Sample queries
This document provides you with suggested queries to make it easier to findimportant logs using the Logs Explorer in the Google Cloud console.The listed queries are written in theLogging query language,and they can be used in theLogs Explorer, theLogging API,or thecommand-line interface.
The Logs Explorer uses Boolean expressions to specify a subset of allthe log entries in your project. You can use these queries to choose log entriesfrom specific logs or log services, or that satisfy conditions on metadata oruser-defined fields.
Before you begin
Ensure that you have the correct Identity and Access Management permissions or roles forbuilding queries using the Logs Explorer. For details on thenecessary IAM permissions, seePermissions for the Google Cloud console.
Get started
In the Google Cloud console, go to theLogs Explorer page:
If you use the search bar to find this page, then select the result whose subheading isLogging.
Select the appropriate Google Cloud project or other Google Cloudresource for which you want to view logs.
Use the sample queries
To apply a query from the following tables, click thecontent_copyContent Copy icon for the expression,and then paste the copied expression intothe Logs Explorer query-editor field.
The following screenshot illustrates the query pane:
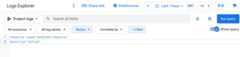
If you don't see the query-editor field, enableShow query.
After you review your query expression, clickRun query. Logs that match yourquery are listed underQuery results.
Some of the queries listed later on this page include variables that you shouldreplace with valid values. For example, when a query includeslogName, thenthePROJECT_ID you supply must refer to the selectedGoogle Cloud project; otherwise, the query won't work.
Note the following:
If you have a query with a timestamp, then thetime-range selectoris disabled, and the query uses the timestamp expression as its time-rangerestriction. If a query doesn't use a timestamp expression, then the queryuses the time-range selector as its time-range restriction.
The length of a query can't exceed 20,000 characters.
TheLogging query languageis case-insensitive, with the exception of regular expressions.
You can use the
log_idfunction for queries with alog_nameexpression. For example, the expressionlog_name="projects/PROJECT_ID/logs/cloudaudit.googleapis.com%2Fdata_access"is the same aslog_id("cloudaudit.googleapis.com/data_access").For more information about thelog_idfunction, seeLogging query language: Functions.
For instructions about querying in the Google Cloud console, seeBuild queries in the Logs Explorer.
The following sections group queries by Google Cloud services.
App Engine queries
| Query/filter name | Expression |
|---|---|
| App Engine logs from New Year's Eve (in UTC time) | resource.type="gae_app"ANDseverity>=ERRORANDtimestamp>="2018-12-31T00:00:00Z"ANDtimestamp<="2019-01-01T00:00:00Z" |
| App Engine request logs with server errors | resource.type="gae_app"ANDlog_id("appengine.googleapis.com/request_log")ANDhttpRequest.status>=500 |
| Sampled HTTP error logs | resource.type="gae_app"ANDprotoPayload.status>=400ANDsample(insertId,0.1) |
| Search for App Engine trace ID | resource.type="gae_app"ANDtrace="projects/PROJECT_ID/traces/TRACE_ID" |
| App Engine logs | resource.type="gae_app"ANDresource.labels.module_id="MODULE_ID"ANDresource.labels.version_id="VERSION_ID" |
| Recent App Engine deployments | resource.type="gae_app"ANDprotoPayload."@type"="type.googleapis.com/google.cloud.audit.AuditLog"ANDprotoPayload.serviceName="appengine.googleapis.com" |
API enable and disable queries
| Query/filter name | Expression |
|---|---|
| Audit API enable logs | protoPayload.methodName="google.api.serviceusage.v1.ServiceUsage.EnableService" |
| Audit API disable logs | protoPayload.methodName="google.api.serviceusage.v1.ServiceUsage.DisableService" |
BigQuery queries
| Query/filter name | Expression |
|---|---|
| BigQuery audit logs | resource.type=("bigquery_dataset"OR"bigquery_project")ANDlogName:"cloudaudit.googleapis.com" |
| BigQuery audit logs for a project | resource.type="bigquery_project"ANDlogName:"cloudaudit.googleapis.com" |
| BigQuery audit logs for a dataset | resource.type="bigquery_dataset"ANDlogName:"cloudaudit.googleapis.com" |
