CN101582769A - Authority setting method of user access network and equipment - Google Patents
Authority setting method of user access network and equipmentDownload PDFInfo
- Publication number
- CN101582769A CN101582769ACNA2009101487926ACN200910148792ACN101582769ACN 101582769 ACN101582769 ACN 101582769ACN A2009101487926 ACNA2009101487926 ACN A2009101487926ACN 200910148792 ACN200910148792 ACN 200910148792ACN 101582769 ACN101582769 ACN 101582769A
- Authority
- CN
- China
- Prior art keywords
- network
- access
- user
- user account
- network insertion
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/60—Context-dependent security
- H04W12/63—Location-dependent; Proximity-dependent
- H04W12/64—Location-dependent; Proximity-dependent using geofenced areas
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W4/00—Services specially adapted for wireless communication networks; Facilities therefor
- H04W4/02—Services making use of location information
- H04W4/021—Services related to particular areas, e.g. point of interest [POI] services, venue services or geofences
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明涉及通信技术领域,特别涉及一种用户接入网络的权限设置方法和设备。The invention relates to the field of communication technology, in particular to a method and device for setting permissions for users to access a network.
背景技术Background technique
随着网络应用的不断普及与发展,网络安全逐渐成为各企业极为重视的问题。其中,如何对用户进行接入控制是至关重要的问题,允许合法的用户使用网络并对其进行正确的认证、授权是对用户进行网络接入控制的最基本要求。远端拨入验证服务(Remote Access Dial In user Services,RADIUS)协议是控制网络用户接入的标准协议,基于客户端/服务器(Client/Server,C/S)模式。用户在接入网络之前必须先经过认证、授权与计费(AuthenticationAuthorization Accounting,AAA)服务器的认证,保证只有通过认证的合法用户才能访问网络。With the continuous popularization and development of network applications, network security has gradually become an issue that enterprises attach great importance to. Among them, how to control user access is a crucial issue. Allowing legal users to use the network and performing correct authentication and authorization are the most basic requirements for network access control of users. The Remote Access Dial In user Services (RADIUS) protocol is a standard protocol for controlling network user access, based on the client/server (Client/Server, C/S) model. Users must be authenticated by the Authentication Authorization Accounting (AAA) server before accessing the network to ensure that only authenticated legal users can access the network.
在网络身份认证的基础之上,网络准入控制(Network Admission Control,NAC)技术方案的提出,对接入网络的用户终端提出了更为严格的安全要求。网络准入控制方案是一个整合方案,其基本部件包括安全客户端、安全联动设备、安全策略服务器以及防病毒服务器、补丁服务器等第三方服务器。方案中的各部件各司其职,由安全策略中心协调与整合各功能部件,共同完成对网络接入终端的安全状态评估、隔离与修复,提升网络的整体防御能力。On the basis of network identity authentication, the proposal of the Network Admission Control (NAC) technical solution puts forward stricter security requirements for user terminals accessing the network. The network access control solution is an integrated solution, and its basic components include security clients, security linkage devices, security policy servers, and third-party servers such as antivirus servers and patch servers. Each component in the solution performs its own duties, and the security policy center coordinates and integrates various functional components to jointly complete the security status assessment, isolation and repair of network access terminals, and improve the overall defense capability of the network.
个人计算机(Personal Computer,PC)的台式机和便携计算机以及其他可以进行网络接入的设备统称为终端,网络接入控制应用系统的客户端软件都运行在各个终端上,网络准入控制方案要求对通过身份认证的用户进行终端的安全认证,根据网络管理员定制的安全策略进行安全检查,例如:病毒库更新情况、系统补丁安装情况、软件的黑白名单、U盘外设使用情况等等。根据检查的结果,网络准入控制方案对用户网络准入进行授权和控制。通过安全认证后,用户可以正常使用网络,与此同时,网络准入控制方案可以对用户终端运行情况和网络使用情况进行审计和监控。Personal Computer (Personal Computer, PC) desktop and portable computers and other devices that can access the network are collectively referred to as terminals. The client software of the network access control application system runs on each terminal. The network access control scheme requires Perform terminal security authentication for authenticated users, and perform security checks according to the security policies customized by the network administrator, such as: virus database update, system patch installation, software black and white lists, U disk peripheral usage, etc. According to the inspection result, the network access control scheme authorizes and controls the user's network access. After passing the security authentication, users can use the network normally. At the same time, the network access control scheme can audit and monitor the operation of user terminals and network usage.
如图1所示,是一个用户接入网络的技术方案的典型组网图。As shown in FIG. 1 , it is a typical networking diagram of a technical solution for user access to a network.
企业在引入网络接入控制技术方案时,往往在各个机构、部门按照相关的信息安全政策制定不同的安全控制策略等。但是随着跨部门运作与办公协同的发展,往往存在着对“漫游用户”(网络接入用户从一个位置移动到另一个位置,仍能正常使用网络即漫游)的网络接入认证和权限控制问题。When enterprises introduce network access control technology solutions, they often formulate different security control strategies in various institutions and departments in accordance with relevant information security policies. However, with the development of cross-departmental operations and office collaboration, there are often network access authentication and authority control for "roaming users" (network access users move from one location to another, and can still use the network normally, that is, roaming). question.
如图2所示,企业由于职能而划分为不同的行政区域,而每个行政区域因为信息安全的需要而配置不同的网络安全控制策略。在实际工作中,往往存在跨部门工作交流问题,例如图2中,某市场部员工携带笔记本电脑到研发部进行工作交流,则可能存在如下问题:As shown in Figure 2, enterprises are divided into different administrative regions due to their functions, and each administrative region configures different network security control strategies because of the needs of information security. In actual work, there are often cross-department work communication problems. For example, in Figure 2, an employee in the marketing department carries a laptop to the R&D department for work communication, and the following problems may exist:
1、如果该员工使用其接入用户名无法接入研发部网络(接入系统未授权接入研发区域),则该员工无法使用当前的网络资源;1. If the employee cannot access the R&D department network with his access user name (the access system is not authorized to access the R&D area), the employee cannot use the current network resources;
2、如果该员工可接入研发区域,且使用研发区既定的网络安全控制策略,可访问研发区域的资源,则可能造成研发信息泄漏。2. If the employee can access the R&D area and use the established network security control strategy of the R&D area to access the resources of the R&D area, it may cause R&D information leakage.
为解决漫游用户的接入问题,企业往往采用“多用户名、多域名”的方式来区别用户漫游到不同接入区域。用户在不同的接入区域使用不同的用户名或者域名进行网络接入认证,认证接入服务器根据用户名、域名来识别不同的安全控制策略并授予用户不同的访问权限。例如“ABC”是接入市场部网络的用户名,“ABC@research”(用户名+域名方式)是接入研发区网络的用户名,“ABC.bj”是接入北京办事处的用户名。这样该用户每次漫游到不同的区域均使用不同的用户接入帐号进行网络接入认证。In order to solve the access problem of roaming users, enterprises often adopt the method of "multiple user names and multiple domain names" to distinguish users roaming to different access areas. Users use different user names or domain names for network access authentication in different access areas, and the authentication access server identifies different security control policies based on user names and domain names and grants users different access rights. For example, "ABC" is the username for accessing the network of the marketing department, "ABC@research" (username + domain name) is the username for accessing the R&D area network, and "ABC.bj" is the username for accessing the Beijing Office . In this way, each time the user roams to a different area, a different user access account is used for network access authentication.
在实现本发明的过程中,申请人发现现有技术至少存在以下问题:In the process of realizing the present invention, the applicant finds that the prior art has at least the following problems:
1、漫游用户需要记忆各种不同的接入帐号,每次接入到不同的区域均要进行接入帐号的切换工作;1. Roaming users need to memorize various access accounts, and each time they access to a different area, they must switch access accounts;
2、若漫游用户在某接入区域未配置接入帐号和权限,需要请求网管人员为其分配接入帐号和访问权限;2. If the roaming user has not configured an access account and access authority in a certain access area, it is necessary to request the network administrator to assign an access account and access authority;
3、大量的帐号管理配置和访问权限分配给网管人员带来大量重复工作;3. A large number of account management configurations and access rights assignments bring a lot of repetitive work to network administrators;
4、无法对帐号的生命周期进行有效控制,例如某员工离职,其所在部门的帐号虽然也同时注销,但是系统中其漫游帐号仍然存在,给企业网络带来后门隐患;4. It is impossible to effectively control the life cycle of the account. For example, when an employee resigns, although the account of his department is also canceled at the same time, his roaming account still exists in the system, which brings backdoor hidden dangers to the enterprise network;
5、各行政区域缺乏对漫游用户的安全访问权限进行统一管理,难免因为安全访问权限配置的不同,而造成某些漫游用户可访问未授权的网络资源。5. There is a lack of unified management of the security access rights of roaming users in various administrative regions. It is inevitable that some roaming users may access unauthorized network resources due to different configurations of security access rights.
