reassembly unit (module), 6.3. Application layer protocol normalization unit (module), 7. Application layer suspected threat packet screening module, 7.1. Rules Header matching unit, 7.2. Content matching unit, 7.3. Suspected threat data packet output unit, 8. Software and hardware interface; A. Intrusion detection system, B. Filter, C1 ~Cn: network switching equipment.
具体实施方式Detailed ways
本实施方式以与有10套网络交换设备(C1-10)及对应的入侵检测系统A配套使用为例:In this implementation mode, it is used with 10 sets of network switching devices (C1-10 ) and the corresponding intrusion detection system A as an example:
本实施方式中的筛选器B采用ALTERA公司生产的STRATIX III EP3SL150F型FPGA(现场可编程门阵列)器件作为筛选器本体,其中所设:数据聚合模块1资源配置1500个逻辑单元以及0.5兆比特RAM;包头及净荷分离模块2资源配置600个逻辑单元;网络层疑似威胁数据包筛选3资源配置为1500个逻辑单元;传输层疑似威胁数据包筛选模块4资源配置为1500个逻辑单元;处理输出模块5资源配置为150个逻辑单元;预处理模块6中:IP重组单元6.1资源配置为2000个逻辑单元以及5兆比特RAM,TCP会话重组单元6.2资源配置为2000个逻辑单元以及2.5兆比特RAM,应用层规范化单元6.3资源配置2500个逻辑单元;应用层疑似威胁数据包筛选模块7中:规则头匹配单元7.1资源配置为5000个逻辑单元,内容匹配单元7.2资源配置为25000个逻辑单元,疑似威胁数据包输出单元7.3资源配置为150个逻辑单元;本实施方式将软硬件接口8设于FPGA器件内、资源配置为1500个逻辑单元。上述各(功能)模块中:数据聚合模块1与包头及净荷分离模块2,输出处理模块5与预处理模块6、预处理模块6与应用层疑似威胁数据包筛选模块7之间的输出、输入端通过数据线依次连接,网络层疑似威胁数据包筛选模块3与传输层疑似威胁数据包筛选模块4则并联于包头及净荷分离模块2与输出处理模块5之间;输出处理模块5、预处理模块6通过TCP会话重组单元6.2、应用层疑似威胁数据包筛选模块7通过疑似威胁数据包输出单元7.3分别与软硬件接口连接。The filter B in the present embodiment adopts the STRATIX III EP3SL150F type FPGA (field programmable gate array) device produced by ALTERA Company as the filter body, wherein it is set:
本实施方式筛选器的筛选方法(流程):The screening method (flow process) of the filter of the present embodiment:
步骤1.聚合处理:首先通过数据聚合模块1将网络中各个交换设备输入的数据(信息)进行聚合处理,然后将聚合后的数据包发送到包头及净荷分离模块2;
步骤2.分离处理:包头及净荷分离模块2接收到聚合处理后的数据包后,首先从接收到的数据包中提取出协议类型字段并判断以太帧中封装的是否是IP数据包,如果不是,则将该数据包丢弃;如果是IP数据包,则根据IP协议以及传输层协议的相关规定,从IP数据包中分离出IP包头、IP净荷以及传输层包头,并将IP包头、IP净荷与传输层包头、IP包头分别发送到网络层疑似威胁数据包筛选模块3及传输层疑似威胁数据包筛选模块4,以并行进行网络层及传输层非规则攻击疑似威胁数据包的筛选;
步骤3.网络层疑似威胁数据包筛选:网络层疑似威胁数据包筛选模块3在接收到来自包头净荷分离模块2分离出的IP包头、净荷后,首先根据IP协议的规定,提取出IP头部中的协议类型字段、包总长度字段、分片标志字段以及选项字段,并将以上提取出的两部分数据分别送入ICMP疑似威胁数信息筛选单元以及IP疑似威胁信息筛选单元中,经两个单元并行运行处理,其中:ICMP疑似威胁信息筛选单元对疑似含ICMP洪范攻击信息、超长ICMP数据包攻击信息、ICMP数据包碎片攻击信息的数据包进行筛选并给出筛选结果,本实施方式该部分具体筛选流程为:若ICMP报文为回送请求或回答、封装ICMP报文的IP总包长超过预先设定的阈值、封装ICMP报文的IP分片标志位有效三种情况之一出现,则该数据包为含疑似威胁信息的数据包;与此同时,IP疑似威胁信息筛选单元对选项字段疑似非正常的数据包进行筛选并给出筛选结果,其具体筛选流程为:若IP包头的选项字段不为空,则该数据包含疑似威胁信息;两个单元筛选完成后,将筛选结果进行逻辑或并连同包头与净荷分离模块输入的IP包头、净荷一并送入输出处理模块;
步骤4.传输层疑似威胁数据包筛选:传输层疑似威胁数据包筛选模块4在接收到来自包头及净荷分离模块2送入的IP包头及传输层包头后,判断传输层协议是否是TCP协议,若是传输层协议,则首先根据TCP协议的规定,将TCP头部中的控制字段提取出并对含疑似SYN(同步序号)洪范攻击信息、端口扫描攻击信息、操作系统探查攻击信息的传输层包头进行筛选并给出筛选结果,其具体筛选方法为:只要TCP控制字段的SYN/FIN/RST(同步序号/终止连接/连接复位)位有效或未设TCP控制字段标志,则该包头为含疑似威胁信息的包头;筛选完成后,将筛选结果连同传输层包头一并经输出单元送入输出处理模块5;
步骤5.输出处理:经步骤3和步骤4筛选后同时送入输出处理模块6的筛选结果及其包头、净荷进行匹配处理,若其中只要有一结果的结论为含疑似威胁信息,则将该数据包作为含非规则疑似威胁信息的数据包,经软硬件接口8送入侵检测系统A;若所有结论均为正常(不含疑似威胁信息),则将该数据包作为正常数据包输入预处理模块6;
步骤6.数据包预处理:整个预处理流程由预处模块6中的IP分片重组单元6.1、TCP会话重组单元6.2、应用层规范化单元6.3完成;当IP分片重组单元6.1将由步骤5输入的正常数据包,通过提取IP包头的标志字段,如果分片标志字段无效,则直接将数据包送入TCP会话重组单元6.2;若分片标志字段有效时,则继续查看目前的分片重装表里是否已有重组该数据包IP净荷的表项;如果表项不存在则创建一个新的表项并存入IP包头和IP净荷,否则根据IP包头的偏移字段装入到已有表项中存储IP净荷的指定位置;然后查看该数据包的IP净荷是否为最后一个分片,如果是、则重组完成,将IP净荷和IP包头送入到TCP会话重组模块;否则查看该表项的计时器,如果计时器超时则直接将该表项中部分重组的IP净荷和IP数据包发送到TCP会话重组单元6.2;