| BigQuery audit logs for BI Engine Model | resource.type="bigquery_biengine_model"ANDlogName:"cloudaudit.googleapis.com" |
| BigQuery audit logs for a Data Transfer Service Run. | resource.type="bigquery_dts_run"ANDlogName:"cloudaudit.googleapis.com" |
| BigQuery audit logs for a Data Transfer Service configuration. | resource.type="bigquery_dts_config"ANDlogName:"cloudaudit.googleapis.com" |
| BigQuery data transfer service jobs | resource.type=("bigquery_project")ANDprotoPayload.requestMetadata.callerSuppliedUserAgent="BigQuery Data Transfer Service"ANDprotoPayload.methodName=("google.cloud.bigquery.v2.JobService.InsertJob"OR"google.cloud.bigquery.v2.JobService.Query") |
| BigQuery transfer run logs | resource.type="bigquery_dts_config"ANDlabels.run_id="RUN_ID"ANDresource.labels.config_id="CONFIG_ID" |
| BigQuery dataset updates | resource.type="bigquery_dataset"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.methodName="google.cloud.bigquery.v2.DatasetService.UpdateDataset" |
| BigQuery jobs completed | resource.type="bigquery_project"ANDlog_id("cloudaudit.googleapis.com/data_access")ANDprotoPayload.methodName=("google.cloud.bigquery.v2.JobService.InsertJob"OR"google.cloud.bigquery.v2.JobService.Query") |
| BigQuery large queries | resource.type="bigquery_project"ANDprotoPayload.metadata.jobChange.job.jobStats.queryStats.totalBilledBytes>1073741824 |
| BigQuery quota exceeded | resource.type=("bigquery_dataset"OR"bigquery_project")ANDprotoPayload.status.code=8ANDseverity>=WARNING |
| BigQuery query started | resource.type="bigquery_project"ANDprotoPayload.metadata.jobInsertion.reason:* |
| BigQuery concurrent load/extract jobs | resource.type="bigquery_resource"ANDprotoPayload.methodName="jobservice.insert"ANDprotoPayload.serviceData.jobInsertRequest.resource.jobConfiguration.query.query:"extract" |
| BigQuery audit logs for Row Access Policy | protoPayload.methodName="jobservice.insert"ANDprotoPayload.serviceData.jobInsertRequest.resource.jobConfiguration.query.query:"ROW ACCESS POLICY" |
Dataflow queries
| Query/filter name | Expression |
|---|---|
| Errors and warnings in Dataflow workers | resource.type="dataflow_step"ANDlog_id("dataflow.googleapis.com/worker")ANDseverity>=WARNING |
Dataproc queries
| Query/filter name | Expression |
|---|---|
| Dataproc Apache Hadoop logs | resource.type="cloud_dataproc_cluster"ANDjsonPayload.class:"org.apache.hadoop.mapreduce" |
Cloud Deployment Manager
| Query/filter name | Expression |
|---|---|
| Deployment Manager errors | resource.type="deployment"ANDseverity>=ERROR |
Cloud Run functions queries
| Query/filter name | Expression |
|---|---|
| Cloud function errors | resource.type="cloud_function"ANDlog_id("cloudfunctions.googleapis.com/cloud-functions")ANDseverity>=ERROR |
Cloud Monitoring queries
| Query/filter name | Expression |
|---|---|
| Show all notification channel errors | resource.type="stackdriver_notification_channel"ANDseverity>=ERROR |
| Show notification channel errors due to throttling | resource.type="stackdriver_notification_channel"ANDseverity>=ERRORANDjsonPayload.summary="Notification delivery throttled." |
| Show logs written by the uptime resource | resource.type="uptime_url" |
| Show requests received from the uptime-check service | "GoogleStackdriverMonitoring-UptimeChecks" |
Cloud Run queries
| Query/filter name | Expression |
|---|---|
| Cloud Run logs for a specific job | resource.type="cloud_run_job"ANDresource.labels.service_name="JOB_NAME" |
| Cloud Run logs for a specific revision and service | resource.type="cloud_run_revision"ANDresource.labels.service_name="SERVICE_NAME" |
Cloud Source Repositories queries
| Query/filter name | Expression |
|---|---|
| Cloud Source Repository logs | resource.type="csr_repository"ANDresource.labels.name="REPOSITORY_NAME" |
Spanner queries
| Query/filter name | Expression |
|---|---|
| Cloud Spanner logs for a specific spanner instance | resource.type="spanner_instance"ANDresource.labels.instance_id="SPANNER_INSTANCE" |
Cloud SQL queries
| Query/filter name | Expression |
|---|---|
| Cloud SQL audit logs | resource.type="cloudsql_database"ANDresource.labels.database_id="DATABASE_ID"ANDlog_id("cloudaudit.googleapis.com/activity") |