发明内容Contents of the invention
本发明提供一种用户接入网络的权限设置方法和设备,使用户通过单一帐号进行网络认证接入,并可以根据该用户的接入位置分配相应的网络访问权限。The invention provides a method and device for setting user access rights to the network, enabling the user to perform network authentication and access through a single account, and assign corresponding network access rights according to the user's access location.
为达到上述目的,本发明一方面提供了一种用户接入网络的权限设置方法,应用于包括网络认证服务器和多个网络接入区域的网络系统中,其中,每个所述网络接入区域分别包括一个接入设备和至少一个用户终端,所述网络系统中建立至少一个用户账户,所述用户账户对应一个用户名,所述方法包括:To achieve the above object, the present invention provides a method for setting user access rights to a network, which is applied to a network system including a network authentication server and a plurality of network access areas, wherein each of the network access areas An access device and at least one user terminal are respectively included, at least one user account is established in the network system, and the user account corresponds to a user name, and the method includes:
所述网络认证服务器分别为每个所述网络接入区域建立至少一种资源访问权限;The network authentication server respectively establishes at least one resource access right for each of the network access areas;
所述网络认证服务器分别设置所述用户账户在每个所述网络接入区域中所对应的资源访问权限;The network authentication server respectively sets the resource access rights corresponding to the user accounts in each of the network access areas;
所述网络认证服务器保存所述用户账户的用户名在每个网络接入区域中的资源访问权限与所述网络接入区域的位置识别信息的对应关系信息。The network authentication server saves the correspondence relationship information between the resource access authority of the user name of the user account in each network access area and the location identification information of the network access area.
优选的,所述网络接入区域的位置识别信息,具体为:Preferably, the location identification information of the network access area is specifically:
所述网络接入区域的接入设备的IP地址;或,the IP address of the access device in the network access area; or,
所述网络接入区域中的用户终端的IP地址。The IP address of the user terminal in the network access area.
优选的,如果所述网络接入区域的位置识别信息具体为所述网络接入区域中的用户终端的IP地址,所述方法还包括:Preferably, if the location identification information of the network access area is specifically the IP address of the user terminal in the network access area, the method further includes:
所述多个网络接入区域分别对应多个IP地址区间;The multiple network access areas respectively correspond to multiple IP address ranges;
所述网络接入区域中所包括的用户终端的IP地址处于所述网络接入区域所对应的IP地址区间中。The IP addresses of the user terminals included in the network access area are in the IP address range corresponding to the network access area.
优选的,当有用户账户请求访问资源时,所述方法还包括:Preferably, when a user account requests access to resources, the method further includes:
所述网络认证服务器接收所述接入设备发送的包含所述用户账户的用户名、密码和所述用户账户当前所处的网络接入区域的位置识别信息的认证请求消息;The network authentication server receives an authentication request message sent by the access device that includes the username and password of the user account and the location identification information of the network access area where the user account is currently located;
所述网络认证服务器对所述用户账户的用户名和密码的匹配关系进行认证,并获取所述用户账户的用户名在所述网络接入区域的位置识别信息所对应的网络接入区域中所对应的资源访问权限。The network authentication server authenticates the matching relationship between the user name of the user account and the password, and obtains the corresponding information of the user name of the user account in the network access area corresponding to the location identification information of the network access area. resource access permissions.
优选的,所述方法还包括:Preferably, the method also includes:
如果对所述用户账户的用户名和密码的匹配关系进行认证成功,所述网络认证服务器向所述接入设备发送所述用户账户的认证确认信息,为所述用户账户分配资源访问权限;If the matching relationship between the user name and the password of the user account is successfully authenticated, the network authentication server sends authentication confirmation information of the user account to the access device, and assigns resource access rights to the user account;
如果对所述用户账户的用户名和密码的匹配关系进行认证失败,或所述网络认证服务器获取所述用户账户的用户名在所述网络接入区域的位置识别信息所对应的网络接入区域中所对应的资源访问权限失败,所述网络认证服务器向所述接入设备发送认证失败消息,拒绝所述用户账户进行资源访问。If the authentication of the matching relationship between the user name and password of the user account fails, or the network authentication server obtains that the user name of the user account is in the network access area corresponding to the location identification information of the network access area If the corresponding resource access authority fails, the network authentication server sends an authentication failure message to the access device, rejecting resource access by the user account.
另一方面,本发明还提供了一种网络认证服务器,应用于包括网络认证服务器和多个网络接入区域的网络系统中,其中,每个所述网络接入区域分别包括一个接入设备和至少一个用户终端,所述网络系统中建立至少一个用户账户,所述用户账户对应一个用户名,包括:On the other hand, the present invention also provides a network authentication server, which is applied in a network system including the network authentication server and multiple network access areas, wherein each network access area includes an access device and At least one user terminal, at least one user account is established in the network system, and the user account corresponds to a user name, including:
设置模块,用于为每个所述网络接入区域建立至少一种资源访问权限,并分别设置所述用户账户在每个所述网络接入区域中所对应的资源访问权限;A setting module, configured to establish at least one resource access right for each of the network access areas, and respectively set the resource access rights corresponding to the user accounts in each of the network access areas;
存储模块,与所述设置模块电性连接,用于存储所述用户账户的用户名在每个网络接入区域中的资源访问权限与所述网络接入区域的位置识别信息的对应关系信息;A storage module, electrically connected to the setting module, for storing the correspondence relationship information between the resource access authority of the user name of the user account in each network access area and the location identification information of the network access area;
通信模块,与所述存储模块电性连接,用于接收所述接入设备发送的包含所述用户账户的用户名、密码和所述用户账户当前所处的网络接入区域的位置识别信息的认证请求消息,并根据认证结果向所述接入设备发送所述用户名的认证确认信息或认证失败消息,以及在用户名认证成功的情况下,向接入设备发送所述用户的资源访问权限;A communication module, electrically connected to the storage module, configured to receive the information sent by the access device, including the user name and password of the user account, and the location identification information of the network access area where the user account is currently located an authentication request message, and send the authentication confirmation information or authentication failure message of the user name to the access device according to the authentication result, and send the user's resource access right to the access device if the user name authentication is successful ;
认证模块,与所述存储模块和所述通信模块电性连接,用于根据所述存储模块所存储的访问权限信息与所述用户名在网络接入区域的对应关系,对所述用户名在所述网络接入区域进行认证。An authentication module, electrically connected to the storage module and the communication module, configured to verify the user name in the network access area according to the corresponding relationship between the access authority information stored in the storage module and the user name in the network access area The network access area is authenticated.
优选的,所述用户名所对应的用户账户当前所处的网络接入区域的位置识别信息,具体为:Preferably, the location identification information of the network access area where the user account corresponding to the user name is currently located is specifically:
所述网络接入区域的接入设备的IP地址;或,the IP address of the access device in the network access area; or,
所述网络接入区域中的用户终端的IP地址。The IP address of the user terminal in the network access area.
优选的,如果所述网络接入区域的位置识别信息具体为所述网络接入区域中的用户终端的IP地址,具体还包括:Preferably, if the location identification information of the network access area is specifically the IP address of the user terminal in the network access area, it specifically further includes:
所述多个网络接入区域分别对应多个IP地址区间;The multiple network access areas respectively correspond to multiple IP address intervals;
所述网络接入区域中所包括的至少一个用户终端的IP地址处于所述网络接入区域所对应的IP地址区间中。The IP address of at least one user terminal included in the network access area is in the IP address range corresponding to the network access area.
优选的,所述认证模块对用户账户在网络接入区域的认证,具体为:Preferably, the authentication module authenticates the user account in the network access area, specifically:
如果所述认证模块对用户账户的用户名和密码的匹配关系进行认证成功,所述网络认证服务器向所述接入设备发送所述用户账户的认证确认信息,并根据访问权限信息与所述用户名在网络接入区域的对应关系,为所述用户账户分配资源访问权限;If the authentication module successfully authenticates the matching relationship between the user name and password of the user account, the network authentication server sends the authentication confirmation information of the user account to the access device, and In the corresponding relationship of the network access area, assign resource access rights to the user account;
如果所述认证模块对所述用户账户的用户名和密码的匹配关系进行认证失败,或所述网络认证服务器获取所述用户账户的用户名在所述网络接入区域的位置识别信息所对应的网络接入区域中所对应的资源访问权限失败,所述网络认证服务器向所述接入设备发送认证失败消息,拒绝所述用户账户进行资源访问。If the authentication module fails to authenticate the matching relationship between the username and password of the user account, or the network authentication server obtains the network address corresponding to the location identification information of the username of the user account in the network access area If the corresponding resource access authority in the access area fails, the network authentication server sends an authentication failure message to the access device, rejecting resource access by the user account.
