- Notifications
You must be signed in to change notification settings - Fork100
ee09115/spoofing_detection
Folders and files
| Name | Name | Last commit message | Last commit date | |
|---|---|---|---|---|
Repository files navigation
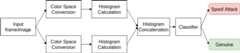
This repository is dedicated to the image-based Presentation Attack Detection - PAD - systems in two different domains: (i) cork and (ii) face PAD. The proposed PAD system relies on the combination of two different color spaces and uses only a single frame to distinguish from a bona fide image and an image attack, see Fig. 1.
Fig. 1 - General flowchart for the developed image-based PAD system.
- Trained models for the public face anti-spoofingPrint-attack database;
- Trained models for the public face anti-spoofingReplay-attack database;
- Error rate curve for the development set of thePrint-attack database
- Error rate curve for the development set of theReplay-Attack database;
- [1] -Image-based Object Spoofing Detection - Conference paper
| Method | Print-attack | Replay-attack | ||
| EER(%) | HTER(%) | EER(%) | HTER(%) | |
| YCRCB+LUV+ETC [1] | 1.33 | 0.00 | 0.00756 | 0.5954 |
| YCRCB+LUV+SVM [1] | 0.00 | 1.76 | 4.30 | 7.86 |
Demonstrative results of the proposed face PAD system - YCRCB+LUV+ETC. The classification model used in this test was trained using the training set of the Replay-Attack database.
If you use any part of this work please cite [1]:
@InProceedings{10.1007/978-3-030-05288-1_15,author="Costa, Valterand Sousa, Armandoand Reis, Ana",editor="Barneva, Reneta P.and Brimkov, Valentin E.and Tavares, Jo{\~a}o Manuel R.S.",title="Image-Based Object Spoofing Detection",booktitle="Combinatorial Image Analysis",year="2018",publisher="Springer International Publishing",address="Cham",pages="189--201",abstract="Using 2D images in authentication systems raises the question of spoof attacks: is it possible to deceive an authentication system using fake models possessing identical visual properties of the genuine one? In this work, an anti-spoofing method approach for a wine anti-counterfeiting system is presented. The proposed method relies in two different color spaces: CIE L*u*v* and {\$}{\$}YC{\_}rC{\_}b{\$}{\$}, to distinguish between a genuine instance and a spoof attack. To evaluate the proposed strategy, two databases were used: a private database, with photos/2D attacks of cork stoppers, created for this work; and the public Replay-Attack database that is used for face spoofing detection methods testing. The results on the private database show that the anti-spoofing approach is able to distinguish with high accuracy a real photo from an attack. Regarding the public database, the results were obtained with existing methods, as the best HTER results using a single frame approach.",isbn="978-3-030-05288-1"}About
Cork/Face Presentation Attack Detection
Topics
Resources
Uh oh!
There was an error while loading.Please reload this page.
Stars
Watchers
Forks
Releases
Packages0
Uh oh!
There was an error while loading.Please reload this page.