步骤6.2.TCP会话重组:TCP会话重组单元6.2接收到IP分片重组单元6.1的IP包头和重组后的IP净荷后,判断其传输层协议是否为TCP协议,如果不是TCP协议,则直接送入到应用层规范化单元6.3;否则,根据IP包头和重组后的IP净荷里的IP源目地址、源目端口号查看目前的会话重组表里是否已有重组该TCP净荷的表项,本实施方式的会话重组表是采用通过软硬件接口从入侵检测系统索取的TCP连接信息建立的,并实时更新;如果表项不存在则将IP包头、TCP包头、TCP净荷(其中,TCP包头和TCP净荷即为重组后的IP净荷)直接送入应用层规范化模块,否则将TCP净荷存入到已有表项中存储TCP净荷的指定位置;然后再查看重组后的TCP净荷是否达到了规定的长度(或者已完成重组),如果是、则将IP包头、TCP包头、重组后的TCP净荷送入应用层规范化单元6.3;Step 6.2.TCP session reorganization: TCP session reorganization unit 6.2 after receiving the IP header of IP fragmentation reorganization unit 6.1 and the IP payload after reorganization, judges whether its transport layer protocol is TCP agreement, if not TCP agreement, then directly send Enter application layer standardization unit 6.3; Otherwise, according to the IP source-destination address and source-destination port number in the IP packet header and the reorganized IP payload, check whether there is an entry for reorganizing the TCP payload in the current session reorganization table, The session reorganization table of the present embodiment adopts the TCP connection information that obtains from the intrusion detection system through the hardware and software interface to set up, and updates in real time; and the TCP payload is the reassembled IP payload) directly into the application layer normalization module, otherwise the TCP payload will be stored in the specified location where the TCP payload is stored in the existing entry; and then check the reassembled TCP payload Whether the load has reached the specified length (or has completed the reorganization), if so, the TCP payload after the IP header, the TCP header, and the reorganization is sent to the application layer normalization unit 6.3;
步骤6.3.应用层数据规范化处理:应用层规范化单元6.3接收到TCP会话重组后的IP包头、传输层包头以及重组后的净荷后,首先判断应用层协议是否包含HTTP协议以或Telnet协议;若包含HTTP协议则将HTTP协议URL地址的编码方式统一为ASCII编码方式;若包含Telnet协议,则将Telnet会话流中的冗余协商信息删除;完成规范化处理后,将IP包头、传输层包头以与应用层数据分别送入应用层疑似威胁数据包筛选模块7;Step 6.3. Application layer data normalization processing: After the application layer normalization unit 6.3 receives the IP header after the TCP session reorganization, the transport layer header and the reorganized payload, it first judges whether the application layer protocol includes the HTTP protocol or the Telnet protocol; if If the HTTP protocol is included, the encoding method of the URL address of the HTTP protocol will be unified to the ASCII encoding method; if the Telnet protocol is included, the redundant negotiation information in the Telnet session flow will be deleted; The application layer data are respectively sent to the application layer suspected threat data packet screening module 7;
步骤7.应用层疑似威胁数据包筛选:应用层疑似威胁数据包筛选由规则头匹配单元7.1、内容匹配单元7.2、疑似威胁数据包输出单元7.3进行,其具体流程为:Step 7. Application layer suspected threat data packet screening: Application layer suspected threat data packet screening is carried out by rule header matching unit 7.1, content matching unit 7.2, suspected threat data packet output unit 7.3, and its specific process is:
步骤7.1.规则头匹配处理:规则头匹配单元7.1将IP包头和传输层协议包头中的源目IP地址、源目端口号、传输层和网络层的协议类型与规则库中规则的规则头进行匹配,其中:由于规则头中的源目IP地址采用前缀表达,因此直接采用三态内容可寻址存储器的方式进行与IP包头中的源目IP地址的匹配,而规则头中的端口号一般采用范围的方式表达(如:60-80),因而采用二叉决策树方法完成匹配处理;在规则头匹配完成后,将匹配结果连同包头一并送入疑似威胁数据包输出单元7.3;Step 7.1. Rule header matching processing: Rule header matching unit 7.1 performs a rule header with the source and destination IP address in the IP header and the transport layer protocol header, the source and destination port number, the protocol type of the transport layer and the network layer, and the rule in the rule base Matching, where: since the source and destination IP addresses in the rule header are expressed by a prefix, the tri-state content addressable memory is directly used to match the source and destination IP addresses in the IP packet header, and the port number in the rule header is generally Expressed in the form of range (such as: 60-80), thus adopting the binary decision tree method to complete the matching process; after the rule header matching is completed, the matching result is sent to the suspected threat data packet output unit 7.3 together with the packet header;
步骤7.2.内容匹配处理:对送入内容匹配单元7.2内的应用层数据进行常字符串和正则表达式的匹配,其中:应用层数据与规则库中的常字符串的匹配采用非确定状态机的方式进行;而正则表达式的匹配则分三步完成:其一、共享所有正则表达式相同的前缀、中缀、后缀;其二、基于第一步得到的前缀、中缀、后缀共享结构,通过非确定状态机的方式生成匹配电路;其三、对正则表达式中的常字符串和复杂运算符再进行优化处理;匹配完成后,将匹配结果连同应用层数据一并输入到疑似威胁数据包输出单元7.3;若任一匹配结果为含疑似威胁信息数据包,疑似威胁数据包输出单元7.3则将该数据包经软硬件接口8发送到入侵检测系统A;否则,将该数据包直接丢弃。Step 7.2. Content matching processing: match the constant character strings and regular expressions on the application layer data sent into the content matching unit 7.2, wherein: the matching between the application layer data and the constant character strings in the rule base uses a non-deterministic state machine The matching of regular expressions is done in three steps: first, share the same prefix, infix, and suffix of all regular expressions; second, share the structure based on the prefix, infix, and suffix obtained in the first step , generate a matching circuit through a non-deterministic state machine; third, optimize the constant strings and complex operators in the regular expression; after the matching is completed, input the matching result together with the application layer data to the suspected threat Data packet output unit 7.3; If any matching result contains the suspected threat information data packet, the suspected threat data packet output unit 7.3 sends the data packet to the intrusion detection system A through the software and
本实施方式试运行中:网络交换设备(C1-10)为S2403TP-EA型交换机及SRW208型交换机,总共10台;每个交换机的镜像端口速率为1Gbps(吉比特每秒);入侵检测系统A为SNORT IDS(SNORT为开发源代码的入侵检测系统);In the trial operation of this embodiment: the network switching devices (C1-10 ) are S2403TP-EA switches and SRW208 switches, a total of 10; the mirror port rate of each switch is 1Gbps (gigabits per second); the intrusion detection system A is SNORT IDS (SNORT is an intrusion detection system that develops source code);
本实施方式筛选器B与各网络交换设备(C1-10)及入侵检测系统A连接用网卡芯片采用Marvell公司生产的88E1111,该芯片支持1000兆的网络连接,总共11个;In this embodiment, the network card chip used to connect the filter B to each network switching device (C1-10 ) and the intrusion detection system A adopts the 88E1111 produced by Marvell, and the chip supports a network connection of 1000 megabytes, and there are 11 in total;
运行中,若每套网络交换设备C输入的拟进入入侵检测系统A的流量为1Gbps,10套设备的流量共计10Gbps,本实施方式筛选器将其中95~98%的不含疑似威胁信息的正常数据包筛选出,而只有≤5%(即≤500Mbps)的含疑似威胁信息的数据包进入入侵检测系统A;从而大幅度降低了入侵检测系统A的负荷。During operation, if the traffic input by each network switching device C to enter the intrusion detection system A is 1Gbps, and the total traffic of 10 sets of devices is 10Gbps, the filter in this embodiment filters 95-98% of the normal traffic without suspected threat information. The data packets are screened out, and only ≤5% (ie ≤500 Mbps) data packets containing suspected threat information enter the intrusion detection system A; thereby greatly reducing the load of the intrusion detection system A.