与现有技术相比,本发明具有以下优点:Compared with the prior art, the present invention has the following advantages:
通过本发明,实现了基于用户的实际接入位置进行访问权限分配,可以避免由于接入区域变更而访问权限不可控,并可以对于各接入区域的非固定工作人员采用统一的访问权限控制,而单一账号进行访问的方式也为用户的使用提供了便利,在提高网络安全性的同时,改善了用户体验。Through the present invention, the distribution of access rights based on the actual access location of the user is realized, which can avoid uncontrollable access rights due to changes in access areas, and can adopt unified access rights control for non-fixed staff in each access area, The way of accessing with a single account also provides convenience for users, and improves user experience while improving network security.
附图说明Description of drawings
图1为现有技术中的网络接入控制技术方案的组网结构示意图;FIG. 1 is a schematic diagram of a network structure of a network access control technical solution in the prior art;
图2为现有技术中的企业分区域组网结构示意图;FIG. 2 is a schematic diagram of an enterprise sub-area networking structure in the prior art;
图3为本发明提供的一种用户接入网络的权限设置方法的流程示意图;FIG. 3 is a schematic flow diagram of a method for setting a user access network authority provided by the present invention;
图4为本发明提供的一种根据用户接入网络的权限设置进行权限认证的流程示意图;FIG. 4 is a schematic flow diagram of authorization authentication according to the authorization settings of users accessing the network provided by the present invention;
图5为本发明提供的一种802.1x认证的典型组网结构示意图;Fig. 5 is a schematic diagram of a typical networking structure of 802.1x authentication provided by the present invention;
图6为本发明提供的一种应用于802.1x认证的典型组网结构中的RADIUS认证过程的流程示意图;Fig. 6 is a schematic flow chart of a RADIUS authentication process applied to a typical networking structure of 802.1x authentication provided by the present invention;
图7为本发明提供的一种网络认证服务器的结构示意图。FIG. 7 is a schematic structural diagram of a network authentication server provided by the present invention.
具体实施方式Detailed ways
如背景技术所述,现有的网络接入控制机制一方面无法对于在不同区域之间进行漫游的用户的访问权限进行有效控制,增加了网络资源安全隐患,另一方面,也不能对用户的访问权限信息进行有效的统一管理,增加了网络管理的工作量,同时,也给用户在不同区域之间的网络资源访问带来了不便,影响了用户体验。As mentioned in the background technology, on the one hand, the existing network access control mechanism cannot effectively control the access rights of users roaming between different areas, which increases the security risks of network resources; The effective unified management of access rights information increases the workload of network management. At the same time, it also brings inconvenience to users' access to network resources between different regions and affects user experience.
所以,本发明希望通过用户实际接入网络的区域范围对用户的访问权限进行区别设定。Therefore, the present invention hopes to set the user's access rights differently according to the area in which the user actually accesses the network.
为达到上述目的,本发明提供了一种用户接入网络的权限设置方法,应用于包括网络认证服务器和多个网络接入区域的网络系统中,其中,每个网络接入区域分别包括一个接入设备和至少一个用户终端,该网络系统中建立至少一个用户账户,该用户账户对应一个用户名。To achieve the above object, the present invention provides a method for setting user access rights to the network, which is applied to a network system including a network authentication server and multiple network access areas, wherein each network access area includes an access An access device and at least one user terminal, at least one user account is established in the network system, and the user account corresponds to a user name.
如图3所示,该方法具体包括以下步骤:As shown in Figure 3, the method specifically includes the following steps:
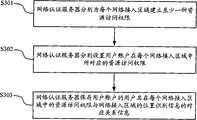
步骤S301、网络认证服务器分别为每个网络接入区域建立至少一种资源访问权限。Step S301, the network authentication server establishes at least one resource access right for each network access area.
通过本步骤,可以根据需要,为网络接入区域设置多层次的访问权限规则,对不同的用户账户进行资源访问时的资源访问范围进行控制。Through this step, multi-level access authority rules can be set for the network access area as required, so as to control the scope of resource access when different user accounts perform resource access.
步骤S302、网络认证服务器分别设置用户账户在每个网络接入区域中所对应的资源访问权限。Step S302, the network authentication server respectively sets resource access rights corresponding to user accounts in each network access area.
设置同一个用户名在不同的网络接入区域中对应的资源访问权限,实现同一个用户账户在不同的网络接入区域中可以通过同一个用户名进行资源访问。Set resource access permissions corresponding to the same user name in different network access areas, so that the same user account can access resources through the same user name in different network access areas.
这些信息可以根据用户账户的具体属性或者访问规则具体设定。This information can be specifically set according to specific attributes of the user account or access rules.
步骤S303、网络认证服务器保存用户账户的用户名在每个网络接入区域中的资源访问权限与网络接入区域的位置识别信息的对应关系信息。Step S303 , the network authentication server saves the correspondence relationship information between the resource access authority of the username of the user account in each network access area and the location identification information of the network access area.
其中,网络接入区域的位置识别信息具体包括两种情况:Among them, the location identification information of the network access area specifically includes two situations:
情况一、网络接入区域的接入设备的IP地址。Case 1: The IP address of the access device in the network access area.
这种情况下,网络接入区域的接入设备直接被作为该网络区域中唯一的认征点。In this case, the access device in the network access area is directly used as the only authentication point in the network area.
网络认证服务器并不在意用户账户是在该网络接入区域中的哪一台接入终端中进行资源访问,因此,用户账户进行资源访问时,只需要告知网络认证服务器当前所处的是哪一个网络接入区域即可,而该网络接入区域的接入设备的IP地址可以实现这样的效果。The network authentication server does not care which access terminal the user account is in the network access area for resource access. Therefore, when the user account accesses resources, it only needs to inform the network authentication server which terminal it is currently in. The network access area is sufficient, and the IP address of the access device in the network access area can achieve this effect.
在实际的应用场景中,上述的接入设备通常是指接入层交换机,而相应的网络接入区域的位置识别信息除了接入层交换机的IP地址信息之外,还可以包括用户请求接入的端口信息,这样的变化并不影响本发明的保护范围。In actual application scenarios, the above-mentioned access device usually refers to an access layer switch, and the location identification information of the corresponding network access area may include, in addition to the IP address information of the access layer switch, user requests to access port information, such changes do not affect the protection scope of the present invention.
这种情况多出现在802.1x认证的组网结构中。This situation often occurs in the networking structure of 802.1x authentication.
情况二、网络接入区域中的用户终端的IP地址。Case 2: the IP address of the user terminal in the network access area.
这种情况下是将接入终端的位置信息作为网络接入区域的标识,这样设置的前提是网络认证服务器存储有全部接入终端的位置信息和该接入终端所处的网络接入区域的对应关系,或者,接入终端的位置信息(IP地址)设置具有一定的规律性,比如,每个网络接入区域对应一定的IP地址范围,该网络接入区域中的所有接入终端的IP地址,都出与上述的IP地址范围之内。In this case, the location information of the access terminal is used as the identifier of the network access area. The premise of this setting is that the network authentication server stores the location information of all access terminals and the ID of the network access area where the access terminal is located. Correspondence, or, the location information (IP address) setting of the access terminal has a certain regularity, for example, each network access area corresponds to a certain range of IP addresses, and the IP addresses of all access terminals in the network access area The addresses are all out of the above IP address range.
在此种情况下,虽然是将接入终端的IP地址作为位置识别信息,但是,网络认证服务器只是通过接入终端的IP地址找到对应的IP地址范围,从而确定相对应的网络接入区域,因此,与情况一相类似的,网络认证服务器并不在意用户账户是在该网络接入区域中的哪一台接入终端中进行资源访问,而只是需要定位用户账户所处的网络接入区域。In this case, although the IP address of the access terminal is used as the location identification information, the network authentication server only finds the corresponding IP address range through the IP address of the access terminal, thereby determining the corresponding network access area, Therefore, similar to case 1, the network authentication server does not care which access terminal in the network access area the user account is in for resource access, but only needs to locate the network access area where the user account is located .
这种情况多出现在Portal认证的组网结构中。This situation often occurs in the networking structure of Portal authentication.
上述两种情况的具体信息内容虽然不同,但通过上述信息所最终获取的目的信息是一致的,因此,在具体应用场景中,只要能够实现网络接入区域的定位,具体应用上述那种信息,并不影响本发明的保护范围。Although the specific information content of the above two cases is different, the purpose information finally obtained through the above information is consistent. Therefore, in a specific application scenario, as long as the positioning of the network access area can be realized, the above information can be specifically applied. Does not affect the protection scope of the present invention.
同时,上述的接入设备和接入终端的IP地址只是本发明的优选实施例,其他能够达到相同技术效果的信息内容,也应属于本发明的保护范围。At the same time, the above-mentioned IP addresses of the access device and the access terminal are only preferred embodiments of the present invention, and other information content that can achieve the same technical effect should also belong to the protection scope of the present invention.