| Cloud SQL MySQL error logs | resource.type="cloudsql_database"ANDlog_id("cloudsql.googleapis.com/mysql.err") |
| Cloud SQL MySQL-based databases | resource.type="cloudsql_database"ANDresource.labels.database_id="DATABASE_ID"ANDlog_id("cloudsql.googleapis.com/mysql") |
| Cloud SQL Postgres-based databases | resource.type="cloudsql_database"ANDresource.labels.database_id="DATABASE_ID"ANDlog_id("cloudsql.googleapis.com/postgres.log") |
| Cloud SQL SQL Server error logs | resource.type="cloudsql_database"ANDlog_id("cloudsql.googleapis.com/sqlserver.err") |
| Cloud SQL SQL Server-based databases | resource.type="cloudsql_database"ANDresource.labels.database_id="DATABASE_ID"ANDlog_id("cloudsql.googleapis.com/sqlagent.out") |
Cloud Storage queries
| Query/filter name | Expression |
|---|---|
| GCS bucket logs | resource.type="gcs_bucket"ANDresource.labels.bucket_name="BUCKET_NAME" |
| GCS bucket audit logs | resource.type="gcs_bucket"ANDlogName:"cloudaudit.googleapis.com" |
| GCS bucket creation logs | resource.type="gcs_bucket"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.method_name="storage.buckets.create" |
| GCS bucket deletion logs | resource.type="gcs_bucket"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.method_name="storage.buckets.delete" |
Cloud Tasks queries
| Query/filter name | Expression |
|---|---|
| Cloud Tasks queue logs | resource.type="cloud_tasks_queue"ANDresource.labels.queue_id="QUEUE_ID" |
Compute Engine queries
| Query/filter name | Expression |
|---|---|
| Compute Engine Admin Activity logs | resource.type="gce_instance"ANDlog_id("cloudaudit.googleapis.com/activity") |
| Compute Engine firewall rule deletion | resource.type="gce_firewall_rule"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.methodName:"firewalls.delete" |
| Compute Engine VM syslogs | resource.type="gce_instance"ANDlog_id("syslog") |
| Compute Engine VM authlogs | resource.type="gce_instance"ANDlog_id("authlog") |
| Compute Engine Host Error | resource.type="gce_instance"protoPayload.serviceName="compute.googleapis.com"(protoPayload.methodName:"compute.instances.hostError"ORoperation.producer:"compute.instances.hostError")log_id("cloudaudit.googleapis.com/system_event")resource.labels.instance_id="INSTANCE_ID"severity=INFO |
| Compute Engine Host Memory Alert | resource.type="gce_instance"ANDprotoPayload.serviceName="compute.googleapis.com"AND(jsonPayload.methodName:"compute.instances.host_event_notify"ORoperation.producer:"compute.instances.host_event_notify")ANDlog_id("cloudaudit.googleapis.com/host_event_notify")ANDresource.labels.instance_id="INSTANCE_ID"ANDseverity=CRITICAL |
| Compute Engine Host Migrated | resource.type="gce_instance"protoPayload.serviceName="compute.googleapis.com"(protoPayload.methodName:"compute.instances.migrateOnHostMaintenance"ORoperation.producer:"compute.instances.migrateOnHostMaintenance")log_id("cloudaudit.googleapis.com/system_event")resource.labels.instance_id="INSTANCE_ID"severity=INFO |
| Compute Engine VM Terminated/Preempted | resource.type="gce_instance"protoPayload.methodName=~"compute\.instances\.(guestTerminate|preempted)"log_id("cloudaudit.googleapis.com/system_event")resource.labels.instance_id="INSTANCE_ID" |
| Compute Engine VM terminated due to Scratch Disk Creation Failure | resource.type="gce_instance"protoPayload.serviceName="compute.googleapis.com"(protoPayload.methodName="compute.instances.scratchDiskCreationFailed"ORoperation.producer:"compute.instances.scratchDiskCreationFailed)log_id("cloudaudit.googleapis.com/system_event")resource.labels.instance_id="INSTANCE_ID"severity=INFO |
| Compute Engine VM Instance Created | resource.type="gce_instance"protoPayload.methodName:"compute.instances.insert"log_id("cloudaudit.googleapis.com/activity")protoPayload.request.name="INSTANCE_NAME" |
| Compute Engine VM Instance Deleted with Name | resource.type="gce_instance"protoPayload.methodName:"compute.instances.delete"log_id("cloudaudit.googleapis.com/activity")protoPayload.resourceName:"INSTANCE_NAME" |
| Compute Engine VM Instance Deleted with ID | resource.type="gce_instance"protoPayload.methodName:"compute.instances.delete"log_id("cloudaudit.googleapis.com/activity")resource.labels.instance_id="INSTANCE_ID" |