Claims (7)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN2009100595514ACN101599963B (en) | 2009-06-10 | 2009-06-10 | Suspected network threat information screener and screening and processing method |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN2009100595514ACN101599963B (en) | 2009-06-10 | 2009-06-10 | Suspected network threat information screener and screening and processing method |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN101599963Atrue CN101599963A (en) | 2009-12-09 |
| CN101599963B CN101599963B (en) | 2012-07-04 |
Family
ID=41421210
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN2009100595514AExpired - Fee RelatedCN101599963B (en) | 2009-06-10 | 2009-06-10 | Suspected network threat information screener and screening and processing method |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN101599963B (en) |
Cited By (15)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN101964751A (en)* | 2010-09-30 | 2011-02-02 | 华为技术有限公司 | Transmission method and device of data packets |
| CN102098289A (en)* | 2010-12-17 | 2011-06-15 | 天津曙光计算机产业有限公司 | Network security accessing and sealing method based on FPGA (field programmable gate array) |
| CN102906756A (en)* | 2010-05-25 | 2013-01-30 | 惠普发展公司,有限责任合伙企业 | Security Threat Detection Associated with Security Event and Actor Classification Models |
| CN103455376A (en)* | 2012-06-20 | 2013-12-18 | 微软公司 | Managing use of a field programmable gate array by multiple processes in an operating system |
| CN103647708A (en)* | 2013-11-29 | 2014-03-19 | 曙光信息产业(北京)有限公司 | ATCA-based data message processing board |
| CN104219242A (en)* | 2014-09-09 | 2014-12-17 | 天津大学 | Hardware-based network data packet filtering structure |
| CN105103496A (en)* | 2013-03-14 | 2015-11-25 | 菲德利斯网络安全有限公司 | System and method for extracting and storing metadata for analyzing network communications |
| CN106301992A (en)* | 2015-06-12 | 2017-01-04 | 阿里巴巴集团控股有限公司 | A kind of attack message detection method and equipment |
| CN106789695A (en)* | 2016-11-24 | 2017-05-31 | 杭州迪普科技股份有限公司 | Message processing method and device |
| CN106961414A (en)* | 2016-01-12 | 2017-07-18 | 阿里巴巴集团控股有限公司 | A kind of data processing method based on honey jar, apparatus and system |
| CN108206826A (en)* | 2017-11-29 | 2018-06-26 | 华东师范大学 | A kind of lightweight intrusion detection method towards Integrated Electronic System |
| CN108650274A (en)* | 2018-05-21 | 2018-10-12 | 中国科学院计算机网络信息中心 | A kind of network inbreak detection method and system |
| CN111414402A (en)* | 2020-03-19 | 2020-07-14 | 北京神州绿盟信息安全科技股份有限公司 | Log threat analysis rule generation method and device |
| CN117009961A (en)* | 2023-09-28 | 2023-11-07 | 北京安天网络安全技术有限公司 | Method, device, equipment and medium for determining behavior detection rule |
| CN117118717A (en)* | 2023-09-01 | 2023-11-24 | 湖北顺安伟业科技有限公司 | User information threat analysis method and system |
Families Citing this family (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN109753518A (en)* | 2018-12-28 | 2019-05-14 | 成都九洲电子信息系统股份有限公司 | The data depth threat detection system and method for rule-based data |