在上述的权限设置过程完成后,如果出现用户账户请求进行资源访问的情况,则首先根据上述的权限设置对该用户账户进行权限认证,该认证过程如图4所示,具体包括以下步骤:After the above permission setting process is completed, if a user account requests resource access, first perform permission authentication on the user account according to the above permission setting. The authentication process is shown in Figure 4, and specifically includes the following steps:
步骤S401、网络认证服务器接收接入设备发送的包含用户账户的用户名、密码和用户账户当前所处的网络接入区域的位置识别信息的认证请求消息。Step S401 , the network authentication server receives an authentication request message sent by the access device, which includes the username and password of the user account and the location identification information of the network access area where the user account is currently located.
其中,根据网络接入区域的位置识别信息的具体内容,对应上述的两种情况进行详细说明:Among them, according to the specific content of the location identification information in the network access area, the above two situations will be described in detail:
情况一、用户账户当前所处的网络接入区域的接入设备的IP地址。Case 1: The IP address of the access device in the network access area where the user account is currently located.
在这种情况中,用户通过一个用户账户的用户名在某个网络接入区域中的任意一台用户终端中请求认证,该请求所对应的认证请求消息都会以接入设备的IP地址为当前网络接入区域的唯一标识,向网络认证服务器请求用户在当前网络接入区域中相应的权限认证。In this case, the user requests authentication in any user terminal in a certain network access area through the user name of a user account, and the authentication request message corresponding to the request will use the IP address of the access device as the current The unique identifier of the network access area, and requests the network authentication server for the user's corresponding authority authentication in the current network access area.
情况二、用户名所对应的用户进行认证的用户终端的IP地址。Case 2: the IP address of the user terminal for authentication of the user corresponding to the user name.
在这种情况下,如果用户通过某个网络接入区域中的任意一台用户终端请求认证时,在相应的认证请求消息中携带该用户终端的IP地址,由于先前设定的IP地址处于当前网路接入区域所对应的IP地址区间中,所以,当携带有该用户终端的IP地址的认证请求消息发送给网络认证服务器时,网络认证服务器可以直接根据用户终端的IP地址确定其所处的IP地址区间,从而确定对应的网络接入区域,从而完成对用户所处区域位置的确定,并进而确定相应的访问权限。In this case, if the user requests authentication through any user terminal in a certain network access area, the IP address of the user terminal is carried in the corresponding authentication request message. Since the previously set IP address is in the current Therefore, when the authentication request message carrying the IP address of the user terminal is sent to the network authentication server, the network authentication server can directly determine the location of the user terminal according to the IP address of the user terminal. IP address range, so as to determine the corresponding network access area, so as to complete the determination of the location of the user's area, and then determine the corresponding access rights.
步骤S402、网络认证服务器对用户账户的用户名和密码的匹配关系进行认证,并获取用户账户的用户名在网络接入区域的位置识别信息所对应的网络接入区域中所对应的资源访问权限。Step S402, the network authentication server authenticates the matching relationship between the username and password of the user account, and obtains the resource access authority corresponding to the username of the user account in the network access area corresponding to the location identification information of the network access area.
在本步骤中,网络认证服务器首先对用户名和密码的匹配关系进行确认,判断该用户名是否合法,如果该用户名和密码不对应,即判断该用户名不合法,从而,无需进一步判断用户当前所处的网络接入区域,而直接拒绝该用户名的访问请求。当然,在具体的应用场景中,也可以将用户名合法性认证和权限认证同时进行,只是,如果用户名合法性认证失败,即使权限认证已经完成,也不再返回权限认证的结果。In this step, the network authentication server first confirms the matching relationship between the user name and the password, and judges whether the user name is legal. If the user name and the password do not correspond, it judges that the user name is illegal. The network access area where the user is located, and directly rejects the access request of the user name. Of course, in a specific application scenario, user name authentication and authority authentication can also be performed at the same time, but if the user name authentication fails, even if the authority authentication has been completed, the authority authentication result will not be returned.
相反,如果该用户名和密码对应,即判断该用户名合法,继续进行后续步骤,由于用户名和密码的匹配关系的判断并不是本发明所关注的重点,因此,不再另行说明。On the contrary, if the user name corresponds to the password, it is judged that the user name is legal, and the subsequent steps are continued. Since the judgment of the matching relationship between the user name and the password is not the focus of the present invention, it will not be further explained.
在本步骤中,网络认证服务器明确了两点信息:In this step, the network authentication server specifies two pieces of information:
1、用户名是否合法。1. Whether the user name is legal.
如果不合法,则直接拒绝用户的认证请求,如果合法,则开始进行用户所处的网络接入区域的识别或者确认用户所处的网络接入区域的识别有效。If it is not legal, the authentication request of the user is directly rejected; if it is legal, the identification of the network access area where the user is located is started or the identification of the network access area where the user is located is confirmed to be valid.
2、用户所处的网络接入区域的识别。2. Identification of the network access area where the user is located.
通过上述的接入设备的IP地址或用户终端的IP地址所处的IP地址区间确定用户所出的网络接入区域。The network access area from which the user exits is determined by the IP address of the above access device or the IP address range of the IP address of the user terminal.
在上述两点信息明确后,网络认证服务器根据用户名和网络接入区域信息直接确定该用户名在此网络接入区域中的访问权限信息。After the above two points of information are clarified, the network authentication server directly determines the access right information of the user name in the network access area according to the user name and the information of the network access area.
具体的访问权限信息是在前述的权限设置流程中,由管理员在网络认证服务器中提前统一设定的,对于具体的用户名,在多个网络接入区域中可以分别具有不同的访问权限,例如:用户在本身部门所属的网络接入区域中具有不受限的访问权限,可以不受限的访问所有的网络资源,而在其他部门所属的网络接入区域中具有受限的访问权限,用户只能访问部分网络资源,或者完全不能访问当前的网络资源。The specific access rights information is uniformly set in advance by the administrator in the network authentication server in the aforementioned rights setting process. For specific user names, different access rights can be obtained in multiple network access areas. For example: a user has unlimited access rights in the network access area of his own department, and can access all network resources without restriction, but has restricted access rights in the network access areas of other departments. Users can only access some network resources, or cannot access current network resources at all.
在具体的应用场景中,还可以设置缺省权限定义,当用户账户的用户名在某个网络接入区域中没有设定相应的访问权限,即该用户名在某个网络接入区域中的访问权限缺省时,网络认证服务器可以根据缺省权限定义,判定该用户名在此网络接入区域中不具有资源访问权限,因此,不能访问当前网络接入区域中的网络资源。In specific application scenarios, you can also set the default permission definition. When the user name of the user account does not set the corresponding access permission in a certain network access area, that is, the user name in a certain network access area When the access authority is defaulted, the network authentication server can determine that the user name does not have resource access authority in this network access area according to the default authority definition, and therefore cannot access the network resources in the current network access area.
这样的缺省权限定义是出于网络资源安全的考虑,当然,在实际应用中,也可以设定缺省权限定义为受限的资源访问权限,即只能访问部分网络资源,这些资源是公开资源,不会危害企业信息安全,这样的变化同样属于本发明的保护范围。Such default permissions are defined for the security of network resources. Of course, in practical applications, the default permissions can also be defined as limited resource access permissions, that is, only part of the network resources can be accessed, and these resources are public resources. Resources will not endanger enterprise information security, and such changes also belong to the scope of protection of the present invention.
相应的,根据上述的网络认证服务器对用户账户的用户名和密码的匹配关系进行认证的结果,后续步骤也存在相应的区别,具体如下:Correspondingly, according to the above-mentioned result of the network authentication server authenticating the matching relationship between the username and password of the user account, there are corresponding differences in the subsequent steps, as follows:
如果对用户账户的用户名和密码的匹配关系进行认证成功,则执行步骤S403;If the matching relationship between the user name and the password of the user account is authenticated successfully, step S403 is executed;
如果对用户账户的用户名和密码的匹配关系进行认证失败,则执行步骤S404。If the authentication of the matching relationship between the user name and the password of the user account fails, step S404 is executed.
步骤S403、网络认证服务器向接入设备发送用户账户的认证确认信息,为用户账户分配资源访问权限。Step S403, the network authentication server sends authentication confirmation information of the user account to the access device, and assigns resource access rights to the user account.
步骤S404、网络认证服务器向接入设备发送认证失败消息,拒绝用户账户进行资源访问。Step S404, the network authentication server sends an authentication failure message to the access device, rejecting resource access by the user account.
本步骤对应的是用户账户的用户名和密码的匹配关系进行认证失败的情况,在实际的应用场景中,网络认证服务器获取用户账户的用户名在网络接入区域的位置识别信息所对应的网络接入区域中所对应的的资源访问权限失败也可以导致本步骤的发生,即查不到资源访问权限信息或不能查资源访问权限信息则认为权限认证失败,当然,也可以根据上述的缺省权限定义进行处理,这样的变化并不影响本发明的保护范围。This step corresponds to the situation where the matching relationship between the user name and password of the user account fails to authenticate. The failure of the corresponding resource access authority in the entry area can also lead to this step. That is, if the resource access authority information cannot be found or the resource access authority information cannot be found, it is considered that the authority authentication has failed. Of course, it can also be based on the above default authority. Definitions, such changes do not affect the protection scope of the present invention.