| Compute Engine VM Instance Restarted | resource.type="gce_instance"protoPayload.methodName=~"compute\.instances\.(stop|reset|automaticRestart|guestTerminate|instanceManagerHaltForRestart)"(log_id("cloudaudit.googleapis.com/activity")ORlog_id("cloudaudit.googleapis.com/system_event"))resource.labels.instance_id="INSTANCE_ID" |
| Compute Engine Shielded VM Boot Integrity Failure | resource.type="gce_instance"log_id("compute.googleapis.com/shielded_vm_integrity")jsonPayload.earlyBootReportEvent.policyEvaluationPassed="false"resource.labels.instance_id="INSTANCE_ID" |
| Compute Engine VM instance stopped by Guest OS | resource.type="gce_instance"protoPayload.serviceName="compute.googleapis.com"(protoPayload.methodName:"compute.instances.guestTerminate"ORoperation.producer:"compute.instances.guestTerminate")log_id("cloudaudit.googleapis.com/system_event")resource.labels.instance_id="INSTANCE_ID"severity=INFO |
| Compute Engine Shielded VM boot file was blocked | resource.type="gce_instance"log_id("serialconsole.googleapis.com/serial_port_1_output")textPayload:("Security Violation")resource.labels.instance_id="INSTANCE_ID" |
| Persistent Disk Created | resource.type="gce_disk"ANDprotoPayload.methodName:"compute.disks.insert"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.resourceName:"PERSISTENT_DISK_NAME" |
| Nodes added in Sole Tenant Node | resource.type="gce_node_group"log_id("cloudaudit.googleapis.com/activity")protoPayload.methodName=~("compute.nodeGroups.addNodes"OR"compute.nodeGroups.insert")resource.labels.node_group_id="NODE_GROUP_ID"severity="INFO" |
| Autoscale events in Sole Tenant Node | resource.type="gce_node_group"log_id("cloudaudit.googleapis.com/system_event")protoPayload.methodName=~("compute.nodeGroups.deleteNodes"OR"compute.nodeGroups.addNodes")resource.labels.node_group_id="NODE_GROUP_ID" |
| Manual Snapshot Taken | resource.type="gce_snapshot"log_id("cloudaudit.googleapis.com/activity")protoPayload.methodName:"compute.snapshots.insert"protoPayload.resourceName:"SNAPSHOT_NAME" |
| Scheduled Snapshot Taken | resource.type="gce_disk"log_id("cloudaudit.googleapis.com/system_event")protoPayload.methodName="ScheduledSnapshots"protoPayload.response.operationType="createSnapshot"protoPayload.response.targetLink="PERSISTENT_DISK_NAME" |
| Snapshot Schedule Created | resource.type="gce_resource_policy"log_id("cloudaudit.googleapis.com/activity")protoPayload.methodName:"compute.resourcePolicies.insert"protoPayload.request.name="SCHEDULE_NAME" |
| Snapshot Schedule Attached | resource.type="gce_disk"log_id("cloudaudit.googleapis.com/activity")protoPayload.methodName:"compute.disks.addResourcePolicies"protoPayload.request.resourcePolicys:"SCHEDULE_NAME"protoPayload.resourceName:"PERSISTENT_DISK_NAME" |
| Quota Exceeded | resource.type="gce_instance"protoPayload.methodName:"compute.instances.insert"protoPayload.status.message:"QUOTA_EXCEEDED"severity=ERROR |
| Query unhealthy instances in instance group | resource.type="gce_instance_group"resource.labels.instance_group_name="INSTANCE_GROUP_NAME"jsonPayload.healthCheckProbeResult.healthState="UNHEALTHY" |
| Query instance group members within a time frame in UTC time format | resource.type="gce_instance_group_manager"resource.labels.instance_group_manager_name="INSTANCE_GROUP_NAME"jsonPayload.@type="type.googleapis.com/compute.InstanceGroupManagerEvent"jsonPayload.instanceHealthStateChange.detailedHealthState="HEALTHY"timestamp>=START_TIMEtimestamp<=END_TIME |
| Instances added to Instance Group | resource.type="gce_instance_group"protoPayload.methodName:"compute.instanceGroups.addInstances"log_id("cloudaudit.googleapis.com/activity")resource.labels.instance_group_name="INSTANCE_GROUP_NAME" |
| Instances removed from Instance Group | resource.type="gce_instance_group"protoPayload.methodName:"compute.instanceGroups.removeInstances"log_id("cloudaudit.googleapis.com/activity")resource.labels.instance_group_name="INSTANCE_GROUP_NAME" |
| Instance template set or updated | resource.type="gce_instance_group_manager"log_id("cloudaudit.googleapis.com/activity")protoPayload.methodName="v1.compute.instanceGroupManagers.setInstanceTemplate"resource.labels.instance_group_manager_name="INSTANCE_GROUP_MANAGER" |
| Firewall rule deleted | resource.type="gce_firewall_rule"log_id("cloudaudit.googleapis.com/activity")protoPayload.methodName:"firewalls.delete" |
