- Notifications
You must be signed in to change notification settings - Fork2
A client-server application for CVE analysis and exploit detection with bilingual support, detailed reports, and a modern web interface.
License
cansolele/exploit-seek
Folders and files
| Name | Name | Last commit message | Last commit date | |
|---|---|---|---|---|
Repository files navigation

A client-server application for comprehensive CVE analysis, exploit detection and vulnerability assessment. The system provides a modern web interface with powerful features to aggregate data from multiple trusted sources, helping security professionals evaluate risks, detect available exploits and determine patching priorities through detailed analysis and reporting capabilities.
Installation Guide •Features •Examples •Roadmap

Click to expand
Exploit Seek is a comprehensive client-server application designed to analyze CVE vulnerabilities and detect available exploits. The system features an intuitive web interface with bilingual support, customizable themes, and real-time analysis tracking. It collects and processes data from multiple trusted sources, including exploit databases, security research repositories, and vulnerability intelligence platforms, helping security professionals assess exploitation risks, identify public exploits, and generate detailed analytical reports.
- Dark/Light theme support for comfortable work at any time
- Bilingual interface (English/Russian)
- Real-time analysis progress tracking
- File history with quick access to previous reports
- User-friendly settings management:
- Server configuration
- API keys management
- Proxy configuration (HTTP/HTTPS support with authentication)
- Language selection
- Theme preferences
- Secure authentication system
- Comprehensive vulnerability assessment using CVSS scoring system
- Exploitation probability evaluation through EPSS
- Public exploit detection from multiple sources:
- ExploitDB repository scanning
- GitHub security research monitoring
- VulnCheck intelligence integration
- Integration with CISA Known Exploited Vulnerabilities (KEV) catalog
- Nuclei template matching for vulnerability verification
- Advanced patching priority assessment (A+ to D rating) based on:
- CVSS base scores
- EPSS probability
- Public exploit availability
- Presence in CISA KEV catalog
- Multiple vulnerability scanner format support:
- REDCheck reports
- Nmap Vulners output
- Custom XML formats
- Direct CVE list input
- PDF report analysis
- Plain text file processing
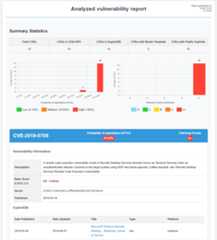
- Detailed Excel reports with:
- Summary statistics
- Color-coded priority indicators
- Data filtering capabilities
- Multiple sheets for exploits and references
- HTML report generation with interactive elements
- Bilingual report support (English/Russian)
View sample reports and outputs in our examples directory:
# Clone repositorygit clone https://github.com/cansolele/exploit-seek.gitcd exploit-seek# Build and start containersdocker-compose build --no-cachedocker-compose up -d# The server will be available at http://0.0.0.0:5000# The client will be available at http://0.0.0.0:8080
Server Setup
- Install system dependencies:
sudo apt updatesudo apt install -y python3 python3-pip python3-venv libxml-xpath-perl pdfgrep
- Create and activate virtual environment:
python3 -m venv venvsource venv/bin/activate- Install Python dependencies:
cd serverpip install -r requirements.txt- Run the server:
# Development modepython server.py# Production mode with Gunicorngunicorn --worker-class geventwebsocket.gunicorn.workers.GeventWebSocketWorker \ --workers 1 --bind 0.0.0.0:5000 server:app
Client Setup
- Navigate to the client directory:
cd exploit-seek/client- Install client dependencies:
npm install
- Build the client application:
npm run build
- Serve the client application:
- Using Python's HTTP server:
python3 -m http.server 8080 --directory dist
- Or using Node.js serve package:
npx serve -s dist
exploit-seek/├─ client/ # Frontend application│ ├─ Dockerfile│ ├─ src/│ │ ├─ components/ # React components│ │ │ ├─ Auth/ # Authentication components│ │ │ ├─ ExploitsTable/ # Main analysis interface│ │ │ ├─ Footer/ # Footer components│ │ │ └─ Header/ # Header and settings│ │ ├─ hooks/ # Custom React hooks│ │ └─ App.jsx # Main application component│ └─ vite.config.js # Vite configuration├─ server/ # Backend application│ ├─ Dockerfile│ ├─ auth.py # Authentication handling│ ├─ constants.py # Configuration constants│ ├─ cve_parsers.py # CVE extraction logic│ ├─ data_loaders.py # External API integrations│ ├─ excel_generator.py # Excel report generation│ ├─ html_generator.py # HTML report generation│ ├─ exploitdb_data.py # ExploitDB integration│ ├─ logger_config.py # Logging configuration│ ├─ models.py # Database models│ ├─ routes.py # API routes│ └─ server.py # Server initialization├─ docs/ # Screenshots and examples│ └─ images/│ ├─ dashboard.png│ └─ logo.png└─ docker-compose.yml # Docker compose configurationThe application requires API keys for full functionality:
- NVD API key: Register atNVD Portal
- VulnCheck API key: Available atVulnCheck
Configure these in the application settings after installation.