通过本发明,实现了基于用户的实际接入位置进行访问权限分配,可以避免由于接入区域变更而访问权限不可控,并可以对于各接入区域的非固定工作人员采用统一的访问权限控制,而单一账号进行访问的方式也为用户的使用提供了便利,在提高网络安全性的同时,改善了用户体验。Through the present invention, the distribution of access rights based on the actual access location of the user is realized, which can avoid uncontrollable access rights due to changes in access areas, and can adopt unified access rights control for non-fixed staff in each access area, The way of accessing with a single account also provides convenience for users, and improves user experience while improving network security.
通过上述说明可以看出,本发明所提出的技术方案的基本思路如下:As can be seen from the above description, the basic idea of the technical solution proposed by the present invention is as follows:
根据接入用户的用户属性在各个网络接入区域中分配相应的访问权限;Allocate corresponding access rights in each network access area according to the user attributes of the access users;
网络认证服务器根据用户当前所处的网络接入区域识别该用户相应的访问权限,并为其分配相应的网络资源。The network authentication server identifies the corresponding access rights of the user according to the network access area where the user is currently located, and allocates corresponding network resources for the user.
在具体的实施场景中,上述的用户属性可以是该用户的工作职能,各个网络接入区域可以是企业内具体的行政区域,网络接入区域的具体识别依据可以是接入设备IP或者接入终端IP地址,当然,根据实际的需要,上述各项内容也可以发生相应的变化,这样的变化同样属于本发明的保护范围。In a specific implementation scenario, the above-mentioned user attributes may be the job function of the user, each network access area may be a specific administrative area within the enterprise, and the specific identification basis of the network access area may be the access device IP or access The IP address of the terminal, of course, according to actual needs, the above items can also be changed accordingly, and such changes also belong to the protection scope of the present invention.
下面结合具体的实施场景阐述本发明所提出的技术方案的实现思路。The implementation idea of the technical solution proposed by the present invention will be described below in conjunction with specific implementation scenarios.
企业网实现认证接入主要有802.1x和Portal两种方式。这两种组网方式在本方案的实现方式上略有不同,但实现思路上基本相同。两者之间具体的差别在于:There are mainly two methods for enterprise network to realize authentication access: 802.1x and Portal. These two networking methods are slightly different in the implementation of this solution, but the implementation ideas are basically the same. The specific differences between the two are:
在802.1x系统中,网络接入区域的具体识别依据是接入设备的IP地址,例如接入层交换机的IP地址。In the 802.1x system, the specific basis for identifying the network access area is the IP address of the access device, such as the IP address of the access layer switch.
而在Portal系统中,网络接入区域的具体识别依据是接入终端的IP地址,例如用户用来进行网络访问的用户终端的IP地址。In the Portal system, the specific basis for identifying the network access area is the IP address of the access terminal, for example, the IP address of the user terminal used by the user for network access.
为了避免具体叙述文字的重复,本发明的后续说明中将以802.1x认证组网方式描述本发明的技术实现过程。In order to avoid repetition of specific descriptions, the technical implementation process of the present invention will be described in the form of 802.1x authentication networking in the subsequent description of the present invention.
为了方便说明,本发明还给出了具体的组网模型,如图5所示,是一种802.1x认证的典型组网图,每个接入终端将接入交换机作为认证点。For the convenience of description, the present invention also provides a specific networking model, as shown in Figure 5, which is a typical networking diagram of 802.1x authentication, and each access terminal uses an access switch as an authentication point.
由于接入层交换机的网络特性,因此每个行政区域均拥有独立的一台及多台接入设备。根据企业实际的情况,可将各行政区域内的接入设备的IP地址作为识别接入区域的信息,RADIUS服务器可根据认证报文的接入设备的IP地址识别接入用户是从什么区域接入网络。Due to the network characteristics of the access layer switch, each administrative area has one or more independent access devices. According to the actual situation of the enterprise, the IP address of the access device in each administrative area can be used as the information to identify the access area, and the RADIUS server can identify the area from which the access user is connected based on the IP address of the access device in the authentication message. into the network.
基于上述的组网结构,本发明所提出的技术方案具体如图6所示,包括以下步骤:Based on the above-mentioned networking structure, the technical solution proposed by the present invention is specifically shown in Figure 6, including the following steps:
步骤S601、根据行政划分网络接入区域,并在RADIUS服务器中设置各种访问权限。Step S601, divide the network access area according to the administration, and set various access rights in the RADIUS server.
在RADIUS服务器(也可以是基于RADIUS服务器的网络接入控制系统)上为各接入区域配置各类访问权限。例如:为本区域内的固定工作人员配置级别较高的访问权限,包括可访问本行政区域网络的服务器、业务系统、存储设备等资源的权限。而针对本区域内的非固定工作人员,例如:漫游工作人员、访客、合作供应商,可以根据需要提供最基本的网络访问权限,包括可访问互联网,但不可访问本行政区域网络内的关键资源的权限。Configure various access rights for each access area on the RADIUS server (or a network access control system based on the RADIUS server). For example: configure higher-level access rights for permanent staff in the region, including access to resources such as servers, business systems, and storage devices in the administrative region network. For non-fixed staff in this area, such as roaming staff, visitors, and cooperative suppliers, the most basic network access rights can be provided as needed, including access to the Internet, but not access to key resources in the administrative area network permission.
步骤S602、RADIUS服务器设置接入用户在各行政区域的访问权限。Step S602, the RADIUS server sets the access rights of the access users in each administrative area.
根据接入用户的实际职能及工作需要,在RADIUS服务器(也可以是基于RADIUS服务器的网络接入控制系统)上为其分配访问权限。根据接入用户的所属行政部门,为其设置适当的网络访问权限,以利于其在所属行政区域正常访问工作需要的资源。若该用户有漫游到其他行政部门工作的需求,则需要为其申请其他接入区域的访问权限。这种访问权限是经过统一定义的,具体的权限内容可以根据需要进行设定,避免因工作场所漫游而导致的安全隐患。According to the actual functions and work needs of access users, assign access rights to them on the RADIUS server (or a network access control system based on the RADIUS server). According to the administrative department to which the access user belongs, set the appropriate network access authority for it, so as to facilitate its normal access to the resources needed for work in the administrative area to which it belongs. If the user needs to roam to work in other administrative departments, he needs to apply for access rights to other access areas. This kind of access right is uniformly defined, and the specific content of the right can be set as needed to avoid security risks caused by roaming in the workplace.
步骤S603、接入主机向接入设备发送用户名和密码,请求进行认证。Step S603, the access host sends the user name and password to the access device, requesting authentication.
接入用户无论在何行政区域接入上网,均采用固定用户名通过802.1x协议认证接入上网。Regardless of the administrative area where the access user accesses the Internet, they all use a fixed user name to access the Internet through 802.1x protocol authentication.
步骤S604、接入设备向RADIUS服务器发送包含用户名、密码和接入设备IP地址信息的认证请求消息。Step S604, the access device sends an authentication request message including the user name, password and IP address information of the access device to the RADIUS server.
在收到用户进行认证的请求后,接入设备发送一个访问-请求(Access-Request)消息到RADIUS服务器,此消息一般包含以下信息:After receiving the user's authentication request, the access device sends an Access-Request (Access-Request) message to the RADIUS server. This message generally includes the following information:
(1)用户名;(1) Username;
(2)加密格式的用户口令;(2) user password in encrypted format;
(3)接入设备IP和端口。(3) Access device IP and port.
步骤S605、RADIUS服务器向接入设备返回认证成功或失败的消息。Step S605, the RADIUS server returns a message of authentication success or failure to the access device.
如果RADIUS服务器对用户进行了成功的认证,就会发送一个访问-接受(Access-Accept)消息。该消息包含了应用到用户的授权属性值(AVP)对;If the RADIUS server successfully authenticates the user, it sends an Access-Accept (Access-Accept) message. The message contains authorization attribute value (AVP) pairs that apply to the user;
如果RADIUS服务器不接受接入设备提供给RADIUS服务器的任何一个值时,会发送一个访问-拒绝(Access-Reject)消息。If the RADIUS server does not accept any value provided by the access device to the RADIUS server, it will send an Access-Reject (Access-Reject) message.
后续的步骤S606至步骤S611具体为认证成功后的资源访问流程,这并分本发明关注的重点,因此,不再详细叙述。Subsequent steps S606 to S611 are specifically the resource access process after the authentication is successful, which is not the focus of the present invention, so it will not be described in detail.
