- Notifications
You must be signed in to change notification settings - Fork131
Humanitec AWS Reference Architecture implementation
License
humanitec-architecture/reference-architecture-aws
Folders and files
| Name | Name | Last commit message | Last commit date | |
|---|---|---|---|---|
Repository files navigation
The deprecation only affects the reference implementation contained in this repository, not the underlying conceptual architectures and supplementary materials shown on theHumanitec website.
TL;DR
Skip the theory? Gohere to spin up your Humanitec AWS Reference Architecture Implementation.
Follow this learning path to master your Internal Developer Platform.
Building an Internal Developer Platform (IDP) can come with many challenges. To give you a head start, we’ve created a set ofreference architectures based on hundreds of real-world setups. These architectures described in code provide a starting point to build your own IDP within minutes, along with customization capabilities to ensure your platform meets the unique needs of your users (developers).
The initial version of this reference architecture has been presented by Mike Gatto, Sr. DevOps Engineer, McKinsey and Stephan Schneider, Digital Expert Associate Partner, McKinsey atPlartformCon 2023.
AnInternal Developer Platform (IDP) is the sum of all the tech and tools that a platform engineering team binds together to pave golden paths for developers. IDPs lower cognitive load across the engineering organization and enable developer self-service, without abstracting away context from developers or making the underlying tech inaccessible. Well-designed IDPs follow a Platform as a Product approach, where a platform team builds, maintains, and continuously improves the IDP, following product management principles and best practices.
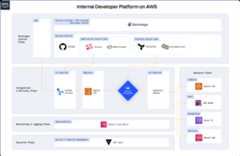
When McKinsey originallypublished the reference architecture they proposed five planes that describe the different parts of a modern Internal Developer Platform (IDP).
This plane is the primary configuration layer and interaction point for the platform users. It harbors the following components:
- AVersion Control System. GitHub is a prominent example, but this can be any system that contains two types of repositories:
- Application Source Code
- Platform Source Code, e.g. using Terraform
- Workload specifications. The reference architecture usesScore.
- Aportal for developers to interact with. It can be the Humanitec Portal, but you might also useBackstage or any other portal on the market.
This plane is about building and storing the image, creating app and infra configs from the abstractions provided by the developers, and deploying the final state. It’s where the domains of developers and platform engineers meet.
This plane usually contains four different tools:
- ACI pipeline. It can be Github Actions or any CI tooling on the market.
- Theimage registry holding your container images. Again, this can be any registry on the market.
- Anorchestrator which in our example, is the Humanitec Platform Orchestrator.
- TheCD system, which can be the Platform Orchestrator’s deployment pipeline capabilities — an external system triggered by the Orchestrator using a webhook, or a setup in tandem with GitOps operators like ArgoCD.
The integration of monitoring and logging systems varies greatly depending on the system. This plane however is not a focus of the reference architecture.
The security plane of the reference architecture is focused on the secrets management system. The secrets manager stores configuration information such as database passwords, API keys, or TLS certificates needed by an Application at runtime. It allows the Platform Orchestrator to reference the secrets and inject them into the Workloads dynamically. You can learn more about secrets management and integration with other secrets managementhere.
The reference architecture sample implementations use the secrets store attached to the Humanitec SaaS system.
This plane is where the actual infrastructure exists including clusters, databases, storage, or DNS services. The configuration of the Resources is managed by the Platform Orchestrator which dynamically creates app and infrastructure configurations with every deployment and creates, updates, or deletes dependent Resources as required.
This repo contains an implementation of part of the Humanitec Reference Architecture for an Internal Developer Platform, including Backstage as optional Portal solution.
This repo covers the base layer of the implementation for AWS.
By default, the following will be provisioned:
- VPC
- EKS Cluster
- IAM User to access the cluster
- Ingress NGINX in the cluster
- Resource Definitions in Humanitec for:
- Kubernetes Cluster
- A Humanitec account with the
Administratorrole in an Organization. Get afree trial if you are just starting. - An AWS account
- AWS CLI installed locally
- terraform installed locally
- (Optional)Humanitec CLI installed locally
- (Optional)GitHub CLI installed locally
Note: Using this Reference Architecture Implementation will incur costs for your AWS project.
It is recommended that you fully review the code before you run it to ensure you understand the impact of provisioning this infrastructure.Humanitec does not take responsibility for any costs incurred or damage caused when using the Reference Architecture Implementation.
This reference architecture implementation uses Terraform. You will need to do the following:
Fork this GitHub repo, clone it to your local machine and navigate to the root of the repository.
Set the required input variables. (seeRequired input variables)
Ensure you are logged in with
aws. (Follow thequickstart if you aren't)Login to Humanitec (your user needs to have the
Administratorrole on the Humanitec Organization)humctl login
Alternatively: Set the
HUMANITEC_TOKENenvironment variable to an appropriateHumanitec API token with theAdministratorrole on the Humanitec Organization.
For example:
export HUMANITEC_TOKEN="my-humanitec-api-token"
Run terraform:
terraform initterraform planterraform apply
Terraform reads variables by default from a file calledterraform.tfvars. You can create your own file by renaming theterraform.tfvars.example file in the root of the repo and then filling in the missing values.