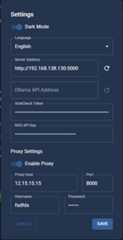
The application supports HTTP/HTTPS proxy configuration for all external API requests. You can configure proxy settings in three ways:
- No proxy (default)
- Basic proxy with host and port
- Authenticated proxy with username and password
To configure proxy in the web interface:
- Open Settings
- Enable proxy toggle
- Enter proxy details:
- Host (required)
- Port (required)
- Username (optional)
- Password (optional)
The proxy configuration will be applied to all external API requests, including:
- NVD API
- EPSS API
- GitHub API
- VulnCheck API
- ExploitDB data
- KEV catalog
- Nuclei templates
- Initial Setup
- Configure server address
- Set up API keys (NVD, VulnCheck)
- Choose interface language (English/Russian)
- Select theme mode (Dark/Light)
- Configure other interface preferences
- Data Input
- Choose input method (manual/file upload)
- Select vulnerability scanner type
- Upload or enter CVE data
- Analysis Configuration
- Select data sources
- Configure output settings
- Choose sorting options
- Report Generation
- Select report format (HTML/Excel)
- Configure report details
- Download and view results
Reports include:
- Detailed CVE information with CVSS scores
- Exploitation probability assessments
- Available public exploits from multiple sources
- Patching priority recommendations
- References and additional resources
Excel reports feature:
- Color-coded priority indicators
- Custom data filtering
- Multiple data sheets
- Summary statistics
HTML reports provide:
- Interactive elements
- Comprehensive data presentation
- Easy navigation
- Export capabilities
- NVD - CVE information and CVSS scores
- FIRST.org - EPSS scoring
- CISA - Known Exploited Vulnerabilities Catalog
- Offensive Security - Exploit Database
- Project Discovery - Nuclei Templates
- VulnCheck - Vulnerability Intelligence
- React + Vite
- Material-UI
- Socket.IO Client
- Recharts
- Flask
- SQLAlchemy
- Flask-SocketIO
- OpenPyXL
- Jinja2
- Docker
- Docker Compose
- Gunicorn
- Gevent
Upcoming features and improvements:
- 🧠 Neural analysis integration with Ollama
- 🤖 AI-powered vulnerability assessment
- 📈 Advanced risk prediction models
- 🔍 Additional vulnerability scanner support
- 🔄 Automated scan result import
- 📊 Enhanced interactive HTML reports
- 🎨 Customizable report templates
- 📈 Advanced data visualization options
- 🔍 Deep learning-based exploit detection
- 🎯 Enhanced risk scoring algorithms
- 🔄 Real-time threat intelligence integration
For questions, bug reports, and suggestions, please contact:shvs@cbi-info.ru
About
A client-server application for CVE analysis and exploit detection with bilingual support, detailed reports, and a modern web interface.
Topics
Resources
License
Uh oh!
There was an error while loading.Please reload this page.
Stars
Watchers
Forks
Releases
Packages0
Uh oh!
There was an error while loading.Please reload this page.