需要指出的是,其中的计费过程,对于企业内部来讲,计费过程中的具体计费数值一直为0。It should be pointed out that, in the billing process, for the enterprise internally, the specific billing value in the billing process is always 0.
由上述说明可以确认,在RADIUS认证过程中认证请求报文包含接入设备IP和端口。由于在步骤S601中,通过将接入设备的IP组根据行政区域划分设置成接入区域信息,并保存到RADIUS服务器中。因此,在认证时,RADIUS服务器可以判断接入用户是从何区域接入的。根据步骤S502中为用户设置的在各个接入区域的访问权限信息,在接入用户认证成功后,RADIUS服务器将符合既定安全策略的网络访问授权信息下发给接入设备,从而保证了接入用户对网络的安全使用。It can be confirmed from the above description that during the RADIUS authentication process, the authentication request message contains the IP and port of the access device. Because in step S601, the IP group of the access device is set as the access area information according to the division of the administrative area, and is saved in the RADIUS server. Therefore, during authentication, the RADIUS server can determine from which area the user accesses. According to the access authority information in each access area set for the user in step S502, after the access user is successfully authenticated, the RADIUS server will send the network access authorization information that conforms to the established security policy to the access device, thus ensuring access User's Safe Use of the Network.
为了实现上述的技术方案,本发明还提供了一种网络认证服务器,应用于包括网络认证服务器和多个网络接入区域的网络系统中,其中,每个网络接入区域分别包括一个接入设备和至少一个用户终端,网络系统中建立至少一个用户账户,用户帐户对应一个用户名。In order to realize the above technical solution, the present invention also provides a network authentication server, which is applied to a network system including a network authentication server and multiple network access areas, wherein each network access area includes an access device and at least one user terminal, at least one user account is established in the network system, and the user account corresponds to a user name.
如图7所示,网络认证服务器具体包括:As shown in Figure 7, the network authentication server specifically includes:
设置模块71,用于为每个网络接入区域建立至少一种资源访问权限,并分别设置用户账户在每个网络接入区域中所对应的资源访问权限。The
存储模块72,与设置模块71电性连接,用于存储用户账户的用户名在每个网络接入区域中的资源访问权限与网络接入区域的位置识别信息的对应关系信息。The
通信模块73,与存储模块72电性连接,用于接收接入设备发送的包含用户账户的用户名、密码和用户账户当前所处的网络接入区域的位置识别信息的认证请求消息,并根据认证结果向接入设备发送用户名的认证确认信息或认证失败消息,以及在用户名认证成功的情况下,向接入设备发送该用户账户的资源访问权限。The
其中,在具体的应用场景中,用户名所对应的用户当前所处的网络接入区域的位置识别信息具体为:Among them, in a specific application scenario, the location identification information of the network access area where the user corresponds to the user name is specifically:
用户名所对应的用户当前所处的网络接入区域的接入设备的IP地址;或,The IP address of the access device in the network access area where the user corresponds to the user name; or,
用户名所对应的用户当前所处的网络接入区域中的用户终端的IP地址。The user name corresponds to the IP address of the user terminal in the network access area where the user is currently located.
在具体的应用场景中,如果用户名所对应的用户当前所处的网络接入区域的位置识别信息具体为用户名所对应的用户进行认证的用户终端的IP地址,网络认证服务器中还需要进行以下设定:In a specific application scenario, if the location identification information of the network access area where the user corresponding to the user name is currently located is specifically the IP address of the user terminal for authentication by the user corresponding to the user name, the network authentication server also needs to perform the following settings: Certainly:
多个网络接入区域分别对应多个IP地址区间;Multiple network access areas correspond to multiple IP address intervals;
网络接入区域中所包括的至少一个用户终端的IP地址处于网络接入区域所对应的IP地址区间中。The IP address of at least one user terminal included in the network access area is in the IP address range corresponding to the network access area.
认证模块74,与存储模块72和通信模块73电性连接,用于根据存储模块72所存储的访问权限信息,获取通信模块73所接收的用户名在网络接入区域的位置识别信息所对应的网络接入区域中的访问权限信息。The
在具体的应用场景中,认证模块74对用户账户在网络接入区域的认证具体通过以下方式实现。In a specific application scenario, the
如果认证模块74对用户账户的用户名和密码的匹配关系进行认证成功,则通信模块73向接入设备发送用户账户的认证确认信息,并根据访问权限信息与用户名在网络接入区域的对应关系,为该用户账户分配资源访问权限;If the
如果认证模块74对所述用户账户的用户名和密码的匹配关系进行认证失败,或认证模块74向存储模块72获取用户账户的用户名在网络接入区域的位置识别信息所对应的网络接入区域中所对应的资源访问权限失败,t通信模块73向接入设备发送认证失败消息,拒绝该用户账户进行资源访问。If the
通过本发明,实现了基于用户的实际接入位置进行访问权限分配,可以避免由于接入区域变更而访问权限不可控,并可以对于各接入区域的非固定工作人员采用统一的访问权限控制,而单一账号进行访问的方式也为用户的使用提供了便利,在提高网络安全性的同时,改善了用户体验。Through the present invention, the distribution of access rights based on the actual access location of the user is realized, which can avoid uncontrollable access rights due to changes in access areas, and can adopt unified access rights control for non-fixed staff in each access area, The way of accessing with a single account also provides convenience for users, and improves user experience while improving network security.
通过以上的实施方式的描述,本领域的技术人员可以清楚地了解到本发明可以通过硬件实现,也可以借助软件加必要的通用硬件平台的方式来实现。基于这样的理解,本发明的技术方案可以以软件产品的形式体现出来,该软件产品可以存储在一个非易失性存储介质(可以是CD-ROM,U盘,移动硬盘等)中,包括若干指令用以使得一台计算机设备(可以是个人计算机,服务器,或者网络设备等)执行本发明各个实施场景所述的方法。Through the above description of the embodiments, those skilled in the art can clearly understand that the present invention can be realized by hardware, or by software plus a necessary general hardware platform. Based on this understanding, the technical solution of the present invention can be embodied in the form of software products, which can be stored in a non-volatile storage medium (which can be CD-ROM, U disk, mobile hard disk, etc.), including several The instructions are used to make a computer device (which may be a personal computer, a server, or a network device, etc.) execute the methods described in various implementation scenarios of the present invention.
本领域技术人员可以理解附图只是一个优选实施场景的示意图,附图中的模块或流程并不一定是实施本发明所必须的。Those skilled in the art can understand that the accompanying drawing is only a schematic diagram of a preferred implementation scenario, and the modules or processes in the accompanying drawings are not necessarily necessary for implementing the present invention.
本领域技术人员可以理解实施场景中的装置中的模块可以按照实施场景描述进行分布于实施场景的装置中,也可以进行相应变化位于不同于本实施场景的一个或多个装置中。上述实施场景的模块可以合并为一个模块,也可以进一步拆分成多个子模块。Those skilled in the art can understand that the modules in the devices in the implementation scenario can be distributed among the devices in the implementation scenario according to the description of the implementation scenario, or can be located in one or more devices different from the implementation scenario according to corresponding changes. The modules of the above implementation scenarios can be combined into one module, or can be further split into multiple sub-modules.
上述本发明序号仅仅为了描述,不代表实施场景的优劣。The above serial numbers of the present invention are for description only, and do not represent the pros and cons of the implementation scenarios.
以上公开的仅为本发明的几个具体实施场景,但是,本发明并非局限于此,任何本领域的技术人员能思之的变化都应落入本发明的保护范围。The above disclosures are only some specific implementation scenarios of the present invention, however, the present invention is not limited thereto, and any changes conceivable by those skilled in the art shall fall within the protection scope of the present invention.