| Firewall logs | resource.type="gce_subnetwork"log_id("compute.googleapis.com/firewall")jsonPayload.instance.vm_name="INSTANCE_NAME" |
Google Cloud Observability queries
| Query/filter name | Expression |
|---|---|
| Log sink activities | resource.type="logging_sink"ANDlog_id("cloudaudit.googleapis.com/activity") |
| Log-based metric create or update activities | resource.type="metric"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.methodName:(UpdateLogMetricORCreateLogMetric) |
| Uptime URL checks for a host | resource.type="uptime_url"ANDresource.labels.host="URL" |
Identity and Access Management queries
| Query/filter name | Expression |
|---|---|
| Service account creation logs | resource.type="service_account"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.methodName="google.iam.admin.v1.CreateServiceAccount" |
| Service account creation key logs | resource.type="service_account"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.methodName="google.iam.admin.v1.CreateServiceAccountKey" |
| Set access control policy logs | resource.type="project"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.methodName="SetIamPolicy" |
| External principal granted access to organization | resource.type="project"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.@type="type.googleapis.com/google.cloud.audit.AuditLog"ANDprotoPayload.request.@type:"IamPolicy"ANDprotoPayload.serviceData.policyDelta.bindingDeltas.member:*ANDNOTprotoPayload.serviceData.policyDelta.bindingDeltas.member:"@DOMAIN_NAME.com" |
| Resource creation, modification, or deletion | log_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.methodName:("create"OR"delete"OR"update") |
| Role granted to principal | log_id("cloudaudit.googleapis.com/activity")ANDresource.type="project"ANDprotoPayload.serviceName="cloudresourcemanager.googleapis.com"ANDprotoPayload.methodName="SetIamPolicy"ANDprotoPayload.serviceData.policyDelta.bindingDeltas.action="Add"ANDprotoPayload.serviceData.policyDelta.bindingDeltas.member:"EMAIL_ID" |
| Role removed from principal | log_id("cloudaudit.googleapis.com/activity")ANDresource.type="project"ANDprotoPayload.serviceName="cloudresourcemanager.googleapis.com"ANDprotoPayload.methodName="SetIamPolicy"ANDprotoPayload.serviceData.policyDelta.bindingDeltas.action="Remove"ANDprotoPayload.serviceData.policyDelta.bindingDeltas.member:"EMAIL_ID" |
| Permission updated in a custom role | log_id("cloudaudit.googleapis.com/activity")ANDresource.type="iam_role"ANDprotoPayload.serviceName="iam.googleapis.com"ANDprotoPayload.methodName:"UpdateRole"ANDresource.labels.role_name:"ROLE_ID" |
Kubernetes-related queries
For an overview and examples of Admin Activity audit log queries, see those provided on theGKE Audit logging page.Cluster-level queries
| Query/filter name | Expression |
|---|---|
| Google Kubernetes Engine cluster operations | resource.type="gke_cluster"ANDlog_id("cloudaudit.googleapis.com/activity") |
| Google Kubernetes Engine cluster creation | resource.type="gke_cluster"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.methodName="google.container.v1.ClusterManager.CreateCluster" |
| Kubernetes cluster deployment | resource.type="k8s_cluster"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.methodName:"deployments" |
| Kubernetes cluster authentication failure | resource.type="k8s_cluster"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.authenticationInfo.principalEmail="system:anonymous" |
Kubernetes cluster operations and events inus-central1-b | resource.type="k8s_cluster"ANDresource.labels.location="us-central1-b" |
| Kubernetes pod requests from users | resource.type="k8s_cluster"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.methodName:"io.k8s.core.v1.pods"ANDprotoPayload.authenticationInfo.principalEmail="USER_EMAIL" |
| Kubernetes events | resource.type="k8s_cluster"ANDlog_id("events") |
| Kubernetes Endpoints update | resource.type="k8s_cluster"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.request.kind="Endpoints" |
| Kubernetes control plane logs | resource.type="k8s_cluster"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.serviceName="k8s.io" |
| Kubernetes Engine control plane logs | resource.type="k8s_cluster"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.serviceName="container.googleapis.com" |