Family Cites Families (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN1435977A (en)* | 2002-02-01 | 2003-08-13 | 联想(北京)有限公司 | Method for detecting and responding of fire wall invasion |
| EP1738531B1 (en)* | 2004-04-19 | 2014-06-11 | The Regents of the University of California | Deep Packet Filter and Respective Method |
| KR101206542B1 (en)* | 2006-12-18 | 2012-11-30 | 주식회사 엘지씨엔에스 | Apparatus and method of securing network of supporting detection and interception of dynamic attack based hardware |
- 2009
- 2009-06-10CNCN2009100595514Apatent/CN101599963B/ennot_activeExpired - Fee Related
Cited By (22)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN102906756A (en)* | 2010-05-25 | 2013-01-30 | 惠普发展公司,有限责任合伙企业 | Security Threat Detection Associated with Security Event and Actor Classification Models |
| CN101964751B (en)* | 2010-09-30 | 2013-01-16 | 华为技术有限公司 | Transmission method and device of data packets |
| CN101964751A (en)* | 2010-09-30 | 2011-02-02 | 华为技术有限公司 | Transmission method and device of data packets |
| CN102098289A (en)* | 2010-12-17 | 2011-06-15 | 天津曙光计算机产业有限公司 | Network security accessing and sealing method based on FPGA (field programmable gate array) |
| CN102098289B (en)* | 2010-12-17 | 2014-08-27 | 曙光信息产业股份有限公司 | Network security accessing and sealing method based on FPGA (field programmable gate array) |
| CN103455376A (en)* | 2012-06-20 | 2013-12-18 | 微软公司 | Managing use of a field programmable gate array by multiple processes in an operating system |
| CN105103496A (en)* | 2013-03-14 | 2015-11-25 | 菲德利斯网络安全有限公司 | System and method for extracting and storing metadata for analyzing network communications |
| CN103647708A (en)* | 2013-11-29 | 2014-03-19 | 曙光信息产业(北京)有限公司 | ATCA-based data message processing board |
| CN104219242A (en)* | 2014-09-09 | 2014-12-17 | 天津大学 | Hardware-based network data packet filtering structure |
| CN106301992B (en)* | 2015-06-12 | 2019-09-03 | 阿里巴巴集团控股有限公司 | A kind of attack message detection method and equipment |
| CN106301992A (en)* | 2015-06-12 | 2017-01-04 | 阿里巴巴集团控股有限公司 | A kind of attack message detection method and equipment |
| CN106961414A (en)* | 2016-01-12 | 2017-07-18 | 阿里巴巴集团控股有限公司 | A kind of data processing method based on honey jar, apparatus and system |
| CN106789695A (en)* | 2016-11-24 | 2017-05-31 | 杭州迪普科技股份有限公司 | Message processing method and device |
| CN106789695B (en)* | 2016-11-24 | 2020-04-03 | 杭州迪普科技股份有限公司 | Message processing method and device |
| CN108206826A (en)* | 2017-11-29 | 2018-06-26 | 华东师范大学 | A kind of lightweight intrusion detection method towards Integrated Electronic System |
| CN108206826B (en)* | 2017-11-29 | 2020-07-14 | 华东师范大学 | A Lightweight Intrusion Detection Method for Integrated Electronic Systems |
| CN108650274A (en)* | 2018-05-21 | 2018-10-12 | 中国科学院计算机网络信息中心 | A kind of network inbreak detection method and system |
| CN111414402A (en)* | 2020-03-19 | 2020-07-14 | 北京神州绿盟信息安全科技股份有限公司 | Log threat analysis rule generation method and device |
| CN117118717A (en)* | 2023-09-01 | 2023-11-24 | 湖北顺安伟业科技有限公司 | User information threat analysis method and system |
| CN117118717B (en)* | 2023-09-01 | 2024-05-31 | 湖北顺安伟业科技有限公司 | User information threat analysis method and system |