You can see find a details about each of those variables and additional supported variables underInputs.
Check for the existence of key elements of the reference architecture. This is a subset of all elements only. For a complete list of what was installed, review the Terraform code.
Set the
HUMANITEC_ORGenvironment variable to the ID of your Humanitec Organization (must be all lowercase):export HUMANITEC_ORG="my-humanitec-org"
Verify the existence of the Resource Definition for the EKS cluster in your Humanitec Organization:
curl -s https://api.humanitec.io/orgs/${HUMANITEC_ORG}/resources/defs/ref-arch \ --header"Authorization: Bearer${HUMANITEC_TOKEN}" \| jq .id,.type
This should output:
"ref-arch""k8s-cluster"
Verify the existence of the newly created EKS cluster:
aws eks list-clusters --region<your-region>
This should output:
{"clusters": ["ref-arch","[more previously existing clusters here]" ]}
Backstage requires a GitHub connection, which in turn needs:
A GitHub organization and permission to create new repositories in it. Go tohttps://github.com/account/organizations/new to create a new org (the "Free" option is fine). Note: is has to be an organization, a free account is not sufficient.
Configured GitHub access
Either using the GitHub CLI:
gh auth login --scopes repo,workflow,admin:org,delete_repo
Or using a token:
Create a classic github personal access token with
repo,workflow,delete_repoandadmin:orgscopehere.Set the
GITHUB_TOKENenvironment variable to your token.export GITHUB_TOKEN="my-github-token"
Set the
GITHUB_ORG_IDenvironment variable to your GitHub organization ID.export GITHUB_ORG_ID="my-github-org-id"
Install the GitHub App for Backstage into your GitHub organization
- Run
docker run --rm -it -e GITHUB_ORG_ID -v $(pwd):/pwd -p 127.0.0.1:3000:3000 ghcr.io/humanitec-architecture/create-gh-app(image source) and follow the instructions:- “All repositories” ~> Install
- “Okay, […] was installed on the […] account.” ~> You can close the window and server.
- Run
- Enable
with_backstageinside yourterraform.tfvarsand configure the additional variables that a required for Backstage. - Perform another
terraform apply
- Fetch the DNS entry of the Humanitec Application
backstage, Environmentdevelopment. - Open the host in your browser.
- Click the "Create" button and scaffold your first application.
Once you are finished with the reference architecture, you can remove all provisioned infrastructure and the resource definitions created in Humanitec with the following:
Delete all Humanitec Applications scaffolded using the Portal, if you used one, but not the
backstageapp itself.Ensure you are (still) logged in with
aws.Ensure you still have the
HUMANITEC_TOKENenvironment variable set to an appropriate Humanitec API token with theAdministratorrole on the Humanitec Organization.Run terraform:
terraform destroy
| Name | Version |
|---|---|
| terraform | >= 1.3.0 |
| aws | ~> 5.17 |
| github | ~> 5.38 |
| helm | ~> 2.12 |
| humanitec | ~> 1.0 |
| kubernetes | ~> 2.25 |
| random | ~> 3.5 |
| Name | Version |
|---|---|
| humanitec | ~> 1.0 |
| Name | Source | Version |
|---|---|---|
| base | ./modules/base | n/a |
| github | ./modules/github | n/a |
| github_app | github.com/humanitec-architecture/shared-terraform-modules//modules/github-app | v2024-06-12 |
| portal_backstage | ./modules/portal-backstage | n/a |
| Name | Type |
|---|---|
| humanitec_service_user_token.deployer | resource |
| humanitec_user.deployer | resource |
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| aws_account_id | AWS Account (ID) to use | string | n/a | yes |
| aws_region | AWS region | string | n/a | yes |
| disk_size | Disk size in GB to use for EKS nodes | number | 20 | no |
| github_org_id | GitHub org id (required for Backstage) | string | null | no |
| humanitec_org_id | Humanitec Organization ID (required for Backstage) | string | null | no |
| instance_types | List of EC2 instances types to use for EKS nodes | list(string) | [ | no |
| with_backstage | Deploy Backstage | bool | false | no |
Expand your knowledge by heading over to our learning path, and discover how to:
- Deploy the Humanitec reference architecture using a cloud provider of your choice
- Deploy and manage Applications using the Humanitec Platform Orchestrator and Score
- Provision additional Resources and connect to them
- Achieve standardization by design
- Deal with special scenarios
Master your Internal Developer Platform
- Introduction
- Design principles
- Structure and integration points
- Dynamic Configuration Management
- Tutorial: Set up the reference architecture in your cloud
- Theory on developer workflows
- Tutorial: Scaffold a new Workload and create staging and prod Environments
- Tutorial: Deploy an Amazon S3 Resource to production
- Tutorial: Perform daily developer activities (debug, rollback, diffs, logs)
- Tutorial: Deploy ephemeral Environments
- Theory on platform engineering workflows
- Resource management theory
- Tutorial: Provision a Redis cluster on AWS using Terraform
- Tutorial: Update Resource Definitions for related Applications
About
Humanitec AWS Reference Architecture implementation
Topics
Resources
License
Uh oh!
There was an error while loading.Please reload this page.
Stars
Watchers
Forks
Contributors8
Uh oh!
There was an error while loading.Please reload this page.