| Pod deletion | resource.type="k8s_cluster"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.methodName=~"io\.k8s\.core\.v1\.pods\.(create|delete)" |
| Kubernetes pod audit logs from control plane | resource.type="k8s_cluster"ANDresource.labels.location="CLUSTER_LOCATION"ANDresource.labels.cluster_name="CLUSTER_NAME"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.resourceName="core/v1/namespaces/POD_NAMESPACE/pods/POD_NAME |
| Kubernetes pod evictions | resource.type="k8s_cluster"ANDresource.labels.location="CLUSTER_LOCATION"ANDresource.labels.cluster_name="CLUSTER_NAME"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.methodName="io.k8s.core.v1.pods.eviction.create" |
| Kubernetes node audit logs from the control plane | resource.type="k8s_cluster"ANDresource.labels.location="CLUSTER_LOCATION"ANDresource.labels.cluster_name="CLUSTER_NAME"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.methodName:"io.k8s.core.v1.nodes" |
| Kubernetes cluster control plane for Addon Manager Activity | resource.type="k8s_cluster"ANDresource.labels.location="CLUSTER_LOCATION"ANDresource.labels.cluster_name="CLUSTER_NAME"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.authenticationInfo.principalEmail="system:addon-manager" |
Kubernetes control plane errors (excludingConflict, which is normal) | resource.type="k8s_cluster"ANDresource.labels.location="CLUSTER_LOCATION"ANDresource.labels.cluster_name="CLUSTER_NAME"ANDlog_id("cloudaudit.googleapis.com/activity")ANDprotoPayload.status.message!="Conflict"ANDprotoPayload.status.code!=0 |
| Ingress Controller events | resource.type="k8s_cluster"ANDresource.labels.location="CLUSTER_LOCATION"ANDresource.labels.cluster_name="CLUSTER_NAME"ANDlog_id("events")ANDjsonPayload.source.component="loadbalancer-controller" |
| Service Controller events (kube-controller-manager) | resource.type="k8s_cluster"ANDresource.labels.location="CLUSTER_LOCATION"ANDresource.labels.cluster_name="CLUSTER_NAME"ANDlog_id("events")ANDjsonPayload.source.component="service-controller" |
| Cluster Autoscaler events | resource.type="k8s_cluster"ANDresource.labels.location="CLUSTER_LOCATION"ANDresource.labels.cluster_name="CLUSTER_NAME"ANDlog_id("events")ANDjsonPayload.source.component="cluster-autoscaler" |
Pod-level queries
| Filter name | Expression |
|---|---|
| Query pod during creation | resource.type="k8s_pod"ANDresource.labels.pod_name="POD_NAME"ANDlog_id("events") |
| Query pod terminated due to resource pressure | resource.type="k8s_pod"ANDlog_id("events")ANDjsonPayload.reason="Evicted" |
| Scheduler events | resource.type="k8s_pod"ANDresource.labels.location="CLUSTER_LOCATION"ANDresource.labels.cluster_name="CLUSTER_NAME"ANDlog_id("events")ANDjsonPayload.source.component="default-scheduler" |
| Scheduler events (preemptions) | resource.type="k8s_pod"ANDresource.labels.location="CLUSTER_LOCATION"ANDresource.labels.cluster_name="CLUSTER_NAME"ANDlog_id("events")ANDjsonPayload.source.component="default-scheduler"ANDjsonPayload.reason="Preempted" |
Node-level queries
| Filter name | Expression |
|---|---|
| Node events | resource.type="k8s_node"ANDlog_id("events") |
| Looking at Kube-proxy logs | resource.type="k8s_node"ANDlog_id("kube-proxy") |
| Looking at dockerd logs | resource.type="k8s_node"ANDlog_id("container-runtime") |
| Looking at kubelet errors or failures | resource.type="k8s_node"ANDlog_id("kubelet")ANDjsonPayload.MESSAGE:("error"OR"fail") |
| Looking at node logs for GKE system logs | resource.type="k8s_node"logName:("logs/container-runtime"OR"logs/docker"OR"logs/kube-container-runtime-monitor"OR"logs/kube-logrotate"OR"logs/kube-node-configuration"OR"logs/kube-node-installation"OR"logs/kubelet"OR"logs/kubelet-monitor"OR"logs/node-journal"OR"logs/node-problem-detector") |
Namespace queries
| Filter name | Expression |
|---|---|
| Container and pod logs for GKE system logs | resource.type=("k8s_container"OR"k8s_pod")resource.labels.namespace_name=("cnrm-system"OR"config-management-system"OR"gatekeeper-system"OR"gke-connect"OR"gke-system"OR"istio-system"OR"knative-serving"OR"monitoring-system"OR"kube-system") |
Container queries
| Filter name | Expression |
|---|---|
| Stdout container logs across all pods and containers in a cluster | resource.type="k8s_container"ANDlog_id("stdout") |