| CN117009961A (en)* | 2023-09-28 | 2023-11-07 | 北京安天网络安全技术有限公司 | Method, device, equipment and medium for determining behavior detection rule |
| CN117009961B (en)* | 2023-09-28 | 2023-12-08 | 北京安天网络安全技术有限公司 | Method, device, equipment and medium for determining behavior detection rule |
Also Published As
| Publication number | Publication date |
|---|---|
| CN101599963B (en) | 2012-07-04 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN101599963A (en) | Network suspected threat information filter and screening processing method | |
| CN101789931B (en) | Network intrusion detection system and method based on data mining | |
| US8065722B2 (en) | Semantically-aware network intrusion signature generator | |
| CN104539594B (en) | SDN architecture, system and working method integrating DDoS threat filtering and routing optimization | |
| US12218937B2 (en) | Packet processing method and apparatus, device, and computer-readable storage medium | |
| CN100558089C (en) | A Realization Method of Content Filtering Gateway Based on Network Filter | |
| US8149705B2 (en) | Packet communications unit | |
| CN104767752A (en) | Distributed network isolating system and method | |
| CN109936578A (en) | A detection method for HTTPS tunnel traffic in the network | |
| CN100542176C (en) | Method and system for analyzing and processing data packet content | |
| CN107968785A (en) | A kind of method of defending DDoS (Distributed Denial of Service) attacks in SDN data centers | |
| CN104539625A (en) | Network security defense system based on software definition and working method thereof | |
| CN101217547B (en) | A flood request attaching filtering method based on the stateless open source core | |
| WO2008061483A1 (en) | A method and apparatus for identifying the data content | |
| CN107222491A (en) | A kind of inbreak detection rule creation method based on industrial control network mutation attacks | |
| CN102387151A (en) | Block-based virus detection method in P2P (peer-to-peer) network | |
| CN113518042B (en) | Data processing method, device, equipment and storage medium | |
| CN110417729A (en) | Service and application classification method and system for encrypted traffic | |
| CN107666486A (en) | A kind of network data flow restoration methods and system based on message protocol feature | |
| CN111245866B (en) | Ethernet application layer protocol control system and method based on hardware acceleration | |
| CN108229159A (en) | A kind of malicious code detecting method and system | |
| CN110912887B (en) | A Bro-based APT monitoring system and method | |
| De Bruijn et al. | Safecard: a gigabit ips on the network card | |
| CN107864110A (en) | Botnet main control end detection method and device | |
| CN113347184A (en) | Method, device, equipment and medium for testing network flow security detection engine |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| C06 | Publication | ||
| PB01 | Publication | ||
| C10 | Entry into substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| C14 | Grant of patent or utility model | ||
| GR01 | Patent grant | ||
| CF01 | Termination of patent right due to non-payment of annual fee | Granted publication date:20120704 Termination date:20150610 | |
| EXPY | Termination of patent right or utility model |