Claims (9)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN2009101487926ACN101582769B (en) | 2009-07-03 | 2009-07-03 | Authority setting method of user access network and equipment |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN2009101487926ACN101582769B (en) | 2009-07-03 | 2009-07-03 | Authority setting method of user access network and equipment |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN101582769Atrue CN101582769A (en) | 2009-11-18 |
| CN101582769B CN101582769B (en) | 2012-07-04 |
Family
ID=41364751
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN2009101487926AExpired - Fee RelatedCN101582769B (en) | 2009-07-03 | 2009-07-03 | Authority setting method of user access network and equipment |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN101582769B (en) |
Cited By (36)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN101958846A (en)* | 2010-11-03 | 2011-01-26 | 北京北信源软件股份有限公司 | Method for client roaming across servers |
| CN102404110A (en)* | 2011-12-08 | 2012-04-04 | 宇龙计算机通信科技(深圳)有限公司 | Method and device for obtaining secret key |
| CN102413137A (en)* | 2011-11-21 | 2012-04-11 | 北京地拓科技发展有限公司 | Data access method and device |
| CN102487383A (en)* | 2010-12-02 | 2012-06-06 | 上海可鲁系统软件有限公司 | An industrial Internet distributed system security access control device |
| CN102959928A (en)* | 2011-02-28 | 2013-03-06 | 西门子企业通讯有限责任两合公司 | Apparatus and mechanism for dynamically allocating survivability services to mobile equipment |
| CN103383724A (en)* | 2013-06-28 | 2013-11-06 | 记忆科技(深圳)有限公司 | Storing device and data access authority management method thereof |
| CN103607372A (en)* | 2013-08-19 | 2014-02-26 | 深信服网络科技(深圳)有限公司 | Authentication method and device for network access |
| CN104052756A (en)* | 2014-06-27 | 2014-09-17 | 北京思特奇信息技术股份有限公司 | Method and system for service network elements to have safe access to service controller |
| CN104125066A (en)* | 2013-04-26 | 2014-10-29 | 美国博通公司 | Methods and systems for secured authentication of applications on a network |
| CN104394219A (en)* | 2014-11-27 | 2015-03-04 | 英业达科技有限公司 | Cloud management method |
| CN104468553A (en)* | 2014-11-28 | 2015-03-25 | 北京奇虎科技有限公司 | Method, device and system for login of public account |
| CN104717062A (en)* | 2013-12-11 | 2015-06-17 | 杭州华三通信技术有限公司 | Method and device for quick visitor access based on BYOD management system |
| CN104767715A (en)* | 2014-01-03 | 2015-07-08 | 华为技术有限公司 | Network access control method and device |
| CN104916101A (en)* | 2015-04-14 | 2015-09-16 | 北京网河时代科技有限公司 | Bluetooth 4.0 wall switch control system |
| CN104951692A (en)* | 2015-05-04 | 2015-09-30 | 联想(北京)有限公司 | Information processing method and first electronic equipment |
| CN105429998A (en)* | 2015-01-06 | 2016-03-23 | 李先志 | Network security area login method and device |
| CN105516378A (en)* | 2014-09-25 | 2016-04-20 | 华为技术有限公司 | Method and device for providing access position |
| CN105847239A (en)* | 2016-03-17 | 2016-08-10 | 汉柏科技有限公司 | User authentication manner determining method and device |
| CN106034104A (en)* | 2015-03-07 | 2016-10-19 | 华为技术有限公司 | Authentication method, device and system for network application access |
| CN106162549A (en)* | 2015-05-19 | 2016-11-23 | 中兴通讯股份有限公司 | The processing method and processing device of access network |
| CN107005546A (en)* | 2014-12-12 | 2017-08-01 | 英特尔公司 | Technology for the Authorized operation of authentication server |
| CN103905431B (en)* | 2014-03-07 | 2017-08-08 | 汉柏科技有限公司 | A kind of user authen method and subscriber authentication server |
| CN108429732A (en)* | 2018-01-23 | 2018-08-21 | 平安普惠企业管理有限公司 | A kind of method and system obtaining resource |
| US10079836B2 (en) | 2013-04-26 | 2018-09-18 | Avago Technologies General Ip (Singapore) Pte. Ltd. | Methods and systems for secured authentication of applications on a network |
| CN109150787A (en)* | 2017-06-13 | 2019-01-04 | 西安中兴新软件有限责任公司 | A kind of authority acquiring method, apparatus, equipment and storage medium |
| CN109145560A (en)* | 2018-08-08 | 2019-01-04 | 北京小米移动软件有限公司 | The method and device of accessing monitoring equipment |
| CN109660593A (en)* | 2018-11-05 | 2019-04-19 | 深圳绿米联创科技有限公司 | Platform of internet of things access management method, apparatus and system |
| CN109831492A (en)* | 2013-08-14 | 2019-05-31 | 华为技术有限公司 | Access the method and device of OTT application, server push message |
| WO2019157934A1 (en)* | 2018-02-14 | 2019-08-22 | 华为技术有限公司 | Network access method and related apparatus |
| CN110519404A (en)* | 2019-08-02 | 2019-11-29 | 锐捷网络股份有限公司 | A kind of policy management method based on SDN, device and electronic equipment |
| CN110620782A (en)* | 2019-09-29 | 2019-12-27 | 深圳市珍爱云信息技术有限公司 | Account authentication method and device, computer equipment and storage medium |
| CN112822160A (en)* | 2020-12-29 | 2021-05-18 | 新华三技术有限公司 | Equipment identification method, device, equipment and machine-readable storage medium |
| CN113271285A (en)* | 2020-02-14 | 2021-08-17 | 北京沃东天骏信息技术有限公司 | Method and device for accessing network |
| CN113596044A (en)* | 2021-08-03 | 2021-11-02 | 北京恒安嘉新安全技术有限公司 | Network protection method and device, electronic equipment and storage medium |
| CN113612740A (en)* | 2021-07-21 | 2021-11-05 | 腾讯科技(深圳)有限公司 | Authority management method and device, computer readable medium and electronic equipment |
| CN119760755A (en)* | 2025-03-07 | 2025-04-04 | 祥符实验室 | A data information management method and system based on the field of medical research and development |
Families Citing this family (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN113468511B (en)* | 2021-07-21 | 2022-04-15 | 腾讯科技(深圳)有限公司 | Data processing method and device, computer readable medium and electronic equipment |
Family Cites Families (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US7072945B1 (en)* | 2000-06-30 | 2006-07-04 | Nokia Corporation | Network and method for controlling appliances |
| CN1248455C (en)* | 2003-02-21 | 2006-03-29 | 北京润汇科技有限公司 | Customer access management system for wideband network |
| CN100499554C (en)* | 2007-06-28 | 2009-06-10 | 杭州华三通信技术有限公司 | Network admission control method and network admission control system |
- 2009
- 2009-07-03CNCN2009101487926Apatent/CN101582769B/ennot_activeExpired - Fee Related
Cited By (60)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN101958846A (en)* | 2010-11-03 | 2011-01-26 | 北京北信源软件股份有限公司 | Method for client roaming across servers |
| CN101958846B (en)* | 2010-11-03 | 2015-04-15 | 北京北信源软件股份有限公司 | Method for client roaming across servers |
| CN102487383A (en)* | 2010-12-02 | 2012-06-06 | 上海可鲁系统软件有限公司 | An industrial Internet distributed system security access control device |
| CN102487383B (en)* | 2010-12-02 | 2015-01-28 | 上海可鲁系统软件有限公司 | An industrial Internet distributed system security access control device |
| CN102959928B (en)* | 2011-02-28 | 2016-09-07 | 西门子企业通讯有限责任两合公司 | Apparatus and mechanism for dynamically allocating survivability services to mobile equipment |
| CN102959928A (en)* | 2011-02-28 | 2013-03-06 | 西门子企业通讯有限责任两合公司 | Apparatus and mechanism for dynamically allocating survivability services to mobile equipment |
| CN102413137B (en)* | 2011-11-21 | 2014-10-08 | 北京地拓科技发展有限公司 | Data access method and device |
| CN102413137A (en)* | 2011-11-21 | 2012-04-11 | 北京地拓科技发展有限公司 | Data access method and device |
| CN102404110A (en)* | 2011-12-08 | 2012-04-04 | 宇龙计算机通信科技(深圳)有限公司 | Method and device for obtaining secret key |
| CN104125066A (en)* | 2013-04-26 | 2014-10-29 | 美国博通公司 | Methods and systems for secured authentication of applications on a network |
| US10079836B2 (en) | 2013-04-26 | 2018-09-18 | Avago Technologies General Ip (Singapore) Pte. Ltd. | Methods and systems for secured authentication of applications on a network |
| CN104125066B (en)* | 2013-04-26 | 2018-01-26 | 安华高科技通用Ip(新加坡)公司 | The method and system of the safety certification of application on network |
| CN103383724A (en)* | 2013-06-28 | 2013-11-06 | 记忆科技(深圳)有限公司 | Storing device and data access authority management method thereof |
| CN109831492B (en)* | 2013-08-14 | 2021-06-22 | 华为技术有限公司 | Method and device for accessing OTT applications and server push messages |
| CN109831492A (en)* | 2013-08-14 | 2019-05-31 | 华为技术有限公司 | Access the method and device of OTT application, server push message |
| CN103607372A (en)* | 2013-08-19 | 2014-02-26 | 深信服网络科技(深圳)有限公司 | Authentication method and device for network access |
| CN103607372B (en)* | 2013-08-19 | 2016-12-28 | 深信服网络科技(深圳)有限公司 | The authentication method of network insertion and device |
| CN104717062B (en)* | 2013-12-11 | 2018-03-16 | 新华三技术有限公司 | The method and device that a kind of visitor based on BYOD management systems quickly accesses |
