- Notifications
You must be signed in to change notification settings - Fork281
For basic researches, top 25 vulnerability parameters that can be used in automation tools or manual recon. 🛡️⚔️🧙
License
lutfumertceylan/top25-parameter
Folders and files
| Name | Name | Last commit message | Last commit date | |
|---|---|---|---|---|
Repository files navigation
For basic researches, top 25 vulnerability parameters that can be used in automation tools or manual recon
For basic researches, top 25 vulnerable parameters based on frequency of use with reference to various articles. These parameters can be used for automation tools or manual recon. Although the prevalence percentages of these parameters cannot be proven precisely.
Data sources include numerous articles, blogs, and other resources obtained via OSINT and other open-source projects including work similar to that of Jason Haddix and HUNT.
This repo contains common parameters of the following vulnerabilities:
- Cross-Site Scripting (XSS)- Server-Side Request Forgery (SSRF)- Local File Inclusion (LFI)- SQL Injection (SQLi)- Remote Code Execution (RCE) - [for GET and POST methods]- Open Redirect- Cross-Site Scripting
- Server-Side Request Forgery
- Local File Inclusion
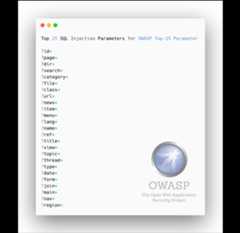
- SQL Injection
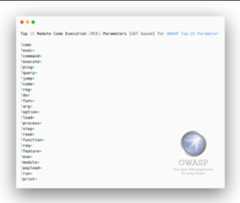
- Remote Code Execution
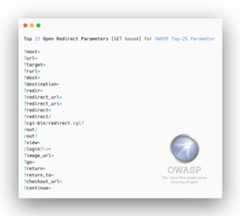
- Open Redirect
To report issues or make suggestions for the Top-25 Parameters, please useGitHub Issues.
For everything else, we're easy to answer your e-mail :
- Send an e-mail tolutfu.mertceylan[at]owasp.org
- Send an e-mail toinfo[at]lutfumertceylan.com.tr
You can @ us on Twitter@lutfumertceylan.
About
For basic researches, top 25 vulnerability parameters that can be used in automation tools or manual recon. 🛡️⚔️🧙
Topics
Resources
License
Uh oh!
There was an error while loading.Please reload this page.
Stars
Watchers
Forks
Packages0
Contributors3
Uh oh!
There was an error while loading.Please reload this page.