| Container error logs across all pods and containers in a cluster | resource.type="k8s_container"ANDlog_id("stderr")ANDseverity=ERROR |
| Container error logs for a pod with a specific name | resource.type="k8s_container"ANDresource.labels.pod_name="POD_NAME"ANDseverity=ERROR |
| Container error logs for a specific container in a specific pod | resource.type="k8s_container"ANDresource.labels.pod_name="POD_NAME"ANDresource.labels.container_name="server"ANDseverity=ERROR |
| Container error logs for a specific namespace and container | resource.type="k8s_container"ANDresource.labels.namespace_name="istio-system"ANDresource.labels.container_name="egressgateway"ANDseverity=ERROR |
| Container logs for a pod with a specific label | resource.type="k8s_container"ANDlabels."k8s-pod/app"="loadgenerator"ANDseverity=ERROR |
| Container error logs for pods running on a specific node | resource.type="k8s_container"ANDlabels."compute.googleapis.com/resource_name"=NODE_NAMEANDseverity=ERROR |
| Container logs for a pod with a label generated using skaffold | resource.type="k8s_container"ANDlabels."k8s-pod/app"="loadgenerator"ANDlabels."k8s-pod/skaffold_dev/run-id"=SKAFFOLD_RUN_IDseverity=ERROR |
Container error logs for a specific pod containing aPOST in the textPayload | resource.type="k8s_container"ANDresource.labels.pod_name="POD_NAME"ANDtextPayload:"POST"ANDseverity=ERROR |
Container error logs for a specific pod containing aGET in the structured JSON | resource.type="k8s_container"ANDresource.labels.pod_name="POD_NAME"ANDjsonPayload."http.req.method"="GET"ANDseverity=ERROR |
| Container errors logs in the kube-system namespace | resource.type="k8s_container"ANDresource.labels.namespace_name="kube-system"ANDseverity=ERROR |
| Container error in the container insights log | resource.type="k8s_container"ANDlog_id("clouderrorreporting.googleapis.com/insights") |
| Kubernetes container logs | resource.type="k8s_container"ANDresource.labels.container_name="CONTAINER_NAME" |
Control plane queries
Note: GKE control plane logs must be enabled.| Filter name | Expression |
|---|---|
| Kubernetes API server logs | resource.type="k8s_control_plane_component"resource.labels.component_name="apiserver"resource.labels.location="CLUSTER_LOCATION"resource.labels.cluster_name="CLUSTER_NAME" |
| Kubernetes Scheduler logs | resource.type="k8s_control_plane_component"resource.labels.component_name="scheduler"resource.labels.location="CLUSTER_LOCATION"resource.labels.cluster_name="CLUSTER_NAME" |
| Kubernetes Controller Manager logs | resource.type="k8s_control_plane_component"resource.labels.component_name="controller-manager"resource.labels.location="CLUSTER_LOCATION"resource.labels.cluster_name="CLUSTER_NAME" |
TPU workload queries
Note: GKE system and workload logging must be enabled.| Filter name | Expression |
|---|---|
| Stdout container logs across all TPU nodes with the same prefix | resource.type="k8s_container"ANDlabels."compute.googleapis.com/resource_name"=~"TPU_NODE_PREFIX.*"ANDlog_id("stdout") |
| Container error logs across all TPU nodes with the same prefix | resource.type="k8s_container"ANDlabels."compute.googleapis.com/resource_name"=~"TPU_NODE_PREFIX.*"ANDlog_id("stderr")ANDseverity=ERROR |
| Stdout container logs from the same GKE Job | resource.type="k8s_container"ANDlabels."k8s-pod/batch.kubernetes.io/job-name"="JOB_NAME"ANDlog_id("stdout") |
| Container error logs from the same GKE Job | resource.type="k8s_container"ANDlabels."k8s-pod/batch.kubernetes.io/job-name"="JOB_NAME"ANDlog_id("stderr")ANDseverity=ERROR |
| Stdout container logs from the same GKE JobSet | resource.type="k8s_container"ANDlabels."k8s-pod/jobset_sigs_k8s_io/jobset-name"="JOBSET_NAME"ANDlog_id("stdout") |
| Container error logs from the same GKE JobSet | resource.type="k8s_container"ANDlabels."k8s-pod/jobset_sigs_k8s_io/jobset-name"="JOBSET_NAME"ANDlog_id("stderr")ANDseverity=ERROR |
Third-party application queries
The following queries use thedefault log IDsfor logs collected by thelegacy Logging agent. If you arecollecting logs by using theOps Agent,then the log names might be configured differently. For more informationabout the Ops Agent and application logs, seeCollect logs fromthird-party applications.