| CN104717062A (en)* | 2013-12-11 | 2015-06-17 | 杭州华三通信技术有限公司 | Method and device for quick visitor access based on BYOD management system |
| WO2015085872A1 (en)* | 2013-12-11 | 2015-06-18 | Hangzhou H3C Technologies Co., Ltd | Method and device for access of guests |
| CN104767715B (en)* | 2014-01-03 | 2018-06-26 | 华为技术有限公司 | Access control method and equipment |
| CN104767715A (en)* | 2014-01-03 | 2015-07-08 | 华为技术有限公司 | Network access control method and device |
| CN103905431B (en)* | 2014-03-07 | 2017-08-08 | 汉柏科技有限公司 | A kind of user authen method and subscriber authentication server |
| CN104052756B (en)* | 2014-06-27 | 2017-08-01 | 北京思特奇信息技术股份有限公司 | A kind of method and system of business network element secure accessing service controller |
| CN104052756A (en)* | 2014-06-27 | 2014-09-17 | 北京思特奇信息技术股份有限公司 | Method and system for service network elements to have safe access to service controller |
| CN105516378A (en)* | 2014-09-25 | 2016-04-20 | 华为技术有限公司 | Method and device for providing access position |
| CN105516378B (en)* | 2014-09-25 | 2019-02-12 | 华为技术有限公司 | Method and device for providing access location |
| CN104394219A (en)* | 2014-11-27 | 2015-03-04 | 英业达科技有限公司 | Cloud management method |
| CN104468553A (en)* | 2014-11-28 | 2015-03-25 | 北京奇虎科技有限公司 | Method, device and system for login of public account |
| CN107005546B (en)* | 2014-12-12 | 2020-11-17 | 英特尔公司 | Method, device and apparatus for verifying authorized operation of server |
| CN107005546A (en)* | 2014-12-12 | 2017-08-01 | 英特尔公司 | Technology for the Authorized operation of authentication server |
| CN105429998A (en)* | 2015-01-06 | 2016-03-23 | 李先志 | Network security area login method and device |
| CN106034104A (en)* | 2015-03-07 | 2016-10-19 | 华为技术有限公司 | Authentication method, device and system for network application access |
| US10924495B2 (en) | 2015-03-07 | 2021-02-16 | Huawei Technologies Co., Ltd. | Verification method, apparatus, and system used for network application access |
| CN104916101A (en)* | 2015-04-14 | 2015-09-16 | 北京网河时代科技有限公司 | Bluetooth 4.0 wall switch control system |
| CN104951692A (en)* | 2015-05-04 | 2015-09-30 | 联想(北京)有限公司 | Information processing method and first electronic equipment |
| CN106162549A (en)* | 2015-05-19 | 2016-11-23 | 中兴通讯股份有限公司 | The processing method and processing device of access network |
| CN105847239A (en)* | 2016-03-17 | 2016-08-10 | 汉柏科技有限公司 | User authentication manner determining method and device |
| CN109150787A (en)* | 2017-06-13 | 2019-01-04 | 西安中兴新软件有限责任公司 | A kind of authority acquiring method, apparatus, equipment and storage medium |
| CN108429732A (en)* | 2018-01-23 | 2018-08-21 | 平安普惠企业管理有限公司 | A kind of method and system obtaining resource |
| CN110167102B (en)* | 2018-02-14 | 2021-01-15 | 华为技术有限公司 | Network access method and related device |
| US11297587B2 (en) | 2018-02-14 | 2022-04-05 | Huawei Technologies Co., Ltd. | Network access method and related apparatus |
| CN110167102A (en)* | 2018-02-14 | 2019-08-23 | 华为技术有限公司 | A kind of method and relevant apparatus of network insertion |
| WO2019157934A1 (en)* | 2018-02-14 | 2019-08-22 | 华为技术有限公司 | Network access method and related apparatus |
| CN109145560A (en)* | 2018-08-08 | 2019-01-04 | 北京小米移动软件有限公司 | The method and device of accessing monitoring equipment |
| CN109145560B (en)* | 2018-08-08 | 2022-03-25 | 北京小米移动软件有限公司 | Method and device for accessing monitoring equipment |
| CN109660593A (en)* | 2018-11-05 | 2019-04-19 | 深圳绿米联创科技有限公司 | Platform of internet of things access management method, apparatus and system |
| CN109660593B (en)* | 2018-11-05 | 2021-12-07 | 深圳绿米联创科技有限公司 | Internet of things platform access management method, device and system |
| CN110519404B (en)* | 2019-08-02 | 2022-04-26 | 锐捷网络股份有限公司 | SDN-based policy management method and device and electronic equipment |
| CN110519404A (en)* | 2019-08-02 | 2019-11-29 | 锐捷网络股份有限公司 | A kind of policy management method based on SDN, device and electronic equipment |
| CN110620782A (en)* | 2019-09-29 | 2019-12-27 | 深圳市珍爱云信息技术有限公司 | Account authentication method and device, computer equipment and storage medium |
| CN113271285A (en)* | 2020-02-14 | 2021-08-17 | 北京沃东天骏信息技术有限公司 | Method and device for accessing network |
| CN113271285B (en)* | 2020-02-14 | 2023-08-08 | 北京沃东天骏信息技术有限公司 | Method and device for accessing network |
| CN112822160B (en)* | 2020-12-29 | 2022-10-21 | 新华三技术有限公司 | Equipment identification method, device, equipment and machine-readable storage medium |
| CN112822160A (en)* | 2020-12-29 | 2021-05-18 | 新华三技术有限公司 | Equipment identification method, device, equipment and machine-readable storage medium |
| CN113612740A (en)* | 2021-07-21 | 2021-11-05 | 腾讯科技(深圳)有限公司 | Authority management method and device, computer readable medium and electronic equipment |
| CN113612740B (en)* | 2021-07-21 | 2022-08-26 | 腾讯科技(深圳)有限公司 | Authority management method and device, computer readable medium and electronic equipment |
| CN113596044B (en)* | 2021-08-03 | 2023-04-25 | 北京恒安嘉新安全技术有限公司 | Network protection method and device, electronic equipment and storage medium |
| CN113596044A (en)* | 2021-08-03 | 2021-11-02 | 北京恒安嘉新安全技术有限公司 | Network protection method and device, electronic equipment and storage medium |
| CN119760755A (en)* | 2025-03-07 | 2025-04-04 | 祥符实验室 | A data information management method and system based on the field of medical research and development |
Also Published As
| Publication number | Publication date |
|---|---|
| CN101582769B (en) | 2012-07-04 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN101582769B (en) | Authority setting method of user access network and equipment | |
| US12126997B2 (en) | Mobile authentication in mobile virtual network | |
| US12199971B2 (en) | System and method for transferring device identifying information | |
| CN101120569B (en) | Remote access system and method for user to remotely access terminal equipment from user terminal | |
| EP2014067B1 (en) | Provisioned configuration for automatic wireless connection | |
| CN104813328B (en) | trusted container | |
| JP5260634B2 (en) | Stepwise authentication system | |
| US20050132229A1 (en) | Virtual private network based on root-trust module computing platforms | |
| US20110167256A1 (en) | Role-based access control utilizing token profiles | |
| US20110167483A1 (en) | Role-based access control utilizing token profiles having predefined roles | |
| CN102916946B (en) | Connection control method and system | |
| US20130339740A1 (en) | Multi-factor certificate authority | |
| CN101567878B (en) | The Method of Improving the Security of Network Identity Authentication | |
| KR20100029098A (en) | Device provisioning and domain join emulation over non-secured networks | |
| US20220311777A1 (en) | Hardening remote administrator access | |
| CA2647684A1 (en) | Secure wireless guest access | |
| CN101986598B (en) | Authentication method, server and system | |
| CN108881309A (en) | Access method, device, electronic equipment and the readable storage medium storing program for executing of big data platform | |
| CN101291220B (en) | System, device and method for identity security authentication | |
| CN105610839A (en) | Controlling method and device for accessing network by terminal | |
| CN112016073A (en) | Method for constructing server zero trust connection architecture | |
| US20180145984A1 (en) | System and method for providing security solutions to protect enterprise critical assets | |
| CN118890518A (en) | A security authentication method for smart set-top box | |
| WO2007090866A1 (en) | Collaborative access control in a computer network | |
| CN116938588A (en) | Local area network security access method, system and network connection equipment |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| C06 | Publication | ||
| PB01 | Publication | ||
| C10 | Entry into substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| C14 | Grant of patent or utility model | ||
| GR01 | Patent grant | ||
| CP03 | Change of name, title or address | Address after:310052 Binjiang District Changhe Road, Zhejiang, China, No. 466, No. Patentee after:NEW H3C TECHNOLOGIES Co.,Ltd. Address before:310053 Hangzhou hi tech Industrial Development Zone, Zhejiang province science and Technology Industrial Park, No. 310 and No. six road, HUAWEI, Hangzhou production base Patentee before:HANGZHOU H3C TECHNOLOGIES Co.,Ltd. | |
| CP03 | Change of name, title or address | ||
| CF01 | Termination of patent right due to non-payment of annual fee | Granted publication date:20120704 | |
| CF01 | Termination of patent right due to non-payment of annual fee |