| Query/filter name | Expression |
|---|---|
| Apache logs | resource.type="gce_instance"AND(logName:"/apache-access"ORlogName:"/apache-error") |
| Cassandra logs | resource.type="gce_instance"ANDlog_id("cassandra") |
| Chef logs | resource.type="gce_instance"ANDlogName:"projects/PROJECT_ID/logs/chef-" |
| Gitlab logs | resource.type="gce_instance"logName:"projects/PROJECT_ID/logs/gitlab-" |
| Jenkins logs | resource.type="gce_instance"ANDlog_id("jenkins") |
| Jetty logs | resource.type="gce_instance"ANDlogName:"projects/PROJECT_ID/logs/jetty-" |
| Joomla logs | resource.type="gce_instance"ANDlog_id("joomla") |
| Linux syslogs | resource.type="gce_instance"ANDlog_id("syslog") |
| Magneto logs | resource.type="gce_instance"ANDlogName:"projects/PROJECT_ID/logs/magneto-" |
| Mediawiki logs | resource.type="gce_instance"ANDlog_id("mediawiki") |
| memcached logs | resource.type="gce_instance"ANDlog_id("memcached") |
| MongoDB logs | resource.type="gce_instance"ANDlog_id("mongodb") |
| MySQL logs | resource.type="gce_instance"ANDlog_id("mysql") |
| Nginx logs | resource.type="gce_instance"ANDlogName:"projects/PROJECT_ID/logs/nginx-" |
| PostgreSQL logs | resource.type="gce_instance"ANDlog_id("postgresql") |
| Puppet logs | resource.type="gce_instance"ANDlogName:"projects/PROJECT_ID/logs/puppet-" |
| RabbitMQ logs | resource.type="gce_instance"ANDlogName:"projects/PROJECT_ID/logs/rabbitmq-" |
| Redmine logs | resource.type="gce_instance"ANDlog_id("redmine") |
| Salt logs | resource.type="gce_instance"ANDlogName:"projects/PROJECT_ID/logs/salt-" |
| Slow MySQL queries | resource.type="gce_instance"ANDlog_id("mysql-slow") |
| Solr logs | resource.type="gce_instance"ANDlog_id("solr") |
| SugarCRM logs | resource.type="gce_instance"ANDlog_id("sugarcrm") |
| Tomcat logs | resource.type="gce_instance"ANDlog_id("tomcat") |
| Zookeeper logs | resource.type="gce_instance"ANDlog_id("zookeeper") |
Networking queries
| Query/filter name | Expression |
|---|---|
| Firewall- all logs | resource.type="gce_subnetwork"ANDlog_id("compute.googleapis.com/firewall") |
| Firewall logs for a given country | resource.type="gce_subnetwork"ANDlog_id("compute.googleapis.com/firewall")ANDjsonPayload.remote_location.country=COUNTRY_ISO_ALPHA_3 |
| Firewall logs from a VM | resource.type="gce_subnetwork"ANDlog_id("compute.googleapis.com/firewall")ANDjsonPayload.instance.vm_name="INSTANCE_NAME" |
| Firewall subnet logs | resource.type="gce_subnetwork"ANDlog_id("compute.googleapis.com/firewall")ANDresource.labels.subnetwork_name="SUBNET_NAME" |
| Compute Engine subnetwork traffic logs to a subnet | resource.type="gce_subnetwork"ANDip_in_net(jsonPayload.connection.dest_ip,"SUBNET_IP") |
| VPC Flow logs | resource.type="gce_subnetwork"ANDlog_id("compute.googleapis.com/vpc_flows") |
| VPC Flow logs for specific port and protocol | resource.type="gce_subnetwork"ANDlog_id("compute.googleapis.com/vpc_flows")ANDjsonPayload.connection.src_port="PORT_ID"ANDjsonPayload.connection.protocol="PROTOCOL" |
| VPC Flow logs for specific subnet | resource.type="gce_subnetwork"ANDlog_id("compute.googleapis.com/vpc_flows")ANDresource.labels.subnetwork_name"=SUBNET_NAME" |
| VPC Flow logs for specific subnet prefix | resource.type="gce_subnetwork"ANDlog_id("compute.googleapis.com/vpc_flows")ANDip_in_net(jsonPayload.connection.dest_ip,SUBNET_IP) |
| VPC Flow logs for a specific VM | resource.type="gce_subnetwork"ANDlog_id("compute.googleapis.com/vpc_flows")ANDjsonPayload.src_instance.vm_name="VM_NAME" |
| VPN gateway logs | resource.type="vpn_gateway"ANDresource.labels.gateway_id="GATEWAY_ID" |
| HTTP Load Balancer 5xx errors | resource.type="http_load_balancer"ANDhttpRequest.status>=500 |
| HTTP Load Balancer requests to PHPMyAdmin | resource.type="http_load_balancer"ANDhttpRequest.request_url:"phpmyadmin" |
Security queries
| Query/filter name | Expression |
|---|---|
| Audit logs—all | logName:"cloudaudit.googleapis.com" |
| Audit logs- Access Transparency (AXT) | log_id("cloudaudit.googleapis.com/access_transparency") |
| Audit logs- Admin Activity | log_id("cloudaudit.googleapis.com/activity") |
| Audit logs- Data Access | log_id("cloudaudit.googleapis.com/data_access") |
| Audit logs- System Event | log_id("cloudaudit.googleapis.com/system_event") |
Troubleshooting
For instructions about troubleshooting common issues when using theLogs Explorer, seeUsing the Logs Explorer: Troubleshooting.
What's next
For more information about the query syntax, which you can use to customizethese queries, seeLogging query language.
For more information about querying in the Google Cloud console, seeBuild queries by using the Logging query language.
Except as otherwise noted, the content of this page is licensed under theCreative Commons Attribution 4.0 License, and code samples are licensed under theApache 2.0 License. For details, see theGoogle Developers Site Policies. Java is a registered trademark of Oracle and/or its affiliates.
Last updated 2026-02-19 UTC.
